ISO 27001 vs HIPAA: Incident Response Differences
Post Summary
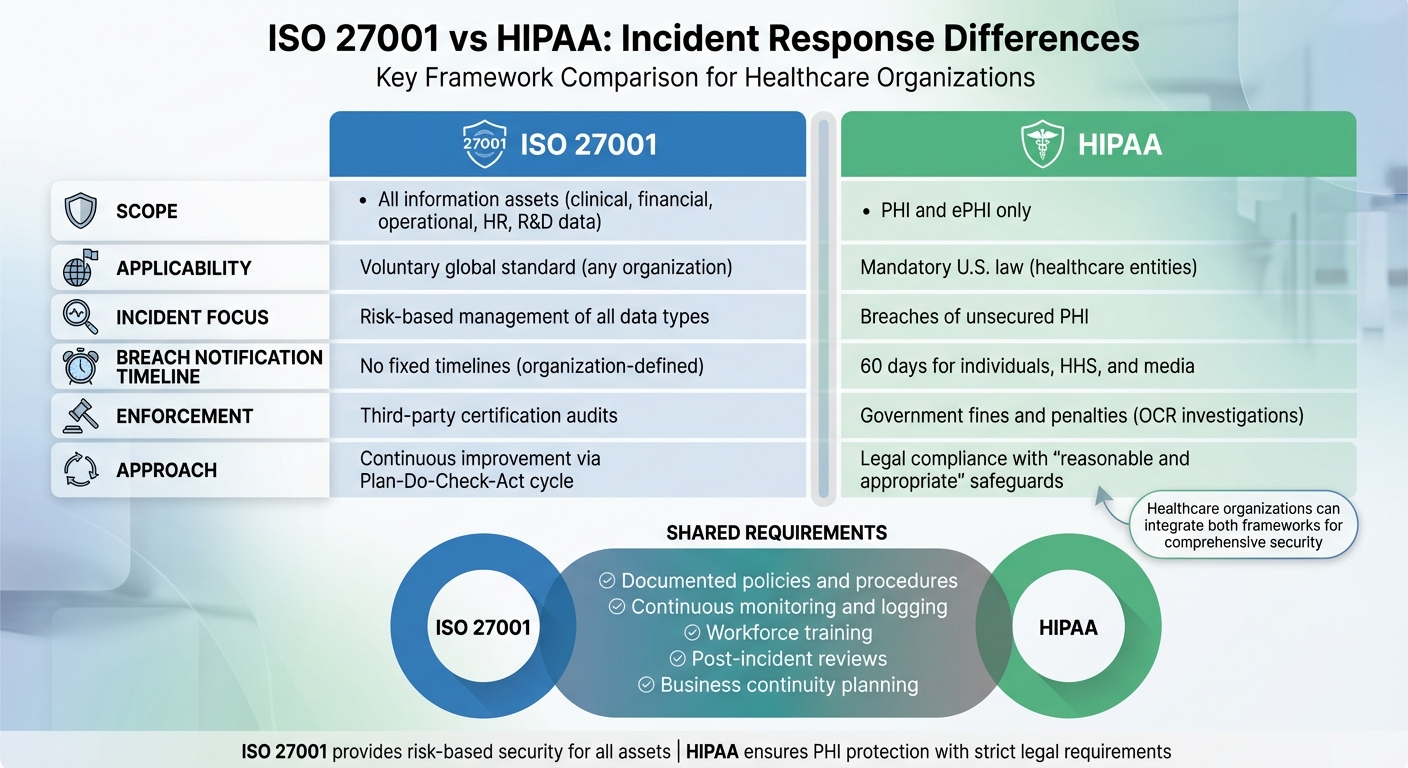
ISO 27001 and HIPAA are two frameworks often used by healthcare organizations to manage data security. While HIPAA is a U.S. federal law focused on protecting Protected Health Information (PHI) with strict breach notification rules, ISO 27001 is an international standard that manages risks across all types of information assets. The key difference lies in their scope and enforcement: HIPAA mandates compliance with legal penalties for breaches, while ISO 27001 focuses on a risk-based, voluntary approach to improving overall security practices.
Key Points:
- HIPAA: Focuses exclusively on PHI and enforces strict breach notification timelines (e.g., notify affected individuals within 60 days of a breach).
- ISO 27001: Covers all information assets, including financial, clinical, and operational data. It emphasizes continuous improvement through a structured process but does not enforce breach notification timelines.
- Both require documented incident response plans, workforce training, and post-incident reviews.
- HIPAA penalties are legal and financial, while ISO 27001 compliance is validated through third-party certification.
Quick Comparison:
| Aspect | ISO 27001 | HIPAA |
|---|---|---|
| Scope | All information assets | PHI and ePHI only |
| Applicability | Voluntary, global standard | Mandatory for U.S. healthcare entities |
| Incident Focus | Risk-based management of all data | Breaches of unsecured PHI |
| Notification | No fixed timelines; organization-defined | 60 days for individuals, HHS, and media |
| Enforcement | Certification audits | Government-imposed fines and penalties |
ISO 27001 vs HIPAA Incident Response Requirements Comparison
ISO 27001: Incident Response Requirements
After setting the stage with the overall framework, let’s explore ISO 27001’s specific incident response requirements. Incident response is a key component of ISO 27001’s Information Security Management System (ISMS), operating within a Plan–Do–Check–Act (PDCA) cycle. This means that incident management is not a one-off activity - it’s a continuous process of planning, execution, monitoring, and improvement, integrated with other security processes. This approach ensures that every security event - whether it involves sensitive patient data, financial records, or operational technology - is managed with precision and contributes to the organization’s broader risk management and business continuity planning.
Key Clauses and Controls for Incident Response
ISO 27001 embeds incident response requirements throughout its clauses and Annex A controls:
- Clause 8 (Operation): Organizations must plan, implement, and control operational processes, including formal incident management procedures.
- Clause 9 (Performance Evaluation): Emphasizes the importance of tracking and measuring incident metrics - like detection and containment times - and conducting internal audits on how incidents are handled.
- Clause 10 (Improvement): Requires organizations to use lessons learned from incidents, nonconformities, and corrective actions to refine and improve the ISMS.
Annex A controls outline specific practices, including logging and monitoring security events, ensuring timely reviews, setting up clear reporting channels, and managing incidents through containment, eradication, recovery, and communication. Post-incident reviews are also critical, as is preserving evidence for potential legal or forensic needs. Additionally, organizations must ensure business continuity during major incidents and include incident notification requirements in vendor contracts. This integrated approach forms the backbone of the operational practices we’ll discuss further.
Formal Processes and Roles
ISO 27001 places significant emphasis on having structured processes and clearly defined roles for incident response. Organizations are required to document procedures for every phase of incident management - detection, logging, reporting, triage, containment, eradication, recovery, and post-incident reviews. These procedures must include lessons learned to avoid repeating mistakes.
Roles like incident manager, communications lead, legal/privacy officer, and technical responders must be clearly defined and documented within the ISMS. To support these roles, organizations should develop playbooks for common scenarios, such as compromised credentials, lost devices, or cloud misconfigurations. These playbooks are tied to Annex A controls and the risk register, ensuring alignment with the organization’s broader security strategy.
Training is another critical requirement. All staff should be trained to recognize and report incidents quickly, while incident responders need specialized training and the authority to act decisively. For example, whether it’s a phishing email targeting hospital staff or a misconfigured cloud database exposing research data, ISO 27001 ensures that the response is swift, coordinated, and well-documented.
Scope Beyond PHI
Unlike HIPAA, which focuses on protecting PHI and ePHI, ISO 27001 applies to all information assets within the defined ISMS scope. This means incident response must address any security event that threatens the confidentiality, integrity, or availability of those assets. In healthcare, this broad scope includes not just clinical applications and electronic health records (EHRs) but also scheduling systems, billing data, research datasets, HR and payroll systems, proprietary healthtech software, analytics data, intellectual property, and even operational technology like networked medical devices and building systems.
ISO 27001 also requires organizations to maintain a comprehensive asset inventory and classification. Incident data - such as frequency, severity, and root causes - feeds back into the risk register and business impact analyses, influencing future risk treatment decisions and business continuity strategies. This feedback loop enhances the organization’s overall security posture, extending well beyond PHI-specific compliance.
In the healthcare context, ISO 27001 can also demonstrate a "good faith effort" to meet HIPAA’s Security Rule requirements. Regulators may view this as a mitigating factor in the event of a PHI breach, offering an additional layer of assurance for organizations aiming to align with both standards.
HIPAA: Incident Response and Breach Notification
HIPAA takes a targeted approach to protecting electronic Protected Health Information (ePHI), emphasizing quick incident response and strict breach notification requirements. The Security and Breach Notification Rules are designed to ensure that any compromise of ePHI is identified, managed, and disclosed within specific timeframes. For healthcare organizations, this means having robust systems in place to protect patient data while meeting legal obligations to avoid federal scrutiny and hefty penalties.
Security Rule: Incident Response Procedures
Under HIPAA's Security Rule, covered entities and business associates must create security incident procedures to address and respond to potential or confirmed incidents involving ePHI. A "security incident" includes any attempted or successful unauthorized access, use, disclosure, modification, or destruction of information, or interference with system operations.[3] This broad definition even covers failed attempts, such as blocked phishing emails or denied logins from suspicious locations, which must be logged and assessed.
To comply, organizations need an incident response plan that outlines detection, reporting, and mitigation strategies. This includes monitoring ePHI systems, reporting suspicious activities through pre-established channels, and implementing containment, mitigation, and post-incident reviews.[3][5] Many healthcare organizations align their procedures with NIST SP 800-61, following phases like preparation, detection, containment, eradication, recovery, and lessons learned.
Training the workforce is crucial. Employees must be able to recognize and report incidents, whether it's a lost device with patient records, a ransomware alert, or a misdirected email containing sensitive information. To streamline responses, organizations often develop playbooks that clearly define roles and actions for common scenarios.[6]
These detection and containment measures are just the beginning. HIPAA also enforces specific breach notification rules that organizations must follow.
Breach Notification Rule: Timelines and Obligations
Once an incident is detected, HIPAA's Breach Notification Rule outlines precise steps and deadlines for reporting breaches. A breach refers to the impermissible use or disclosure of unsecured PHI that compromises its security or privacy, with certain exceptions (such as unintentional access by an employee acting in good faith).[5] "Unsecured PHI" means data that hasn’t been made unreadable or unusable through encryption or similar methods.[2][3]
To determine whether a notification is required, organizations must conduct a documented four-factor risk assessment that evaluates:
- The type and extent of PHI involved, including identifiers and the risk of re-identification.
- The unauthorized person who accessed or received the PHI.
- Whether the PHI was actually acquired or viewed.
- The extent to which the risk has been mitigated (e.g., retrieving a lost device or confirming encryption).[5]
If the assessment doesn’t show a low probability that the PHI was compromised, the incident is presumed to be a reportable breach.
Once confirmed, strict timelines apply. Organizations must notify affected individuals within 60 calendar days of discovering the breach.[5] Notifications, typically sent via first-class mail or email (if agreed upon), must include:
- A summary of what happened.
- The types of PHI involved.
- Steps individuals can take to protect themselves.
- Actions the organization is taking to investigate and mitigate the breach.
- Contact details for further questions.[2][3]
For breaches impacting 500 or more individuals, additional steps are required. Organizations must notify prominent media outlets and the HHS Office for Civil Rights (OCR) within 60 days of discovery.[2][3] Smaller breaches, affecting fewer than 500 individuals, must be logged and reported to HHS within 60 days after the calendar year ends.[2][3] Even minor incidents demand detailed documentation and tracking.
Healthcare entities must maintain thorough records to demonstrate compliance, including:
- Incident and breach notification policies.
- Logs and investigation records.
- Documented four-factor risk assessments.
- Copies of notifications sent to individuals and HHS.
- Evidence of corrective actions and workforce training.[5][3]
This documentation is critical during OCR investigations, which often follow reported breaches and can lead to severe penalties if procedures or notifications fall short.[1][2]
Role of Business Associates
Business associates (BAs) - such as vendors and contractors handling PHI - are vital to HIPAA compliance. Business Associate Agreements (BAAs) must clearly outline how security incidents and breaches involving PHI will be reported and managed between the parties.[3][4] These agreements require BAs to adopt HIPAA-compliant incident procedures and immediately report breaches of unsecured PHI.[4]
While covered entities usually handle notifications to individuals, HHS, and media, BAAs often specify timelines for BAs to report breaches - typically within 24 to 48 hours of discovery. BAs must notify covered entities of breaches, including details about affected individuals, within 60 days of discovery.[3]
To overcome challenges like limited visibility into covered entities' environments or ambiguous BAA language, BAs should:
- Negotiate BAAs with clear definitions of "security incident" and "breach."
- Establish specific internal notification timelines.
- Share logs and forensic data as needed.
BAs should also implement standardized incident response plans that can scale across clients and ensure subcontractors follow equivalent contractual obligations. Tools like Censinet RiskOps™ can help manage incidents, risk assessments, and compliance across multiple entities and vendors.
Key Differences and Overlaps: ISO 27001 vs HIPAA
While both ISO 27001 and HIPAA emphasize the importance of robust incident response, they differ significantly in their focus, enforcement mechanisms, and methodologies. HIPAA is a U.S. federal law designed to protect PHI (Protected Health Information) and ePHI (electronic Protected Health Information), with strict breach notification requirements and government-imposed penalties. ISO 27001, on the other hand, is a voluntary international standard that applies to all types of information assets across any industry. It is enforced through certification audits rather than regulatory fines.
Comparison Table: ISO 27001 vs HIPAA
| Dimension | ISO 27001 | HIPAA |
|---|---|---|
| Scope | Covers all information assets, including clinical, financial, R&D, HR, and operational data | Focuses exclusively on PHI and ePHI within U.S. healthcare entities and their business associates |
| Applicability | Voluntary global standard; open to adoption by any organization | Mandatory U.S. law for healthcare entities handling PHI |
| Incident Definition | Addresses security incidents affecting any asset within the ISMS | Focuses on security incidents involving ePHI; mandates notification for breaches of unsecured PHI |
| Breach Notification | No fixed timelines; organizations set processes based on legal and contractual obligations | Requires notification within 60 days; includes notifying individuals, HHS, and media for large breaches |
| Enforcement | Certification audits by third parties; noncompliance risks loss of certification and reputation | Investigations by HHS OCR; penalties include fines, corrective actions, and possible criminal charges |
| Approach | Risk-based, focusing on continuous improvement through the Plan-Do-Check-Act cycle | Legal compliance requiring "reasonable and appropriate" safeguards for PHI |
This table highlights the primary differences, but it’s important to note that both frameworks share key principles when it comes to incident response.
Overlapping Requirements
Despite their differences, ISO 27001 and HIPAA share several common requirements. Both frameworks emphasize the need for:
- Documented policies and procedures
- Continuous monitoring and logging
- Post-incident reviews to improve controls
ISO 27001 integrates these activities into its continuous improvement cycle, while HIPAA’s Security Rule mandates ongoing risk analysis and evaluation, which naturally encourages similar practices. For organizations managing both frameworks, aligning efforts can simplify compliance. A single incident response program can be designed to satisfy HIPAA’s legal obligations for PHI while extending ISO 27001’s structured management to all information assets. This unified approach minimizes duplication, ensures consistent documentation, and strengthens the organization’s overall security posture.
Key Differences in Approach
While there are overlaps, the operational approaches of these frameworks diverge in critical ways. HIPAA enforces strict deadlines for breach notifications - affected individuals, HHS, and, in some cases, the media must be notified within 60 days of a breach. Noncompliance can lead to monetary penalties, corrective action plans, or even criminal charges. ISO 27001, in contrast, does not impose external notification timelines or government fines. Instead, it requires organizations to establish and follow their own incident handling procedures based on risk, legal obligations, and stakeholder needs. These procedures are then evaluated during certification audits.
For U.S. healthcare organizations, HIPAA serves as the mandatory baseline for protecting patient data. ISO 27001 provides a broader, risk-based framework that extends beyond PHI to include all information assets. By treating HIPAA as the foundation, healthcare entities can use ISO 27001’s continuous improvement model to enhance their overall security practices. This includes refining detection capabilities, conducting tabletop exercises, and tracking incident metrics like mean time to detect and contain threats.
sbb-itb-535baee
Integrating ISO 27001 and HIPAA for Healthcare Incident Response
Designing a Unified Program
Creating an incident response program that satisfies both ISO 27001 and HIPAA requirements starts with an ISMS-based approach. Prioritize PHI and ePHI as high-risk assets in your risk register, accounting for HIPAA-specific threats like unauthorized access and data integrity issues. Your policies and playbooks should follow ISO 27001's structured documentation, while incorporating HIPAA's unique elements: workflows for breach determination, "low probability of compromise" analyses, 60-day federal notification deadlines, and OCR documentation protocols.
Assign an ISO 27001 security manager to oversee incident response governance, ensuring this role aligns with HIPAA's security officer and privacy officer responsibilities. Use a RACI matrix to define roles and responsibilities clearly, and conduct regular tabletop exercises to test and refine your response plans. For business associates, combine ISO 27001's supplier security controls with HIPAA's Business Associate Agreement (BAA) requirements, ensuring incident reporting obligations and timelines are detailed in contracts. Leverage ISO 27001's Plan-Do-Check-Act cycle to continuously improve procedures after each exercise.
Using Technology for Compliance
Technology plays a critical role in executing a unified incident response strategy. Modern healthcare platforms simplify the challenge of managing both ISO 27001 and HIPAA frameworks. Censinet RiskOps™ is one example that centralizes third-party and enterprise risk assessments, incident tracking, and remediation efforts across clinical systems, medical devices, and supply chain vendors. It standardizes patient data risk evaluations, maps ISO 27001 controls to HIPAA safeguards, automates evidence collection, and maintains a consolidated risk register.
Terry Grogan, CISO at Tower Health, shared that using Censinet RiskOps™ allowed 3 full-time equivalent (FTE) employees to return to their primary roles, while the organization increased its capacity for risk assessments with only 2 FTEs.
James Case, VP & CISO at Baptist Health, noted: "Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with."
These collaborative tools enable covered entities and vendors to coordinate better during incident handling, reducing manual workloads and enhancing documentation quality for ISO 27001 audits and HIPAA investigations. This integration reduces redundancy and improves overall efficiency in incident response.
Reducing Duplication and Improving Readiness
A unified approach streamlines processes, eliminating redundancies and strengthening security measures. By integrating HIPAA decision points into ISO 27001-based playbooks, logs, and vendor management workflows, organizations can manage incidents more effectively. For example, tracking Business Associate Agreements alongside ISO 27001 supplier risk assessments in a single system simplifies vendor oversight and reduces fragmentation.
This alignment also accelerates response times. Embedding HIPAA's PHI-focused considerations within ISO 27001's risk-based impact matrix allows security teams to quickly determine whether an incident meets breach notification thresholds while assessing broader risks to the organization. Entities that adopt systematic, ISMS-based programs typically manage PHI breaches more effectively, which can positively influence OCR investigation outcomes. Treating HIPAA as the baseline and extending ISO 27001's continuous improvement model across all information assets enhances resilience and prepares healthcare organizations for audits and investigations.
Conclusion
ISO 27001 provides a risk-based framework for managing the security of all information assets, while HIPAA focuses specifically on safeguarding Protected Health Information (PHI) with strict breach reporting timelines. HIPAA serves as the regulatory foundation for PHI protection, whereas ISO 27001 offers a more expansive set of best practices that can bolster an organization’s overall security measures.
The two frameworks share common ground, such as the need for documented policies, regular risk assessments, workforce training, and business continuity planning. By aligning these frameworks, healthcare organizations can create a more cohesive and efficient response strategy. This unified approach helps reduce response times, streamline vendor management through consistent Business Associate Agreements, and meet HIPAA’s reporting deadlines while benefiting from ISO 27001’s emphasis on continuous improvement. According to the HIPAA Journal, implementing an ISO 27001 Information Security Management System (ISMS) can demonstrate a “good faith effort” to comply with the HIPAA Security Rule, which may result in more favorable outcomes during breach investigations. However, it’s important to recognize that HIPAA alone is not a comprehensive cybersecurity strategy. It provides a baseline that must be supplemented with proactive, risk-based controls to address emerging threats across clinical operations, medical devices, and supply chains. Combining these frameworks strengthens incident preparedness and reduces both regulatory and reputational risks.
By leveraging the complementary strengths of ISO 27001 and HIPAA, U.S. healthcare leaders can not only meet legal requirements but also build a robust and auditable security program that safeguards patient data. Tools like Censinet RiskOps™ can help centralize risk management activities, including assessments, incident tracking, and vendor oversight, across systems handling PHI, clinical applications, and medical devices - making it easier to implement both frameworks effectively.
To get started, healthcare organizations should map ISO 27001 controls to HIPAA requirements, integrate breach assessment workflows into their incident response plans, and use the Plan-Do-Check-Act cycle to continuously refine their processes. This integrated approach provides stronger protection for the patient data that is central to every healthcare mission.
FAQs
How does ISO 27001 support HIPAA compliance for healthcare organizations?
ISO 27001 plays a key role in supporting HIPAA compliance by providing a clear framework for managing information security risks. It focuses on ongoing risk assessments, creating robust incident response plans, and implementing security controls that align with HIPAA's requirements for protecting patient data.
For healthcare organizations, adopting ISO 27001 can strengthen HIPAA compliance efforts by encouraging better security practices, enabling quicker detection and response to incidents, and fostering a culture of heightened security awareness. This structured approach ensures sensitive information, such as Protected Health Information (PHI), remains safeguarded while maintaining consistent and effective risk management processes.
How do incident response timelines differ between ISO 27001 and HIPAA?
ISO 27001 takes a forward-thinking stance on handling security incidents, requiring organizations to act within 24 hours of an incident. This includes having a formal incident response plan ready to go, along with ongoing monitoring and management to address issues as they arise.
HIPAA, however, zeroes in on breach reporting timelines. If a breach impacts 500 or more individuals, HIPAA mandates that notifications must be sent out within 60 days of discovering the breach. This timeframe allows for investigation, notifying affected individuals, and reporting the incident to the Department of Health and Human Services (HHS). For smaller breaches, the reporting requirements may differ.
While both standards stress the importance of timely action, ISO 27001 leans heavily on immediate response and management, whereas HIPAA puts more weight on structured breach reporting and ensuring affected individuals are informed within the set deadlines.
What makes ISO 27001's risk-based approach more adaptable than HIPAA's compliance requirements?
ISO 27001 adopts a risk-focused strategy for security, prioritizing the identification and management of threats unique to an organization. Instead of strictly adhering to predefined standards like HIPAA, it emphasizes creating custom controls and making ongoing adjustments to address shifting risks.
On the other hand, HIPAA centers around compliance with specific regulations aimed at safeguarding patient data. In contrast, ISO 27001 encourages continuous evolution of security practices, allowing organizations to adapt to emerging challenges and technologies. This makes it a strong choice for businesses looking for a more adaptable and thorough way to handle risks.


