ISO 27001 and HIPAA: Control Mapping Guide
Post Summary
ISO 27001 is an international standard for information security management systems (ISMS), while HIPAA is a U.S. regulation for protecting ePHI. Mapping ISO 27001 to HIPAA helps organizations align security controls and streamline compliance.
A crosswalk matrix maps HIPAA safeguards to ISO 27001 controls, identifying overlaps and ensuring compliance with both frameworks.
Benefits include reduced duplication of efforts, streamlined audits, enhanced ePHI protection, and a unified approach to compliance.
For example, HIPAA 164.308(a)(4) (access control) maps to ISO 27001 Annex A.9.2 (user access management).
By creating a crosswalk matrix, conducting gap analyses, and aligning security policies with both frameworks.
Tools like compliance management platforms and automated crosswalk generators can simplify the mapping process and evidence management.
ISO 27001 and HIPAA share overlapping goals but serve different purposes. ISO 27001 is an international standard for managing information security, while HIPAA is a U.S. regulation focused on protecting health information (PHI/ePHI). For healthcare organizations, aligning these frameworks can streamline compliance and improve security practices.
Here’s the key takeaway: ISO 27001 provides a structured approach to managing security risks, while HIPAA sets specific legal requirements for safeguarding health data. Mapping ISO 27001 controls to HIPAA safeguards helps healthcare providers manage both frameworks efficiently, reducing duplicate efforts.
Quick Highlights:
- ISO 27001: Risk-based, global standard for an Information Security Management System (ISMS).
- HIPAA: U.S. law with mandatory safeguards for PHI, enforced by HHS.
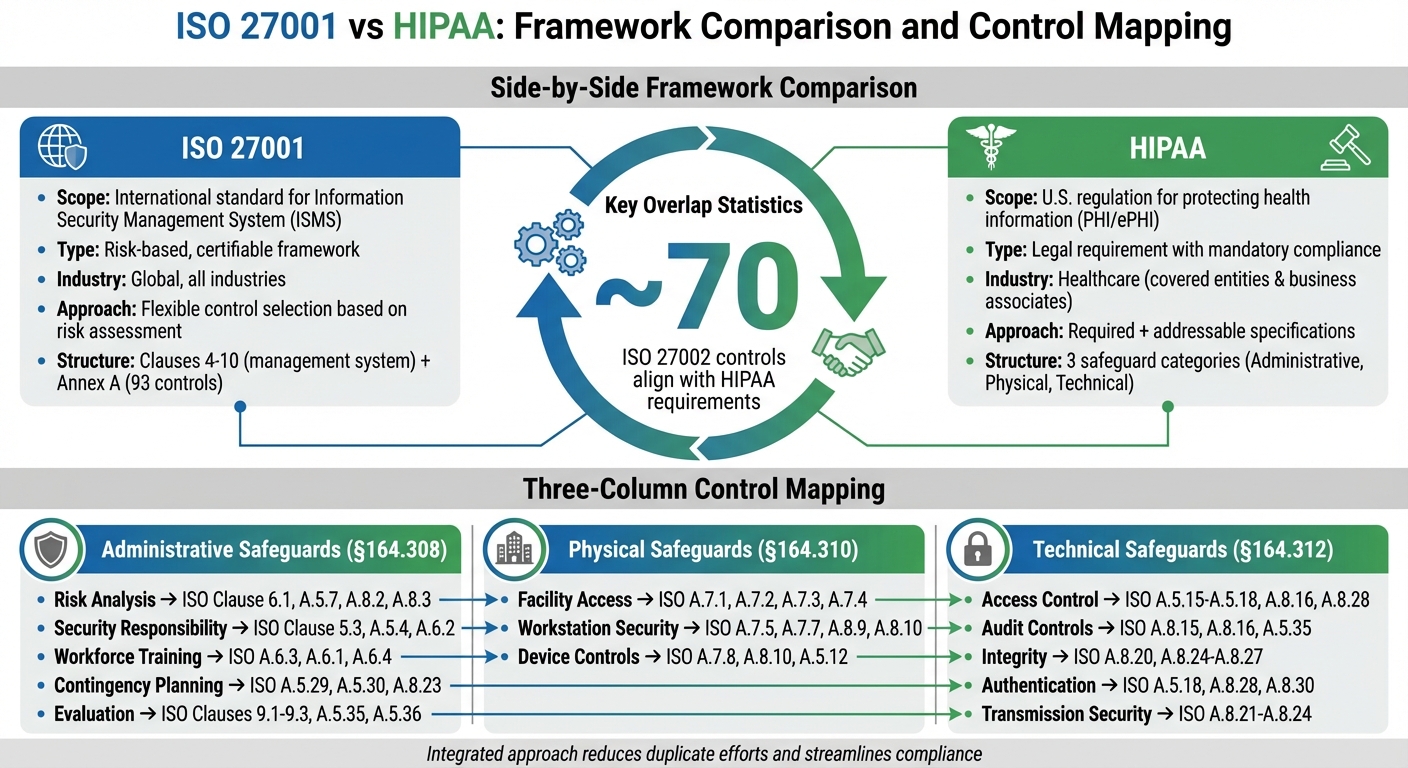
- Overlap: ~70 ISO 27002 controls align with HIPAA, covering areas like risk management, access controls, and incident response.
- Approach: Use a crosswalk matrix to link HIPAA rules to ISO 27001 controls, creating a unified compliance program.
ISO 27001 vs HIPAA Framework Comparison and Control Mapping
Key Differences and Similarities Between ISO 27001 and HIPAA
Structure Comparison
ISO 27001 and HIPAA take different approaches to organizing their requirements. ISO 27001 divides its framework into two main sections. Clauses 4–10 focus on the management system itself - covering aspects like context, leadership, planning, support, operations, performance evaluation, and improvement. Annex A, on the other hand, offers a catalog of 93 controls grouped into themes: organizational, people, physical, and technological. Think of the clauses as a roadmap for managing your security program, while Annex A serves as a menu of controls chosen based on your risk assessment.
HIPAA's Security Rule follows a different structure. It categorizes its requirements into three safeguard types: administrative (45 CFR 164.308), physical (45 CFR 164.310), and technical (45 CFR 164.312). It also includes organizational requirements, policies, and documentation. Each safeguard comes with specific implementation instructions, some labeled as "required" and others as "addressable." Unlike ISO 27001, HIPAA zeroes in on protecting electronic protected health information (ePHI) rather than establishing a broader management system.
Interestingly, studies reveal a significant alignment between ISO 27001/27002 and HIPAA requirements. However, their structural differences highlight contrasting compliance philosophies, which we’ll explore next.
Requirement Types
The differences between ISO 27001 and HIPAA extend beyond structure to how they approach control implementation. ISO 27001 adopts a risk-based, flexible model. You choose controls from Annex A based on your organization's specific risk assessment and document these choices in a Statement of Applicability. Controls are not mandatory - you decide which ones apply and justify your decisions.
HIPAA, by contrast, sets a legal baseline with minimum requirements. "Required" specifications must be implemented, while "addressable" specifications allow some flexibility. However, "addressable" doesn’t mean optional. For instance, if encryption is listed as addressable and you choose not to implement it, you must provide documented justification and compensating controls.
ISO 27001 is designed for certifiable, risk-based information security management across industries. HIPAA, on the other hand, focuses on regulatory compliance and legal protection of health information, with penalties for non-compliance. HIPAA defines what outcomes must be achieved but leaves the "how" open-ended. ISO 27001 often provides the operational tools to meet those outcomes, but its broader scope means healthcare-specific nuances may require additional attention.
Healthcare-Specific Considerations
When it comes to healthcare, both frameworks address unique challenges, but they do so in distinct ways. Medical devices, clinical applications, and ePHI workflows introduce vulnerabilities that general security frameworks may overlook. As Matt Christensen, Sr. Director GRC at Intermountain Health, explains:
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare."
HIPAA is explicitly designed around ePHI and the ecosystem of covered entities and business associates. ISO 27001, while not specifically mentioning ePHI, can be scoped to include it. Both require organizations to manage vendor and third-party risks, but HIPAA’s rules for business associate agreements and breach notifications are more detailed than ISO 27001's supplier relationship controls.
Common HIPAA violations - such as failures in risk analysis, access controls, and audit logging - are areas ISO 27001 systematically addresses through its risk management process and Annex A controls. This overlap makes ISO 27001 a practical operational framework for achieving HIPAA’s objectives. However, healthcare organizations must still layer in HIPAA-specific legal requirements that ISO 27001 does not fully address.
Mapping ISO 27001 Controls to HIPAA Requirements
To align ISO 27001 controls with HIPAA requirements, start by using HIPAA's Security Rule citations (45 C.F.R. §164.306–316) as the framework. Then, identify the corresponding ISO 27001 clauses and Annex A controls. A crosswalk matrix can help organize this information, including the HIPAA citation, requirement text, relevant ISO 27001 clauses and Annex A controls, and the safeguard category (administrative, physical, or technical) [2].
Mapping Administrative Safeguards
HIPAA's administrative safeguards (§164.308) are the backbone of its security framework, closely aligning with ISO 27001's governance and risk management principles. For example:
- Risk Analysis and Risk Management (§164.308(a)(1)) correspond to ISO 27001 Clause 6.1 (actions to address risks and opportunities) and Annex A controls A.5.7 (threat intelligence), A.5.9 (asset inventory), A.8.2 (risk assessment), and A.8.3 (risk treatment) [2][8]. You can use your ISO 27001 risk assessment to meet HIPAA's requirements for risk analysis.
- Assigned Security Responsibility (§164.308(a)(2)) aligns with ISO 27001 Clause 5.3 (organizational roles and responsibilities) and Annex A controls A.5.4 (management responsibilities) and A.6.2 (segregation of duties) [4][8]. Document the designated security official role within your ISO 27001 ISMS to avoid duplicating efforts.
- Workforce Security and Training (§164.308(a)(3) and (a)(5)) map to ISO 27001 Annex A controls A.6.3 (security awareness and training), A.6.1 (screening), A.6.4 (disciplinary processes), and A.5.18 (access rights) [4][8]. By tailoring your ISO 27001 training program to include ePHI handling and policy enforcement, you can meet HIPAA's workforce training requirements.
- Contingency Planning (§164.308(a)(7)) maps to ISO 27001 Annex A controls A.5.29 (security during disruptions), A.5.30 (ICT continuity readiness), and A.8.23 (cloud security) [2][8].
- HIPAA's Evaluation requirement (§164.308(a)(8)) corresponds to ISO 27001 Clauses 9.1–9.3 (monitoring, internal audits, and management reviews) and Annex A controls A.5.35 (independent reviews) and A.5.36 (policy compliance) [2][8]. Your ISO 27001 internal audit program can double as HIPAA's periodic evaluations.
Next, align physical safeguards to further integrate compliance efforts.
Mapping Physical Safeguards
HIPAA's physical safeguards (§164.310) focus on protecting the physical environments where ePHI is stored or accessed. Here's how they map to ISO 27001:
- Facility Access Controls (§164.310(a)) align with ISO 27001 Annex A controls A.7.1 (physical security perimeters), A.7.2 (entry controls), A.7.3 (securing offices and facilities), and A.7.4 (physical monitoring) [2][8]. Ensure measures like locked server rooms, secure cable routing, and perimeter protections are documented to align with both frameworks [7][2].
- Workstation Use and Security (§164.310(b) and (c)) correspond to Annex A controls A.7.5 (equipment protection), A.7.7 (secure disposal), A.8.9 (cryptographic controls), and A.8.10 (data deletion) [2][8]. For clinical areas, document safeguards like workstation placement, secure storage for portable devices, and measures to prevent unauthorized access to ePHI [7].
- Device and Media Controls (§164.310(d)) map to Annex A controls A.7.8 (unattended equipment), A.8.10 (data deletion), and A.5.12 (media classification) [2][8]. For third-party hosting, confirm that providers' physical controls align with ISO 27001 and HIPAA obligations, documenting any inherited controls or mitigating measures, such as SOC 2 or ISO certifications [1][2].
Finally, align technical safeguards to complete the compliance mapping.
Mapping Technical Safeguards
HIPAA's technical safeguards (§164.312) focus on protecting ePHI through technology. These align with ISO 27001 as follows:
- Access Control (§164.312(a)) maps to Annex A controls A.5.15–A.5.18 (access control policies, identity management, access restrictions, and rights management), A.8.16 (privileged access), and A.8.28 (secure authentication) [2][8]. A robust ISO 27001 access control framework can meet HIPAA's requirements if scoped to ePHI systems.
- Audit Controls (§164.312(b)) align with Annex A controls A.8.15 (logging), A.8.16 (monitoring), and A.5.35 (independent reviews) [2][8].
- Integrity (§164.312(c)) corresponds to Annex A controls A.8.20 (log protection), A.8.24 (cryptography), A.8.25 (secure development lifecycle), A.8.26 (application security), and A.8.27 (system architecture) [2][8]. Ensure logging captures access to ePHI, modifications, and security events, with logs protected and reviewed regularly.
- Person or Entity Authentication (§164.312(d)) maps to Annex A controls A.5.18 (access rights), A.8.28 (authentication), and A.8.30 (cryptography) [2][8].
- Transmission Security (§164.312(e)) corresponds to Annex A controls A.8.21 (network security), A.8.22 (network segregation), A.8.24 (cryptography), and A.8.23 (cloud security) [2][8]. For telehealth and remote access, enforce TLS 1.2+ encryption and align VPN configurations with both standards.
Building an Integrated Compliance Program
To streamline compliance efforts, organizations can create a unified program that merges ISO 27001 and HIPAA requirements into a single governance structure. This approach uses ISO 27001 as the foundation for an overarching Information Security Management System (ISMS), while incorporating HIPAA Security Rule requirements into the Statement of Applicability (SoA) and the risk treatment plan. By doing so, you eliminate redundant policies, assessments, and documentation, ensuring that one comprehensive set of records satisfies both frameworks. Here's how this integration can simplify operations.
Steps to Integration
Start by defining the scope to include all systems, facilities, and third parties that handle electronic Protected Health Information (ePHI). Conduct a risk assessment that meets both ISO 27001 Clause 6 and HIPAA’s risk analysis standards. This involves identifying threats, vulnerabilities, and treatment decisions for each ePHI asset.
Next, create a crosswalk matrix to map HIPAA Security Rule standards (45 C.F.R. §164.308–316) to the corresponding ISO 27001 clauses and Annex A controls. Address any gaps, such as Business Associate Agreements (BAAs) or breach notification processes, directly within your SoA. The matrix should include:
- HIPAA citations
- Mapped ISO controls
- Safeguard categories (administrative, physical, technical)
- Implementation status
- Responsible owners
- Evidence references
Finally, align your policies so that each control satisfies both ISO 27001 and HIPAA requirements. This eliminates the need for separate HIPAA-specific documents, creating a more cohesive compliance framework.
Technology for Compliance
After integrating processes, automation can further simplify compliance management. Platforms like Censinet RiskOps™ centralize control mapping, automate risk assessments, and streamline workflows for healthcare organizations. These tools maintain your crosswalk matrix and SoA in one system, automate recurring HIPAA technical evaluations and ISO internal audits, and collect evidence - such as screenshots, configurations, logs, and training records - at scheduled intervals.
Terry Grogan, CISO of Tower Health, shared how automation transformed their operations:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." [5]
Similarly, James Case, VP & CISO of Baptist Health, highlighted the benefits:
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." [5]
By replacing manual spreadsheet tracking with automated workflows, healthcare organizations can handle more assessments, enhance data accuracy, and present a stronger compliance posture to auditors and regulators.
Operationalizing Across HDOs and Vendors
To extend the integrated ISO 27001–HIPAA controls to vendor management, classify vendors based on the criticality of the PHI they handle. Adjust the depth of assessments accordingly. Require vendors to provide evidence of equivalent controls, such as ISO 27001 certifications, SOC 2 reports with HIPAA criteria, or detailed control attestations. Incorporate these attestations into your control matrix.
Document shared and inherited controls - like cloud provider encryption and logging - directly in your crosswalk matrix and vendor contracts. For high-risk vendors, implement continuous monitoring through reassessments, vulnerability scans, and annual HIPAA/ISO attestations. Align internal audit plans to evaluate both your operations and those of key business associates, reusing the same testing methods and evidence library. This ensures consistent compliance across all parties handling PHI, while reducing the administrative workload tied to managing separate vendor programs.
sbb-itb-535baee
Continuous Improvement and Audit Readiness
Embedding Continuous Improvement
ISO 27001's Plan-Do-Check-Act (PDCA) cycle offers healthcare organizations a structured way to meet HIPAA's ongoing evaluation requirements. Specifically, the Check phase aligns with HIPAA's directive for periodic technical and nontechnical assessments under 45 CFR 164.308(a)(8). By using your crosswalk matrix, you can conduct internal audits to verify control effectiveness, review logs, analyze metrics, and test controls on a regular basis. The Act phase focuses on addressing findings by updating your risk register, revising treatment plans, and documenting decisions to prepare for future audits. ISO 27001 Clauses 9 and 10 help establish a repeatable process to maintain HIPAA compliance.
Tracking KPIs across clinical, IT, and compliance areas is a practical way to demonstrate program maturity. Metrics to monitor might include the percentage of controls tested on schedule, average time to remediate findings, incident response times, and training completion rates. Make it a point to schedule management reviews at least annually to assess ISMS performance, HIPAA risk posture, incidents, and improvement actions. Be sure to record minutes and decisions in your evidence library. This structured approach is critical, especially given OCR enforcement data showing that risk analysis and risk management failures are among the most commonly cited areas of HIPAA noncompliance in resolution agreements [2][8]. By following this continuous improvement process, you set the stage for thorough audit readiness.
Preparing for Audits
A well-structured ISO 27001 internal audit program can directly support HIPAA OCR investigations and external assessments. Start by designing a risk-based audit plan that addresses HIPAA’s administrative, physical, and technical safeguards on a prioritized schedule. For each requirement mapped in your crosswalk matrix, define specific test methods and maintain up-to-date artifacts like policies, configurations, screenshots, and training records [2][6].
When tailoring HIPAA’s addressable requirements, document your decisions and any compensating controls in the crosswalk matrix. If you rely on cloud providers for controls like encryption or logging, clearly outline these shared responsibilities in both your crosswalk matrix and vendor contracts. This documentation is invaluable during OCR reviews, as it supports risk-based decision-making. To ensure consistency, coordinate with vendors and business associates by aligning audit schedules and using shared testing methods and evidence libraries. Leveraging automation can simplify and streamline this entire process, making audit readiness more efficient.
Role of Technology in Sustaining Compliance
Technology plays a key role in maintaining compliance over time. Purpose-built platforms can transform manual, spreadsheet-heavy processes into automated workflows, making continuous monitoring and audit readiness far more efficient. For example, Censinet RiskOps™ centralizes your crosswalk matrix and Statement of Applicability, integrates with logging and SIEM tools to handle access audits aligned with HIPAA's audit control standard, and automates evidence collection at scheduled intervals. Its AI-powered tools speed up risk assessments and validate evidence, all while keeping human oversight intact.
Brian Sterud, CIO of Faith Regional Health, highlighted the importance of benchmarking:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." [5]
Conclusion
Aligning ISO 27001 controls with HIPAA requirements offers a structured and repeatable way to meet regulatory demands while enhancing security. ISO 27001 provides the framework for managing information security - the "how" - while HIPAA outlines the healthcare-specific rules - the "what" - for protecting electronic protected health information (ePHI) [2][3]. By creating a crosswalk matrix that maps HIPAA safeguards to ISO 27001 clauses and Annex A controls, organizations can streamline efforts, minimize redundant tasks, and maintain a single set of evidence for multiple audits. This approach also enables quicker responses to OCR investigations, payer assessments, and vendor due diligence requests [1][2][3].
Approximately 70 ISO 27002 controls align with HIPAA safeguards, meaning a significant portion of HIPAA’s requirements can be addressed through an ISO-based information security management system [4]. This integration shifts compliance from a one-time task to an ongoing improvement process. ISO 27001’s three-year certification cycle, paired with annual surveillance audits, supports the continuous maintenance of controls that also meet HIPAA standards [1]. The Plan-Do-Check-Act cycle ensures controls evolve alongside new threats, technologies, and regulatory updates [2][3][6].
Technology is key to sustaining this integrated approach. Automated compliance platforms replace manual processes with centralized crosswalk matrices, automated logging, and scheduled evidence collection. These tools not only improve operational efficiency but also enhance security and audit readiness, showcasing the practical benefits of combining ISO 27001 and HIPAA strategies.
To begin, conduct a gap assessment using the crosswalk matrix to pinpoint areas where ISO controls fall short of HIPAA requirements. Then, incorporate these findings into your risk treatment plan [1][2][4]. By using HIPAA as the baseline and ISO 27001 as the operational framework, healthcare organizations can develop a compliance program that grows with their needs, adapts to changes, and safeguards patient data effectively.
FAQs
How can organizations align ISO 27001 with HIPAA to simplify compliance?
Aligning ISO 27001 with HIPAA creates a streamlined path for managing security and privacy requirements. By mapping the controls of ISO 27001 to HIPAA standards, organizations can pinpoint overlaps, address any gaps, and build a more efficient compliance strategy.
Healthcare organizations can take this a step further by using tools that automate risk assessments, maintain ongoing compliance, and compare their efforts against industry benchmarks. This not only cuts down on manual work but also strengthens the protection of sensitive patient information while staying aligned with regulatory demands.
What are the key differences between ISO 27001 and HIPAA requirements?
ISO 27001 serves as an internationally acknowledged framework for managing information security using a risk-based methodology. It guides organizations in setting up, implementing, and continually refining an Information Security Management System (ISMS). On the other hand, HIPAA is a U.S. federal law aimed specifically at safeguarding the privacy and security of Protected Health Information (PHI) within the healthcare industry.
Here’s how they differ:
- Structure: ISO 27001 offers a flexible management standard, allowing organizations to adapt it to their specific needs. HIPAA, in contrast, is a legal mandate with clearly defined requirements that organizations must follow.
- Focus: ISO 27001 prioritizes risk management and ongoing improvement of security practices. HIPAA, however, is centered on enforcing specific safeguards to protect PHI.
- Scope: ISO 27001 applies universally across all industries, addressing information security broadly. HIPAA is exclusively designed for healthcare organizations, focusing on their unique data privacy and security responsibilities.
What is a crosswalk matrix, and how does it help map ISO 27001 controls to HIPAA requirements?
A crosswalk matrix serves as a practical tool to align ISO 27001 controls with HIPAA requirements, offering healthcare organizations a clear path to manage compliance with both frameworks. By mapping specific controls to their corresponding HIPAA safeguards, this matrix helps pinpoint gaps, prioritize necessary actions, and simplify compliance efforts.
This organized method not only saves time but also ensures that essential areas - like patient data protection and risk management - are properly addressed. For healthcare organizations, it’s a straightforward way to efficiently meet both regulatory and security standards.
Related Blog Posts
Key Points:
What is ISO 27001 and how does it relate to HIPAA?
- ISO 27001: An international standard for establishing, implementing, maintaining, and improving an information security management system (ISMS).
- HIPAA: A U.S. regulation focused on protecting electronic Protected Health Information (ePHI).
- Relationship: Mapping ISO 27001 to HIPAA helps organizations align their security controls, ensuring compliance with both frameworks while reducing duplication.
What is a crosswalk matrix in ISO 27001 and HIPAA mapping?
- Definition: A crosswalk matrix is a document that maps HIPAA safeguards to ISO 27001 controls, identifying overlaps and gaps.
- Purpose: It serves as a roadmap for implementing security measures that satisfy both frameworks, ensuring compliance and audit readiness.
What are the benefits of mapping ISO 27001 to HIPAA?
- Streamlined Compliance: Reduces duplication of efforts by aligning overlapping controls.
- Enhanced Security: Strengthens ePHI protection by integrating ISO 27001’s ISMS approach.
- Audit Efficiency: Simplifies audits by providing a unified compliance framework.
- Scalability: Supports organizations managing multiple compliance requirements.
What are some examples of mapped controls between ISO 27001 and HIPAA?
- Access Control:
- HIPAA 164.308(a)(4) (access control) maps to ISO 27001 Annex A.9.2 (user access management).
- Risk Management:
- HIPAA 164.308(a)(1) (risk analysis) maps to ISO 27001 Clause 6.1.2 (information security risk assessment).
- Incident Response:
- HIPAA 164.308(a)(6) (security incident procedures) maps to ISO 27001 Annex A.16 (information security incident management).
How can organizations implement ISO 27001 and HIPAA mapping?
- Create a Crosswalk Matrix: Develop a document that maps HIPAA requirements to ISO 27001 controls.
- Conduct Gap Analyses: Identify gaps in compliance and prioritize remediation efforts.
- Align Policies: Update security policies and procedures to reflect both frameworks.
- Train Staff: Educate employees on the requirements of both ISO 27001 and HIPAA.
What tools can help with ISO 27001 and HIPAA mapping?
- Compliance Management Platforms: Automate the creation of crosswalk matrices and track compliance progress.
- Crosswalk Generators: Tools that map HIPAA safeguards to ISO 27001 controls, simplifying evidence management.
- Audit Tools: Platforms that centralize documentation and streamline audit preparation.


