ISO 27001 for Multi-State Healthcare Compliance
Post Summary
ISO 27001 is a global standard for building a structured Information Security Management System (ISMS). It's especially useful for healthcare organizations in the U.S. managing Protected Health Information (PHI) across multiple states. Why? It provides a unified framework to meet HIPAA requirements while addressing state-specific privacy rules. With healthcare breaches costing $10.93 million per incident on average in 2023, organizations need a system to reduce risks, ensure compliance, and simplify operations.
Key takeaways:
- ISO 27001 helps align HIPAA safeguards with state laws.
- It emphasizes risk assessment, access control, encryption, and incident management.
- A unified ISMS streamlines compliance across locations and reduces errors.
- Tools like Censinet RiskOps™ automate assessments and centralize risk data for easier management.
Core ISO 27001 Components for Healthcare Compliance
ISO 27001 Components Mapped to HIPAA and State Healthcare Compliance Requirements
ISO 27001 Clauses and Annex A Controls for Healthcare
ISO 27001 is built around Clauses 4–10, which establish governance and operational standards, and Annex A, which contains 93 controls spanning Organizational, People, Physical, and Technological domains. For healthcare organizations handling PHI (Protected Health Information) across multiple states, certain clauses and controls are especially relevant.
Clause 6 (Planning and Risk Treatment) emphasizes conducting a formal risk assessment to identify and address threats to information assets. In the healthcare context, this involves assessing risks to PHI, medical devices, clinical applications, and third-party vendors, while also factoring in state-specific legal requirements.
Clauses 7 and 8 (Support and Operation) focus on implementing policies, training programs, and change management processes, aligning closely with HIPAA's administrative safeguards.
Key Annex A control areas for healthcare include:
- Access Control: This highlights role-based access, least privilege principles, multi-factor authentication (MFA), and secure user authentication. These measures align with HIPAA's technical safeguards for controlling access and ensuring unique user identification.
- Cryptography: This involves encrypting PHI both in transit and at rest, supported by strong key management practices, which align with HIPAA's encryption standards.
- Operations Security and Logging: Controls like audit logs, system monitoring, malware protection, and backup procedures support HIPAA's audit requirements and help meet state expectations for maintaining adequate security measures.
According to BSI's analysis of HIPAA and ISO 27001, there are strong overlaps between the two, particularly in areas like risk analysis, access control, audit logging, and incident response [2]. The 2022 update to ISO 27001 reorganized controls into 93 items across four themes, creating a modern, risk-based structure that is especially useful for healthcare organizations managing cloud services and complex third-party relationships [4].
These controls not only protect sensitive assets but also help organizations align with regulatory requirements.
Aligning ISO 27001 with HIPAA and State Privacy Laws
While HIPAA is a federal regulation with mandatory safeguards enforced by the Office for Civil Rights, ISO 27001 is a voluntary framework that provides a certifiable structure for managing information security. HIPAA specifies what protections are required, whereas ISO 27001 offers a comprehensive system for implementing, monitoring, and improving those protections.
For instance, HIPAA requires a risk analysis, and ISO 27001's Clause 6 provides a structured methodology to conduct one. Similarly, Annex A’s detailed guidance on access control and audit logging aligns closely with HIPAA's technical safeguard requirements.
ISO 27001's risk-based approach also allows healthcare organizations operating in multiple states to incorporate state-specific requirements into a unified Information Security Management System (ISMS). For states with stricter breach notification rules or broader definitions of sensitive data - like biometric or genetic information - ISO 27001 enables tailored control implementations while maintaining a consistent governance framework [2][4]. BSI highlights that ISO 27001 can help organizations meet multiple regulatory requirements simultaneously, as many Annex A controls align directly with HIPAA's administrative, physical, and technical safeguards.
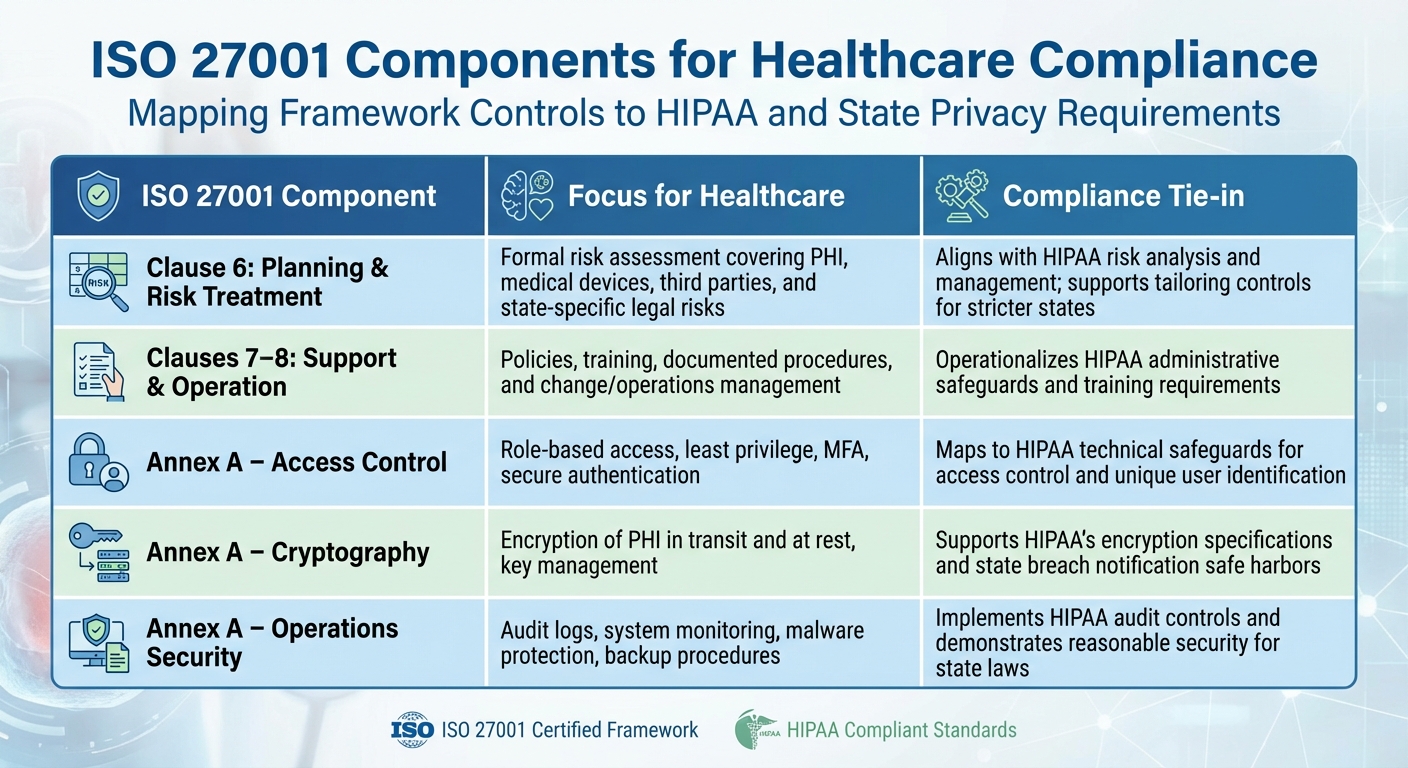
ISO 27001 Components and Healthcare Compliance
| ISO 27001 Component | Focus for Healthcare | Compliance Tie-in (HIPAA / State Laws) |
|---|---|---|
| Clause 6: Planning & Risk Treatment | Formal risk assessment covering PHI, medical devices, third parties, and state-specific legal risks | Aligns with HIPAA risk analysis and management; supports tailoring controls for stricter states [2][4] |
| Clauses 7–8: Support & Operation | Policies, training, documented procedures, and change/operations management | Operationalizes HIPAA administrative safeguards and training requirements [3][2] |
| Annex A – Access Control | Role-based access, least privilege, MFA, secure authentication | Maps to HIPAA technical safeguards for access control and unique user identification [3][2] |
| Annex A – Cryptography | Encryption of PHI in transit and at rest, key management | Supports HIPAA's encryption specifications and state breach notification safe harbors [3][2][4] |
| Annex A – Operations Security | Audit logs, system monitoring, malware protection, backup procedures | Implements HIPAA audit controls and demonstrates reasonable security for state laws [3][2][4] |
How to Implement ISO 27001 Across Multi-State Operations
Building a Unified ISMS for Multi-State Operations
To start, create a single, unified scope statement that applies across all locations. This should cover every system that processes sensitive data, such as PHI, regulated information, cloud platforms, medical devices, clinical tools, research data, supply chain partners, and third-party vendors in all states. Be sure to document any exceptions for states with stricter rules on data retention or breach notifications.
Next, establish a central risk register that connects each risk and asset to the specific regulations and jurisdictions they impact. This approach helps pinpoint which risks apply to which states and identifies the controls already in place.
To balance enterprise-wide consistency with state-specific requirements, implement centralized governance paired with localized execution. Designate local security or privacy coordinators in each state to enforce overarching policies and relay any state-specific needs to the central team. Standardize key policies - like access control, incident response, vendor risk management, and data classification - while managing state-specific variations with controlled appendices rather than creating separate policy sets.
This unified approach ensures a solid foundation for mapping controls to meet both HIPAA and state-specific regulations.
Mapping ISO 27001 Controls to HIPAA and State Requirements
Develop a crosswalk document that aligns ISO 27001 clauses and Annex A controls with HIPAA Security Rule standards and major state privacy laws. Organize the document with ISO controls listed in rows and columns for HIPAA’s administrative, physical, and technical safeguards. Add columns for state-specific requirements, such as breach definitions, notification timelines, encryption rules, and data retention policies.
For each ISO control, indicate the level of coverage: full, partial, or none. Full coverage means the ISO control completely addresses the regulatory requirement, partial coverage suggests additional steps are needed, and non-coverage indicates new controls must be implemented. For example, while ISO 27001 access control measures might fully satisfy HIPAA’s user identification standards, stricter state requirements may call for further enhancements.
Use ISO 27001 Annex A as your baseline and add safeguards only where absolutely necessary. Draft a single enterprise policy for each topic that meets the strictest requirement, documenting state-specific variations as exceptions. Conduct annual reviews with privacy and legal experts to ensure your framework stays aligned with evolving state laws and addresses any gaps.
Once control mapping is in place, the next step is to standardize how incidents and breaches are managed.
Standardizing Incident and Breach Management
Align your incident management processes with HIPAA’s definitions of "security incident" and "breach" by integrating the HIPAA four-factor breach risk assessment into your workflow. Create a central incident response plan that outlines roles, decision-making paths, and escalation procedures. Add state-specific annexes detailing relevant laws, notification thresholds, and timing requirements. Use the shortest notification window required by any state as your baseline.
Implement standardized triage and classification protocols to quickly determine if an event qualifies as an ISO security incident, a HIPAA security incident, or a notifiable breach under either HIPAA or state laws. Develop playbooks for common scenarios, such as misdirected PHI, lost devices, ransomware attacks, or vendor breaches. These playbooks should include notification templates and task lists tailored to the strictest applicable requirements.
Maintain a central legal requirements register to track notification triggers, required recipients (e.g., patients, state attorneys general, or regulators), and content requirements for each jurisdiction. Standardize notification templates to meet HIPAA content rules while adding conditional sections for state-specific language. Regular multi-state breach drills will help ensure your teams can meet tight deadlines and comply with varying legal obligations at the same time.
sbb-itb-535baee
Using Technology to Simplify ISO 27001 Compliance
Censinet RiskOps™ for Third-Party and Enterprise Risk Management

Managing ISO 27001 compliance across multiple states can quickly become overwhelming when relying on spreadsheets and manual processes. Technology changes the game by centralizing risk data, automating assessments, and keeping audit readiness in check - all within a single platform. This unified approach simplifies navigating the complexities of diverse regulatory landscapes.
Censinet RiskOps™ is specifically designed to address the challenges healthcare organizations face when implementing ISO 27001 across multiple states. The platform provides a centralized vendor inventory, runs standardized ISO 27001-aligned questionnaires, and tracks remediation actions. By tagging controls to both HIPAA and state-specific requirements, while maintaining a single set of unified policies, organizations can streamline compliance without sacrificing precision.
The results speak for themselves. Terry Grogan, CISO at Tower Health, shared:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." [1]
With AI-powered tools, the platform automates tedious tasks like completing security questionnaires, summarizing evidence, and generating risk summary reports. For organizations operating across multiple states, it offers state-specific views and policies while maintaining a global baseline aligned with ISO 27001. This reduces duplication, ensures consistency, and makes compliance a smoother process.
These automated features are part of a larger trend of leveraging technology to simplify compliance workflows and boost efficiency.
Making Compliance Easier with Technology
Healthcare-specific platforms take this centralized approach a step further, delivering tailored solutions for one of the most complex industries. Matt Christensen, Sr. Director GRC at Intermountain Health, explained:
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." [1]
Platforms designed for healthcare integrate risk management across different regions and legal frameworks. They maintain centralized, ISO 27001-aligned risk registers with designated risk owners for each location. Key features include automated access reviews for PHI systems and integration with HR and identity systems to detect personnel changes, such as new hires, transfers, or departures. For incident management, these platforms allow organizations to create playbooks that align ISO 27001 controls with state notification requirements, while logging every action, decision, and approval with timestamps to meet compliance and audit demands.
Improved visibility is another major benefit. Brian Sterud, CIO at Faith Regional Health, highlighted:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." [1]
With real-time risk data displayed in intuitive dashboards, boards and executives gain the insights needed to make informed decisions about resource allocation and strategic priorities across all state operations.
Organizations that transition from manual processes to automated, centralized ISMS platforms report significant gains in efficiency. By reducing documentation duplication, streamlining audits, and replacing fragmented spreadsheets with a collaborative risk network of healthcare delivery organizations and over 50,000 vendors, platforms like Censinet RiskOps™ transform ISO 27001 compliance into a strategic advantage rather than a cumbersome task.
Conclusion
Unified compliance simplifies the chaos of fragmented programs. ISO 27001 provides a comprehensive framework that aligns with HIPAA and various state laws, enabling healthcare organizations to safeguard Protected Health Information (PHI) while showcasing due diligence to regulators and partners. As BSI notes, when applied effectively, ISO 27001 can "meet and exceed multiple regulatory requirements" by creating a cohesive security program rather than relying on disjointed, siloed efforts [2]. This streamlined approach not only makes compliance more manageable but also lays the groundwork for ongoing operational efficiency.
An Information Security Management System (ISMS) brings structure, ensuring organizations are always audit-ready - no more last-minute scrambles. With standardized documentation, centralized evidence, and consistent controls, audits become less burdensome, and duplicate efforts are reduced. Considering that healthcare data breaches often cost organizations over $10 million per incident - far exceeding the average across industries - the systematic risk management offered by ISO 27001 is a vital investment. This approach not only mitigates breach risks but also enhances operational consistency, a critical point emphasized earlier.
For CIOs, CISOs, and compliance leaders, success hinges on three key actions: securing executive sponsorship for an organization-wide ISMS, developing a unified control framework that aligns with HIPAA and state laws, and adopting technology to automate workflows and maintain consistency.
Achieving these goals depends on leveraging advanced tools. Platforms like Censinet RiskOps™ transform ISO 27001 into a strategic advantage by centralizing risk data, automating assessments, and providing real-time visibility across multiple state operations. Integrating such technology with a unified ISMS ensures organizations can balance compliance with operational efficiency. The outcome? Stronger security, reduced costs, and comprehensive protection across all states.
FAQs
How can ISO 27001 help healthcare organizations meet HIPAA and state-specific privacy requirements?
ISO 27001 offers healthcare organizations a solid framework to manage information security effectively. It helps them meet HIPAA standards as well as state-specific privacy regulations. By adopting ISO 27001, organizations can create policies, procedures, and controls designed to safeguard sensitive patient data, like Protected Health Information (PHI), while also addressing potential risks and ensuring regulatory compliance.
The standard’s emphasis on ongoing improvement ensures that organizations can keep pace with shifting privacy laws across different states. This flexibility is essential for navigating the challenges of a constantly changing legal environment.
Which ISO 27001 controls support HIPAA's technical safeguard requirements?
ISO 27001 incorporates critical controls that align closely with HIPAA's technical safeguards. For instance, Access Control (A.9) ensures that sensitive information is accessible only to those with proper authorization. Similarly, Cryptography (A.10) focuses on safeguarding data through encryption techniques. Another key element, Information Security Incident Management (A.16), facilitates prompt detection and effective response to security breaches. Together, these measures address HIPAA requirements for authentication, encryption, and breach response, providing strong safeguards for patient data.
How does Censinet RiskOps™ help healthcare organizations achieve ISO 27001 compliance across different states?
Censinet RiskOps™ provides healthcare organizations with a smarter way to handle ISO 27001 compliance. It simplifies the often-tedious process of risk assessments and documentation by automating key tasks. With its real-time analytics and centralized tools, managing cybersecurity risks becomes more efficient, even in the face of diverse state privacy laws.
By cutting down on manual work and promoting consistent compliance practices, healthcare teams can prioritize what matters most - protecting patient data, securing critical systems, and meeting regulatory standards with peace of mind.


