Penetration Testing vs. Vulnerability Scanning in Healthcare
Post Summary
Penetration testing simulates real-world cyberattacks to identify and exploit vulnerabilities, providing insights into how systems could be compromised.
Vulnerability scanning is an automated process that detects known vulnerabilities, misconfigurations, and missing patches across systems.
Penetration testing is manual, in-depth, and performed less frequently, while vulnerability scanning is automated, broader, and conducted regularly.
Together, they provide a comprehensive approach: vulnerability scanning offers continuous monitoring, while penetration testing validates risks and identifies critical vulnerabilities.
Penetration testing is ideal after major system changes, during mergers, or to validate high-risk vulnerabilities.
Tools like Censinet RiskOps™ streamline vulnerability scanning and risk management, while penetration testing requires skilled professionals and specialized tools.
Healthcare organizations face increasing cybersecurity threats, from ransomware attacks disrupting medical services to data breaches exposing sensitive patient information. To combat these risks, penetration testing and vulnerability scanning are two key methods for identifying and addressing security weaknesses. While both are critical, they serve different purposes:
- Penetration Testing: Simulates attacks to identify and exploit vulnerabilities, providing insights into how systems could be compromised.
- Vulnerability Scanning: Automates the detection of known vulnerabilities, offering a broad overview of security issues across systems.
Key Differences:
- Penetration testing is manual, in-depth, and performed less frequently (e.g., annually or after system changes).
- Vulnerability scanning is automated, broader, and conducted regularly (e.g., weekly or monthly).
Quick Comparison:
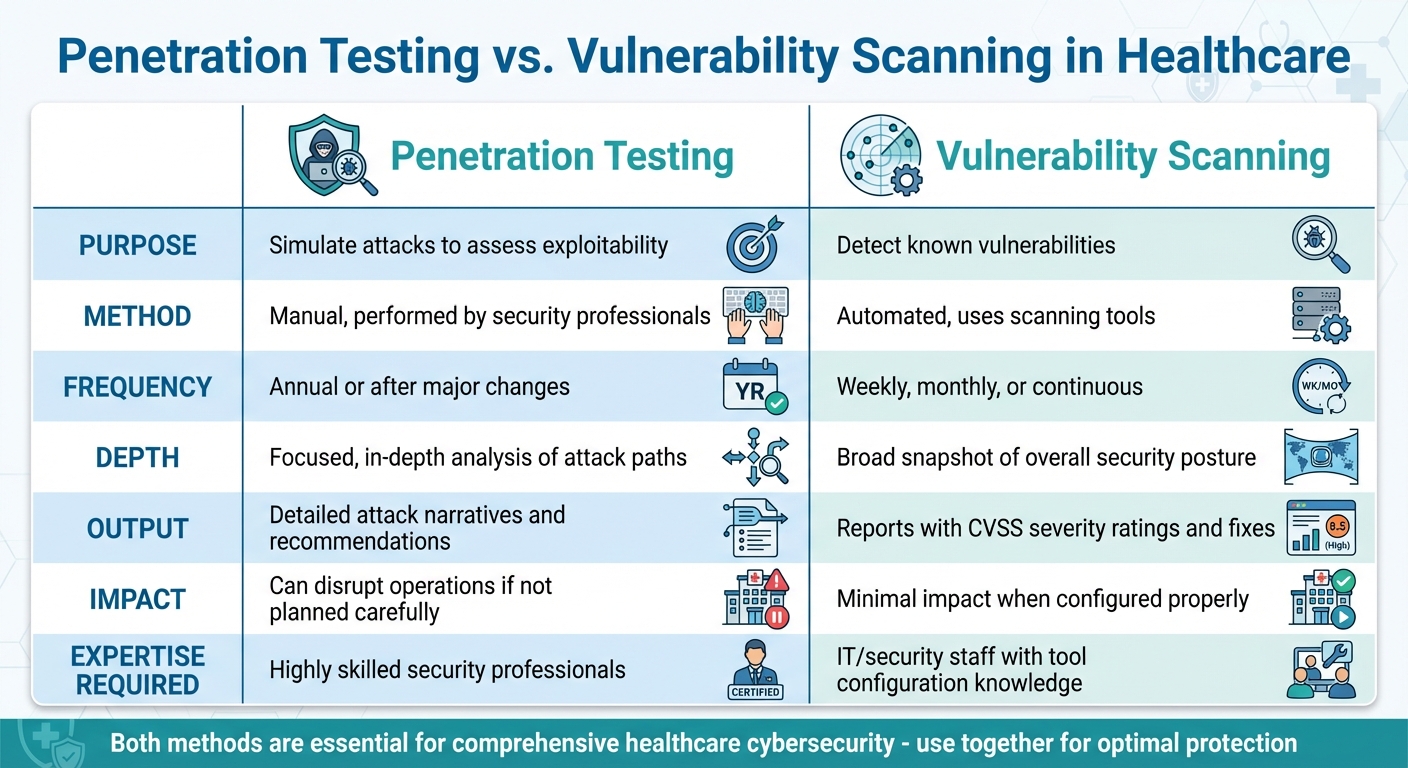
| Criteria | Penetration Testing | Vulnerability Scanning |
|---|---|---|
| Purpose | Simulate attacks to assess exploitability | Detect known vulnerabilities |
| Method | Manual, performed by security professionals | Automated, uses scanning tools |
| Frequency | Annual or after major changes | Weekly, monthly, or continuous |
| Output | Detailed attack narratives and recommendations | Reports with severity ratings and fixes |
| Impact | Can disrupt operations if not planned carefully | Minimal impact when configured properly |
Both methods are essential for healthcare cybersecurity. Vulnerability scanning provides continuous monitoring, while penetration testing validates risks and offers deeper insights into critical vulnerabilities. Together, they help healthcare organizations safeguard patient information and comply with regulations like HIPAA.
Penetration Testing vs Vulnerability Scanning in Healthcare: Key Differences
What Are Penetration Testing and Vulnerability Scanning?
Healthcare organizations use two key methods to safeguard patient data and clinical systems: penetration testing and vulnerability scanning. While penetration testing mimics real-world cyberattacks to uncover potential entry points, vulnerability scanning automates the search for known weaknesses in systems. Each approach plays a unique role in building a strong cybersecurity framework. Let’s break down what each entails and how they contribute to healthcare security.
What is Penetration Testing?
Penetration testing, or pen testing, is essentially a controlled cyberattack performed by ethical hackers. These professionals simulate the tactics of malicious attackers to find and exploit vulnerabilities in healthcare systems, such as patient portals, vendor applications, and internal networks [4][6]. The objective isn’t just to identify weaknesses, but to demonstrate how they could be exploited and the potential damage that could follow.
Penetration testing typically follows the Penetration Testing Execution Standard (PTES), which includes phases like pre-engagement, intelligence gathering, threat modeling, vulnerability analysis, exploitation, post-exploitation, and reporting [4]. For example, in a healthcare setting, testers might examine web portals and APIs to identify exposed interfaces, attempt to bypass authentication, or escalate privileges. They may also simulate how a compromised vendor-facing application could grant access to sensitive patient health information (PHI) or disrupt critical clinical operations [2].
The final deliverable is a comprehensive report that includes attack narratives, proof-of-concept exploits, impact assessments, and prioritized recommendations for fixing vulnerabilities [4][5][7]. This approach helps healthcare organizations understand their most pressing risks and how those risks could directly affect patient care and data security.
Now, let’s look at how vulnerability scanning complements penetration testing.
What is Vulnerability Scanning?
Vulnerability scanning is an automated process that systematically checks systems for known vulnerabilities, misconfigurations, and missing security controls. It relies on databases like the Common Vulnerabilities and Exposures (CVE) to identify issues [4][5][2]. In healthcare, these scans are applied to systems such as servers hosting electronic health records (EHRs), web portals, databases, and network devices that support clinical operations. They help identify problems like unpatched software, weak passwords, outdated libraries, or improper configurations [5][2].
The results are presented in detailed reports that classify vulnerabilities by severity using the Common Vulnerability Scoring System (CVSS), ranking them as critical, high, medium, or low. These reports also provide insights into the potential impact of each issue and suggest remediation steps [5]. By running regular scans and conducting additional checks after major updates - like deploying new versions of patient portals or EHR modules - IT and security teams can ensure ongoing system security and hygiene across their complex environments [4][5].
How Penetration Testing and Vulnerability Scanning Differ
Methodology and Purpose
Penetration testing and vulnerability scanning serve distinct roles in cybersecurity, particularly in healthcare settings. Penetration testing is a hands-on, manual process carried out by skilled security professionals who simulate real-world attacks. This method involves probing specific systems, applications, or pathways to uncover vulnerabilities and assess their potential impact on sensitive data like PHI (Protected Health Information) or patient care. By actively exploiting weaknesses, penetration testers can identify complex attack chains and flaws in business logic that automated tools often overlook [4] [6] [7].
On the other hand, vulnerability scanning is an automated process that scans multiple systems simultaneously to identify known vulnerabilities, configuration issues, or missing patches. It provides a broad overview of an organization's infrastructure, covering servers, workstations, network devices, and EHR systems. Think of vulnerability scanning as a routine check-up - it highlights what vulnerabilities exist. In contrast, penetration testing is more like an in-depth evaluation, revealing how those vulnerabilities could be exploited and the potential consequences [2] [4] [5] [7].
Another key distinction lies in their frequency and timing. Penetration tests are typically conducted annually or after significant system changes [4] [5] [7]. Vulnerability scans, however, are performed more frequently - weekly, monthly, or even continuously. This higher frequency is crucial in healthcare environments, where unpatched systems and outdated medical devices are common. Regular scanning helps quickly identify new vulnerabilities or configuration issues that could lead to ransomware attacks or breaches of sensitive patient data if left unaddressed [2] [5].
Comparison Table
| Criteria | Penetration Testing | Vulnerability Scanning |
|---|---|---|
| Primary Goal | Simulate real attacks to identify and exploit weaknesses; assess potential impact on systems and patient care | Detect and report known vulnerabilities, misconfigurations, and missing patches across systems |
| Methodology | Manual testing by ethical hackers with a deep focus on specific systems or applications | Automated tools providing a broad overview of security across multiple systems |
| Frequency | Conducted annually or after significant system changes | Performed weekly, monthly, or continuously to catch emerging vulnerabilities |
| Depth vs. Breadth | Focused, in-depth analysis of attack paths and exploitability | Broad snapshot of overall security posture across infrastructure |
| Output Type | Detailed reports with attack narratives, proof-of-concept exploits, and prioritized recommendations | Reports with CVSS severity ratings (critical, high, medium, low) and remediation steps |
| Expertise Required | Highly skilled security professionals with advanced knowledge of attack techniques | IT or security staff to configure tools and interpret results |
| Impact on Operations | Can be disruptive if not carefully planned; typically scheduled to avoid interference with clinical workflows | Low impact, though sensitive devices may experience performance issues if scans aren't properly configured |
| Validation of Exploitability | Confirms which vulnerabilities are exploitable and pose significant risk | May include false positives or issues already mitigated by existing controls |
| Regulatory Alignment | Recommended by standards like PCI DSS (annual requirement), NIST 800-53, CIS Controls, and ISO/IEC 27001 | Considered a baseline control; routinely expected by auditors as part of HIPAA risk analysis and monitoring [4] [5] [7] |
Both methods are essential for maintaining a strong cybersecurity posture, but they serve different purposes. Penetration testing digs deep to uncover and validate risks, while vulnerability scanning provides ongoing, broad surveillance to identify potential issues early. Together, they create a more comprehensive approach to protecting sensitive healthcare systems.
When to Use Each Method in Healthcare
When to Use Penetration Testing
Penetration testing is ideal for high-risk scenarios where the stakes are significant, such as major electronic health record (EHR) updates, introducing new infrastructure (e.g., switching to a new cloud provider), launching Internet-facing patient portals, or during mergers and acquisitions. These situations often create fresh attack surfaces that automated tools alone can’t fully evaluate [5][6].
This method is particularly useful for determining whether identified vulnerabilities can actually be exploited and for understanding the potential impact on patient safety and the security of protected health information (PHI). For example, while a vulnerability scanner might flag a critical issue with a high Common Vulnerability Scoring System (CVSS) rating, penetration testing can reveal if that vulnerability could realistically allow an attacker to access sensitive data [5][6]. Penetration tests can also be structured as red team exercises to assess how quickly and effectively your organization detects and responds to threats. These tests are typically conducted annually or after major changes to your security operations center (SOC) [5][6].
From a compliance and insurance standpoint, penetration testing is often a key requirement. While the Health Insurance Portability and Accountability Act (HIPAA) doesn’t explicitly mandate penetration testing, it does require covered entities to perform risk analyses, which often include testing security controls. Regulators might interpret the lack of such testing as a failure to adequately manage risks [3]. Additionally, cyber insurance providers increasingly expect proof of periodic penetration testing for high-risk systems as part of their underwriting or renewal processes [5].
When to Use Vulnerability Scanning
Vulnerability scanning, on the other hand, is best suited for routine security maintenance and ongoing monitoring.
This method involves frequent, automated scans of servers, workstations, network devices, and clinical systems [4][5]. Conducting weekly or monthly internal scans, along with external perimeter scans at least once a month, helps ensure that vulnerabilities are caught and addressed promptly [4][5]. These scans are especially critical for tracking remediation deadlines and ensuring that commonly exploited vulnerabilities don’t linger.
Vulnerability scanning is also an essential step when rolling out minor updates, patches, or configuration changes in systems where uptime is crucial. For instance, scanning can verify that applying a security patch to an EHR web interface or updating TLS settings on a patient portal hasn’t introduced new vulnerabilities or misconfigurations [4][5]. Integrating automated vulnerability scans into change management workflows ensures a repeatable and reliable security process.
For medical devices and clinical systems, it’s essential to collaborate with vendors and biomedical engineering teams to determine safe scanning practices, appropriate frequencies, and operational windows [2]. Network-level scans of medical device VLANs can uncover issues like default passwords, open management ports, or improper segmentation, all of which could allow attackers to move laterally toward sensitive data or critical devices [2]. Auditors often view regular vulnerability scanning as a fundamental part of HIPAA’s risk analysis and monitoring requirements [3][5].
Using Both Methods Together
A combination of penetration testing and vulnerability scanning provides a comprehensive approach to securing healthcare systems.
Vulnerability scanning delivers broad, frequent checks for known issues, while penetration testing dives deeper into how those vulnerabilities could be exploited in real-world scenarios [4][5][6]. Scanning results can guide the scope of penetration tests by identifying critical systems with clusters of vulnerabilities. In turn, penetration tests validate which scanner-detected issues are exploitable and assess the effectiveness of existing security measures [4][5][6].
Establish a policy-driven schedule: conduct continuous or weekly scans for Internet-facing assets, monthly scans for core infrastructure, quarterly risk assessments, and annual or event-driven penetration tests for high-risk systems [4][5]. Tools like Censinet RiskOps™ can streamline this process by centralizing risk data, mapping vulnerabilities and penetration test findings to specific systems, and facilitating collaboration between IT, security, compliance, and clinical teams. This integrated approach not only strengthens PHI protection but also enhances patient safety overall.
sbb-itb-535baee
Adding Testing to Healthcare Cyber Risk Management Programs
Meeting Regulatory Requirements
Incorporating testing methods like vulnerability scans and penetration tests into healthcare risk management programs is a practical way to ensure compliance and enhance patient safety. While HIPAA doesn't specify exact testing requirements, its Security Rule mandates thorough risk analyses and management under §164.308(a)(1)(ii)(A) and (B). These testing approaches provide technical evidence by identifying vulnerabilities in systems handling electronic protected health information (ePHI), assessing their potential impact, and documenting the steps taken to address them [3][8].
Vulnerability scans offer ongoing evaluations of security controls, while penetration tests confirm your organization's ability to detect and address exploitable weaknesses. These efforts align with HIPAA's call for regular technical and nontechnical evaluations under §164.308(a)(8) [3]. Many healthcare organizations also align their testing programs with frameworks like NIST SP 800-53, NIST Cybersecurity Framework, CIS Controls, and ISO/IEC 27001. Doing so not only strengthens compliance but also bolsters defensibility during audits or cyber insurance reviews [5].
Keeping your risk register updated and tracking remediation efforts are key components of effective risk management. Using a unified platform can make meeting these regulatory requirements more straightforward.
Using Censinet for Risk Management
Healthcare organizations can simplify these processes by using dedicated tools like Censinet RiskOps™. This platform consolidates penetration testing and vulnerability scanning results, links vulnerabilities to specific systems and vendors, and streamlines remediation workflows. By doing so, it eliminates the need for spreadsheets across various systems, including clinical applications, medical devices, patient portals, and vendor platforms.
Censinet's collaborative risk network connects healthcare providers with over 50,000 vendors and products, allowing secure sharing and tracking of third-party security practices [1]. For vendors handling PHI, organizations can require annual penetration test reports or attestations of regular scanning. This ensures a system of continuous monitoring rather than relying on one-time reviews.
The platform also offers cybersecurity benchmarking, which provides context for testing outcomes by comparing metrics like vulnerability remediation rates, mean time to remediate (MTTR), and control effectiveness against peer organizations. This benchmarking helps healthcare providers demonstrate progress to executives, boards, and regulators while identifying areas where their program excels or needs improvement. As Brian Sterud, CIO of Faith Regional Health, explained:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters" [1].
Best Practices for Healthcare Organizations
To minimize disruptions to patient care, schedule testing during maintenance windows or off-peak hours. Avoid live scanning of critical devices during busy clinical operations, and adopt a "test-in-staging-first" approach for major clinical applications before conducting limited production tests [2].
For legacy systems and medical devices that may not tolerate standard scans, collaborate with vendors and biomedical engineering teams to establish safe testing practices. This includes determining appropriate scanning frequencies and operational windows [2]. Use credentialed or rate-limited scans for sensitive systems, or implement strong compensating controls like network segmentation and enhanced monitoring [2].
Focus remediation efforts on risks that have the greatest impact, such as those involving PHI exposure, patient safety, and operational disruptions. Internet-facing systems with high-severity vulnerabilities and direct access to ePHI should be addressed with the shortest remediation timelines and receive executive-level attention [5]. Track performance metrics such as the percentage of critical vulnerabilities resolved within defined timeframes, MTTR by severity and asset type, the number of exploitable paths to PHI identified in penetration tests, and the reduction of recurring issues across tests [4][5].
Conclusion
Penetration testing and vulnerability scanning serve as essential, yet distinct, tools in bolstering healthcare cybersecurity. Vulnerability scanning provides a wide, ongoing view of potential risks across networks, servers, endpoints, and clinical applications by identifying vulnerabilities in real time. On the other hand, penetration testing takes a more focused approach, simulating real-world attacks to deeply evaluate high-risk systems, assess exploitability, and determine the potential impact on patient safety and sensitive health information.
Each method plays a unique role in addressing cybersecurity risks. Vulnerability scanning offers a broad, continuous assessment of potential weaknesses, while penetration testing goes further by validating whether those vulnerabilities can actually be exploited. It also identifies attack chains and ensures that controls like network segmentation are functioning as intended. Together, they create a comprehensive testing strategy that balances ongoing risk detection with deeper, periodic evaluations - particularly vital for systems managing electronic protected health information (ePHI), clinical workflows, and connected medical devices.
Compliance frameworks such as HIPAA, NIST SP 800-53, ISO/IEC 27001, CIS Controls, and PCI DSS emphasize the importance of regular risk analysis and security evaluations. By integrating vulnerability scan and penetration test results into platforms like Censinet RiskOps™, healthcare organizations can better correlate findings, prioritize remediation, and track progress. This unified approach not only supports compliance but also strengthens strategic risk management efforts over time.
FAQs
What’s the difference between penetration testing and vulnerability scanning in healthcare cybersecurity, and how do they work together?
Penetration testing and vulnerability scanning play distinct yet complementary roles in strengthening cybersecurity in healthcare. Vulnerability scanning is an automated process that works continuously to spot potential weaknesses, such as outdated software or system misconfigurations. On the other hand, penetration testing takes it a step further by simulating real-world cyberattacks to confirm these vulnerabilities and determine how attackers might exploit them.
Together, these approaches create a more comprehensive security strategy. Vulnerability scanning focuses on the ongoing identification of risks, while penetration testing helps validate and prioritize those risks by testing them in realistic scenarios. This dual approach enables healthcare organizations to better safeguard sensitive data, including patient records and clinical systems, while ensuring adherence to industry regulations and standards.
When should healthcare organizations use penetration testing instead of vulnerability scanning?
Healthcare organizations can benefit greatly from penetration testing when they need to simulate real-world attack scenarios. This approach helps identify exploitable vulnerabilities that might slip through the cracks during routine vulnerability scans. It’s especially useful for assessing the security of medical devices, clinical applications, or specific network segments after completing an initial scan.
Penetration testing is also a key tool for compliance audits. It helps verify the effectiveness of security measures and ensures that critical systems safeguarding patient data and PHI (Protected Health Information) remain secure. By mimicking the techniques attackers might use, penetration testing offers a clearer picture of how weaknesses could be exploited, enabling organizations to bolster their defenses more effectively.
How can healthcare organizations use penetration testing and vulnerability scanning to meet regulatory requirements?
Healthcare organizations depend on penetration testing and vulnerability scanning to spot and fix security gaps, ensuring they meet important regulations such as HIPAA, HITECH, and CMS cybersecurity standards. These processes play a critical role in managing risks and safeguarding sensitive patient data.
By conducting these assessments regularly, healthcare providers can confirm the effectiveness of their security measures, show compliance with regulatory requirements, and maintain proper documentation of their efforts. Using platforms tailored for healthcare cybersecurity and risk management can make these tasks more efficient, enabling organizations to concentrate on protecting patient information and preserving trust.
Related Blog Posts
Key Points:
What is penetration testing in healthcare?
- Definition: Penetration testing, or pen testing, is a controlled simulation of cyberattacks performed by ethical hackers to identify and exploit vulnerabilities in healthcare systems.
- Purpose: It helps organizations understand how attackers could compromise systems, such as patient portals, EHRs, or vendor applications, and provides actionable insights to mitigate risks.
What is vulnerability scanning in healthcare?
- Definition: Vulnerability scanning is an automated process that systematically checks systems for known vulnerabilities, misconfigurations, and missing patches.
Purpose: It provides a broad overview of security issues across healthcare infrastructure, including servers, databases, and network devices.
How do penetration testing and vulnerability scanning differ?
- Penetration Testing:
- Manual and in-depth, performed by skilled professionals.
- Simulates real-world attacks to assess exploitability.
- Conducted annually or after major system changes.
- Vulnerability Scanning:
- Automated and broad, using tools to detect known vulnerabilities.
- Performed regularly (e.g., weekly or monthly).
- Provides reports with severity ratings and remediation steps.
Why are both methods important for healthcare cybersecurity?
- Complementary Roles: Vulnerability scanning offers continuous monitoring to detect known issues, while penetration testing validates risks and identifies complex vulnerabilities that automated tools might miss.
- Regulatory Compliance: Both methods are essential for meeting HIPAA and other regulatory requirements.
When should healthcare organizations use penetration testing?
- High-Risk Scenarios: After major system updates, during mergers, or when introducing new infrastructure like cloud services.
- Validation: To confirm whether identified vulnerabilities can be exploited and assess their potential impact on patient safety and data security.
What tools can healthcare organizations use for these methods?
- Vulnerability Scanning Tools: Platforms like Censinet RiskOps™ automate scanning, track compliance, and provide real-time risk visibility.
- Penetration Testing Tools: Requires skilled professionals using tools like Metasploit or Burp Suite to simulate attacks and analyze vulnerabilities.


