Quantum Computing and Healthcare Vendor Risk: Preparing for the Next Technology Revolution
Post Summary
Quantum computing is about to change the game for healthcare security. It threatens to break current encryption methods like RSA and ECC, which protect patient data, medical devices, and vendor systems. This puts sensitive healthcare information at risk of future breaches, especially through tactics like "Harvest Now, Decrypt Later", where attackers steal encrypted data today to decrypt it later using quantum technology.
Here’s what you need to know:
- Quantum computers can crack today's encryption. Algorithms like Shor's and Grover's make quantum systems capable of breaking widely used cryptographic methods.
- Healthcare is especially vulnerable. In 2024, there were 677 cyber breaches exposing 182 million records globally. Long data retention periods in healthcare make it an easy target for future decryption.
- Vendor systems are a weak link. Many rely on outdated encryption, and their long-lived hardware is hard to update.
- Action is urgent. Organizations must transition to quantum-resistant cryptography, update vendor contracts, and assess risks now to avoid being caught unprepared.
The article provides a step-by-step guide to secure healthcare systems against quantum risks, including evaluating vendor cryptographic practices, requiring quantum-safe algorithms, and building governance frameworks. Healthcare leaders must act now to protect sensitive data before "Q-Day" arrives, when quantum computers will render current encryption obsolete.
Quantum Threats to Healthcare Vendor Ecosystems
How Quantum Computing Defeats Current Encryption
Quantum computers pose a serious challenge to the encryption methods that currently protect healthcare data. Take Shor's algorithm, for example - it can break RSA and ECC encryption by efficiently factoring the prime numbers these systems rely on. While classical computers would need centuries to achieve this, quantum computers can do it in a fraction of the time[7].
Then there’s Grover's algorithm, which speeds up brute-force attacks on symmetric keys. While AES-256 is expected to hold up against quantum attacks until at least 2050, AES-128 could be at risk much sooner[8]. The real issue lies in protocols like Transport Layer Security (TLS), widely used in healthcare systems. Since TLS depends on asymmetric encryption to exchange symmetric keys, a successful quantum attack on its asymmetric component could expose entire communications to attackers[4].
Quantum computing is no longer a distant concept - some companies are already operating up to 60 functional quantum computers[7]. Experts predict a 19% to 34% chance that cryptographically relevant quantum computers (CRQCs) will emerge within the next decade, with widespread availability expected between 2030 and 2035[4][9]. A survey of 562 professionals in healthcare, biotechnology, and pharmaceuticals found that 67% are concerned about quantum computing's potential to compromise encryption in the future[10]. These vulnerabilities significantly increase risks across various healthcare vendor categories.
High-Risk Vendor Categories in Healthcare
Certain types of healthcare vendors are especially exposed to quantum threats due to encryption challenges. EHR platform providers are at the forefront of this risk. These platforms store massive amounts of patient data secured with RSA and ECC encryption, making them prime targets for "Harvest Now, Decrypt Later" attacks[1][11].
Similarly, medical device manufacturers face serious vulnerabilities. Many Internet of Medical Things (IoMT) devices use lightweight encryption and have long operational lifespans, making it difficult to implement quantum-resistant updates once they’re deployed[1][3].
Telehealth platforms are also at risk, as they transmit sensitive patient communications using encryption methods that quantum computers could potentially break. Cloud-based healthcare infrastructure providers face exposure, too - especially concerning given that 47% of healthcare cloud data is classified as sensitive[10].
Additional high-risk categories include genomic database providers, which handle data requiring decades of confidentiality, and AI-driven diagnostics vendors, where compromised datasets could lead to incorrect diagnoses and treatment plans[1][12].
Impact of Quantum Risks on U.S. Healthcare Organizations
The risks faced by vendors ultimately create significant challenges for U.S. healthcare organizations. Beyond data breaches, these threats jeopardize patient safety and privacy. For example, compromised medical devices or systems could lead to life-threatening situations for patients[4]. Additionally, decrypted health data could be misused to discriminate against vulnerable populations, eroding public trust in healthcare systems[4]. Violations of HIPAA due to quantum-enabled breaches could also result in severe financial penalties.
"The healthcare sector faces an imminent and profound cybersecurity threat from the advent of quantum computing. To mitigate these impending dangers, it is imperative for healthcare organizations to adopt quantum-resistant solutions immediately, ensuring the protection of patient data and the integrity of healthcare systems before the arrival of 'Q-Day' - the point at which quantum computers can compromise existing encryption methods." - Forward Edge-AI, Inc.[1]
Healthcare organizations that still rely on legacy PKI-based systems are particularly vulnerable to CRQCs[1]. Vendors in Operational Technology (OT) and Industrial Control Systems (ICS) are also at risk. Their hardware and cryptographic keys are often difficult to update quickly, which could jeopardize critical healthcare services[3]. These risks highlight the urgent need for updated vendor risk management strategies that specifically address quantum-related vulnerabilities.
Regulatory Requirements for Quantum Readiness
As quantum computing advances, healthcare organizations are under growing pressure to address vendor risks tied to quantum threats. Regulatory mandates are now pushing the sector to prepare for these challenges.
NIST Post-Quantum Cryptography Standards

In 2016, the U.S. National Institute of Standards and Technology (NIST) began the process of standardizing post-quantum cryptography (PQC) to safeguard data against emerging quantum threats [4]. So far, NIST has approved three PQC algorithms (FIPS 203–205), with additional algorithms expected in the future [3]. These new standards are designed to replace vulnerable public-key encryption methods that quantum computers could compromise.
For healthcare organizations, adopting these NIST standards has become a federal compliance priority. The algorithms offer quantum-resistant solutions for key exchanges, digital signatures, and encryption, ensuring patient data remains secure across vendor systems. This means healthcare providers must assess whether their vendors plan to incorporate FIPS 203–205 algorithms into their products and services.
Federal Policies Affecting Healthcare Quantum Readiness
Federal agencies are now requiring transitions to quantum-resistant cryptography across critical infrastructure, including healthcare. The National Security Agency's Commercial National Security Algorithm Suite 2.0 (CNSA 2.0) outlines timelines for adopting quantum-safe cryptography in government systems [4]. While CNSA 2.0 primarily focuses on federal systems, healthcare providers involved with federal programs or managing government health data must align their vendor requirements with these standards.
Additionally, the Cybersecurity and Infrastructure Security Agency (CISA) and the Department of Health and Human Services (HHS) are creating frameworks to guide healthcare entities toward quantum readiness [6]. These frameworks emphasize the need for healthcare organizations to include quantum-readiness requirements in vendor contracts and compliance assessments, ensuring third-party providers meet the same stringent standards expected of federal systems.
Connecting Quantum Readiness to HIPAA and NIST Frameworks
Although the U.S. does not yet have quantum-specific healthcare regulations, existing frameworks like HIPAA already demand robust technical safeguards that now extend to quantum-resistant methods [1][14][15]. The HIPAA Security Rule requires "appropriate" encryption to protect electronic protected health information (ePHI). As quantum computing threatens current encryption methods, healthcare organizations must interpret this requirement to include quantum-resistant encryption.
The NIST Cybersecurity Framework offers a practical roadmap for integrating quantum risk management into existing security strategies. Healthcare providers should update their risk assessments to account for quantum vulnerabilities, particularly when evaluating vendors handling sensitive patient information with long-term confidentiality needs. Incorporating these updated standards into vendor evaluations is essential for maintaining cybersecurity resilience.
The FDA is also leveraging its existing guidance to address quantum readiness for medical devices. While no formal regulations for quantum-specific devices exist yet, these efforts highlight the importance of including quantum-readiness provisions in vendor agreements. This alignment with broader regulatory standards ensures that healthcare organizations remain prepared for the quantum era.
Creating a Quantum-Ready Vendor Risk Management Program
To prepare for quantum threats, healthcare organizations need to build a vendor risk management program that focuses on three key actions: identifying the cryptographic methods vendors currently use, assessing each vendor's vulnerability to quantum risks, and including quantum-resistant requirements in vendor contracts.
Evaluating Vendor Cryptographic Practices
Start by cataloging the cryptographic methods your vendors use. This involves creating an inventory of all cryptographic assets and systems within your vendor ecosystem. Think of everything from medical devices and electronic health records (EHRs) to communication channels - essentially, any system that relies on encryption to secure patient data [4]. The goal is to pinpoint vendors using encryption methods that are vulnerable to quantum threats.
After mapping out these cryptographic dependencies, evaluate the quantum vulnerability of each asset. Not all systems face equal risk. For example, patient records with long retention periods are particularly vulnerable to the "Harvest Now, Decrypt Later" tactic, where attackers collect encrypted data now, intending to decrypt it later once quantum computing becomes powerful enough [5][1]. Focus on vendors handling highly sensitive data, critical systems, or information with long lifespans. This prioritization will help you understand where the highest quantum risks lie and guide the next steps in managing those risks.
Creating Quantum Risk Profiles for Each Vendor
Quantum Risk Management (QRM) expands traditional cyber risk strategies to account for the challenges and opportunities posed by quantum technologies [16]. Incorporate quantum risks into your organization's risk register and establish clear policies approved by your board. These policies should outline roles, responsibilities, and funding, as well as how quantum considerations fit into your overall third-party risk management framework [16].
When developing risk profiles for vendors, go beyond their current cryptographic methods. Assess their cryptographic agility - their ability to adapt quickly to new encryption standards as quantum threats emerge [5][3]. Vendors relying on rigid, outdated encryption methods are inherently riskier than those with flexible systems designed to accommodate algorithm changes. Also, evaluate whether vendors have started planning their transition to post-quantum cryptography and if they understand the urgency for healthcare organizations to act. These detailed risk profiles will form the foundation for setting contractual quantum-readiness standards.
Adding Quantum Requirements to Vendor Contracts
Vendor contracts must now explicitly mandate the adoption of Post-Quantum Cryptography (PQC) algorithms and adherence to relevant standards [4][1][3]. Clearly specify which algorithms vendors need to implement and include timelines for transitioning to PQC that align with federal and international guidelines [4][1][3]. For assets like medical devices, which often have long lifecycles, contracts should require quantum-safe algorithms at the time of certification or procurement since updating them later can be challenging [4][17].
In addition to algorithm requirements, contracts should require vendors to inventory their cryptographic systems, assess quantum risks, and put quantum-safe controls in place. Vendors must also demonstrate cryptographic agility, ensuring they can adapt quickly as encryption standards evolve [5][3]. These contractual obligations are critical for ensuring that your vendor ecosystem remains secure in the face of quantum advancements.
sbb-itb-535baee
Implementation Roadmap for Post-Quantum Vendor Security
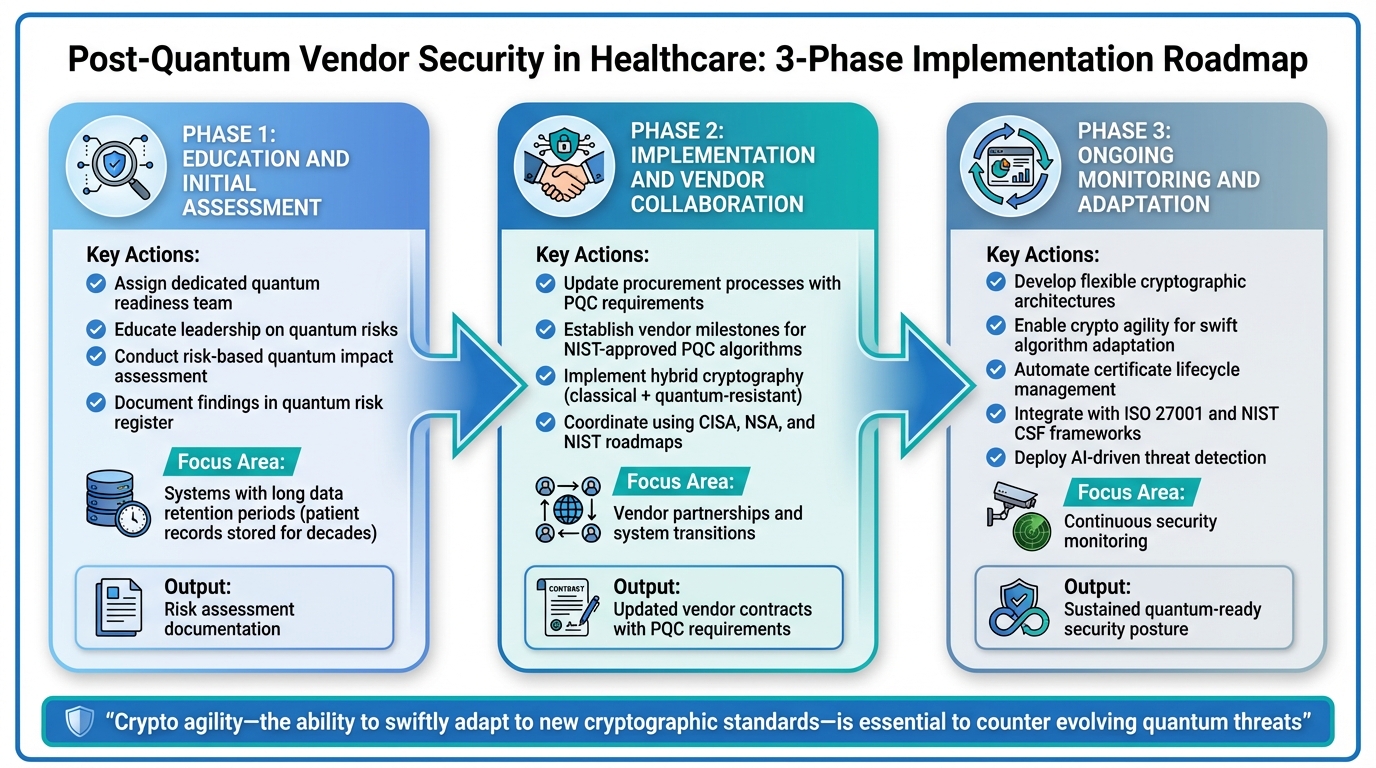
3-Phase Roadmap for Healthcare Quantum Readiness Implementation
Healthcare organizations aiming for quantum readiness need a clear, phased approach. Breaking the process into manageable steps ensures that efforts build logically on existing vendor risk frameworks. This roadmap aligns with earlier strategies to provide a comprehensive pathway toward post-quantum security.
Phase 1: Education and Initial Assessment
The journey begins with building internal expertise. Assign a dedicated team to lead quantum readiness efforts [2]. Educate leadership about quantum computing's potential risks and opportunities, as this understanding is critical for securing the necessary budget and resources. Without executive support, progress can stall.
Conduct a risk-based quantum impact assessment [4] to pinpoint systems, data, and vendor relationships most vulnerable to quantum threats. Pay special attention to data with long retention periods, such as patient records stored for decades - prime targets for "Harvest Now, Decrypt Later" attacks. Document these findings in your existing quantum risk register to guide future actions.
Phase 2: Implementation and Vendor Collaboration
Once internal risks are understood, the focus shifts to working with vendors. Collaborating with technology vendors is key to transitioning to post-quantum cryptography (PQC) [13]. Update procurement processes to include PQC requirements and establish clear milestones for vendors, such as deadlines for adopting NIST-approved PQC algorithms [4][2].
During this period, consider using hybrid cryptography, which combines classical and quantum-resistant algorithms. This approach maintains compatibility with existing systems while gradually introducing quantum-safe measures [13][3]. It minimizes disruption and gives vendors time to adjust their infrastructure. Coordinate these efforts using guidance from CISA, NSA, and NIST roadmaps [3].
Phase 3: Ongoing Monitoring and Adaptation
Quantum readiness is not a one-and-done effort.
"To counter evolving threats, organizations should prioritize crypto agility - the ability to swiftly adapt to new cryptographic standards, whether driven by regulatory changes or emerging technologies like quantum computing" [5].
Organizations should develop flexible cryptographic architectures that allow for easy algorithm swaps as standards evolve and new threats emerge [3][5]. Continuous monitoring is essential to stay ahead of potential vulnerabilities. For instance, in April 2025, Sectigo highlighted its Certificate Lifecycle Management (CLM) solutions, such as Sectigo Certificate Manager, which automate certificate renewal, provide centralized oversight, and proactively detect vulnerabilities - all while supporting quantum-safe encryption [5].
Integrate quantum readiness into broader cybersecurity frameworks like ISO 27001 and NIST CSF for a more cohesive strategy [4]. Automated tools for cryptographic inventory and AI-driven threat detection will also play a critical role in maintaining security as quantum technologies advance [1][5].
Governance and Measurement for Quantum Vendor Risk
Setting Up Governance for Quantum Risks
A solid governance framework is crucial for managing the evolving challenges posed by quantum risks. Preparing for quantum advancements requires active involvement and oversight at the executive level. Healthcare organizations, in particular, should create a quantum risk oversight committee that includes leaders from IT, legal, compliance, and clinical departments. This diverse group ensures that quantum threats are examined from various angles, including technical vulnerabilities, regulatory requirements, and patient safety.
Executive support is critical. As Mayer Brown emphasizes:
"Organisations must adopt a risk-mindset approach to learn, evaluate, and manage the complex opportunities, risks, and challenges associated with quantum computing" [2].
This approach demands a shift from passive observation to proactive planning. The oversight committee should meet regularly to monitor progress on vendor quantum readiness, allocate resources for post-quantum cryptographic (PQC) transitions, and align with federal guidelines from agencies like NIST, NSA, and CISA. Appointing a team lead to coordinate these efforts across departments and report directly to the board ensures accountability and consistent progress. These governance steps lay the foundation for tracking performance effectively and adapting strategies as needed.
Metrics for Tracking Vendor Quantum Readiness
To gauge progress, organizations need clear, measurable metrics. Key indicators include the percentage of vendors who submit PQC transition roadmaps and complete cryptographic inventories. Another critical metric is the adoption rate of NIST-approved PQC algorithms, such as CRYSTALS-Kyber and CRYSTALS-Dilithium, in new deployments.
The urgency of these efforts is highlighted by industry statistics:
- Only 5% of technology professionals see quantum computing as a high priority.
- Just 7% have a solid understanding of NIST's updated standards.
- 62% are concerned that quantum computers could break current encryption before PQC is fully implemented [18].
These numbers reveal significant gaps in awareness and preparedness. Other useful metrics include tracking vendors' implementation of zero-trust architectures, the completion rates of quantum risk assessments, and timelines for upgrading legacy systems - especially IoT medical devices, which often face unique challenges during migration.
Using Censinet RiskOps for Quantum Risk Governance

Technology solutions can simplify the process of managing quantum risks. Censinet RiskOps provides a centralized platform for overseeing vendor risks, including those related to quantum computing. This tool consolidates risk data across the vendor ecosystem, making it easier to perform assessments and automate workflows that notify key stakeholders. By integrating quantum readiness metrics - such as PQC transition roadmaps and cryptographic inventories - into its framework, Censinet RiskOps enables organizations to make informed decisions and stay compliant with evolving regulations.
With real-time dashboards offering visibility into critical metrics, organizations can better monitor vendor quantum readiness and adjust their strategies as post-quantum standards continue to evolve. This comprehensive approach strengthens the ability to secure vendor ecosystems against the challenges posed by quantum advancements.
Conclusion: Getting Ready for Quantum Computing in Healthcare
Quantum computing is no longer a distant possibility; it’s a looming reality that could compromise the encryption protecting today’s healthcare data. Waiting to act increases the risk of "harvest now, decrypt later" attacks, where attackers steal encrypted data now, intending to crack it later using quantum technology [1][2][3][4][5].
The U.S. healthcare sector faces distinct challenges. A staggering 80% of breaches are tied to third-party vendors [6], and the industry’s long-term data retention practices only intensify the potential fallout. Encryption methods like RSA and ECC, which currently protect sensitive patient information, medical devices, and clinical systems, will eventually fail against quantum computing, exposing data collected today to future risks.
Preparing for this shift isn’t simple. Transitioning to post-quantum cryptography calls for meticulous planning, detailed cryptographic inventories, and upgrades across infrastructure - steps that need to be in motion well before "Q-Day" arrives. Healthcare organizations should start by building stronger quantum risk governance and gradually adopting the algorithms approved by NIST. This phased approach - focused on education, vendor collaboration, implementation, and continuous monitoring - lays the groundwork for tackling these emerging threats.
In this dynamic environment, tools like Censinet RiskOps™ play a critical role. By centralizing quantum risk data, streamlining vendor security assessments, and simplifying workflows, this platform supports a proactive approach to vendor risk management. It equips healthcare organizations to strengthen their cybersecurity defenses and address the challenges posed by quantum advancements head-on.
FAQs
When should healthcare organizations start adopting quantum-resistant cryptography?
Healthcare organizations need to start integrating quantum-resistant cryptography sooner rather than later to address the increasing risks associated with quantum computing. Experts suggest beginning this transition by 2026 to stay ahead of emerging threats and align with expected regulatory updates.
To fully protect against quantum-powered cyberattacks, completing the transition by 2030 is recommended. Taking action now will help secure sensitive data and ensure compliance in an evolving technological landscape.
Which healthcare vendors are most at risk from quantum computing threats?
Healthcare vendors facing the greatest risks from quantum computing are those heavily reliant on cryptographic safeguards that could be undermined by quantum advancements. These include:
- Medical device manufacturers: Devices like pacemakers or insulin pumps depend on secure communication protocols that quantum computing could potentially compromise.
- Healthcare IT systems: Platforms managing electronic health records (EHRs) or telemedicine services handle highly sensitive patient data, making robust encryption essential.
- Connected IoT devices: Internet-enabled devices, such as wearables and monitoring systems, rely on current cryptographic standards, leaving them particularly vulnerable.
With the rapid progress of quantum computing, these vendors need to implement quantum-resistant security solutions to protect patient data and ensure compliance with industry regulations.
How can healthcare organizations ensure their vendors are ready for quantum computing risks?
Healthcare organizations can tackle quantum computing risks by teaming up with their vendors to adopt post-quantum cryptography and roll out quantum-resistant encryption solutions. The first step is conducting detailed risk assessments to pinpoint vulnerabilities within vendor systems. Make sure these systems align with emerging standards, such as NIST's Post-Quantum Cryptography (PQC) guidelines, and comply with federal mandates like CNSA 2.0.
Ongoing audits and constant monitoring are essential to staying ahead of potential threats. Work with vendors to implement phased technology upgrades and scalable solutions that reduce disruptions. Building strong partnerships with vendors will play a key role in securing IT systems and protecting sensitive data as quantum technology advances.


