ISO 27001 for Medical Device Manufacturers
Post Summary
Medical device manufacturers face serious cybersecurity risks, including ransomware, data breaches, and firmware tampering, which can compromise patient safety and disrupt operations. ISO/IEC 27001:2022 offers a structured framework for managing these risks through an Information Security Management System (ISMS). This standard helps safeguard data, ensure device functionality, and align with regulatory requirements like FDA guidelines and HIPAA.
Key Takeaways:
- ISO 27001 focuses on protecting the confidentiality, integrity, and availability of information, extending to device safety and functionality.
- It complements ISO 13485 (quality management) and ISO 14971 (safety risk management), creating a unified approach to cybersecurity and compliance.
- Certification demonstrates strong security practices, simplifies regulatory submissions, and improves vendor trust during risk assessments.
- Core requirements include asset management, secure development, encryption, access control, incident response, and supplier security.
- Benefits include reduced risk of cyber incidents, regulatory readiness, faster procurement processes, and better protection of patient data and device reliability.
By integrating ISO 27001 with existing quality and risk management systems, manufacturers can effectively address cybersecurity threats while meeting regulatory and market demands.
ISO 27001 Requirements for Medical Device Manufacturers
ISO 27001 certification aligns with U.S. regulatory expectations by requiring medical device manufacturers to implement an Information Security Management System (ISMS). This ISMS must address both product development and broader enterprise operations. The standard is structured into management system clauses (4–10), which outline how to establish, operate, monitor, and improve the ISMS, and Annex A, which lists 93 specific security controls grouped into four categories: Organizational, People, Physical, and Technological.[6][9]
ISO 27001 Clauses and Annex A Controls
Clauses 4–6 define the ISMS's scope, spanning product development to post-market surveillance, and emphasize leadership's role in ensuring cybersecurity and safeguarding patient data.[6] Clauses 7–8 require documented security policies, workforce training, secure development practices, and controlled operations across development, production, and cloud environments.[2][7] Clauses 9–10 focus on continuous improvement, using internal audits, incident reviews, and corrective actions to address evolving cyber threats.[10][7]
Annex A translates these principles into actionable security measures. For medical device manufacturers, key areas include:
- Asset management: Maintaining inventories of firmware, software, development tools, test systems, and production certificates.
- Access control: Implementing role-based permissions for engineering teams, service technicians, and backend administrators, with multi-factor authentication for critical accounts.
- Cryptography: Encrypting protected health information (PHI) during transit and storage, managing encryption keys securely, and using digitally signed firmware updates.
- Operations security: Using hardened server images, conducting vulnerability scans, managing changes, and segregating development, testing, and production environments.
- Secure development: Applying secure coding standards, performing static and dynamic testing, and incorporating security gates in CI/CD pipelines.
- Supplier relationships: Including security requirements in contracts with cloud providers, component vendors, and contract manufacturers.
- Incident management: Implementing logging, monitoring, and response playbooks for safety-critical anomalies.[2][4][6][8]
These controls create a foundation for a risk-based security strategy tailored to the unique needs of medical devices.
Risk-Based Security Approach for Medical Devices
ISO 27001’s risk-based methodology integrates seamlessly with ISO 14971 for medical device risk management and FDA cybersecurity guidance. Manufacturers can map information security risks - such as unauthorized access, malware, or data corruption - into the ISO 14971 hazard analysis, treating cyber events that could impact clinical performance or patient safety with the same rigor as hardware or software failures.[3][8][9]
For Software as a Medical Device (SaMD) and connected devices, a practical approach begins with asset- and data-centric scoping. This involves identifying all SaMD modules, supporting microservices, APIs, mobile apps, and data flows (including PHI) and incorporating them into the ISMS.[2][9] Next, a threat-informed risk analysis evaluates how cyber events - such as API breaches, cloud outages, or credential theft - might affect clinical workflows, diagnosis, or therapy.[3][8] High-impact components, like decision logic, dosing algorithms, and PHI storage, require stronger controls, while lower-risk elements can use proportionate measures.[2][9] Finally, a feedback loop using field data - such as incident reports and vulnerability disclosures - ensures ongoing risk evaluations as part of the ISMS improvement cycle.[10][7]
Examples of ISO 27001 Controls in Medical Devices
For SaMD backends and APIs, manufacturers implement role-based access controls for developers, DevOps, and support staff, covering code repositories, build pipelines, production databases, and admin portals. Multi-factor authentication is mandatory for accounts that can modify algorithms or access PHI.[2][4] PHI and clinical event logs are encrypted using hardware security modules or cloud key management systems, while API communications are secured with TLS.[2][8] Centralized logging tracks authentication events, API calls, configuration changes, and unusual access patterns, enabling swift responses to safety-critical anomalies.[2][7]
For remote maintenance and support, manufacturers use VPNs or zero-trust solutions to enable controlled remote access. Strong authentication and time-limited, device-specific authorizations ensure that service technicians have only the permissions needed for diagnostics or maintenance, avoiding shared accounts.[2][4][8] Firmware and software updates are digitally signed and verified on devices before installation, preventing tampering. All remote activities, including commands, configuration changes, and updates, are logged for forensic analysis and regulatory compliance.[2][8][7]
In cloud-based environments where PHI and device data are processed or stored, manufacturers treat third-party cloud services as critical information assets. These assets are assigned owners, risk ratings, and lifecycle controls, including patch management and end-of-life planning.[2][4][9] Contracts with cloud providers include security requirements, such as vulnerability disclosure obligations, incident reporting timelines, and data protection clauses.[2][4] Manufacturers regularly reassess cloud providers' security measures to ensure compliance with regulatory and contractual standards. Additionally, contingency plans, backups, and recovery systems are in place to prevent disruptions from impacting device availability or patient care.[2][4][7]
These examples highlight how targeted security measures safeguard both device functionality and patient data, addressing regulatory expectations while protecting public health.
Benefits of ISO 27001 Certification
Regulatory and Compliance Benefits
ISO 27001 offers a structured framework that aligns seamlessly with the FDA's cybersecurity expectations for both premarket and postmarket submissions. This includes documented risk assessments, control evidence, and incident response procedures, all of which can be integrated into design history files, technical documentation, and regulatory submissions. This approach showcases modern security practices to FDA reviewers [3][8]. For manufacturers managing protected health information (PHI), the Information Security Management System (ISMS) aligns with the HIPAA Security Rule's safeguards - administrative, physical, and technical - creating a unified strategy that addresses both safety and privacy requirements [2].
The certification process also strengthens regulatory preparedness. It requires detailed policies, procedures, risk assessments, and control evidence, which are invaluable for FDA submissions, audits by notified bodies, and customer due diligence reviews [2][6]. Regular internal audits, management reviews, and a focus on continuous improvement establish a cycle of evidence collection and corrective actions that regulators view as hallmarks of a mature cybersecurity program [10][6]. Additionally, annual audits conducted by external certification bodies provide third-party assurance, potentially reducing the intensity and frequency of regulatory inspections and customer evaluations. On a global scale, some markets mandate or strongly favor ISO 27001 certification for digital health solutions and software-based medical devices, making it a key to unlocking international market opportunities [3]. These rigorous regulatory practices also pave the way for tangible business benefits.
Business and Competitive Advantages
Achieving ISO 27001 certification sends a strong message to hospitals and health systems: the manufacturer has a mature, verified approach to information security. This builds trust quickly during vendor risk assessments and simplifies the process by addressing many control-related questions upfront [4][5].
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." – Terry Grogan, CISO, Tower Health [1]
The certification also safeguards intellectual property, such as proprietary algorithms, design files, source code, and clinical data sets, through formal asset management, access controls, encryption, and supplier security protocols [2][4]. For U.S. manufacturers, where software and data assets are central to business value, demonstrating a certified, multi-layered security approach can boost investor confidence and enhance valuations during funding rounds or mergers and acquisitions [4][5]. Furthermore, certification can provide a competitive edge in RFPs where cybersecurity and patient data protection are key evaluation criteria, helping manufacturers secure contracts with healthcare buyers who prioritize risk management [2][4]. Beyond competitive advantages, ISO 27001 certification also supports better clinical outcomes and operational stability.
Clinical and Operational Benefits
ISO 27001's risk-based framework helps manufacturers proactively identify and address cybersecurity threats that could impact device performance or patient safety. These threats include unauthorized access, malware, or data corruption, which could disrupt clinical workflows, diagnostics, or therapies [8][9]. By implementing controls for secure software development, change management, and configuration management, the ISMS minimizes the risk of vulnerabilities in device firmware, mobile applications, and cloud platforms [2][8]. Additionally, robust incident management and business continuity measures ensure swift detection, containment, and recovery from cyber incidents, reducing potential harm to patients [2].
Operationally, the standard emphasizes system monitoring, operations security, backups, and continuity planning, all of which contribute to higher reliability and uptime for connected medical devices and their associated services [2][4]. Advanced logging and monitoring systems enable early detection of anomalies, reducing the likelihood of unexpected downtime [2]. Backup and recovery protocols ensure that critical data, logs, and application components can be quickly restored after failures or attacks - an essential safeguard for SaaS-based device platforms operating in U.S. hospitals [2][4]. Lastly, the commitment to continuous improvement drives regular reviews of incidents and near-misses, fostering ongoing enhancements in infrastructure and processes. Over time, this results in more reliable clinical performance and operational resilience [10][6].
How to Achieve ISO 27001 Certification
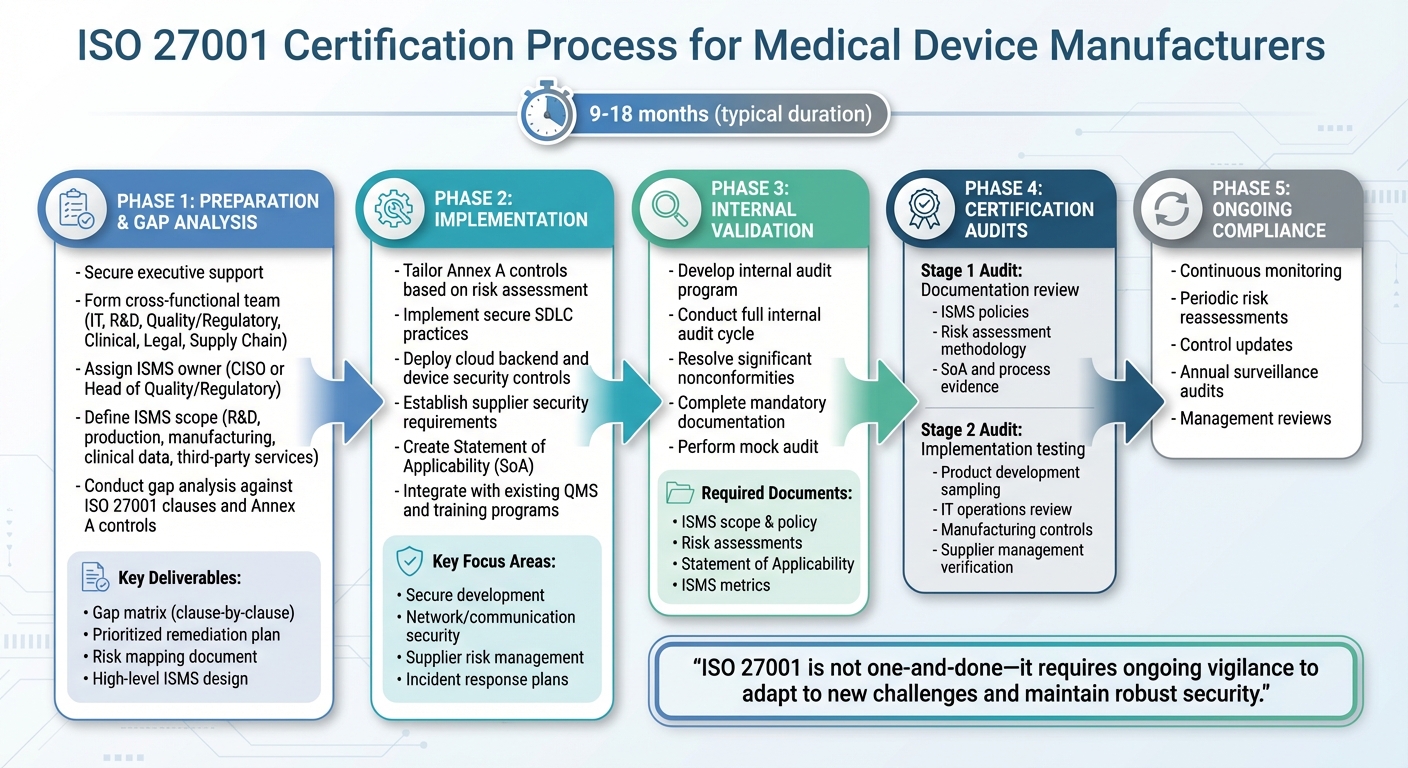
ISO 27001 Certification Process for Medical Device Manufacturers
Gap Analysis and Scope Definition
Start by securing executive support and forming a diverse team from departments like IT, R&D, Quality/Regulatory, Clinical, Legal, and Supply Chain. Assign an ISMS (Information Security Management System) owner - often the CISO or Head of Quality/Regulatory - to lead the initiative. This ensures alignment with FDA cybersecurity guidelines and HIPAA/PHI requirements.
Define the scope of your ISMS to cover areas where security risks are present. This might include R&D, secure development, production environments (both cloud and on-premise), manufacturing, test facilities, clinical and post-market data, and critical third-party services handling ePHI or safety-related data. Start with a focus on products and data, identifying all environments and processes that interact with patient data or control connected devices. Then, narrow the scope to include only the locations, business units, and suppliers that directly impact the confidentiality, integrity, and availability of these assets.
Conduct a gap analysis to compare your current practices against ISO 27001 clauses and Annex A controls. This step builds on your existing risk management framework to ensure all critical areas are addressed. Use existing quality, cybersecurity, and risk documentation to streamline this process. Key deliverables should include:
- A clause-by-clause and control-by-control gap matrix
- A prioritized remediation plan with actionable steps, owners, and timelines
- A mapping of medical device risks to information security risks
- A high-level ISMS design that integrates ISO 27001 into your current QMS and risk management processes
For a small-to-mid-size medical device manufacturer, achieving ISO 27001 certification typically takes 9–18 months from project initiation to passing the Stage 2 audit. The timeline depends on factors like existing controls, regulatory readiness, and product complexity.
With the scope and gaps clearly defined, the next step is implementing the necessary controls.
Implementing ISO 27001 Controls
Tailor Annex A controls based on your risk assessment. For secure development, this may include enforcing security policies, implementing a secure SDLC (Software Development Life Cycle), controlling access to development tools, applying cryptographic controls, and conducting continuous monitoring. Specific actions might involve mandatory code reviews, static and dynamic analysis, threat modeling, and ensuring secure use of open-source components.
For cloud backends and deployed devices, focus on areas like network and communication security, secure update mechanisms, configuration management, robust authentication and authorization, and incident response plans. Supplier security is also critical - classify vendors by risk, use security questionnaires, include specific security clauses in contracts, and conduct regular assessments. High-risk vendors, such as cloud providers or software component suppliers, should meet documented security requirements (e.g., encryption, access control, vulnerability management) and provide evidence of certifications like ISO 27001 or SOC 2. Platforms like Censinet RiskOps™ can simplify third-party risk assessments and continuous monitoring, particularly for healthcare vendors and medical device supply chains.
Leverage existing management review meetings to monitor ISMS performance, address nonconformities through your established CAPA system, and integrate information security training into mandatory annual sessions. Align document control, change control, and record retention with your QMS practices. Create a Statement of Applicability (SoA) to outline which Annex A controls are relevant, how they are implemented, and why any are excluded - customized to your device and operational context.
These controls are the foundation for audits and ongoing compliance. Once implemented, validate their effectiveness through thorough audits.
Certification Audits and Ongoing Compliance
Develop an internal audit program that covers the ISMS scope, including product development, manufacturing, clinical support, and IT operations. A risk-based audit plan should prioritize areas with the greatest impact on patient safety and PHI, such as secure software updates, vulnerability management, and third-party hosting environments. Conduct at least one full internal audit cycle, resolve significant nonconformities, and ensure that mandatory documents (e.g., scope, information security policy, risk assessments, SoA, ISMS metrics) are complete. A "mock audit" can help test readiness and ensure evidence is accessible.
The certification process involves two main stages:
- Stage 1: Auditors review ISMS documentation to assess readiness. This includes evaluating the scope, ISMS policies, risk assessment and treatment methodology, SoA, and evidence of key processes.
- Stage 2: Auditors test the implementation and effectiveness of controls by sampling across product development, IT operations, manufacturing, and supplier management. They will look for records like secure SDLC artifacts, links between cybersecurity risks and device safety risks, supplier security requirements, and incident response exercises.
To maintain certification, commit to continuous monitoring, periodic risk reassessments, updated controls, and annual surveillance audits. This ensures your ISMS evolves alongside changing device portfolios and emerging cyber threats. Remember, ISO 27001 compliance isn’t a one-and-done effort - it requires ongoing vigilance to adapt to new challenges and maintain robust security.
sbb-itb-535baee
Integrating ISO 27001 with Medical Device Risk Management
Aligning ISO 27001 with ISO 13485 and ISO 14971
ISO 27001 plays a key role in reinforcing existing quality and risk management systems by addressing cybersecurity threats as safety hazards. For instance, a ransomware attack delaying treatment or a firmware vulnerability causing dosing errors transforms IT problems into direct risks to patient safety.
To align ISO 27001 with ISO 13485 and ISO 14971, map the Information Security Management System (ISMS) lifecycle - covering context, planning, support, operation, performance evaluation, and improvement - directly to ISO 13485 quality management processes. For example, incorporate Annex A controls into design inputs and verification reports. Supplier controls from ISO 27001 can also be integrated into ISO 13485 purchasing procedures and supplier qualification workflows. Any risk treatment actions identified during ISO 27001 assessments should be documented and maintained within the quality records and change control processes already governed by ISO 13485.
A unified risk register is essential to manage both cybersecurity and safety hazards. For every cybersecurity threat scenario - like unauthorized access to device configurations or data integrity loss - trace the potential patient harms as required by ISO 14971. Use a consistent risk matrix to assess likelihood and severity, but document separate criteria for accepting safety risks versus information security risks. Postmarket surveillance activities should feed security incident data into both the ISMS risk review and the ISO 14971 risk management file. This ensures coordinated updates to risk controls, labeling, and any necessary field actions.
To streamline this approach, establish a cross-functional risk and compliance committee that includes representatives from quality, regulatory, IT/security, R&D, clinical, and supply chain teams. This group should manage a combined framework where shared elements - like document control, training, audits, CAPA, and management review - are unified under a single system. Internal audits can cover ISO 13485, ISO 27001, and related processes in one cycle, while management reviews can address quality, safety, and cybersecurity metrics and incidents in a single agenda.
This integrated approach strengthens the connection between quality and cybersecurity, ensuring that the supply chain remains secure.
Securing the Medical Device Supply Chain
A secure supply chain is critical, as vulnerabilities in third-party components can pose serious risks. ISO 27001 Annex A supplier relationship controls offer a structured way to manage security requirements for third-party software, cloud providers, and service partners throughout the device lifecycle.
Start by classifying and inventorying third-party software components, libraries, and services as information assets under ISO 27001. These assets should be included in device risk analyses, ensuring vulnerabilities trigger formal risk assessments and remediation. Supplier contracts should specify minimum security certifications (like ISO 27001 for cloud providers), access control measures, encryption standards, backup protocols, and incident response processes. Additional requirements should include secure development practices, patching protocols, and obligations to report security incidents within defined timeframes. Contracts should also address data protection clauses for PHI, data residency, and subcontractor management.
For hardware and embedded component suppliers, contracts should cover secure boot processes, cryptographic component sourcing, and chain-of-custody protocols to minimize risks of tampering or counterfeit parts. These supplier requirements should be seamlessly integrated into ISO 13485 processes. During manufacturing and logistics, controls like physical security measures, secure configurations, and production data protection help prevent tampering and data breaches. For field service operations, ISO 27001 promotes secure remote access, authenticated service tools, and maintenance action logging to safeguard device integrity and PHI. At the end of a device's lifecycle, ISO 27001-aligned procedures ensure secure data erasure, destruction, or sanitization to prevent residual data exposure.
Specialized platforms can further enhance these integrated controls.
Using Censinet RiskOps™ for ISO 27001 Programs

Automated platforms like Censinet RiskOps™ simplify the complexities of managing third-party risk at scale. Static spreadsheets are no longer sufficient for continuous monitoring and compliance. Censinet RiskOps™ centralizes third-party risk assessments, automates control validation, and supports ongoing monitoring for ISO 27001 programs across the medical device supply chain.
The platform automates processes like collecting security questionnaires mapped to ISO 27001 controls and healthcare-specific needs, such as PHI handling and device connectivity. It also scores supplier risk and tracks remediation plans. This allows healthcare organizations to evaluate vendors against ISO 27001, FDA cybersecurity guidance, and internal policies in a single workflow. Censinet RiskOps™ provides aggregated risk scores, control maturity metrics, and trends in supplier issues, which can be incorporated into ISO 27001 risk assessments. Recurring high-risk findings - such as issues with access control or encryption - can inform targeted risk treatment plans, updates to controls, or even supplier replacement strategies aligned with Annex A.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." - Terry Grogan, CISO, Tower Health
The platform’s continuous monitoring features - such as alerts for significant security events, certification changes, or unresolved critical findings - help meet ISO 27001’s requirement for ongoing supplier oversight. During management reviews, dashboards and benchmarking tools from Censinet RiskOps™ can illustrate how your organization stacks up against industry peers. This supports decisions on investment priorities, control effectiveness, and diversifying the supply chain. By integrating such platforms with your ISO 13485 QMS, vendor security issues can automatically trigger CAPAs, risk file updates, or design changes. This ensures ISO 27001 compliance becomes part of everyday operations, protecting device functionality and patient safety as part of a broader strategy.
Conclusion
ISO 27001 provides a structured and auditable framework that transforms cybersecurity efforts into an ongoing risk management process. It goes beyond standard IT measures, addressing every stage - from design and manufacturing to deployment and postmarket support - safeguarding sensitive information like PHI, clinical data, and intellectual property.
While not a legal requirement in the U.S., ISO 27001 aligns closely with FDA cybersecurity expectations and demonstrates the maturity vendors need to pass assessments. This alignment can reduce procurement challenges and speed up sales cycles. Internally, implementing an ISMS - with its policies, technical controls, supplier oversight, incident response planning, and business continuity measures - helps cut down on rework, reactive security measures, and the financial toll of breaches or recalls. This level of discipline also integrates naturally with existing quality and risk management standards.
By combining ISO 27001 with ISO 13485 and ISO 14971, manufacturers can weave cybersecurity directly into their quality and risk management systems, treating security risks with the same level of scrutiny as clinical risks.
As cyber threats grow more sophisticated and regulatory expectations increase, adopting ISO 27001 allows manufacturers to stay ahead of the curve. Early adopters gain advantages like easier market access, stronger partnerships, and smoother reimbursement pathways, all while reducing long-term technical debt in their security infrastructure. Tools like Censinet RiskOps™ can further simplify this process by automating risk assessments, validating controls, and benchmarking supplier risks, making ISO 27001 a practical and ongoing commitment.
FAQs
How does ISO 27001 certification help protect medical device manufacturers from cybersecurity threats?
ISO 27001 certification provides medical device manufacturers with a systematic approach to bolstering cybersecurity. It establishes a framework to identify, evaluate, and address risks associated with sensitive information, such as patient data and medical devices. This certification ensures the application of strong security measures while meeting industry regulations, helping to minimize vulnerabilities and strengthen defenses against cyber threats.
By promoting continuous improvement, ISO 27001 safeguards critical information while also fostering trust among patients and partners. This trust is essential for maintaining security and reliability in an increasingly interconnected healthcare environment.
How does ISO 27001 differ from ISO 13485 and ISO 14971 for medical device manufacturers?
ISO 27001 is all about creating and maintaining an information security management system (ISMS) to safeguard sensitive data and tackle cybersecurity risks across an organization. Meanwhile, ISO 13485 zeroes in on quality management systems for medical devices, ensuring these products comply with regulatory and safety standards. Then there's ISO 14971, which focuses specifically on risk management to ensure medical device safety throughout the entire product lifecycle.
The key difference lies in their focus areas: ISO 27001 deals with information security on an organizational level, while ISO 13485 and ISO 14971 are designed specifically for the design, production, and safety of medical devices.
How can medical device manufacturers align ISO 27001 with their existing quality and risk management systems?
Medical device manufacturers can align ISO 27001 with their quality and risk management systems by integrating risk assessment processes into a single, cohesive framework. This approach ensures that cybersecurity measures and quality management practices operate in harmony, reducing gaps and overlaps.
Tools like Censinet RiskOps™ make this process easier by simplifying risk assessments, keeping track of compliance, and supporting ongoing improvements. With this method, manufacturers can meet regulatory demands while protecting patient data, securing medical devices, and strengthening supply chain security.


