RBAC Best Practices for Securing Clinical Applications
Post Summary
Role-Based Access Control (RBAC) is a proven method to secure sensitive healthcare data while maintaining efficient workflows. Clinical systems like EHRs contain critical patient information, making them a prime target for cyberattacks. RBAC assigns permissions based on job roles (e.g., nurse, physician) rather than individuals, ensuring data access is both secure and aligned with responsibilities.
Key Takeaways:
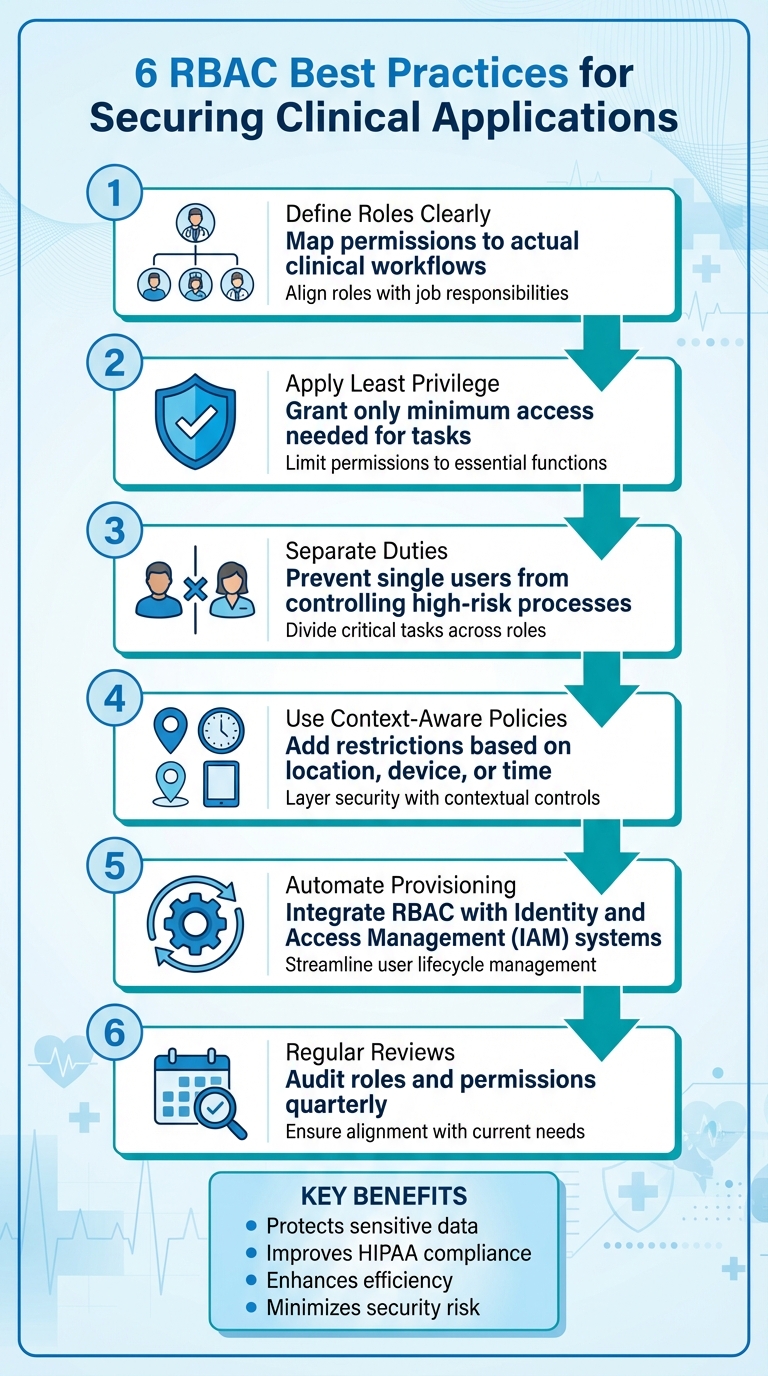
- Protects sensitive data: Limits access to only what's necessary for each role.
- Improves compliance: Meets HIPAA and other regulatory requirements.
- Enhances efficiency: Reduces clutter by tailoring access to job functions.
- Minimizes risk: Restricts potential damage from credential theft.
Best Practices:
- Define roles clearly: Map permissions to actual clinical workflows.
- Apply least privilege: Grant only the minimum access needed for tasks.
- Separate duties: Prevent single users from controlling high-risk processes.
- Use context-aware policies: Add restrictions based on location, device, or time.
- Automate provisioning: Integrate RBAC with Identity and Access Management (IAM) systems.
- Regular reviews: Audit roles and permissions quarterly to ensure alignment with current needs.
RBAC is not a one-time setup. It requires ongoing updates to adapt to evolving technologies, workflows, and threats. By implementing these practices, healthcare organizations can safeguard patient data, streamline operations, and maintain compliance.
6 RBAC Best Practices for Healthcare Security and Compliance
Designing and Managing RBAC in Healthcare
Building an effective Role-Based Access Control (RBAC) system in healthcare starts with a deep understanding of clinical workflows. The primary objective is to safeguard patient data while ensuring that care delivery remains smooth and uninterrupted. This involves creating roles that align closely with actual job responsibilities, all while keeping the permission structure straightforward and manageable. A good starting point is mapping out workflows across various departments. For example, what does an inpatient nurse do differently from an outpatient scheduler? What data does a billing coder need access to compared to a pharmacy technician? This kind of detailed inventory lays the groundwork for defining standardized roles that can scale effectively across the organization. The strategies below outline key approaches to designing and managing RBAC tailored to healthcare needs.
Least Privilege and Role Granularity
The principle of least privilege is foundational to RBAC: every role gets access to only what’s absolutely necessary for its tasks - no more, no less. Permissions should be defined by specific actions, such as viewing lab results, signing orders, or posting charges, and access should be limited to relevant patient contexts. For instance, a medical assistant might update patient demographics and record vital signs but shouldn’t be able to prescribe medications or view sensitive behavioral health records.
Striking the right balance in role granularity is essential. Start with base roles tied to licensure and core job functions - like physician, registered nurse, pharmacist, or medical coder. Then, add variations only when there are clear differences in workflows or risks. For example, an emergency department nurse may need different permissions than an inpatient nurse, and a charge nurse might require additional approval capabilities. To keep things manageable, aim for a concise catalog of standard roles, using metrics like the number of roles per department and how often exceptions occur to guide adjustments.
Separation of Duties
Separation of duties is a critical safeguard to prevent any single individual from having unchecked control over high-risk processes. In clinical settings, this means dividing tasks such as ordering, dispensing, and administering medications among different roles. For example, prescribers can sign orders, but they shouldn’t mark doses as administered, while nurses can handle medication administration but shouldn’t create their own orders. Similarly, splitting responsibilities for charge entry, coding, payment posting, and refund processing helps mitigate the risk of billing fraud.
To enforce these controls, configure them directly in systems like your EHR, pharmacy software, or revenue cycle applications. This ensures that no single role can independently complete sensitive workflows. A formal separation-of-duties matrix, which maps tasks (e.g., creating and approving prescriptions) to specific roles, can further reinforce these safeguards.
Context-Aware Access Policies
Context-aware access policies take RBAC a step further by adding conditions like location, time, device security, or network type to standard permissions. These policies help reduce risk without disrupting care. For instance, full chart editing might only be allowed on secure, on-premises networks or managed devices, while remote access could be limited to read-only functions unless telehealth documentation is involved. After-hours access to patient records might require additional approval, and high-risk actions like prescribing controlled substances could mandate multi-factor authentication.
To implement these policies effectively, integrate them with identity and access management systems, VPNs, and endpoint tools so that contextual signals are factored into authentication. Start by testing these measures in low-risk workflows, gather feedback from clinicians, and fine-tune the policies to ensure patient safety isn’t compromised. In emergencies, having a "break-glass" option is vital - this allows temporary access to restricted data, provided that a reason is documented, activities are logged, and any anomalies are reviewed by a compliance or privacy committee.
For additional efficiency, integrating RBAC with a centralized risk management platform, like Censinet RiskOps™, can streamline compliance efforts and simplify risk assessments across all clinical applications.
Implementing RBAC for Scalability and Efficiency
Rolling out Role-Based Access Control (RBAC) in a large healthcare organization requires thoughtful planning and execution. The process hinges on early standardization of role definitions, automating user provisioning, and ensuring permissions are aligned across clinical systems. By doing this, RBAC reduces the need for manual IT work, speeds up onboarding, and ensures consistent access. Organizations that adopt a phased, well-structured approach often see fewer IT support requests, quicker access for new hires, and improved compliance with HIPAA regulations.
Here’s how to approach RBAC implementation effectively while keeping it scalable and efficient.
Phased Rollout and Testing
Start with a detailed assessment of your current environment. This means cataloging every user, their permissions, the roles they fulfill, and the applications they use - whether it’s EHR, PACS, lab systems, pharmacy, billing, or others. This discovery process highlights permissions that are too broad or too limited and identifies workflows that could be disrupted by sudden changes.
Next, create role templates that reflect actual job functions. For example, roles might include attending physician, resident, registered nurse, medical assistant, pharmacist, registrar, or billing specialist. Test these roles in a staging environment by having clinicians perform routine tasks - like entering orders, reviewing lab results, documenting visits, or administering medications. This ensures each role has the access needed to complete essential workflows without unnecessary permissions.
Before rolling out RBAC across the entire organization, pilot the system in a single department or unit. For instance, you could start in the emergency department or an outpatient clinic. Monitor key metrics such as access-related incidents, task completion times, help desk tickets, and any delays in patient care. Use the insights from this pilot to refine roles and permissions before expanding to other departments in phases. This step-by-step rollout minimizes risks in critical, always-on environments like hospitals, where access disruptions can’t be tolerated.
Integration with Identity and Access Management Systems
Integrating RBAC with an Identity and Access Management (IAM) system streamlines the user lifecycle and eliminates delays caused by manual provisioning. For example, when HR creates a new record for an ICU nurse, the IAM system automatically assigns the appropriate RBAC role across all clinical applications. This ensures "day-one access", allowing new staff to start work immediately without waiting for IT to process tickets. Regular role-level access reviews can also be conducted more efficiently, reducing the need to examine individual accounts.[2]
Automation also simplifies role changes and terminations. If a nurse moves from the ICU to the emergency department, the IAM system updates permissions across all systems in real time. Similarly, when an employee leaves, their access is revoked across the board, reducing security risks and ensuring compliance. Linking role assignments to authoritative data sources - like clinical specialty, unit assignment, or work schedules - keeps permissions accurate and aligned with actual job responsibilities.
Cross-Application Role Alignment
After automating system-wide processes, the next step is aligning roles across all applications. Healthcare organizations often manage dozens of clinical systems, each with its own permission structure. Without coordination, this can lead to a tangle of inconsistent roles that are hard to manage or audit. The solution is to establish an enterprise role catalog that defines standardized roles and maps them to application-specific permissions.[2][7]
For instance, an "Inpatient RN" role in the IAM platform might correspond to specific access levels in the EHR, a view-only role in PACS for reviewing imaging, and medication administration permissions in the pharmacy system. Centralizing these mappings ensures consistent access for a nurse across all systems and eliminates redundant role creation.
To manage complexity, use base roles with limited modifiers. Instead of creating separate roles for every possible variation - like ICU nurses at different facilities - define a single "Registered Nurse" base role and adjust access using attributes like location or unit.[6] This approach keeps the role catalog manageable while meeting the diverse needs of multi-site hospitals, outpatient clinics, and specialty practices.
Standardize role naming conventions across all systems so they’re easy to identify and audit. Conduct periodic cross-system access reviews, involving data owners from each clinical system to confirm that role mappings align with current workflows. This is especially important as new technologies or processes are introduced.[3][4] For healthcare organizations juggling multiple vendors and clinical applications, tools like Censinet RiskOps™ can help centralize RBAC governance, simplify compliance, and streamline risk assessments.
sbb-itb-535baee
Maintaining and Improving RBAC Over Time
RBAC isn't a "set it and forget it" framework - it needs to evolve alongside clinical workflows, technology advancements, and regulatory changes. Without regular upkeep, roles can become outdated, permissions can pile up unnecessarily, and security vulnerabilities may arise. Organizations that treat RBAC as a continuous process often see real benefits, including smoother workflows, fewer disruptions, and lower error rates in operations.[3][6]
Regular Access Reviews and Audits
Conducting regular access reviews is crucial, particularly for high-risk roles like prescribing clinicians, billing administrators, and staff with extensive PHI access. These reviews should happen at least quarterly for high-risk roles and annually for all others to align with HIPAA and Joint Commission audit guidelines.[2][6] Start by reviewing roles to ensure permissions match current workflows, then verify individual assignments through user-to-role attestations. Department heads and managers should confirm that each team member still requires their assigned roles, paying close attention to temporary staff like locum providers, residents, and contractors, who often experience frequent role changes.[3][6]
Audits should focus on recent high-risk activities, such as ePHI exports, medication orders, or billing changes, tracing them back to specific roles. Be on the lookout for red flags like users holding more roles than their peers, accounts with overlapping access to clinical and financial systems (which can breach separation of duties), shared accounts, and dormant accounts that need deactivation.[4][5][6] Automated tools can help by generating exception reports, making it easier for auditors to identify and address these issues on a set schedule.[2]
Once audits confirm that role definitions are stable, you can update RBAC to accommodate new technologies without disruption.
Adapting to New Technologies
Bringing new technologies into the mix - such as telehealth platforms, AI-driven tools, cloud-based systems, or remote monitoring devices - requires careful planning. Before rolling out these tools, conduct a role impact assessment to map existing roles to the new system's capabilities and identify any additional permissions needed.[3][5][6] Start with a pilot group to confirm that permissions align with clinical workflows while avoiding unnecessary PHI exposure.[3][7] Then, update RBAC documentation and train staff on any changes to their access.
For healthcare organizations juggling multiple vendors and systems, platforms like Censinet RiskOps™ can centralize RBAC management, simplify compliance tracking, and make risk assessments more manageable as new technologies are introduced.
Monitoring and Metrics for RBAC Performance
Insights from audits should fuel ongoing improvements, and these changes should be measured with clear KPIs. Track metrics like the number of access violations or policy exceptions (e.g., unauthorized chart access or failed login attempts), the time it takes to provision or deprovision users, the number of users with excessive or conflicting permissions, and the percentage of on-time access reviews completed by managers.[2][3][7]
On the compliance side, monitor audit findings related to access control, how quickly issues are resolved, and the percentage of systems with fully implemented RBAC integrated with single sign-on. Operationally, keep an eye on help-desk tickets tied to access problems, the time clinicians spend locating necessary data, and workflow improvements following role adjustments.[3][4][6]
Track these metrics across key applications like EHR, PACS, telehealth, and revenue cycle management to pinpoint areas needing improvement. Regularly reviewing these KPIs with leadership not only highlights the value of RBAC but also helps secure the resources needed to maintain and refine it. This ensures that both risk reduction and workflow efficiency remain at the forefront.
Conclusion
RBAC isn’t just a technical feature - it’s a critical component for safeguarding patient data, complying with regulations, and improving clinical workflows. By designing RBAC systems based on the principles of least privilege and creating specific, well-defined roles, healthcare organizations can minimize the risks of data breaches while making systems easier to use. This approach also strengthens compliance by offering essential controls and traceability.
A strong RBAC framework doesn’t just enhance security - it also improves operational efficiency. Centralized permission management simplifies onboarding and offboarding processes and aligns access with everyday workflows. For instance, AZZLY Rize, a behavioral health platform, reported a 35% increase in workflow efficiency after adopting RBAC [3]. These gains are particularly valuable as healthcare organizations face increasing data breach costs and stricter regulations.
However, implementing RBAC isn’t a one-and-done process. Continuous governance is essential. Treating RBAC as an evolving program ensures that roles stay aligned with new technologies and changing care models.
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare."
- Matt Christensen, Sr. Director GRC at Intermountain Health [1]
Platforms like Censinet RiskOps™ help healthcare organizations manage RBAC more effectively by centralizing role management, simplifying compliance tracking, and enabling continuous updates as technologies advance.
To make RBAC truly effective, security and clinical leaders should focus on aligning roles across applications, integrating RBAC with identity and access management (IAM) and HR systems for automated provisioning, and setting clear performance metrics. By grounding RBAC in actual job responsibilities and maintaining ongoing governance, healthcare organizations can protect patient data, reduce administrative strain, and scale access management seamlessly as they grow.
FAQs
How does RBAC help healthcare organizations comply with regulations like HIPAA?
Role-Based Access Control (RBAC) plays a critical role in helping healthcare organizations meet HIPAA requirements by limiting access to sensitive patient data based on specific user roles. This approach ensures that only those with proper authorization can view or update Protected Health Information (PHI), significantly lowering the chances of data breaches.
Another key advantage of RBAC is its ability to generate detailed audit trails. These records are essential for showing compliance during regulatory inspections. Beyond safeguarding patient privacy, RBAC also provides a secure framework for managing clinical applications and other healthcare systems efficiently.
What are the advantages of combining RBAC with Identity and Access Management systems?
Combining Role-Based Access Control (RBAC) with Identity and Access Management (IAM) systems brings several advantages to clinical applications. It streamlines how user permissions are managed by offering a centralized, consistent framework. This not only simplifies administrative tasks but also enhances overall security.
Another benefit is flexibility. As organizations expand or adjust, permissions can be updated with ease, making the system adaptable to changing needs. It also plays a critical role in meeting healthcare regulations by aligning access controls with specific roles, which helps reduce the chances of unauthorized access to sensitive clinical information. On top of that, the integration speeds up onboarding and offboarding, ensuring user access is efficiently managed throughout their time with the organization.
What steps can healthcare organizations take to keep their RBAC systems secure and effective?
To keep Role-Based Access Control (RBAC) systems secure and efficient, healthcare organizations should make it a priority to regularly review and update user roles. This ensures that access permissions stay in sync with any changes in job duties. Performing periodic access audits is another important step - it helps confirm that users have the right level of access and reduces the risk of unnecessary or excessive permissions.
Using advanced tools, like AI-powered platforms, can take RBAC management to the next level. These tools can provide real-time risk assessments and simplify the handling of sensitive data, such as patient records and clinical systems. Consistent monitoring, paired with proactive updates, plays a vital role in maintaining security and staying compliant over time.


