How Real-Time Monitoring Improves Cybersecurity
Post Summary
Real-time monitoring is transforming cybersecurity in healthcare by addressing threats as they happen, minimizing disruptions to patient care, and ensuring compliance with regulations like HIPAA. Unlike periodic audits, which leave gaps, real-time systems provide continuous insights into networks, devices, and user activity. This allows security teams to act quickly, reducing the impact of ransomware, data breaches, and system downtimes.
Key Takeaways:
- Immediate Threat Detection: Identifies and isolates risks like ransomware or unauthorized access before they spread.
- Healthcare-Specific Challenges: Accounts for outdated systems, vulnerable medical devices, and complex vendor networks.
- Regulatory Compliance: Simplifies audits with automatic logs and alerts for policy violations.
- AI and Automation: Enhances monitoring by analyzing patterns, prioritizing alerts, and automating responses.
Real-time monitoring is crucial for safeguarding patient safety and maintaining operational stability in healthcare environments. By focusing on critical systems like EHRs and medical devices, organizations can proactively mitigate risks and ensure uninterrupted care.
How Real-Time Monitoring Improves Healthcare Cybersecurity
Real-time monitoring dramatically reduces the time it takes to detect and neutralize cyber threats. Security teams can act within seconds or minutes, which is especially critical in healthcare where even brief system downtimes can have serious consequences - canceled surgeries, rerouted ambulances, and interrupted patient care [2][3]. Beyond protecting patients, this quick action simplifies compliance efforts and streamlines incident management.
Detecting and Preventing Security Risks
Continuous monitoring catches threats that periodic audits might miss. For instance, if a non-authorized user suddenly tries to access sensitive patient records or downloads a large volume of data, real-time systems immediately flag the activity for review [3]. Similarly, if ransomware begins encrypting files on a shared drive, monitoring tools can isolate the affected systems before the attack spreads [3][9]. By analyzing access patterns, these tools can also detect repeated unauthorized attempts by staff to access areas outside their roles, enabling teams to revoke credentials, segment networks, or shut down suspicious processes - all before patient care is impacted [2][3][9].
Modern Security Information and Event Management (SIEM) tools use machine learning to establish what "normal" behavior looks like for users and devices. They can then detect unusual activity - like access during odd hours or unexpected data transfers - in real time [3]. This is especially important in healthcare, where thousands of connected devices, including many running outdated software with default passwords, create a vast attack surface [2][14]. Real-time detection platforms also evaluate device risk continuously, considering vulnerabilities, network activity, and known threat indicators. This helps security teams prioritize their efforts effectively [2].
Faster Incident Response
Once a threat is identified, responding quickly is crucial. Real-time monitoring significantly reduces both the mean time to detect (MTTD) and the mean time to respond (MTTR) by triggering prioritized alerts the moment anomalies are spotted [3][9]. SIEM tools enhance these alerts with contextual information about users, assets, and threats, enabling faster decision-making [3]. Many systems also include automated response protocols. For example, when ransomware-like behavior is detected, the system can isolate the affected workstation, block suspicious IP addresses, and notify the security team - all without manual intervention [3][9].
This level of automation is vital in healthcare, where even brief downtimes in electronic health records or clinical systems can delay care. Faster containment translates to fewer canceled procedures, less ambulance rerouting, and reduced reliance on manual, paper-based workflows [3][11]. Continuous monitoring ensures that healthcare organizations can detect and address suspicious activity quickly, reducing the risk of major breaches and minimizing disruptions to critical services [3]. A 2024 study published by the National Library of Medicine found that ransomware incidents in healthcare were linked to longer hospital stays and higher mortality rates, underscoring how early detection and rapid response can save lives [7].
Meeting Regulatory Requirements
With patient care on the line, continuous monitoring also helps organizations meet stringent healthcare regulations. Real-time systems simplify compliance with frameworks like HIPAA and HITRUST by automatically generating detailed audit trails of detected threats, responses, and system changes [2][3]. Instead of scrambling to gather evidence during an audit, organizations have a steady stream of documentation showing their ongoing efforts to protect sensitive data. These systems flag policy violations and retain logs, making it easier to demonstrate to auditors and regulators that the organization is continuously safeguarding Protected Health Information (PHI) [2][3].
This kind of continuous vigilance is increasingly important as insurers and regulators demand proof of robust detection and response capabilities to mitigate cyber risks [7][12]. Platforms like Censinet RiskOps™ offer healthcare-specific solutions that integrate real-time monitoring, automated risk scoring, and compliance tools, providing a comprehensive approach to cybersecurity tailored to the industry's unique challenges.
How to Implement Real-Time Monitoring
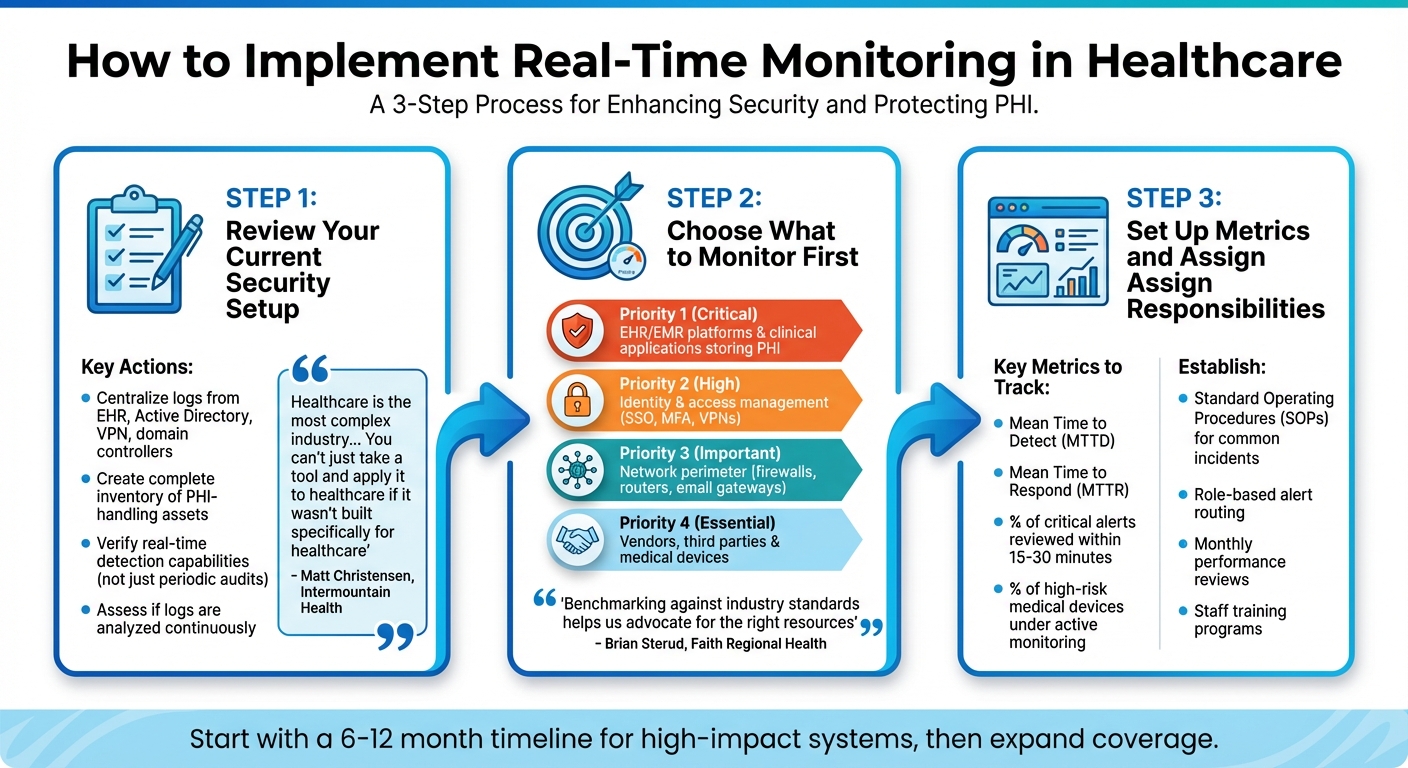
3-Step Implementation Guide for Real-Time Cybersecurity Monitoring in Healthcare
Getting started with real-time monitoring involves assessing your existing systems and focusing on those crucial for patient safety and data security. Here's how you can approach it step by step.
Review Your Current Security Setup
First, ensure all critical systems send logs to a centralized platform. This includes logs from your EHR, Active Directory, VPN, domain controllers, and clinical systems, which are essential for correlation and investigations [3]. Make a complete inventory of assets that handle Protected Health Information (PHI), including medical devices [2]. Check whether your tools allow for real-time detection rather than relying solely on periodic audits. Many healthcare organizations find they collect plenty of logs but fail to analyze them continuously, which undermines the purpose of real-time monitoring.
Matt Christensen, Sr. Director of GRC at Intermountain Health, emphasizes: "Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare" [1].
This highlights the importance of ensuring your tools are tailored to healthcare's unique workflows, devices, and regulations. Platforms like Censinet RiskOps™ provide healthcare-specific features that combine risk assessments, benchmarking, and monitoring, moving organizations away from outdated spreadsheet methods.
Choose What to Monitor First
Based on your assessment, start by prioritizing systems that store PHI, such as EHR/EMR platforms and key clinical applications [3] [7]. These systems should have robust access monitoring, alerts for unusual activity, and mechanisms to detect privilege misuse. Next, focus on identity and access management tools, including directory services, single sign-on, multi-factor authentication, and VPNs. Monitor for red flags like unusual login patterns, off-hours access, or privilege escalation attempts [3].
Expand monitoring to your network and perimeter systems, such as firewalls, routers, wireless controllers, and secure email gateways, to detect suspicious external connections or lateral movement within your network [2] [3]. Don’t overlook vendors, third parties, and medical devices that interact with PHI [1].
Brian Sterud, CIO at Faith Regional Health, notes: "Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters" [1].
Using these benchmarks can guide your focus and help you identify areas that need the most attention.
Set Up Metrics and Assign Responsibilities
Once you've identified and prioritized systems, establish clear metrics to measure the effectiveness of your monitoring. Track key indicators like Mean Time to Detect (MTTD), Mean Time to Respond (MTTR), and the percentage of critical alerts reviewed within 15–30 minutes. Define KPIs, such as the percentage of high-risk medical devices under active monitoring, and create standard operating procedures (SOPs) for common incidents like ransomware, lost devices, unusual EHR access, or compromised vendor accounts [3] [7].
Set up role-based alert routing to ensure timely triage and investigation. For example, IT and network teams can handle tasks like isolating hosts, segmenting networks, and applying patches. Conduct monthly reviews to assess monitoring performance, analyze incident trends, and adjust rules or thresholds to reduce false positives [2] [3]. Additionally, train clinical, IT, and leadership teams on monitoring protocols and response actions, ensuring these processes don’t interfere with patient care [7] [14].
sbb-itb-535baee
Using Automation and AI for Real-Time Monitoring
Automation and AI have become essential tools for cybersecurity teams, especially in managing the overwhelming amount of data and complex threats in healthcare environments. These technologies allow organizations to scale their monitoring efforts, tackling repetitive tasks and identifying advanced threats that traditional methods often overlook. This builds upon the principles of continuous monitoring, offering a way to address the ever-changing challenges in healthcare cybersecurity.
Automate Repetitive Monitoring Tasks
One of the first steps is automating time-consuming security tasks. For example, automated vulnerability scanners can continuously check servers, endpoints, and medical devices for missing patches or misconfigurations, flagging issues for quick resolution [2][9]. Similarly, configuration management tools can compare device settings against approved baselines and automatically create remediation tickets for any deviations [2].
Platforms like SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response) take automation further by analyzing logs, correlating events, and prioritizing critical alerts. This frees up analysts to focus on more pressing threats [2][9]. For instance, automation can filter out low-priority alerts, such as routine port scans, and prioritize more serious issues like credential misuse on remote patient monitoring devices [4][9].
Terry Grogan, CISO at Tower Health, highlighted the impact of automation, saying: "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." [1]
Similarly, James Case, VP & CISO at Baptist Health, noted: "Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." [1]
AI for Detecting Advanced Threats
AI and machine learning bring a new level of sophistication to threat detection. These systems learn normal behavior patterns, making it easier to identify anomalies like insider misuse, account takeovers, or lateral movement within networks [15][10]. In healthcare, for instance, AI models can monitor the typical communication behavior of medical IoT devices, such as infusion pumps, and flag unusual activity, like unexpected external connections or potential data exfiltration attempts [2][5].
AI also excels at connecting subtle signals across multiple data sources - like EHR logs, VPN access logs, and cloud activity - to detect threats that traditional tools might miss [15][10]. For example, it can identify a compromised account by piecing together unusual login locations, irregular queries on PHI records, and abnormal file transfers. AI-powered platforms have even stopped ransomware in its early stages by recognizing suspicious encryption-like file operations and isolating affected systems before the attack could spread [15].
Given the interconnected and time-sensitive nature of U.S. healthcare networks, AI's ability to process data in real time is invaluable. It enables earlier detection of sophisticated threats and can even perform autonomous responses, such as temporarily blocking suspicious activity, while minimizing disruptions to clinical operations [5][15][10].
Maintain Human Oversight of AI Systems
Despite AI's capabilities, human oversight remains critical. AI systems can misclassify events, act on incomplete information, or introduce biases, which could lead to errors like inappropriate blocking or missed incidents [15][10]. Solely relying on AI without human review can also create compliance risks, especially if actions cannot be explained or justified [5][15].
To address this, organizations should establish detailed, risk-based playbooks that outline what automated actions are permissible under specific circumstances. For example, automatically quarantining a non-critical device might be acceptable, but anomalies involving life-support systems should trigger alerts for human review instead [2][14]. Regular governance processes, including reviews of AI detections and false positives, can help fine-tune these systems. Collaboration between security teams and clinical staff is also essential for mapping system criticality, testing automated responses, and conducting simulation exercises [5][14].
Transparency is key to building trust in AI systems. Security teams need to understand why a particular alert or action occurred, ensuring compliance with regulations and maintaining confidence in the technology. Staff should also be trained on AI’s limitations, emphasizing that it is a tool to enhance - not replace - human judgment in both clinical and security contexts.
Conclusion
Real-time monitoring is reshaping how healthcare organizations protect patient data and maintain operational stability. Unlike periodic audits that provide a limited snapshot of security, continuous monitoring offers an ongoing, comprehensive view. This approach brings three key advantages: quicker threat detection and response - reducing threat dwell time from weeks or months to just hours or minutes [13]; proactive risk management across intricate hospital networks; and consistent compliance with HIPAA and other regulations through detailed, time-stamped audit trails.
From 2018 to 2022, healthcare data breaches rose by 93%, with exposed records skyrocketing by 278% [7]. Ransomware attacks have a direct impact on patient care, contributing to higher in-hospital mortality rates, delays in emergency treatment, and extended hospital stays [7][8][14]. Real-time monitoring plays a crucial role in safeguarding patient care by preventing disruptive outages, care diversions, and canceled procedures that can jeopardize lives.
Healthcare leaders - whether in large integrated delivery networks, community hospitals, or specialty clinics - should start by evaluating their current monitoring capabilities. Priority should be given to critical systems like electronic health records (EHRs), picture archiving and communication systems (PACS), pharmacy applications, and life-critical medical devices. Setting clear, achievable goals - such as centralizing log collection for high-impact systems within a 6–12 month timeline - can help organizations establish a strong foundation. From there, monitoring can be expanded to include devices and vendor networks [2][3][6]. Tools specifically designed for healthcare, like Censinet RiskOps, support this process by offering continuous risk monitoring, third-party risk management, and benchmarking across vendors, clinical applications, and medical devices, enabling real-time risk reduction.
To sustain these efforts, real-time monitoring requires regular updates to AI models and detection rules, ongoing staff training, and iterative improvements based on lessons from past incidents [3][7][10]. While automation and AI excel at analyzing vast amounts of data and identifying subtle patterns, human expertise remains indispensable. Skilled professionals are needed to validate alerts, make informed decisions about clinical risks, and ensure that continuous monitoring translates into dependable patient care [3][10].
FAQs
What makes real-time monitoring more effective than periodic audits in healthcare cybersecurity?
Real-time monitoring provides constant insight into your cybersecurity landscape, enabling the instant identification and handling of potential threats. By actively addressing risks as they emerge, this approach lowers the chances of breaches or interruptions.
On the other hand, periodic audits evaluate security measures at set times, which can leave gaps where new or active threats might go unnoticed between check-ins. With real-time monitoring, healthcare organizations can better protect sensitive data, such as patient records and medical information, staying prepared for ever-changing risks.
How does AI improve real-time cybersecurity monitoring in healthcare?
AI is transforming real-time cybersecurity monitoring by offering continuous risk assessments, spotting unusual activity, and delivering actionable insights through advanced analytics and machine learning. These tools enable healthcare organizations to swiftly detect and address potential threats, minimizing vulnerabilities and bolstering overall security.
By automating complex tasks and processing massive datasets in real time, AI safeguards sensitive patient information, such as PHI and medical device data, while ensuring care delivery remains uninterrupted. This proactive method not only enhances the cybersecurity defenses of healthcare organizations but also improves their ability to manage risks effectively.
How does real-time monitoring help healthcare organizations stay HIPAA compliant?
Real-time monitoring plays a key role in helping healthcare organizations stay compliant with HIPAA regulations. By keeping a constant eye on who accesses sensitive data, tracking security events, and spotting vulnerabilities as they happen, this approach ensures that any unauthorized activity or potential breaches are caught and dealt with quickly. This reduces the chances of patient information being compromised.
Tools like Censinet RiskOps™ make this process much easier. They offer features to evaluate risks, measure cybersecurity performance, and oversee third-party vendors. With these capabilities, healthcare organizations can not only meet regulatory standards but also safeguard both patient data and critical systems effectively.


