NIST Framework for Healthcare Supply Chain Security
Post Summary
It guides healthcare organizations in identifying, protecting, detecting, responding to, and recovering from supply chain threats.
Vendor breaches can disrupt clinical operations, compromise PHI, and halt essential patient care.
New governance controls for SCRM, clearer supplier prioritization, and stronger enterprise accountability.
By performing risk assessments, enforcing technical controls, using SBOMs, and monitoring vendors continuously.
SP 800‑161, HIC‑SCRiM, HPH guidance, and NCCoE reference architectures.
It automates NIST‑aligned vendor assessments, enables continuous monitoring, and centralizes supply chain risk data.
The NIST Cybersecurity Framework (CSF) is a critical tool for healthcare organizations to address growing cybersecurity risks in supply chains. It provides a structured, flexible approach to managing threats across vendors, devices, and systems, ensuring patient safety and operational stability. Key takeaways include:
Healthcare organizations can use NIST guidelines and resources like the HIC-SCRiM Guide and tools like Censinet RiskOps™ to streamline processes, reduce risks, and enhance security across their supply chains.
NIST Framework Functions for Healthcare Supply Chains
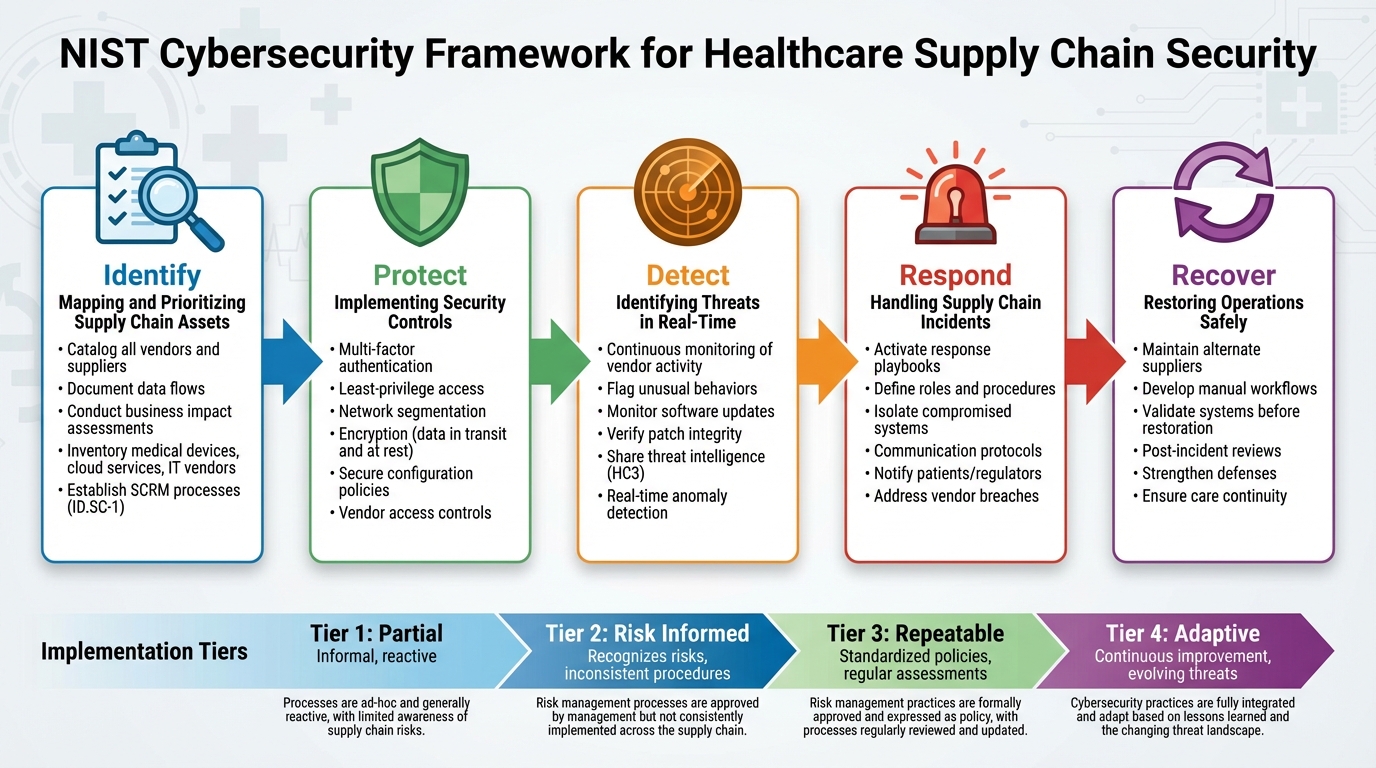
NIST Framework Five Core Functions for Healthcare
The NIST Framework provides a structured approach to securing supply chains, breaking the process into five core functions. These functions guide healthcare organizations in managing risks, from identifying critical assets to recovering from potential incidents. For healthcare systems handling complex vendor networks, this framework offers a clear way to minimize risks while ensuring smooth operations.
Identify: Mapping and Prioritizing Supply Chain Assets
The Identify function focuses on creating a comprehensive map of the supply chain. This involves cataloging vendors, documenting data flows, and assessing the importance of each supplier. For example, healthcare organizations must inventory items like medical devices, cloud service providers, pharmaceutical suppliers, and IT vendors that handle sensitive health data.
Conducting business impact assessments is key to determining which vendors pose the highest risks. For instance, a vendor managing infusion pump software would be considered more critical than one supplying office materials. NIST emphasizes the need to audit the entire business environment and understand dependencies across the supply chain lifecycle.
The ID.SC-1 control specifically requires healthcare organizations to establish supply chain risk management (SCRM) processes agreed upon by all stakeholders. This includes documenting every stage of vendor interaction - onboarding, monitoring, and offboarding - with clear accountability.
Once assets are identified and prioritized, the next step is to implement measures to protect them.
Protect: Implementing Security Controls
The Protect function ensures that vendors have limited and secure access to systems. Measures like multi-factor authentication, least-privilege access, and network segmentation prevent unauthorized movement within systems.
Encryption plays a crucial role in safeguarding data both in transit and at rest. Even if a vendor's system is compromised, encryption ensures that sensitive patient information remains secure. Additionally, secure configuration policies establish baseline security settings for all vendor-provided devices and software.
Segmenting the supply chain is another essential strategy. By creating boundaries between vendor systems and internal networks, organizations can contain breaches before they spread. The NIST National Cybersecurity Center of Excellence (NCCoE) offers guidance on addressing vulnerabilities in areas such as genomic data systems, telehealth platforms, medical imaging, and infusion pumps. Tools like firewalls and network segmentation, based on vendor criticality, further enhance protection.
Detect: Identifying Threats in Real-Time
The Detect function focuses on spotting issues as they arise. Continuous monitoring tools track vendor activity, flagging unusual behaviors such as odd access times, unexpected system changes, or abnormal login patterns. Real-time data from devices and vendor systems strengthens threat detection efforts.
Monitoring software updates is especially critical, as attackers often target supply chains by slipping malware into legitimate updates. Healthcare organizations should verify the integrity of all vendor-supplied patches before deployment. This includes checking digital signatures, testing updates in isolated environments, and monitoring for changes post-installation.
Collaboration is another key component. Sharing threat intelligence through initiatives like the Health Sector Cybersecurity Coordination Center (HC3) helps healthcare organizations stay ahead of emerging risks. The NIST Cybersecurity Framework (CSF) supports threat modeling and intelligence sharing to enhance detection capabilities across the healthcare sector.
Effective detection sets the foundation for a swift and coordinated response.
Respond and Recover: Handling Supply Chain Incidents
The Respond function outlines clear actions for managing supply chain incidents. Healthcare organizations need detailed response playbooks that specify roles, isolation procedures, and communication protocols, including notifying patients or regulators. These playbooks should address scenarios like compromised vendor credentials, malware infections, or third-party data breaches.
The Recover function emphasizes restoring operations quickly and safely. This includes maintaining relationships with alternate suppliers who can step in if primary vendors are compromised. For critical systems, organizations should develop manual workflows to ensure patient care continues, even during digital outages. Recovery also involves validating vendor systems before bringing them back online and conducting post-incident reviews to strengthen defenses.
CSF 2.0 introduces governance controls (GV.SC-01 through GV.SC-04) that require healthcare organizations to prioritize suppliers, coordinate roles with partners, and establish accountability for supply chain security decisions.
NIST Implementation Tiers for Healthcare
To measure progress, the NIST CSF defines four Implementation Tiers that reflect an organization's maturity in supply chain security: Partial, Risk Informed, Repeatable, and Adaptive.
Many healthcare organizations currently fall between the Risk Informed and Repeatable tiers. Advancing to higher tiers requires investment in people, processes, and technology. However, organizations can prioritize critical vendors first, addressing lower-risk suppliers over time. Benchmarking tools can help identify gaps and guide improvements, ensuring steady progress in securing the supply chain.
Best Practices for Healthcare Supply Chain Security
Governance and Program Structure
Setting up a Cyber Supply Chain Risk Management (CSCRM) program with clear governance is essential. According to NIST CSF 2.0, there are four governance components tailored for supply chains. The first step? Develop a solid strategy with well-defined objectives, policies, and processes that all stakeholders can agree on. This ensures compliance with requirement ID.SC-1[3][5]. It's crucial to clearly document who is responsible for supply chain security decisions and how these decisions align with your enterprise risk management framework.
The GV.SC-02 control underlines the importance of assigning and documenting cybersecurity roles for all stakeholders involved in the supply chain. These roles must be communicated effectively, both within the organization and to external partners[5]. Procurement and IT security teams should work together to integrate vendor vetting and technical assessments into existing enterprise risk management systems. This is reinforced by GV.SC-03, which ensures that supply chain risks are seamlessly incorporated into broader organizational risk management processes[5].
Healthcare organizations should also adopt a tiered approach to supplier prioritization, as outlined in GV.SC-04[5]. Vendors critical to operations - such as those handling patient data, managing medical devices, or providing essential clinical services - should be subject to stricter oversight compared to administrative suppliers. This prioritization enables efficient resource allocation while maintaining a secure supply chain. By aligning these activities strategically, organizations can significantly reduce vulnerabilities.
These governance practices are the backbone of effective vendor assessments and ongoing risk management, discussed in the next section.
Controls for Vendor and Supply Chain Risk Management
Standardizing vendor assessments is key. This involves using tools like security questionnaires, technical evaluations, and continuous monitoring. Implementing Software Bill of Materials (SBOM) requirements is especially helpful - it provides a detailed inventory of components in vendor-provided software, making it easier to pinpoint vulnerabilities when new threats arise.
Incident reporting protocols are another must. Vendors should be required to notify healthcare organizations immediately if a breach or security incident occurs. Continuous monitoring of vendors is critical - don’t rely solely on annual reviews. Instead, track their security posture in real time, watch for shifts in risk profiles, and address issues swiftly. Regular audits and documentation reviews can also help verify that vendors comply with established security standards.
These measures not only strengthen vendor oversight but also ensure you're getting the most out of NIST resources, which we'll explore next.
NIST Resources for Healthcare Supply Chains
NIST SP 800-161 is the go-to guide for managing cyber risks in supply chains and serves as a cornerstone for building CSCRM programs[3]. For healthcare-specific insights, the Health Industry Cybersecurity Supply Chain Risk Management (HIC-SCRiM) Guide is invaluable. It aligns NIST principles with FDA cybersecurity requirements and addresses concerns from the Department of Health and Human Services (HHS). The guide focuses on building proactive relationships between acquirers and suppliers, offering actionable strategies to meet ID.SC-1, such as understanding the full supply chain lifecycle and setting up clear stakeholder agreements[3].
Other helpful resources include the HPH Sector CSF Implementation Guide and the NCCoE guidance, which focus on identifying and mitigating vulnerabilities in healthcare technology[2][4]. By using these NIST tools, healthcare organizations can effectively implement, measure, and refine their CSCRM programs to stay ahead of emerging risks.
Benefits of NIST Framework for Healthcare Supply Chains
Reduced Risk and Improved Operations
The structured approach of the NIST Cybersecurity Framework (CSF) offers clear advantages for healthcare organizations. By adopting NIST principles, healthcare providers can better protect against cyber threats such as ransomware attacks, breaches of protected health information (PHI), and operational disruptions. The framework helps organizations proactively identify vulnerabilities, reducing the chances of exploitation and minimizing the impact of cyber incidents across facilities and vendors[3]. When supply chain compromises occur, NIST-aligned organizations can recover more quickly using tools like critical asset mapping, incident response playbooks, and contingency plans.
Beyond risk reduction, the NIST CSF enhances operational efficiency. Its prioritized and adaptable approach to cybersecurity helps limit disruptions while maintaining care continuity. For example, Mayo Clinic leveraged NIST supply chain principles to improve risk visibility across vendors and establish a structured, repeatable process for evaluating supplier security practices[6]. This forward-thinking strategy also strengthens compliance efforts across the board.
Regulatory and Financial Advantages
Implementing the NIST CSF not only ensures adherence to regulations like HIPAA, HITECH, and HHS/HPH guidance but also improves an organization's standing with cyber insurers. This can lead to lower premiums and better coverage terms. Financially, the framework helps reduce costs associated with downtime, streamlines vendor assessments through standardization, and minimizes contractual disputes. By embedding NIST controls into procurement and contracting processes, organizations can establish clear security requirements, set incident reporting timelines, and define recovery objectives. These measures not only address immediate compliance and financial needs but also provide a foundation for long-term success.
Long-Term Value for Healthcare Organizations
Originally designed to safeguard U.S. critical infrastructure, the NIST Cybersecurity Framework explicitly includes healthcare as a key sector[7][4]. This federal backing ensures that NIST-aligned practices evolve alongside government standards and cybersecurity initiatives. As agencies like HHS, FDA, and CMS continue to tighten cybersecurity requirements, organizations already using NIST-based programs are better prepared to meet these rising expectations[3].
Strong supply chain security fosters trust among patients, clinicians, executives, and external partners. By continuously improving under NIST guidelines, healthcare organizations can stay ahead of emerging threats and shifting federal standards[7][4][5].
sbb-itb-535baee
Using Censinet RiskOps™ to Implement NIST Controls

Third-Party Risk Assessments with Censinet
Censinet RiskOps™ brings the principles of the NIST Cybersecurity Framework (CSF) into action for supply chain management. Specifically, it aligns with the Health Industry Cybersecurity Supply Chain Risk Management Guide (HIC-SCRiM) by leveraging structured tools to address NIST CSF control ID.SC‑1, which focuses on cyber supply chain risk management [3]. The platform handles every step of the vendor lifecycle - starting with onboarding and extending through remediation and renewal - ensuring compliance with NIST control ID.SC‑1 [3][5].
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."
This streamlined approach to risk assessments creates a foundation for ongoing, real-time supply chain security.
Continuous Risk Management Across Supply Chains
After conducting thorough risk assessments, Censinet RiskOps™ ensures vulnerabilities are continuously monitored and addressed in real time. Its collaborative risk network brings together healthcare delivery organizations and over 50,000 vendors and products, facilitating secure data sharing. This network-driven approach reduces duplicate assessments and enables ongoing monitoring.
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with."
The platform also allows organizations to benchmark their cybersecurity performance against industry standards, helping them progress through NIST Implementation Tiers. Automated workflows can be configured to trigger remediation tasks for high-risk responses, complete with defined timelines. These features directly support the NIST Protect and Respond functions.
AI-Powered Risk Assessments with Censinet AI™
Censinet AI™ speeds up NIST-aligned risk assessments by enabling vendors to complete security questionnaires in just seconds. The AI technology summarizes evidence and documentation, identifies fourth-party risk exposures, and generates concise risk reports. While automation takes care of repetitive tasks, human oversight remains central through configurable rules and review processes. Key findings are routed to designated stakeholders, including AI governance committees, creating a centralized hub for managing risks.
This balance between automation and human analysis empowers healthcare organizations to scale their risk operations without compromising the nuanced decision-making required for managing patient data, PHI, and clinical systems. By combining speed and oversight, Censinet AI™ ensures that even complex supply chain risks are addressed effectively.
Conclusion
Securing the healthcare supply chain is critical to safeguarding patient care and operational efficiency. The NIST Cybersecurity Framework offers a structured, risk-based approach that healthcare organizations can use to protect their entire supply chain, covering everything from EHR platforms and medical devices to third-party vendors and logistics partners.
As highlighted earlier, the framework's adaptable design supports scalable risk management strategies. NIST CSF 2.0 enhances this by integrating supply chain risk management into enterprise governance, focusing on supplier prioritization, unified governance, and comprehensive risk strategies [5]. Tools like the Health Industry Cybersecurity Supply Chain Risk Management (HIC-SCRiM) guide healthcare organizations and their suppliers in applying these principles through actionable steps [3].
By aligning practices with NIST, healthcare organizations can cut down on redundant assessments, simplify vendor onboarding, and maintain continuous monitoring. A great example of this is Mayo Clinic's integrated risk management approach, which demonstrates how these principles can be successfully implemented [6].
Platforms like Censinet RiskOps™ take these concepts further by operationalizing NIST controls at scale. The platform connects risk assessments to NIST CSF categories, automates third-party risk workflows, and facilitates continuous monitoring across a network of healthcare organizations and more than 50,000 vendors. With tools like Censinet AI™ speeding up processes like questionnaire completion and evidence review, organizations can expand their risk management capabilities while retaining the human oversight needed in the complex world of healthcare.
FAQs
How does the NIST Cybersecurity Framework support healthcare supply chain security?
The NIST Cybersecurity Framework offers healthcare organizations a structured way to tackle supply chain risks. It provides guidance to identify, evaluate, and address cybersecurity threats, helping protect critical systems and safeguard sensitive patient information.
By promoting best practices, the framework enhances visibility into potential third-party weaknesses and supports ongoing monitoring and response efforts. Solutions tailored for healthcare, such as Censinet RiskOps™, make risk management more manageable by simplifying assessments and encouraging collaboration across stakeholders.
How do NIST Implementation Tiers improve cybersecurity in healthcare supply chains?
The NIST Implementation Tiers offer a structured approach to improving cybersecurity in healthcare supply chains. These tiers align an organization's security efforts with its level of risk management maturity, helping to evaluate current practices, spot weaknesses, and prioritize areas for improvement.
By using this framework, healthcare providers and their vendors can build stronger supply chains, better protect sensitive patient information, and secure vital medical systems. This not only ensures operational continuity but also reinforces trust in healthcare services.
How does Censinet RiskOps™ support the use of NIST controls to secure healthcare supply chains?
Censinet RiskOps™ makes applying NIST controls easier and more effective for healthcare organizations. With its AI-driven platform, it offers real-time risk assessments and simplifies overall risk management. This helps organizations not only meet NIST guidelines but also improve how efficiently they operate.
By aligning with industry standards and automating key processes - like evaluating third-party and enterprise risks - Censinet RiskOps™ equips healthcare providers to safeguard critical systems and sensitive data. This includes protecting patient information and medical devices from potential cyber threats.
Related Blog Posts
- How to Secure Healthcare Supply Chains in 2025
- Building Vendor Risk Frameworks for Healthcare IT
- NIST CSF 2.0 Updates: What Healthcare Needs to Know
- NIST CSF vs IoT Device Risks in Healthcare
{"@context":"https://schema.org","@type":"FAQPage","mainEntity":[{"@type":"Question","name":"How does the NIST Cybersecurity Framework support healthcare supply chain security?","acceptedAnswer":{"@type":"Answer","text":"<p>The NIST Cybersecurity Framework offers healthcare organizations a structured way to tackle supply chain risks. It provides guidance to identify, evaluate, and address cybersecurity threats, helping protect critical systems and safeguard sensitive patient information.</p> <p>By promoting best practices, the framework enhances visibility into potential third-party weaknesses and supports ongoing monitoring and response efforts. Solutions tailored for healthcare, such as <em>Censinet RiskOps™</em>, make risk management more manageable by simplifying assessments and encouraging collaboration across stakeholders.</p>"}},{"@type":"Question","name":"How do NIST Implementation Tiers improve cybersecurity in healthcare supply chains?","acceptedAnswer":{"@type":"Answer","text":"<p>The NIST Implementation Tiers offer a structured approach to improving cybersecurity in healthcare supply chains. These tiers align an organization's security efforts with its level of <a href=\"https://www.censinet.com/resource/best-practices-for-cyber-risk-management-success\">risk management maturity</a>, helping to evaluate current practices, spot weaknesses, and prioritize areas for improvement.</p> <p>By using this framework, healthcare providers and their vendors can build stronger supply chains, better protect sensitive patient information, and secure vital medical systems. This not only ensures operational continuity but also reinforces trust in healthcare services.</p>"}},{"@type":"Question","name":"How does Censinet RiskOps™ support the use of NIST controls to secure healthcare supply chains?","acceptedAnswer":{"@type":"Answer","text":"<p>Censinet RiskOps™ makes applying NIST controls easier and more effective for healthcare organizations. With its <strong>AI-driven platform</strong>, it offers <strong>real-time risk assessments</strong> and simplifies overall risk management. This helps organizations not only meet NIST guidelines but also improve how efficiently they operate.</p> <p>By aligning with industry standards and automating key processes - like <a href=\"https://www.censinet.com/choosing-the-right-healthcare-tprm-solution\">evaluating third-party and enterprise risks</a> - Censinet RiskOps™ equips healthcare providers to safeguard critical systems and sensitive data. This includes protecting patient information and medical devices from potential cyber threats.</p>"}}]}
Key Points:
How does the NIST CSF help secure healthcare supply chains?
- Five core functions (Identify, Protect, Detect, Respond, Recover) guide risk management
- Structured vendor mapping reveals critical dependencies and PHI access points
- Security controls enforce least privilege, segmentation, and configuration baselines
- Threat detection tools flag suspicious vendor activities in real time
- Response playbooks ensure coordinated action during incidents
What does NIST CSF 2.0 add for supply chain governance?
- GV.SC‑01 to GV.SC‑04 requirements for accountable supply chain oversight
- Defined stakeholder roles across procurement, IT, clinical, and cybersecurity teams
- Vendor prioritization rules tied to PHI access and clinical criticality
- Integration into enterprise risk management (ERM) systems
- Formal documentation for decision‑making and role clarity
What controls help manage vendor and supply chain risk?
- Standardized security questionnaires and third‑party assessments
- SBOM requirements to track software components
- Incident reporting protocols with immediate vendor notification
- Continuous monitoring for vulnerabilities, policy changes, and sub‑processors
- Periodic audits to validate control effectiveness
Which NIST resources support healthcare SCRM programs?
- SP 800‑161 for cyber supply chain risk management practices
- HIC‑SCRiM guide for healthcare‑specific vendor and device security
- HPH CSF Implementation Guide for sector‑specific best practices
- NCCoE solution guides for securing telehealth, imaging, and genomic systems
- CSF 2.0 updates' to unify governance across supply chain functions
What benefits do healthcare organizations gain from implementing NIST CSF?
- Reduced breach likelihood through structured SCRM controls
- Better regulatory alignment with HIPAA, HITECH, and HHS guidance
- Lower operational and financial risk during vendor outages
- Improved insurer confidence', lowering premiums
- Repeatable, scalable processes for vendor evaluation
How does Censinet RiskOps™ operationalize NIST supply chain controls?
- Automated third‑party assessments aligned with NIST ID.SC controls
- Continuous monitoring for real‑time risk changes
- Benchmarking tools to measure maturity vs. industry peers
- Collaborative vendor network with 50,000+ products
- AI‑powered workflows accelerating risk scoring and documentation


