Quantum AI Security: Preparing for the Next Frontier of Cyber Risk
Post Summary
Quantum computing and AI are reshaping cybersecurity, and healthcare is especially vulnerable. Here's why this matters:
- Current encryption methods like RSA and ECC could be broken by quantum computers in the coming years.
- Cybercriminals are already using tactics like "Harvest Now, Decrypt Later" (HNDL), storing encrypted data today to decrypt it once quantum technology advances.
- Healthcare data, including electronic health records and genomic information, is a prime target due to its long-term value.
To stay protected, healthcare organizations need to act now by:
- Transitioning to quantum-resistant encryption methods approved by NIST.
- Implementing zero-trust security models and AI-driven threat detection systems.
- Prioritizing governance frameworks that integrate automation with human oversight to mitigate risks effectively.
The risks of inaction are high - healthcare breaches already cost $9.77 million on average, and quantum threats could amplify these costs. The time to prepare is now.
How Quantum Computing Threatens Current Encryption Methods
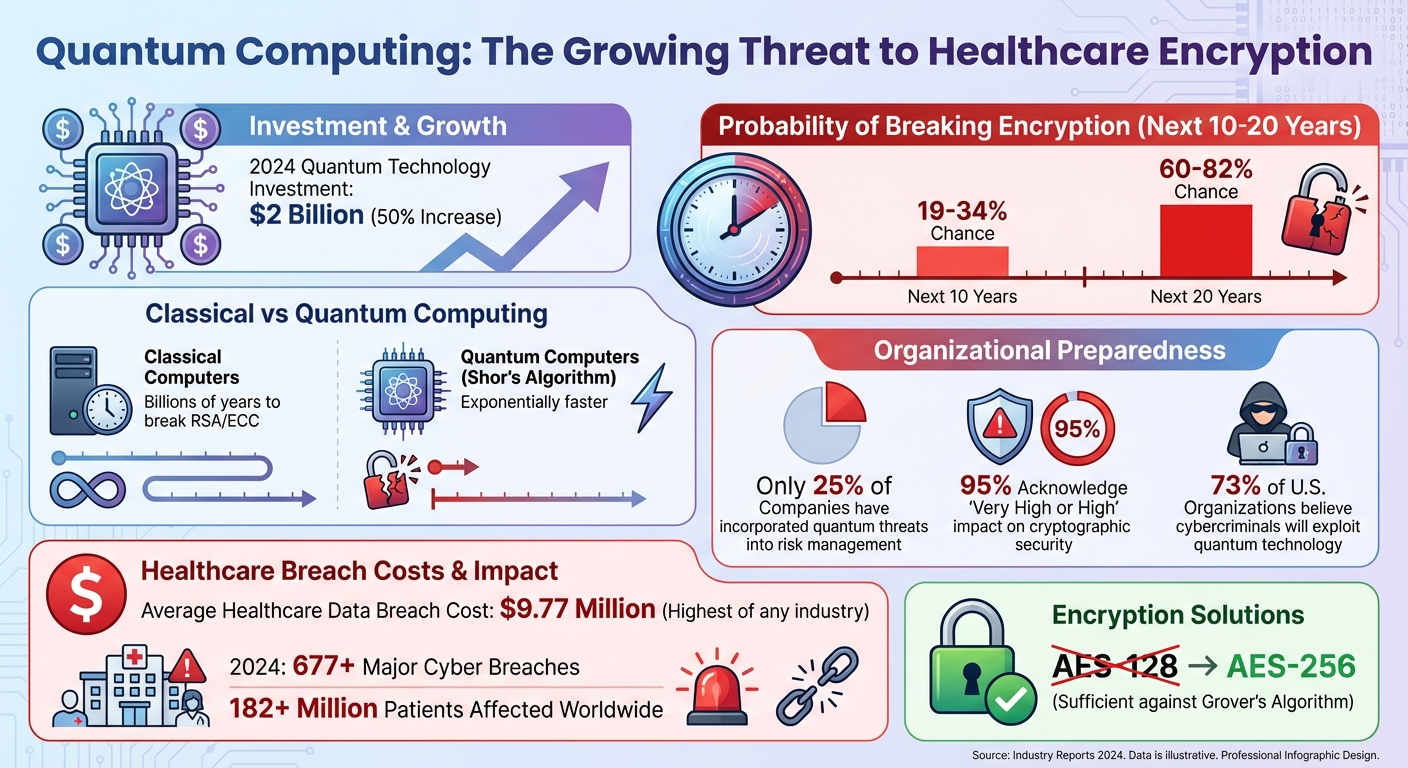
Quantum Computing Threat Statistics and Healthcare Cybersecurity Risks
Healthcare organizations depend heavily on encryption to safeguard patient records, secure medical device communications, and protect genomic data. However, encryption methods like RSA and ECC, which are widely used today, are no match for the power of quantum computing. Unlike classical computers, quantum systems leverage qubits, which can exist in multiple states simultaneously. This unique capability allows quantum computers to solve complex problems at speeds that classical systems simply can't match. Unfortunately, this also makes current encryption methods vulnerable to quantum algorithms specifically designed to exploit their weaknesses.
The surge in quantum technology investment reflects its growing significance. In 2024 alone, investment in the field increased by nearly 50%, reaching approximately $2 billion. Experts predict that within the next decade, there’s a 19% to 34% chance of developing a quantum computer capable of breaking encryption. That probability jumps to between 60% and 82% over the next 20 years. Despite these warnings, a study by KPMG Germany revealed that only 25% of companies have incorporated the quantum threat into their risk management strategies, even though 95% of respondents acknowledge the "very high or high" impact quantum computing could have on cryptographic security.
Shor's Algorithm and RSA/ECC Encryption Vulnerabilities
Encryption methods like RSA and ECC rely on mathematical problems that are extremely difficult to solve with classical computers - such as factoring large numbers or solving discrete logarithms. These challenges are what make them secure in today’s computing landscape. For instance, it would take classical systems billions of years to break these codes. But Shor's algorithm, introduced in 1994, flips the script. By harnessing quantum mechanics, it can factor large prime numbers and compute discrete logarithms exponentially faster than classical computers.
"Quantum computing threatens cybersecurity not because it hacks differently - but because it rewrites the mathematics that modern encryption depends on." - Palo Alto Networks [2]
This breakthrough renders RSA, ECC, and Diffie-Hellman encryption methods vulnerable, as it allows attackers to derive private keys from public keys. Unlike symmetric encryption, which can be fortified by simply increasing key sizes, public-key systems like RSA and ECC require entirely new algorithms designed to withstand quantum attacks. This is especially alarming for protocols like Transport Layer Security (TLS), which rely on asymmetric encryption to establish trust and exchange symmetric keys. If asymmetric encryption is compromised, the symmetric keys it protects could also be exposed, leaving entire communications vulnerable.
Grover's Algorithm and Symmetric Encryption Weaknesses
While Shor's algorithm poses a significant threat to asymmetric encryption, Grover's algorithm targets symmetric methods. Grover’s algorithm accelerates brute-force key searches, but its impact is less severe. For example, healthcare organizations can counter this threat by increasing key sizes - moving from AES-128 to AES-256 is sufficient to maintain security against Grover's algorithm for now.
"In contrast, symmetric algorithms are less affected. Here, Grover's algorithm can speed up brute-force key searches, but its advantage is limited. Increasing key sizes, such as moving from AES-128 to AES-256, is sufficient to maintain security against such attacks for the time being." - Nature [4]
However, hybrid encryption protocols that combine both asymmetric and symmetric methods are at greater risk. If the asymmetric component of a hybrid system is compromised, the symmetric keys it protects could also be decrypted. This is a serious concern for healthcare data, which often needs to be stored securely for a patient's entire lifetime. Medical devices add another layer of complexity, as they typically have long lifecycles and are rarely updated to meet evolving cryptographic standards. Without quantum-safe algorithms built into their design, these devices could remain vulnerable for decades.
Quantum-Powered AI Cyber Threats
The intersection of quantum computing and artificial intelligence (AI) is reshaping the cybersecurity landscape, particularly in healthcare. Quantum computing's ability to process vast possibilities simultaneously, combined with AI's strength in pattern recognition and data analysis, introduces a new breed of cyber threats. Quantum Machine Learning (QML), for example, can analyze patterns, optimize processes, and simulate scenarios at lightning-fast speeds, training massive datasets in mere microseconds. While these advancements promise breakthroughs in medical research and diagnostics, they also equip cybercriminals with tools to uncover vulnerabilities, exploit zero-day flaws, and craft highly sophisticated social engineering schemes aimed at healthcare professionals. This convergence of technologies paves the way for emerging threats like "Harvest Now, Decrypt Later" (HNDL) attacks and adaptive AI-driven breaches.
Harvest Now, Decrypt Later Attacks
One of the most concerning threats is the "Harvest Now, Decrypt Later" (HNDL) strategy. In this scenario, attackers collect encrypted patient data today with the intent of decrypting it in the future, once quantum computers become capable of breaking current encryption standards. This critical juncture, often referred to as "Q-Day", marks the point where today's encryption methods will no longer be effective.
"The healthcare sector faces an imminent and profound cybersecurity threat from the advent of quantum computing. To mitigate these impending dangers, it is imperative for healthcare organizations to adopt quantum-resistant solutions immediately, ensuring the protection of patient data and the integrity of healthcare systems before the arrival of 'Q-Day' - the point at which quantum computers can compromise existing encryption methods."
– Forward Edge-AI, Inc.[1]
Healthcare data is particularly vulnerable to HNDL attacks due to its long-term relevance. Sensitive information, such as genomic data, mental health records, and other personal health details, often remains valuable for decades. With the average cost of a healthcare data breach reaching $9.77 million[1] and hundreds of incidents involving 500 or more patient records reported in 2021 alone, the risks are staggering. Even data that is secure today could become compromised in the future, as adversaries stockpile encrypted records in anticipation of quantum decryption capabilities.
AI-Enhanced Quantum Attack Methods
The threat doesn't stop at data harvesting. Attackers are deploying AI to make quantum-powered attacks more adaptive and efficient. AI can learn and evolve, enabling quantum-driven malware to adjust its tactics in real time. This is especially alarming in healthcare, where the rapid adoption of connected devices expands the attack surface significantly. As Michael Khoury from Palo Alto Networks highlights, "For customers in highly regulated sectors (from healthcare to finance to government) the stakes are especially high, as maintaining long-term data confidentiality is central to trust."[6]
Post-Quantum Cryptography for Healthcare
Post-quantum cryptography (PQC) is transforming how healthcare organizations safeguard sensitive information. These advanced encryption techniques are built to withstand the power of quantum computers, which could one day crack widely used algorithms like RSA and ECC. For healthcare, this isn't just a theoretical concern - quantum computers pose a real risk to electronic health records, genomic data, and even medical devices. A breach could lead to massive data leaks and disrupt critical operations.
The need to act is pressing. Preparing for quantum threats requires years of coordinated effort, and delaying the shift to quantum-resistant encryption leaves sensitive data exposed. Healthcare data, often valuable for decades, is already at risk of being stolen now and decrypted later when quantum technology matures. Below, we’ll look at the NIST standards for PQC and the steps healthcare organizations can take to begin their transition.
NIST Post-Quantum Cryptography Standards

The National Institute of Standards and Technology (NIST) has established three key PQC algorithms under FIPS 203–205, providing a clear roadmap for organizations. These include:
- Module-Lattice-Based Key-Encapsulation Mechanism (ML-KEM): Used for secure key exchanges.
- Module-Lattice-Based Digital Signature Algorithm (ML-DSA): Ensures the authenticity and integrity of digital signatures, vital for verifying medical records.
- Stateless Hash-Based Digital Signature (SLH-DSA): Offers an alternative digital signature approach with unique security attributes.
Additionally, NIST has selected HQC (Hamming Quasi-Cyclic) as another key-encapsulation mechanism, broadening the range of tools available for quantum-resistant encryption. These algorithms focus on lattice-based and hash-based cryptography, areas that remain computationally challenging even for quantum systems.
For healthcare IT teams, these standards provide a practical foundation to replace outdated encryption methods with quantum-resistant solutions. Years of research have gone into ensuring these algorithms can meet the unique challenges posed by quantum computing.
Transitioning to Quantum-Resistant Encryption
With NIST standards in place, healthcare organizations must now focus on transitioning to quantum-resistant encryption. This process should start immediately, even though large-scale quantum computing may still be years away. The first step involves conducting a thorough inventory and assessment of all systems, applications, and data flows that rely on current encryption methods. This includes patient portals, electronic health record systems, and connected medical devices.
Once this inventory is complete, organizations should prioritize their most valuable and vulnerable assets for migration. High-priority targets include electronic health records, genomic databases, and medical device data, which are particularly susceptible to harvest-now-decrypt-later attacks. Transitioning these systems requires rigorous testing in controlled environments to ensure the new algorithms do not interfere with clinical workflows or delay critical processes.
sbb-itb-535baee
Using Censinet RiskOps for Quantum AI Risk Management
Healthcare organizations are facing a growing wave of cybersecurity challenges as quantum computing begins to intersect with AI. Cybercriminals are already leveraging tactics like "Harvest Now, Decrypt Later", which underscores the urgency for proactive risk management strategies.
To tackle these evolving threats, specialized tools are becoming indispensable. Censinet RiskOps™ provides a centralized platform that integrates quantum AI risk protocols into existing cybersecurity strategies. By combining threat intelligence, risk assessments, and governance into one system, it helps organizations pinpoint and address vulnerabilities before they compromise patient data or disrupt clinical operations.
The platform leverages Censinet AITM to accelerate risk evaluations while still maintaining expert oversight. With a unified dashboard offering continuous, real-time insights, leaders can implement effective countermeasures against quantum-driven threats. This approach ensures that while routine tasks are streamlined, critical decisions remain guided by experienced risk professionals. The result? Teams can prioritize patient safety and ensure consistent, reliable care delivery.
As quantum technology continues to advance, staying alert is non-negotiable. Censinet RiskOps equips healthcare organizations with a flexible and forward-thinking cybersecurity framework designed to adapt to emerging quantum risks.
Governance Frameworks for Quantum AI Risk
Healthcare organizations can't afford to ignore quantum AI threats. Preparing for quantum risks is a long-term commitment that demands coordinated efforts across multiple departments [2]. Starting early can significantly reduce the risks posed by quantum-powered attacks [3].
Good governance isn't just about handing off cybersecurity to your IT team - it's about weaving security into every part of the business [6][7]. Leadership must take the reins, shifting from reactive security measures to proactive frameworks designed to anticipate and mitigate risks. This forward-thinking approach depends on collaboration among vendors, partners, and regulators to build a unified defense [6].
For early adopters, quantum readiness is becoming a reputation issue. It’s no longer just a technical challenge; it’s a matter of customer trust and market credibility [2]. In healthcare, safeguarding medical device data from potential quantum decryption attacks is not just about protecting patient privacy. It’s about upholding the trust patients place in providers to keep their sensitive health information secure. This urgency highlights the need to combine automated tools with strategic human oversight to stay ahead of evolving threats.
Balancing Automation with Human Oversight
Quantum-powered AI attacks move at speeds and scales that traditional, human-only defenses simply can't match [8][11]. To keep up, healthcare organizations must rely on automated systems. But automation alone isn’t enough. AI-powered tools like real-time threat detection, autonomous key management, and continuous monitoring can minimize human error and offer instant insights into complex threats [1][9][10]. However, human oversight is still critical for interpreting AI outputs and making strategic calls [5].
Take Censinet AI, for example. It uses human-guided, autonomous automation to streamline key risk assessment processes. Risk teams remain in control through customizable rules and review mechanisms, ensuring that automation enhances rather than replaces decision-making. This "human-in-the-loop" model allows healthcare organizations to scale their defenses while maintaining the expert judgment needed to navigate complex quantum AI risks.
Reporting Quantum AI Risks to Leadership
A balanced approach to automation is just one piece of the puzzle - communicating these risks to leadership is equally vital. Boards need clear, actionable data about quantum AI risks. The challenge? Translating deeply technical threats into terms that align with leadership priorities, such as patient safety, regulatory compliance, financial stability, and organizational reputation.
Censinet RiskOps offers a centralized platform for presenting quantum AI risk data. Its intuitive dashboards compile real-time metrics, making it easier for leadership to identify and address critical issues. This system ensures continuous oversight and accountability throughout the organization.
When briefing leadership, focus on measurable data points: the volume of encrypted data at risk, the timeline for quantum threats becoming a reality, the cost of transitioning to post-quantum cryptography, and the potential financial and reputational fallout from a breach. Always frame these risks in terms of patient safety and care delivery - priorities that resonate deeply with any healthcare organization.
Conclusion
Quantum AI threats are no longer a distant concern. Adversaries are already using "Harvest Now, Decrypt Later" strategies to capture encrypted data, intending to decrypt it with future quantum capabilities [1][4]. In 2024 alone, the healthcare sector reported over 677 major cyber breaches, exposing the data of more than 182 million patients worldwide. The urgency for healthcare organizations to act is undeniable [1].
To strengthen cybersecurity against these emerging threats, organizations should take three immediate steps:
- Inventory all cryptographic assets, including electronic health record (EHR) systems, medical devices, and APIs, to identify vulnerabilities to quantum attacks [1].
- Transition to NIST-approved post-quantum cryptography standards, starting with the most sensitive data and critical infrastructure [1].
- Establish governance frameworks that integrate automated threat detection with human oversight, ensuring timely and efficient responses to quantum-related risks [5][6].
These actions lay the groundwork for more integrated platforms that simplify risk management.
Despite the clear risks, only a small fraction of organizations include quantum threats in their risk management plans. This is alarming, especially since 73% of U.S. organizations believe it's only a matter of time before cybercriminals exploit quantum technology to break current encryption methods [3]. Healthcare data breaches already cost an average of $9.77 million per incident - higher than any other industry [1]. A quantum-powered breach could lead to even more devastating financial and reputational consequences.
Addressing these challenges calls for centralized solutions. Platforms like Censinet RiskOps offer healthcare organizations the tools they need to manage quantum AI risks alongside traditional cybersecurity threats. Through human-guided automation powered by Censinet AI, these platforms provide intuitive dashboards that consolidate real-time risk data. They also ensure leadership can clearly understand and act on risks in terms of patient safety, regulatory compliance, and organizational reputation.
The time to act is now. Preparing for quantum AI risks requires immediate, coordinated efforts. With the timeline for quantum advancements uncertain and the window for preparation closing, building quantum-resistant defenses today is critical. By doing so, organizations not only protect their data but also uphold the trust patients place in them to safeguard their most sensitive information.
FAQs
When will quantum computers be able to break today’s encryption methods?
Experts predict that within the next 10 to 20 years - potentially as early as 2030 - quantum computers could become powerful enough to break current encryption methods. This projection hinges on the fast-paced progress in quantum technology.
For healthcare organizations, this means taking action now. It's time to investigate quantum-resistant encryption techniques and implement strategies to safeguard sensitive information against future vulnerabilities. Staying prepared today will be critical in managing tomorrow's challenges.
How can healthcare organizations prepare their systems for quantum-resistant encryption?
To get ready for quantum-resistant encryption, healthcare organizations need to start by taking stock of their current encryption methods and assets. Shifting to quantum-safe algorithms should be a priority, as these are designed to withstand the power of quantum computing. For new systems, adopting solutions that align with CNSA 2.0 standards offers a reliable starting point. Alongside this, embracing a zero-trust architecture and regularly updating cryptographic protocols are smart moves to bolster defenses against future quantum-driven threats. Preparing well in advance of "Q-Day" will help safeguard critical healthcare data and infrastructure against these emerging challenges.
What risks does quantum AI pose to cybersecurity in healthcare?
Quantum AI introduces serious risks to healthcare cybersecurity, primarily by enabling faster and more advanced cyberattacks. Quantum computing has the potential to break through traditional encryption methods, leaving sensitive patient data and healthcare systems vulnerable to breaches. On top of that, AI-driven automation can adjust and refine attacks in real time, putting medical devices and critical infrastructure at risk. These developments don't just threaten privacy - they could also shake public confidence in healthcare systems and create significant operational challenges.


