IoT Device Compliance: FDA Postmarket Audit Guide
Post Summary
Connected medical devices like insulin pumps and patient monitors face ongoing cybersecurity risks that can impact patient safety. The FDA enforces strict postmarket requirements to ensure these devices remain secure and effective after deployment. This guide breaks down how manufacturers and healthcare organizations can meet these requirements.
Key Takeaways:
- FDA Oversight: The FDA monitors IoT medical devices for safety and cybersecurity through regulations like Section 522 and Section 524B of the FD&C Act.
- Cybersecurity Compliance: Manufacturers must continuously monitor vulnerabilities, provide timely security updates, and maintain a Software Bill of Materials (SBOM).
- Postmarket Audits: FDA audits focus on quality systems, risk management, and documentation. Gaps can lead to enforcement actions.
- Healthcare's Role: Hospitals and clinics must secure device deployment, apply updates, and report incidents.
How to Prepare:
- Maintain Documentation: Keep detailed records of risk management, SBOMs, updates, and incident responses.
- Monitor Threats: Use tools like CVE tracking and threat intelligence feeds.
- Collaborate: Work with healthcare providers to align on patching, monitoring, and incident response.
- Simulate Audits: Conduct internal reviews to ensure FDA readiness.
The stakes are high - proactive management of connected devices is essential for patient safety and regulatory compliance.
FDA Postmarket Oversight Framework for IoT Devices
Regulatory Framework and Cyber Device Definitions
The FDA's approach to overseeing IoT medical devices after they hit the market is built on several statutory requirements. At its core is the Federal Food, Drug, and Cosmetic (FD&C) Act, which lays out provisions like Section 522 for postmarket surveillance, Medical Device Reporting rules, and quality system regulations. These rules apply broadly to all medical devices, covering areas such as adverse event reporting, post-approval studies, and quality management systems.
A significant update came with Section 524B of the FD&C Act, introduced through the Consolidated Appropriations Act of 2023. This section formally defines a "cyber device" and makes cybersecurity a statutory requirement rather than just a guideline. A cyber device is any medical device that uses validated manufacturer software, connects to the internet, and is susceptible to cybersecurity threats. Under this law, manufacturers must submit a plan during the premarket process to address postmarket cybersecurity risks. This includes monitoring vulnerabilities, deploying security updates, and providing a software bill of materials (SBOM) that lists all commercial, open-source, and off-the-shelf components used in the device. While these requirements begin at the premarket stage, they extend into the postmarket phase, where manufacturers are obligated to maintain their monitoring programs and implement updates as planned.
Key FDA Guidance Documents
The FDA has issued several guidance documents to clarify how manufacturers should handle cybersecurity risks. One of the most important is the 2016 "Postmarket Management of Cybersecurity in Medical Devices" guidance, which lays out a risk-based framework for addressing vulnerabilities in devices already on the market. This document emphasizes ongoing monitoring, assessing risks, timely fixes, and coordinated vulnerability disclosure. It also notes that manufacturers don’t need to file individual Medical Device Reporting (MDR) submissions for every vulnerability if risk-based remediation is applied and no serious adverse events occur.
The "Postmarket Surveillance Under Section 522" guidance provides a roadmap for manufacturers under 522 orders to design scientifically sound surveillance programs. For IoT devices, this could involve tracking cybersecurity-related performance issues or identifying failure modes. Other FDA guidance documents focus on lifecycle security, documenting security controls, managing SBOMs, and integrating cybersecurity risk management into design controls and quality systems. Together, these documents create a detailed framework where cybersecurity is treated as a key part of device safety.
How FDA Conducts Postmarket Audits
The FDA uses its statutory and guidance frameworks to guide a structured audit process. Routine surveillance inspections focus on quality system elements outlined in 21 CFR Part 820, such as design controls, corrective and preventive actions (CAPA), complaint handling, and cybersecurity risk management. The FDA also conducts targeted "for-cause" inspections when specific triggers arise, such as cyber incidents, patterns in adverse event reports, or recalls.
During inspections, FDA investigators review documentation to ensure manufacturers are actively monitoring for cybersecurity vulnerabilities, prioritizing and addressing them, and effectively communicating updates to customers and the agency. They also check for compliance with Section 522 orders or post-approval study commitments that include cybersecurity outcomes. For IoT device manufacturers, significant gaps in these areas can lead to warning letters, enforcement actions, or mandated corrective plans. The FDA’s primary focus is on ensuring that postmarket cybersecurity measures are proactive, systematic, and risk-based, rather than reactive and inconsistent.
Postmarket Cybersecurity Requirements for IoT Devices
Continuous Vulnerability Monitoring and Threat Intelligence
Under Section 524B of the FD&C Act, manufacturers of cyber devices are required to maintain a plan to monitor, identify, and address postmarket cybersecurity vulnerabilities and exploits promptly [2]. This involves an ongoing, systematic approach to monitoring software, firmware, and infrastructure to prevent vulnerabilities that could compromise patient safety or critical clinical functions.
To achieve this, manufacturers rely on tools like threat intelligence feeds (e.g., ISACs, MITRE), CVE and NVD tracking, and their software bill of materials (SBOM). The SBOM is especially crucial - it allows manufacturers to quickly trace which device models and firmware versions are affected when a new CVE is identified for an open-source component. This helps assess clinical risks and prioritize fixes based on severity [2][3]. This constant vigilance forms the backbone of coordinated vulnerability disclosure and rapid patch deployment, ensuring devices remain secure after they hit the market.
The challenge is significant: over 60% of healthcare organizations struggle with accurate device inventories and timely patching, and 56% have faced IoT-related cyberattacks [3]. Centralized platforms like Censinet RiskOps simplify this process by aggregating risk and threat intelligence across clinical applications and medical devices, enabling better risk management and faster decision-making [3].
Coordinated Vulnerability Disclosure (CVD)
The FDA requires manufacturers to establish a Coordinated Vulnerability Disclosure (CVD) policy as part of their cybersecurity plans [2][10]. A strong CVD policy includes public guidelines for reporting vulnerabilities, designated communication channels, clear triage procedures, and a framework for publicly disclosing vulnerabilities that pose risks to patient safety [10].
The FDA views CVD programs as a proactive measure to protect patient safety, not as a sign of poor security. In fact, manufacturers with well-structured CVD programs may receive favorable consideration in enforcement decisions [10]. Proper documentation of reports, analyses, and responses is essential to demonstrate compliance during audits [3][10]. With these processes in place, manufacturers can address vulnerabilities efficiently, deploying security patches and updates as needed.
Security Patches and Updates
Manufacturers are expected to respond to vulnerabilities within a "reasonable time", guided by risk assessments that consider factors like CVSS scores and clinical impact. For high-risk issues - such as remotely exploitable flaws that could lead to incorrect therapy or loss of monitoring - swift action is critical. These must be addressed on an expedited timeline with thorough documentation to justify the response [2][3][10].
Healthcare organizations also need to align their internal change management processes to ensure patches are deployed quickly in live environments [3]. When immediate patching isn’t feasible due to clinical workflow constraints, both manufacturers and healthcare providers should implement compensating controls, such as network segmentation, access restrictions, or enhanced monitoring, to temporarily mitigate risks while fulfilling FDA surveillance requirements [3][10].
The FDA encourages manufacturers to design devices with updatability in mind, incorporating features like secure bootloaders, cryptographic signing, and rollback protections. These measures ensure that updates can be applied safely without increasing patient risk [10]. To meet FDA postmarket audit standards, manufacturers should maintain detailed, audit-ready records, including:
- The postmarket cybersecurity risk management plan.
- Logs of threat intelligence feeds and monitoring tools.
- Documentation of CVD policies and workflows.
- Risk assessments and remediation decisions for all significant vulnerabilities.
- Patch and update histories, with validation evidence.
- Communication records with healthcare providers and the FDA regarding major incidents or vulnerabilities affecting safety [3][5][10].
How to Prepare for FDA Postmarket Audits
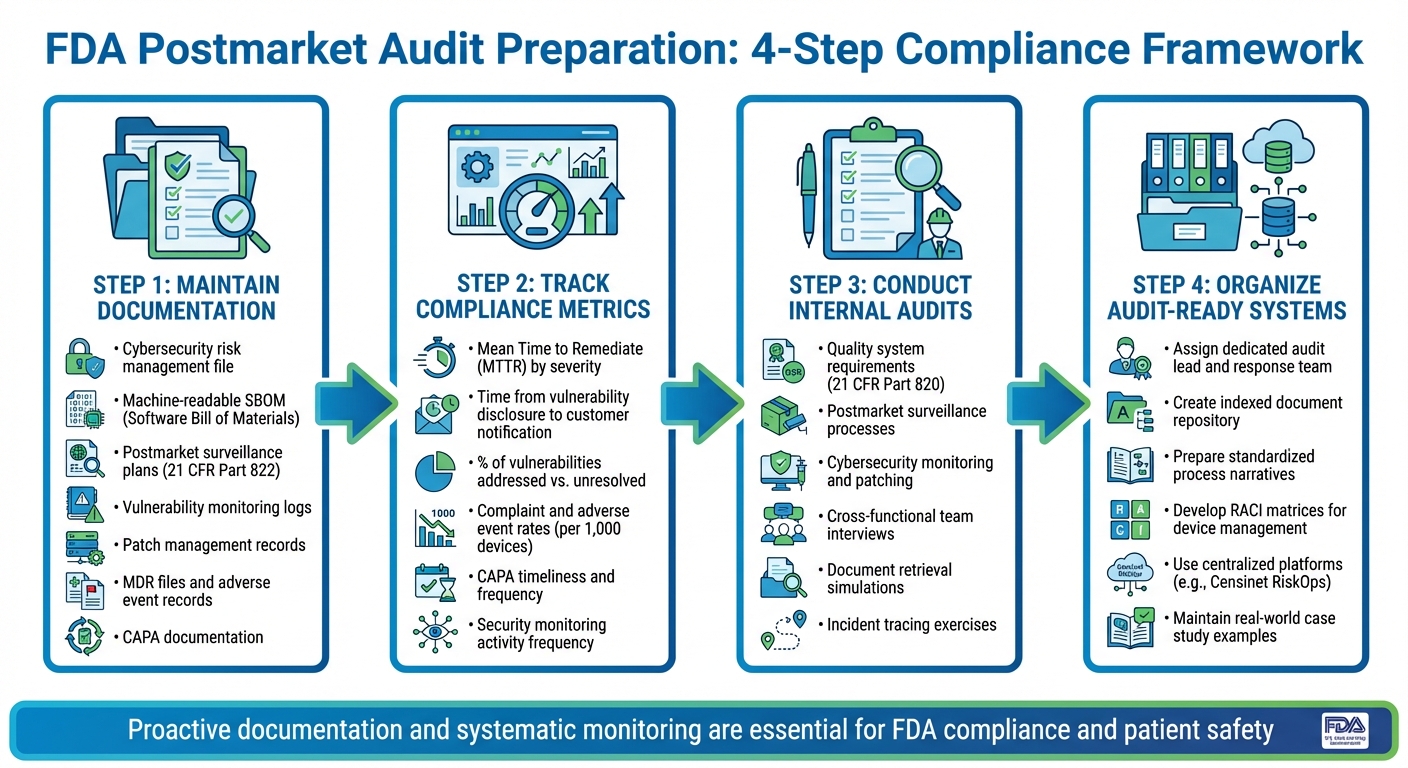
FDA Postmarket Audit Preparation: 4-Step Compliance Framework for IoT Medical Devices
Required Documentation for Audits
To be ready for FDA postmarket audits, manufacturers need to maintain a comprehensive cybersecurity risk management file. This file should cover risk identification, evaluations, and controls from the design phase through ongoing postmarket monitoring. It must also include an up-to-date, device- and version-specific machine-readable SBOM (Software Bill of Materials) listing all components and relevant CVE identifiers.
Your documentation should also feature postmarket surveillance plans and procedures that outline how safety and performance data from the field are collected, analyzed, and escalated in line with 21 CFR Part 822. Include detailed vulnerability monitoring procedures and logs specifying the sources (like security mailing lists, the National Vulnerability Database, vendor advisories, ISACs, and MITRE resources), how often monitoring is conducted, triage criteria, and clearly defined roles. Additionally, maintain patch and update management records that include release notes, risk justifications, validation evidence, deployment plans, and customer communications. Don’t forget to keep complaint files, adverse event records, Medical Device Reporting (MDR) files, and documentation for change control and CAPA (Corrective and Preventive Actions).
Quantify these processes with clear metrics and evidence to back up your compliance efforts.
Metrics and Evidence to Demonstrate Compliance
Auditors will expect measurable proof that your postmarket processes are working effectively. Start by calculating the Mean Time to Remediate (MTTR) cybersecurity vulnerabilities, broken down by severity. Track how long it takes from the initial disclosure of a vulnerability to notifying customers. Measure the percentage of identified vulnerabilities that have been addressed - whether through patches, compensating controls, or documented risk acceptance - compared to those still unresolved.
It’s also important to monitor trends in complaint and adverse event rates (such as incidents per 1,000 devices or device-days) to demonstrate the effectiveness of your surveillance and corrective actions. Keep records of the number and timeliness of CAPAs related to cybersecurity or device failures. Document the frequency of log reviews, security monitoring activities, and penetration tests.
Qualitative evidence can complement the numbers. Prepare case studies of incidents you’ve handled, document risk–benefit analyses for complex updates, and compile cross-functional reviews involving teams from clinical, regulatory, security, and quality departments. If your organization uses centralized platforms like Censinet RiskOps, you can leverage structured data to show how you monitor and respond to incidents collaboratively.
With these metrics and evidence in hand, you can conduct internal audits to simulate FDA inspections.
Internal Audits and Mock Inspections
Conduct mock FDA inspections based on risk to ensure your organization is meeting postmarket requirements. Internal audits should cover FDA quality system requirements, including postmarket surveillance, complaint handling, MDR, CAPA, and design changes. They should also evaluate how well postmarket cybersecurity processes - such as monitoring, vulnerability disclosure, patching, risk assessments, and communications - are being implemented.
Simulate FDA-style interviews with cross-functional teams, including regulatory, quality, cybersecurity, product engineering, and technical support staff. Practice responding to common document requests, such as risk management files, SBOMs, surveillance plans, CAPAs, incident records, patch documentation, and relevant SOPs. Trace actual incidents or vulnerabilities from detection through investigation, risk evaluation, corrective action, and communication. These exercises help reinforce the continuous vigilance needed for effective postmarket cybersecurity management.
Use checklists aligned with FDA guidance to refine your procedures and training, and document lessons learned from each mock inspection. Assign a single audit lead and a dedicated response team to handle document retrieval, coordinate with subject-matter experts, and communicate with the FDA. Organize an audit-ready index of postmarket and cybersecurity documents by topic and regulatory reference, and prepare standardized narratives that explain your processes - for example, how you handle new cybersecurity vulnerabilities - using de-identified real-world examples. Platforms like Censinet can streamline the process for healthcare organizations and vendors, helping them provide consistent and comprehensive evidence of their monitoring, incident response, and remediation efforts.
sbb-itb-535baee
Healthcare Organization Responsibilities in Postmarket Compliance
Shared Responsibilities Between Manufacturers and Healthcare Organizations
When it comes to postmarket compliance, healthcare organizations and manufacturers need to work hand-in-hand. Manufacturers typically handle cybersecurity research and regulatory reporting, but healthcare organizations take charge of securing device deployment and day-to-day operations. This partnership ensures a more comprehensive approach to compliance.[2][10]
Healthcare organizations have a range of critical tasks. They must establish and maintain access controls, use network segmentation, and implement logging and monitoring to spot unusual device behavior. Applying vendor-recommended security patches, documenting device configurations (and any deviations), and training staff on secure device usage and incident reporting are equally essential.[10] By capturing real-world performance data, reporting cyber incidents, and identifying adverse events, healthcare organizations play a key role in supporting manufacturers’ obligations to meet FDA reporting and remediation requirements.[5][6]
These responsibilities should be clearly outlined in contracts, business associate agreements (BAAs), service-level agreements (SLAs), and security addenda. Defining roles for tasks like vulnerability monitoring, patching, incident response, and reporting ensures accountability. Using a RACI (Responsible, Accountable, Consulted, Informed) matrix for each major device or vendor is a practical way to align with FDA postmarket guidance. This matrix should be reviewed regularly, especially during contract renewals, major software updates, or after significant incidents.[10]
Best Practices for IoT Device Management
Effective management of IoT devices starts with a detailed, up-to-date inventory of all clinical devices.[3] This inventory should include details like device type, manufacturer, model, serial number, software/firmware versions, operating system, network identifiers (IP and MAC addresses), physical location, clinical owner, risk classification, data classification (e.g., whether it handles PHI), key software components (SBOM), and the current patch level.[2][3] Without this information, it’s nearly impossible to quickly identify devices affected by new vulnerabilities or prioritize fixes based on clinical risk.
Vulnerability management for IoT devices needs to be risk-focused, device-specific, and integrated with clinical engineering and change management processes.[3][10] Organizations should monitor manufacturer bulletins and credible threat feeds, correlate new vulnerabilities (CVEs) with their device inventory, and assess the potential clinical impact. For instance, vulnerabilities in life-sustaining devices or those critical to patient safety demand immediate attention. When patching isn’t feasible due to FDA-cleared settings, vendor support limitations, or clinical uptime needs, organizations must document and implement alternative measures like network isolation, disabling unused services, or stricter access controls.[10]
Incident response for IoT devices should combine cybersecurity expertise, clinical risk assessment, and manufacturer collaboration at every stage.[6][10] This process includes detection through alerts and monitoring, rapid triage to assess patient safety risks, containment strategies that maintain clinical operations, and thorough investigations using logs and network traces. Coordinating with manufacturers ensures alignment on indicators of compromise and mitigation strategies. Recovery efforts must restore device functionality safely, and all incidents should be documented with lessons learned. Pre-procurement security reviews, secure configuration baselines, network segmentation, and proper decommissioning at the end of a device’s life cycle are also crucial steps.[2][3][10]
Using Centralized Risk Management Platforms
Centralized platforms, such as Censinet RiskOps™, can streamline postmarket compliance by handling risk assessments, continuous monitoring, and documentation efficiently.[3] These platforms standardize security questionnaires for device vendors, automate the ingestion and correlation of vulnerability and incident data, and provide tools to manage remediation workflows, assign responsibilities, and make informed risk acceptance decisions.[3]
For IoT and medical devices, platforms that integrate with CMMS/IT asset inventories, offer device-specific risk scoring, and provide benchmarking tools can help healthcare organizations allocate their resources more effectively. They also demonstrate ongoing progress in meeting FDA expectations. Centralizing risk data improves internal audits, speeds up vulnerability management, and enhances overall compliance efforts.
Terry Grogan, CISO at Tower Health, shared: "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."[1]
James Case, VP & CISO at Baptist Health, remarked: "Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with."[1]
Brian Sterud, CIO at Faith Regional Health, highlighted: "Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."[1]
Dashboards provided by these platforms give governance teams clear visibility into high-risk devices, overdue patches, and unresolved issues. They also house centralized evidence repositories, which support audits, accreditation surveys, and board-level reporting on cyber risks.[3]
Conclusion
Key Takeaways for Manufacturers and Healthcare Organizations
The FDA requires strict postmarket surveillance for connected medical devices, enforcing these rules through tools like MDR reporting, Section 522 surveillance orders, and quality system inspections[5][7]. Manufacturers are tasked with actively monitoring and addressing cybersecurity vulnerabilities using clearly defined Coordinated Vulnerability Disclosure (CVD) processes and remediation timelines[2].
Both manufacturers and healthcare organizations share the responsibility of managing risks after devices are deployed. Manufacturers handle surveillance plans, track vulnerabilities, and submit regulatory reports. Meanwhile, healthcare organizations must maintain accurate device inventories, apply patches securely, and report incidents as they occur. Keeping thorough documentation - including records of surveillance activities, complaints, cybersecurity events, corrective actions, and updates - is essential to pass FDA inspections successfully[5][7][11]. Organizations that integrate cybersecurity and postmarket monitoring into their quality systems and device lifecycles are better positioned to reduce recalls, protect patients, and navigate regulatory processes more efficiently[4][8][9].
Using Technology to Support Compliance
Technology plays a key role in managing these shared responsibilities effectively. Centralized platforms like Censinet RiskOps™ simplify third-party and enterprise risk management by standardizing security questionnaires, automating the correlation of vulnerability data, and streamlining remediation workflows[1].
For example, when the FDA issues a safety or cybersecurity alert, tools like Censinet RiskOps™ allow organizations to quickly identify which device models, locations, and versions are affected, enabling swift, risk-based responses[5][8][11]. These platforms integrate continuous risk management into the device lifecycle, making it a foundational practice. Censinet’s collaborative risk network connects healthcare organizations with over 50,000 vendors and products, fostering seamless data sharing to enhance postmarket surveillance and incident response efforts. Notably, Censinet was named one of TIME Magazine's World's Top HealthTech Companies of 2025, underscoring its impact on healthcare cybersecurity and risk management[1].
Matt Christensen, Sr. Director GRC at Intermountain Health, remarked: "Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare."[1]
FAQs
What must healthcare organizations do to ensure IoT devices stay compliant with FDA regulations after market release?
Healthcare organizations must stay vigilant in monitoring the performance of IoT devices, ensuring they meet safety and compliance standards. This involves promptly addressing any safety or performance issues, regularly updating risk assessments, and keeping detailed records to show adherence to FDA postmarket surveillance guidelines.
To make this process more manageable, organizations can leverage risk management platforms. These tools can help simplify compliance tasks, cut down on administrative work, and strengthen the security of IoT devices, making it easier to stay on top of regulatory requirements.
What does the FDA mean by 'cyber device,' and how does it affect manufacturers' cybersecurity strategies?
The FDA describes a "cyber device" as any medical device equipped with software, connectivity, or other elements that could expose it to cybersecurity risks. This means manufacturers must integrate cybersecurity measures at every stage of the device's lifecycle - from initial design to ongoing postmarket monitoring.
To align with FDA requirements, manufacturers are expected to engage in continuous monitoring, keep thorough records, and take proactive steps to manage potential risks. These efforts are crucial for safeguarding device functionality, protecting patient information, and ensuring compliance during postmarket audits.
What is the importance of a Software Bill of Materials (SBOM) in managing cybersecurity for IoT devices after they hit the market?
A Software Bill of Materials (SBOM) plays a key role in strengthening the cybersecurity of IoT devices after they hit the market. Essentially, it’s a detailed inventory of all the software components within a device, which makes spotting and addressing vulnerabilities much more manageable.
With an SBOM in place, organizations can stay aligned with regulatory standards, react swiftly to new threats, and safeguard the security of devices throughout their lifespan. This forward-thinking strategy not only helps protect sensitive data, like patient records, but also ensures devices operate securely and reliably.


