IoT Medical Devices and Vendor Risk: Connected Healthcare Security Challenges
Post Summary
The rise of IoT medical devices is reshaping healthcare, offering benefits like continuous patient monitoring, real-time data, and improved workflows. However, these advancements come with serious cybersecurity risks, especially when third-party vendors are involved. Many devices lack proper security, rely on outdated firmware, and use weak authentication, making them vulnerable to attacks.
Key challenges include:
- Vendor Risks: Remote access by vendors often bypasses security protocols, exposing healthcare networks.
- Outdated Systems: 14% of connected devices run on unsupported systems, with many lacking timely security patches.
- Data Exposure: Over 1 million IoT medical devices leaked sensitive patient data in 2025 due to missing encryption.
- Default Configurations: Weak default settings and passwords make devices easy targets for attackers.
To mitigate these risks:
- Vendor Assessments: Evaluate vendor security practices, ensure compliance with HIPAA and FDA guidelines, and demand regular updates.
- Contract Security: Include strict cybersecurity requirements in vendor agreements.
- Continuous Monitoring: Use tools for real-time device tracking, network segmentation, and threat detection.
- Device-Level Controls: Enforce encryption, strong authentication, and regular firmware updates.
Platforms like Censinet RiskOps™ streamline vendor risk management, automating assessments and improving oversight. By combining technical controls with robust vendor management, healthcare organizations can better protect patient data and maintain device reliability.
IoT Medical Device Security Statistics and Vulnerabilities in Healthcare 2025
Common Cybersecurity Challenges from Vendor-Supplied IoT Devices
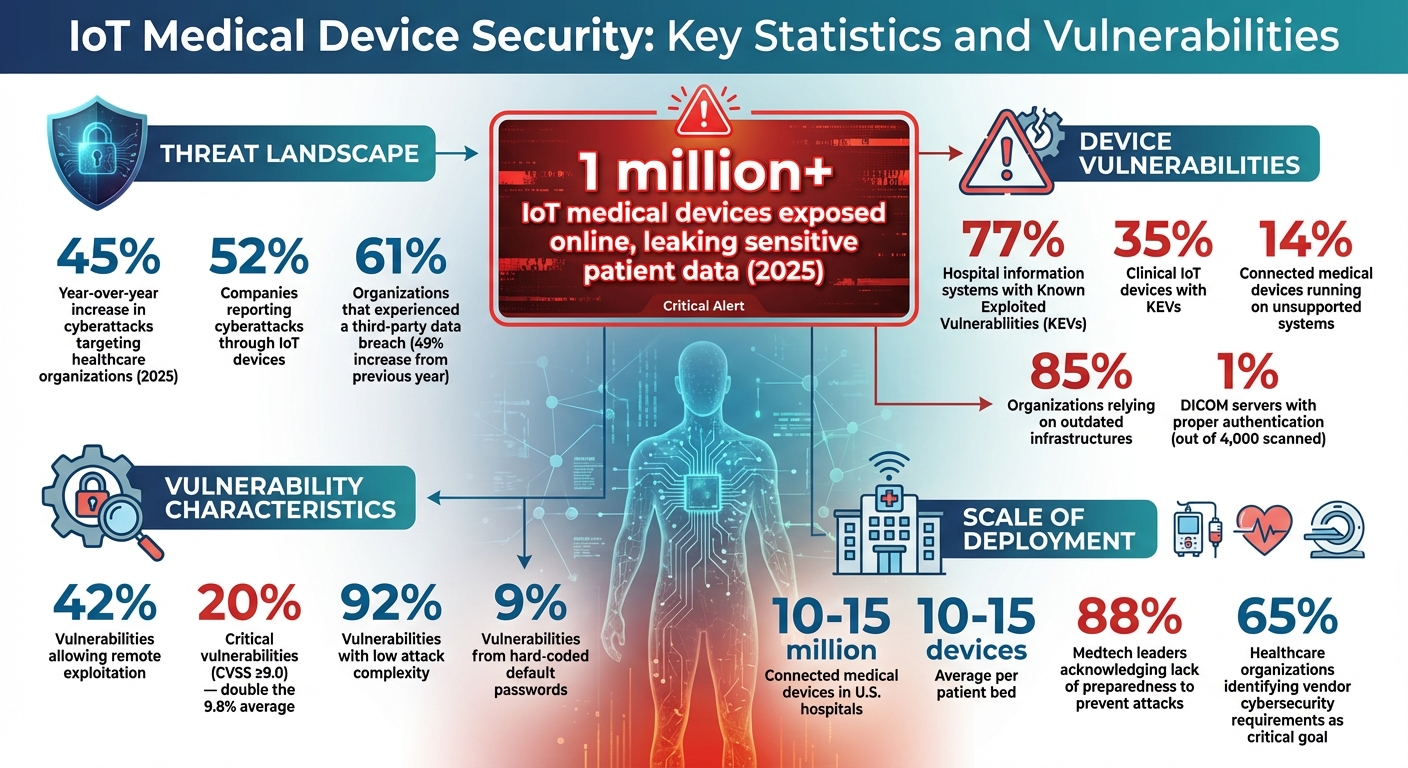
Vendor-supplied IoT devices bring their own set of cybersecurity headaches, often compounding the risks already present in third-party vendor management. These devices frequently come with security flaws that attackers are quick to exploit. For instance, a study by Claroty revealed that 77% of hospital information systems and 35% of clinical IoT devices had Known Exploited Vulnerabilities (KEVs)[4]. Even more concerning, 14% of connected medical devices run on unsupported systems, and 85% of organizations rely on outdated infrastructures[4][6]. The fallout is alarming: Check Point Research reported a 45% year-over-year increase in cyberattacks targeting healthcare organizations as of 2025[4]. These vulnerabilities pose serious threats to both data privacy and system reliability.
Missing Encryption and Insecure Data Transmission
When IoT devices fail to encrypt transmitted data, they leave sensitive patient information exposed to interception. This lack of encryption compromises protected health information (PHI) during communication between devices, servers, and clinical systems. Attackers can easily intercept unencrypted data streams, which may include medical images, lab results, treatment plans, and vital signs. In 2025 alone, over 1 million IoT medical devices were found exposed online, leaking highly sensitive patient data[3]. Shockingly, a study revealed that only 1% of 4,000 scanned DICOM servers had proper authentication[4], leaving medical imaging systems vulnerable to unauthorized access. Without encrypted protocols, every data transfer becomes a ticking time bomb for potential breaches. These risks are further magnified when devices operate on outdated systems, compounding the threats to patient data.
Outdated Firmware and Unpatched Vulnerabilities
Outdated firmware is a goldmine for attackers, offering a direct path to exploit known vulnerabilities. Many vendors fail to release timely security patches, leaving healthcare organizations stuck with devices that are essentially open doors for cyberattacks. A single unpatched vulnerability in one IoT device can ripple across an entire hospital network, leading to data breaches, operational disruptions, and even physical harm to patients[2][5][4]. Attackers can deploy ransomware, manipulate device settings - like altering infusion pump dosages - or gain unauthorized control, putting lives at risk. The FDA has repeatedly flagged such risks.
- On January 30, 2025, the FDA warned about vulnerabilities in Contec CMS8000 and Epsimed MN-120 patient monitors, which could allow unauthorized access and control[8].
- On September 20, 2022, the FDA issued an alert for the Medtronic MiniMed 600 Series Insulin Pump System, where attackers could manipulate insulin doses[8].
- On December 22, 2021, vulnerabilities in the Fresenius Kabi Agilia Connect Infusion System were highlighted, as attackers could exploit these flaws to access sensitive information[8].
Each of these cases underscores the risks tied to unpatched devices, which attackers can exploit with relative ease.
Default Configurations and Unsecured Remote Access
Default settings and weak authentication mechanisms are another major weak spot in vendor-supplied IoT devices. Hard-coded default passwords - responsible for 9% of identified vulnerabilities - are a glaring issue. These weaknesses make it easy for attackers to break in, especially since 42% of vulnerabilities allow remote exploitation, and 20% are classified as critical (CVSS ≥9.0) - double the average critical vulnerability rate of 9.8%[2][9]. Even worse, 92% of these vulnerabilities have low attack complexity[9], meaning cybercriminals don’t need advanced skills to exploit them. Remote access features, designed for vendor maintenance, often become entry points for attackers when not properly secured. Once inside, hackers can disrupt services, steal patient data, or even manipulate device functions, directly jeopardizing patient safety.
How to Assess Vendor Risks for Healthcare IoT Devices
With 52% of companies reporting cyberattacks through IoT devices[13] and 88% of medtech leaders acknowledging their companies' lack of preparedness to prevent such attacks[14], healthcare organizations must take vendor evaluations seriously. The numbers are staggering - 10–15 million connected medical devices are currently in use across U.S. hospitals, with an average of 10–15 devices per patient bed[14]. This isn't just a compliance exercise; it's about safeguarding patient safety and maintaining the integrity of healthcare systems. Vendor risk assessments play a critical role in addressing vulnerabilities tied to outdated practices.
Reviewing Vendor Security Practices
A good starting point is to request detailed security documentation from vendors. This should include their protocols, system architecture, and the security measures built into their devices[12]. Make sure they comply with HIPAA, FDA cybersecurity guidelines, ISO/IEC 27400, and NIST standards[7][12][13]. Ask direct questions about key security features: Does the device support secure boot and hardware security? Are firmware updates both automatic and verified? Is data encrypted at rest and during transmission? What access controls are in place - such as multi-factor authentication (MFA), role-based access control (RBAC), and least privilege principles?[7][11][12][14]
It's also essential to dig into the vendor's track record. Review customer feedback, reported security incidents, and any third-party certifications like SOC 2 Type II or ISO 27001, which demonstrate strong security practices[12]. For example, in 2024, SmartSense earned SOC 2 Type II certification after a rigorous year-long review, implementing continuous monitoring and third-party audits to manage security risks proactively[12]. Transparency is key - ask for Software Bills of Materials (SBOMs) and clear documentation of how they handle vulnerabilities[7][2][11]. These steps set the foundation for holding vendors accountable through contractual agreements.
Including Security Requirements in Vendor Contracts
Vendor contracts should explicitly enforce security requirements. According to the 2025 Healthcare Cybersecurity Benchmarking Study, 65% of respondents identified "Vendor/Supplier Cybersecurity Requirements" as a critical goal[1], yet many organizations still fail to include specific mandates in their agreements. Contracts should demand compliance with federal cybersecurity guidelines and include provisions requiring vendors to:
- Adhere to specified security standards.
- Provide timely security updates and patches.
- Disclose any security incidents or breaches affecting their products or services[15].
The agreement should also require vendors to implement robust cybersecurity measures, such as encryption, access controls, and clear data retention policies for patient information[16]. Align these requirements with the FDA's draft cybersecurity guidance, which outlines key controls like authentication, authorization, cryptography, data integrity, event logging, and patchability[17]. Additionally, contracts should detail performance expectations, audit rights, breach notification protocols, corrective actions for non-compliance, and business continuity plans[15][19]. Regular monitoring is crucial to ensure vendors continue to meet these standards.
Ongoing Monitoring of Vendor Relationships
Continuous monitoring is essential to address evolving threats. Rather than relying on periodic compliance checks, healthcare organizations need ongoing, risk-based oversight[1]. Use tools like intrusion detection systems (IDS), network monitoring software, and IoT platforms with advanced analytics to identify unusual behavior, unauthorized access, or new vulnerabilities in real-time[2][1][15]. Integrate threat intelligence feeds to stay ahead of attacks targeting specific vendors or device types[1][7]. Maintain an up-to-date inventory of all IoT devices, including those managed by third-party vendors, with real-time visibility into device communications, vendor access, and data flows[2][1][18][19].
Hold vendors accountable through regular compliance attestations and periodic security audits[18][7][19]. Review their business continuity plans, including breach notification processes, testing outcomes, and strategies for handling personnel changes[19]. Stay informed by monitoring news for vendor-related incidents and encourage frontline staff to report any issues with IoT devices[19]. The 2024 Third-Party Risk Management Study found that 61% of organizations experienced a third-party data breach or cybersecurity incident, a 49% increase from the previous year[18]. These numbers underscore the importance of vigilance - it's not optional in today’s healthcare environment.
Managing Vendor Risks with Censinet RiskOps™
Keeping track of vendor risks across thousands of IoT devices can feel overwhelming, especially if you're still relying on outdated, manual processes. These methods not only slow down your ability to manage risks effectively but also struggle to keep up with the rapid growth of connected devices - while still safeguarding sensitive patient data. That’s where Censinet RiskOps™ steps in. This platform brings everything you need for vendor risk management into one place, specifically designed to meet the unique demands of the healthcare sector. It’s a streamlined, automated solution that transforms how risks are managed.
Automated Risk Assessments and Vendor Reviews
If you're still handling vendor assessments manually, you’re likely wasting valuable time. Censinet RiskOps™ changes the game by automating the entire process. It simplifies tasks like evaluating a vendor’s security posture, identifying vulnerabilities, and tracking remediation efforts. What used to take weeks can now be done in just days. Even better, this system allows healthcare organizations to scale their risk assessments without needing to expand their teams. Automated workflows ensure that critical findings are sent directly to the right people, minimizing the chance of vulnerabilities slipping through the cracks. This is especially crucial in U.S. hospitals, where managing the sheer number of connected medical devices is a monumental task that manual methods simply can’t handle.
Cybersecurity Benchmarking and Documentation Management
With Censinet RiskOps™, all your vendor-related documentation is stored in one secure, centralized location. This makes it easier to review evidence and track compliance. The platform also enables cybersecurity benchmarking, so healthcare organizations can compare their vendors’ security practices against industry standards and even their peers. From certifications and SBOMs to security policies and compliance records, everything is organized with version control and audit trails. This approach not only boosts visibility into vendor capabilities but also ensures that key cybersecurity standards are consistently met.
Using Censinet AITM to Speed Up Risk Reporting
To make risk management even faster, Censinet AITM integrates seamlessly with RiskOps™. This integration allows vendors to complete security questionnaires in seconds instead of weeks. Meanwhile, the AI system summarizes vendor evidence and documentation automatically. It captures crucial details, such as product integrations and fourth-party risk exposures, and generates risk summary reports based on all the data collected. Despite the automation, risk teams remain in control, using configurable rules and review processes to oversee the system’s work. By cutting down on administrative tasks, teams can focus their energy on addressing the vulnerabilities that pose real threats to patient safety. It’s a smarter, faster way to manage risks without losing sight of what matters most.
sbb-itb-535baee
Strengthening IoT Security with Network and Device Controls
Managing vendor risks is just one piece of the puzzle. Healthcare organizations must also adopt robust technical measures at both the network and device levels to shield IoT medical devices from cyber threats. When combined with vendor oversight, these measures create a strong security framework that protects patient data and ensures critical devices function without disruption. Below, we explore key technical controls that enhance IoT device security.
Network Segmentation and Traffic Monitoring
Keeping IoT devices on a separate network is one of the best ways to minimize risk. Network segmentation establishes dedicated zones - commonly referred to as VLANs - specifically for medical devices. This setup limits the potential damage from a breach, as attackers are prevented from moving freely across the network. For devices that can’t be patched, isolation is especially important [20]. Notably, the updated HIPAA Security Rule now includes network segmentation as a required technical safeguard in business associate agreements [10].
Taking segmentation a step further, micro-segmentation restricts device communication even more by controlling access based on specific application needs [7]. This granular control is a cornerstone of Zero Trust Architecture, which operates on the principle that no device is automatically trusted, and every access request is continuously validated [21]. A stark reminder of the stakes came in February 2024, when attackers exploited stolen credentials to access a remote portal, leading to the exposure of protected health information for at least 150 million individuals during the Change Healthcare breach [1]. This incident highlights the critical need for rigorous access control and constant monitoring.
Patch Management and Strong Authentication
Keeping device firmware updated and enforcing strong authentication practices are essential for securing IoT devices. Many medical devices come with default credentials that are rarely changed, making them easy targets for attackers [15]. Weak passwords and the lack of multi-factor authentication (MFA) leave devices wide open to unauthorized access.
To counter this, healthcare organizations should enforce strict password policies and mandate MFA for all device access. Regularly reviewing device access logs can also help identify unusual activity early, providing an opportunity to respond before significant damage occurs [15].
Data Encryption and PHI Protection
Encryption is a vital safeguard for protecting patient health information (PHI), whether it’s stored on devices or being transmitted. Without proper encryption, sensitive data can be easily accessed by unauthorized parties. In a 2025 breach, over 1 million IoT medical devices were found online with unencrypted directories, resulting in the exposure of highly sensitive patient data [3]. This incident underscores why encryption must be a non-negotiable security measure.
Healthcare organizations should implement end-to-end encryption using trusted algorithms and establish secure processes for managing and rotating encryption keys [15]. Weak encryption in communication protocols can lead to Man-in-the-Middle attacks, which could cause misdiagnoses or delays in treatment [4]. To address these risks, the U.S. government enacted the "Ensuring Cybersecurity of Medical Devices" act on December 29, 2022. This legislation empowers the FDA to enforce cybersecurity standards for connected medical devices, including requirements for encryption and ongoing vulnerability management throughout a device’s lifecycle [21].
Conclusion
Protecting IoT medical devices in the world of connected healthcare calls for a major shift in how vendor relationships are managed. Instead of relying on sporadic compliance checks, healthcare organizations need to adopt continuous, risk-based monitoring across their entire third-party ecosystem. Why? Because attackers often exploit vulnerabilities in devices that prioritize functionality over security, taking advantage of third-party access to break through defenses[1]. This shift lays the groundwork for a solid, multi-layered security strategy.
At its core, IoMT (Internet of Medical Things) security involves safeguarding both the devices and the sensitive data they generate. This means integrating device protection into a broader cybersecurity framework. It’s not just about securing the devices themselves but also addressing vendor-supplied vulnerabilities at every stage - from the initial vendor selection process to ongoing monitoring and relationship management[1][15].
Healthcare organizations also need dynamic tools to keep up with the ever-changing threat landscape. For instance, the Censinet RiskOps™ platform provides a powerful, centralized solution. It automates vendor risk assessments, streamlines cybersecurity documentation, and speeds up risk reporting with the help of Censinet AI™. When paired with technical measures like network segmentation, these tools enable organizations to build a robust security framework that not only protects patient data but also ensures critical medical devices function safely.
On the flip side, manufacturers play a crucial role too. They must embrace security-by-design principles, implement strong controls, and address vulnerabilities quickly. By working together - healthcare organizations, vendors, and manufacturers - all parties can better manage the intricate risks of connected healthcare. With the right tools, processes, and collaboration, safeguarding patient safety and ensuring uninterrupted care delivery becomes a shared, achievable goal.
FAQs
What steps can healthcare organizations take to secure IoT medical devices and address vendor-related risks?
Healthcare organizations can strengthen the security of IoT medical devices by prioritizing vendor risk management and adopting effective cybersecurity practices. A good starting point is to maintain a detailed, up-to-date inventory of all connected devices and their respective vendors. Regular evaluations of vendor security protocols are essential, ensuring they comply with safety and regulatory standards.
To bolster device security, organizations should implement strong authentication and encryption protocols. Network segmentation is another crucial step - it helps isolate critical devices, reducing the chances of widespread breaches. When procuring devices, focus on a security-first approach to ensure potential risks are addressed from the outset.
Other key measures include scheduling timely firmware updates, deploying real-time threat detection systems, and conducting continuous monitoring to identify vulnerabilities. By combining these efforts, healthcare providers can better protect their IoT devices and create a safer environment for patient care.
What are the most common security risks in IoT medical devices, and how can they be addressed?
IoT medical devices come with a range of security challenges, including weak or hardcoded passwords, outdated firmware, and insecure network protocols. On top of that, issues like insufficient data encryption, default factory settings, and poor device management practices make these devices even more vulnerable. The lack of secure update mechanisms further amplifies these risks.
To tackle these challenges, healthcare organizations need to take proactive measures. This includes implementing strong authentication methods and ensuring regular firmware updates to address vulnerabilities. Using encryption to safeguard data during both transfer and storage is another critical step. Additional strategies, such as network segmentation, secure device configurations, and continuous monitoring, can help detect and respond to potential threats effectively. Following established frameworks like HIPAA and NIST provides a solid foundation for creating a secure IoT environment in healthcare.
Why is continuous monitoring essential for securing IoT devices in healthcare?
Continuous monitoring plays a key role in keeping IoT devices secure in healthcare settings. It provides real-time insights into possible vulnerabilities, unusual communication behaviors, and new threats. This constant vigilance helps healthcare organizations spot and resolve security issues quickly, reducing the risk of data breaches or threats to patient safety.
By keeping a close watch on device activity, healthcare providers can stay one step ahead of cyber risks, ensure compliance with regulatory requirements, and safeguard sensitive patient data. In an industry where even small security gaps can have serious repercussions for patients and providers alike, this level of oversight is not just beneficial - it’s essential.


