How ISO 27001 Tools Simplify Healthcare Risk Management
Post Summary
ISO 27001 tools help healthcare organizations manage cybersecurity risks by providing a structured approach to protect sensitive data like patient records and medical device systems. These tools align with HIPAA and other U.S. regulations, enabling organizations to identify risks, implement security controls, and monitor their effectiveness. Key features include:
- Centralized Risk Management: Consolidates all assets, like EHR systems and medical devices, into a single database for easier tracking.
- Automated Workflows: Streamlines risk assessments and remediation processes, reducing manual effort.
- Continuous Monitoring: Offers real-time visibility into vulnerabilities and compliance status.
With healthcare data breaches costing over $10 million on average, these tools not only improve security but also reduce financial and operational impacts. Platforms like Censinet RiskOps™ are specifically designed for healthcare, making risk management more efficient and reliable.
How ISO 27001's Risk-Based Approach Works in Healthcare
ISO 27001 doesn’t dictate a fixed security checklist for everyone. Instead, it asks healthcare organizations to identify their specific risks and implement controls tailored to those risks. This is especially important in healthcare, where threats can range from ransomware attacks on electronic health record (EHR) systems to unauthorized access through connected medical devices. By focusing on the most pressing vulnerabilities, organizations can ensure their resources are used effectively.
The framework addresses risks tied to protected health information (PHI) and EHR systems, medical devices and IoT equipment, third-party vendors, and supply chains. For instance, data classification controls help differentiate PHI from other data types, ensuring that encryption, access controls, and logging are applied where they’re most needed. Network segmentation and vulnerability management protect devices like patient monitors and imaging systems from cyber threats. Meanwhile, asset management tracks devices that handle sensitive information, and change management ensures that system updates don’t inadvertently create new risks within clinical workflows.
This risk-based approach serves as the foundation for the operational controls detailed in ISO 27001’s key clauses.
Key ISO 27001 Clauses for Healthcare Organizations
Several clauses in ISO 27001 directly influence day-to-day hospital operations. Clause 4 (context of the organization) focuses on defining the scope of the information security management system (ISMS). Hospitals must document which systems store PHI, pinpoint dependencies within clinical workflows, and list connected medical devices. This often includes EHR platforms, PACS imaging archives, billing systems, patient portals, and telehealth infrastructure. Relevant U.S. regulations like HIPAA, HITECH, and state privacy laws must also be accounted for.
Clause 5 (leadership and roles) emphasizes accountability by involving key stakeholders like CIOs, CISOs, Chief Medical Officers, nursing leaders, compliance teams, and biomedical engineers in ISMS governance. Clause 6.1 (risk assessment and treatment) makes the framework actionable by requiring risk assessments that evaluate threats based on their potential impact on patient care and data security. Lastly, Clause 10 (improvement) ensures that incidents prompt corrective actions. For example, if a phishing attack occurs, the response might include enhanced staff training, updated email filters, and revised risk scores for the affected systems, with all changes being tracked and reviewed over time.
These clauses not only guide operational protocols but also align with U.S. healthcare requirements.
How ISO 27001 Aligns with U.S. Healthcare Regulations
ISO 27001 offers a structured framework that complements the HIPAA Security Rule’s requirements for administrative, physical, and technical safeguards. While HIPAA sets the baseline for these safeguards, it doesn’t provide detailed implementation guidance. ISO 27001 fills that gap by offering clear methodologies for risk assessment, treatment, and continuous monitoring. This alignment helps healthcare organizations stay compliant with U.S. regulations, reducing the risk of OCR penalties and lowering the costs of breach remediation through auditable and systematic risk management practices.
Healthcare Risk Areas Covered by ISO 27001
ISO 27001’s controls address some of the most critical vulnerabilities in healthcare. For PHI and EHR systems, the standard ensures robust protection through data classification, encryption, and controlled access. Medical devices and IoT equipment - like infusion pumps, patient monitors, and imaging systems - are safeguarded through asset management, network segmentation, and vulnerability management. Third-party vendors and supply chains also receive special attention, with dedicated risk assessments required for business associates handling PHI. Tools like Censinet RiskOps™ support secure data sharing, simplify vendor risk evaluations, and enable continuous monitoring across healthcare networks [1].
Key Features of ISO 27001 Tools for Healthcare Risk Management
Healthcare organizations rely on ISO 27001-compliant tools to simplify and automate the complex, often manual processes involved in managing risks. These tools centralize data, streamline workflows, and provide continuous oversight - essential for safeguarding sensitive systems like EHR platforms, medical devices, and third-party vendor networks. With the average cost of a healthcare data breach in the U.S. surpassing $10 million in 2023, according to IBM's Cost of a Data Breach Report [3], having a strong, automated risk management system in place is no longer optional. Below are the standout features that these tools bring to the table.
Centralized Risk Register and Asset Inventory
One of the most impactful features is a centralized risk register that consolidates all critical assets into a single, searchable database. This includes systems like EHR platforms, PACS imaging systems, infusion pumps, patient monitors, billing software, and third-party vendors. Each asset is continuously mapped to its associated threats, vulnerabilities, and controls, creating a dynamic and up-to-date record. This eliminates the frustrating need to sift through spreadsheets or email threads to find out which systems handle PHI, which vendors have access to sensitive data, or which medical devices need urgent patching.
Tower Health's CISO, Terry Grogan, shared, "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." [1]
Automated Risk Assessment and Treatment Workflows
These tools take centralized data a step further by automating the risk assessment and treatment process. They streamline tasks like identifying risks, analyzing their severity, and determining the appropriate treatments. Configurable workflows and forms ensure that risk scoring is consistent, using standardized criteria for likelihood and impact that align with ISO 27001 and HIPAA requirements. Additional features like task delegation, approval tracking, and built-in commentary make it easier to move from identifying a problem to implementing a solution.
Baptist Health's VP & CISO, James Case, noted, "Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." [1]
Continuous Monitoring and Evidence Collection
Beyond risk registers and automated workflows, continuous monitoring tools provide real-time visibility into high-risk areas. Dashboards track critical assets handling PHI, overdue risk treatments, and recurring control failures, giving organizations a clear picture of their risk landscape. Automated evidence collection further supports compliance efforts by organizing security questionnaires, documentation, and audit trails - all essential for ISO 27001 and HIPAA audits.
Faith Regional Health's CIO, Brian Sterud, emphasized, "Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." [1]
These dashboards also support regular management reviews, enabling leadership to focus on the most pressing risks to patient care and data security. By keeping everything centralized and automated, these tools help healthcare organizations stay ahead of potential threats while ensuring compliance with stringent regulations.
How to Implement ISO 27001 Tools in Healthcare: A Step-by-Step Guide
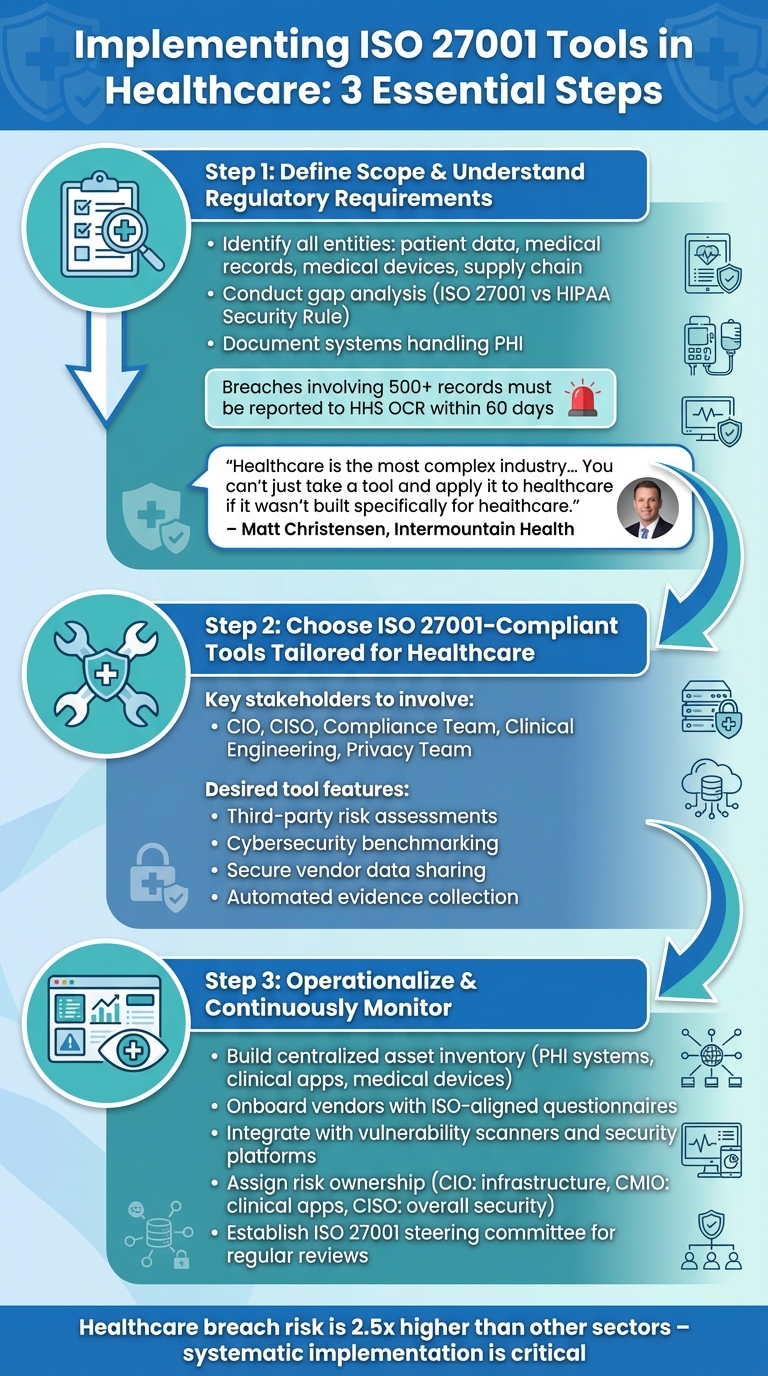
3-Step Implementation Guide for ISO 27001 Tools in Healthcare
Bringing ISO 27001 tools into the healthcare sector requires a methodical approach, tailored to the industry's unique challenges. With healthcare experiencing a breach risk 2.5 times higher than other sectors [2], it’s crucial to implement tools that meet both ISO 27001 standards and U.S. healthcare regulations like HIPAA. Here’s a practical guide to help you navigate this process.
Step 1: Define Scope and Understand Regulatory Requirements
Start by identifying all entities that fall within the scope of your implementation. This includes patient data, medical records, research information, medical devices, and supply chain components - anything critical to operations and patient safety. Conduct a gap analysis to measure your current controls against ISO 27001 standards and the HIPAA Security Rule.
Document which systems handle protected health information (PHI), what clinical and business applications are in use, and which networked devices are connected to your infrastructure. Keep in mind, breaches involving 500 or more records must be reported to the Department of Health and Human Services (HHS) Office for Civil Rights (OCR) within 60 days [3].
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." – Matt Christensen, Sr. Director GRC, Intermountain Health [1]
Once you've outlined your scope and pinpointed gaps, focus on finding tools specifically designed for healthcare environments.
Step 2: Choose ISO 27001-Compliant Tools Tailored for Healthcare
Select tools that are purpose-built for healthcare. Bring together key stakeholders - such as your CIO, CISO, Compliance team, Clinical Engineering team, and Privacy team - to ensure the tools align with clinical workflows and regulatory needs. Look for platforms that simplify third-party and enterprise risk assessments, provide cybersecurity benchmarking, and enable secure sharing of risk data with vendors and partners.
For instance, tools like Censinet RiskOps automate evidence collection and standardize security questionnaires, making compliance more manageable. Additionally, prioritize solutions that can adapt to changes in your organization’s resources, budget, and workforce while maintaining strong risk management capabilities.
Step 3: Operationalize and Continuously Monitor Risk Management
After selecting a tool, configure it to reflect your specific risk landscape. Build a centralized asset inventory that encompasses all systems handling PHI, clinical and business applications, and networked medical devices. Onboard vendors and partners using ISO-aligned questionnaires and required documentation.
Set up continuous monitoring by integrating the tool with vulnerability scanners, configuration management systems, and security monitoring platforms to gather real-time data on control statuses. Assign clear risk ownership: for example, the CIO can oversee infrastructure, the CMIO can manage clinical applications, and the CISO can handle overall security. Risk owners should validate risks, approve mitigation strategies, and track remediation progress.
Finally, establish an ISO 27001 steering committee or ISMS governance board. This group should regularly review reports on top risks, overdue treatments, and trends in control effectiveness. By doing so, risk management becomes a continuous, embedded practice rather than a one-time initiative.
sbb-itb-535baee
Getting the Most from ISO 27001 Tools in Healthcare
ISO 27001 tools can be powerful assets in healthcare, but their true value comes when they’re tailored to the unique demands of clinical environments. Here’s how to make these tools work effectively within healthcare operations.
Align Tools with Healthcare Workflows
To get the best results, your ISO 27001 tool should mirror the day-to-day operations of healthcare workflows. This means syncing risk categories and asset inventories with key clinical processes like EHR usage, patient intake, telehealth sessions, medication administration, and even medical device networks. Generic IT frameworks often miss the complexities of patient care, so customization is critical.
Bring together clinical staff, operations teams, and engineering experts when setting up the tool. Their insights are essential for creating impact scales and treatment thresholds that focus on critical areas like patient harm, care delays, and PHI exposure, rather than just data breaches. For example, document how controls such as access management, encryption, and audit logging protect PHI across systems like EHRs, PACS, lab systems, and cloud services. The closer the tool aligns with real workflows, the easier it becomes for staff to incorporate it into their daily routines.
Integrate ISO 27001 Tools with Existing Processes
Don’t let risk management efforts run in silos. Instead, integrate your ISO 27001 tool with processes already in place, like the HIPAA Security Rule risk analysis. This approach consolidates risks into a single register, reducing duplication and streamlining operations.
Tie the tool into your incident response processes so that security incidents are automatically logged, root causes are tracked, and corrective actions are linked to specific risks. Similarly, connect it with change management workflows to ensure that new EHR modules, medical devices, or vendor onboarding trigger automatic risk reviews and control updates. Many healthcare organizations have successfully eliminated manual, spreadsheet-based risk assessments by adopting such integrations, freeing up staff time while improving accuracy.
Use Automation and Benchmarking with Human Oversight
Once your tools are aligned and integrated, automation can help lighten the load - but it’s no substitute for human expertise. Use features like automated risk scoring and evidence collection to handle repetitive tasks efficiently. However, make sure that experienced professionals review risks related to patient safety, critical clinical workflows, or regulatory compliance to ensure nothing is overlooked.
Leverage benchmarking tools to measure your cybersecurity posture against industry standards. This data can help justify funding for necessary resources and guide long-term strategies. As Brian Sterud, CIO at Faith Regional Health, puts it:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters" [1].
Regularly review dashboards and reports with leadership to translate automated insights into actionable strategies. By pairing automation with expert judgment, healthcare organizations can continuously improve their security posture while staying focused on patient care.
Conclusion
ISO 27001 offers U.S. healthcare organizations a proactive, risk-based framework that surpasses the baseline requirements of HIPAA. By implementing ISO 27001-compliant tools, healthcare leaders can address risks that jeopardize patient safety, protected health information (PHI), and essential clinical operations. The numbers tell a stark story: in 2023 alone, 725 major healthcare data breaches impacted over 133 million individuals, with the average cost of a breach exceeding $10 million [3]. These statistics highlight the critical need for effective and forward-thinking risk management strategies.
The right tools make managing these risks more straightforward by providing centralized oversight, automation, and continuous monitoring. Designed to integrate seamlessly with healthcare workflows, these platforms replace outdated, manual processes - like spreadsheet tracking - while boosting both efficiency and accuracy.
Censinet RiskOps™ stands out as a solution tailored specifically for healthcare's complexities, aligning with ISO 27001 standards. As Matt Christensen, Sr. Director GRC at Intermountain Health, explains:
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." [1]
Tower Health serves as a compelling example of this tailored approach in action. By leveraging the right tools, they increased their risk assessment capacity while reducing staffing needs - from 5 full-time employees to just 2 - without compromising quality.
Whether you're a CIO, CISO, compliance officer, or clinical leader, the path forward is clear: define your scope, choose tools built for healthcare's unique demands, and operationalize risk management processes that prioritize patient care. By continuously refining these efforts, healthcare organizations not only protect patients but also establish strong, resilient defenses against cyber threats. ISO 27001-aligned platforms provide more than just operational efficiency - they deliver strategic benefits like industry benchmarking, executive support for resources, and demonstrable risk maturity that resonates with regulators, partners, and patients alike.
FAQs
How do ISO 27001 tools help healthcare organizations comply with HIPAA regulations?
ISO 27001 tools provide healthcare organizations with a systematic way to meet HIPAA requirements while managing and safeguarding sensitive patient data. These tools assist in critical areas, such as performing regular risk assessments, establishing strong security protocols, and keeping an eye out for potential threats through continuous monitoring.
By following the ISO 27001 framework, healthcare providers can strengthen the protection of Protected Health Information (PHI), improve data privacy practices, and stay compliant with HIPAA's stringent privacy and security standards.
What healthcare risks does ISO 27001 help manage?
ISO 27001 plays a crucial role in helping healthcare organizations tackle risks associated with sensitive patient data, such as protected health information (PHI). It extends its reach to cover clinical applications, medical devices, and even supply chains. Additionally, it addresses cybersecurity challenges that could disrupt operations or jeopardize patient safety.
By adopting ISO 27001-compliant tools, healthcare providers can strengthen data protection, simplify risk assessment processes, and meet regulatory standards. This not only protects patient information but also helps maintain the organization's credibility and trust.
What are the best steps for healthcare organizations to implement ISO 27001 tools effectively?
Healthcare organizations can make the most of ISO 27001 tools by adopting a structured plan that addresses the specific needs and challenges of the healthcare sector. Begin by defining the scope of your risk management efforts and identifying key assets such as patient records, clinical systems, and medical devices. Leveraging tools designed specifically for healthcare can help simplify risk assessments, automate compliance tasks, and maintain continuous monitoring.
For example, solutions like Censinet RiskOps™ are built to integrate seamlessly into existing workflows. They offer benchmarking data to guide better decision-making and promote collaborative risk management. Engaging key stakeholders and fostering open communication throughout the process ensures these tools are used effectively. This approach not only strengthens compliance but also enhances security in a highly regulated industry.


