Securing PHI with Identity Governance
Post Summary
Protecting Protected Health Information (PHI) is a critical challenge for healthcare organizations. With breaches costing an average of $10.93 million, managing digital identities is essential to safeguard patient data, ensure compliance, and reduce risks. Manual processes can't handle the complexity of modern healthcare systems, which face issues like "orphaned accounts" and "entitlement creep."
Identity Governance and Administration (IGA) offers a centralized solution by automating identity management, access reviews, and user lifecycle processes. This approach minimizes insider threats, prevents privilege misuse, and ensures compliance with regulations like HIPAA. Key components include:
- Identity Lifecycle Management: Automates onboarding, role changes, and account deactivation.
- Access Certification: Regularly reviews user permissions to prevent excessive access.
- Segregation of Duties (SoD): Avoids conflicts of interest by enforcing access policies.
- Audit and Reporting: Tracks and logs all access activities for compliance.
Automating these processes not only protects PHI but also improves efficiency, allowing healthcare staff to focus on patient care. Tools like Censinet RiskOps™ further enhance governance by monitoring risks and streamlining compliance efforts. Strong identity governance is no longer optional - it's a necessity for safeguarding patient trust and reducing financial and operational risks.
Healthcare Data Breach Costs and Identity Governance Impact Statistics
What is IGA (Identity Governance and Administration)?
sbb-itb-535baee
What Is Identity Governance in Healthcare
Identity Governance and Administration (IGA) is a framework designed to manage digital identities and control access to sensitive patient information. It ensures that only authorized individuals can access Protected Health Information (PHI) when needed [3]. While Identity and Access Management (IAM) primarily deals with authentication and authorization, IGA adds extra layers of compliance, oversight, and auditing to better safeguard healthcare data [3][2].
"IGA isn't just an IT function; it's a patient safety imperative." - Deepanjali, Author [3]
IGA goes beyond simply granting access. It provides ongoing oversight throughout an employee's time with a healthcare organization - from their first day to their last. This approach tackles risks caused by staff turnover, role changes, and the complex systems used in modern healthcare. By automating identity management across platforms like Electronic Health Records (EHR), billing systems, and clinical tools, IGA reduces the manual steps that often lead to security vulnerabilities [3][2].
Core Components of Identity Governance
IGA is built on four key components that work together to protect PHI.
- Identity Lifecycle Management: This automates the "joiner, mover, leaver" process, ensuring new hires have the right access from day one and that access is revoked immediately when someone leaves. It helps eliminate orphaned accounts, a common security issue flagged by auditors [3][1].
- Access Certification: Managers and data owners regularly review user access to ensure it aligns with current roles. These reviews help prevent "privilege creep", where users accumulate unnecessary permissions over time [3][2].
- Segregation of Duties (SoD): This enforces policies to prevent conflicts of interest, such as ensuring the same person cannot both bill for a service and approve its payment [3][4].
- Audit and Reporting: Centralized logs track all user activity, offering detailed records of "who, what, when, and why" for data access - critical for HIPAA and HITECH audits [3][2].
| Feature | Identity Administration | Identity Governance |
|---|---|---|
| Focus | Day-to-day execution and lifecycle tasks | Policies, processes, and compliance controls |
| Key Functions | Provisioning, password management, self-service requests | Access reviews, SoD enforcement, audit reporting |
| Goal | Operational efficiency and access delivery | Risk management and regulatory alignment |
Why Identity Governance Is Necessary for PHI Security
Healthcare organizations operate under strict regulations, making IGA a necessity rather than an option. HIPAA requires tight control over who can access patient records, and organizations must demonstrate compliance during audits [3][2]. Without IGA, ensuring proper enforcement of access controls becomes nearly impossible, especially for large systems managing thousands of accounts across multiple facilities.
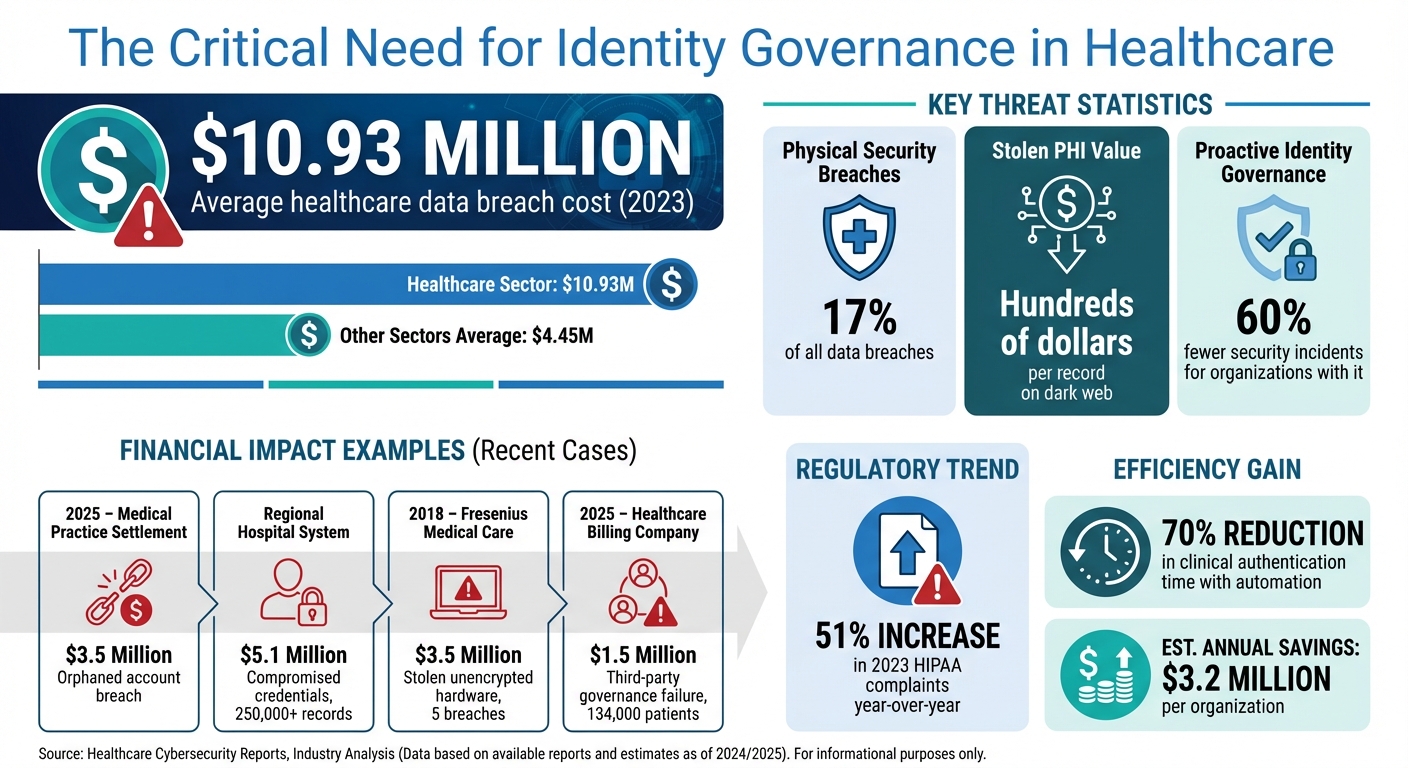
The financial risks are also significant. The average healthcare data breach costs $10.93 million [4], and stolen PHI can sell for hundreds of dollars per record on the dark web [3]. Beyond compliance and financial considerations, IGA improves efficiency by automating repetitive tasks like password resets and access requests. This allows IT teams to focus on more strategic projects while ensuring clinical staff can access the information they need without delays [3][1]. It’s a system that not only protects patient data but also supports smoother operations across healthcare organizations.
Risks of Poor Identity Governance in Healthcare
When healthcare organizations fail to establish strong identity governance, they expose themselves to serious security and financial risks. These weaknesses can cost millions of dollars and jeopardize sensitive patient data daily.
Common Threats to PHI Security
One of the biggest threats to protected health information (PHI) security comes from insider threats. Often, these risks arise from human error or misuse rather than intentional harm, but the consequences remain equally damaging. Automation gaps only make these problems worse.
Another significant issue is orphaned accounts, which leave systems vulnerable to attackers. Without automated processes to manage account lifecycles, these accounts can remain active long after an employee leaves. For example, in 2025, a medical practice faced a $3.5 million settlement when a former employee retained access and downloaded thousands of patient records [5].
Privilege creep is another common problem. This happens when employees accumulate unnecessary access rights as they move between roles or departments. For instance, a nurse who transitions from cardiology to pediatrics might retain access to both areas' systems, exceeding their current job requirements. This violates the principle of least privilege and increases the potential impact of a security breach.
The risk escalates further with compromised credentials, especially in the absence of multi-factor authentication (MFA). In one case, a regional hospital system paid a $5.1 million settlement after compromised credentials led to unauthorized access to over 250,000 patient records. Investigators found that poor access reviews and the lack of MFA allowed the breach to persist [5].
"While the use of shared or generic usernames and passwords may seem to provide some short-term convenience, it severely degrades the integrity of a system because it removes accountability from individual users." - Office for Civil Rights (OCR), HHS [7]
Physical security gaps also play a role in PHI breaches. Lost or stolen equipment accounts for 17% of data breaches, yet only 7% of security leaders view this as a major concern [6]. Between 2020 and 2023, over 50 large breaches reported to the HHS Office for Civil Rights (OCR) involved stolen equipment, affecting more than 1,000,000 individuals [6].
A notable example is Fresenius Medical Care Holdings, Inc. (FMC), which settled for $3.5 million in 2018 after five separate breaches. Three of these incidents involved stolen, unencrypted hardware, compromising PHI for 366 individuals. Investigators found FMC had failed to implement policies to secure facilities and equipment against theft [6].
Regulatory and Financial Consequences
These vulnerabilities don’t just threaten PHI security - they also bring regulatory scrutiny and massive financial penalties. Healthcare breaches average $10.93 million, far surpassing the $4.45 million average in other sectors [5]. These costs include fines, legal settlements, forensic investigations, and long-term reputational harm.
Regulators are paying closer attention than ever. In 2023, the HHS Office for Civil Rights reported a 51% increase in HIPAA complaints compared to the previous year [5]. Common violations include inadequate authentication, failure to revoke access for former employees, and lack of centralized audit trails [5].
Third-party vendor risk management failures add another layer of risk. In one instance, a healthcare billing company faced a $1.5 million settlement in 2025 after a breach affected 134,000 patients. The breach stemmed from weak access controls between the company and its business associates, showing how governance lapses can extend beyond internal systems [5].
Operational inefficiencies compound these challenges. Manual provisioning slows onboarding and delays access revocation, creating both security gaps and productivity losses. Help desk teams are often overwhelmed with password resets and access requests when automated identity management systems are absent. Additionally, the lack of detailed audit trails during inspections can prevent organizations from proving compliance, even when they believe they’re following proper protocols [3].
The evidence is clear: organizations with proactive identity governance programs report 60% fewer security incidents than those that take a reactive approach [5]. These examples highlight the importance of strong identity governance for PHI security. The real question is no longer whether healthcare organizations should invest in identity governance - it’s whether they can afford not to.
How to Secure PHI with Identity Governance
Now that the risks of poor identity governance are clear, healthcare organizations need actionable strategies to safeguard PHI. The following methods address vulnerabilities that could lead to breaches, regulatory issues, or broader enterprise risks.
Role-Based Access Control (RBAC) and Least Privilege
To mitigate risks like unauthorized access and privilege creep, a solid RBAC framework is essential. Role-based access control ensures employees can only access PHI necessary for their specific job duties, offering direct protection for sensitive patient information.
Start by setting up clear, manual security protocols to align roles with the required system permissions. Once this groundwork is in place, automate the process across electronic health records (EHR) and other digital systems [8]. Conduct a thorough inventory of privileged accounts, removing any unnecessary or conflicting permissions as per HHS OCIO guidelines [8].
This approach isn’t limited to human users. Non-person entities like service accounts and machine-to-machine interactions also need to follow least-privilege principles. For example, in containerized environments such as Kubernetes, service roles should be configured with minimal permissions. Similarly, deployment pipelines like GitHub Actions should restrict access to only the resources they need [8].
Automated Access Management
RBAC defines who gets access, but automation ensures these permissions stay up-to-date as roles change. Relying on manual provisioning can create security gaps, inefficiencies, and even orphaned accounts, which automated systems can eliminate [1].
Automated access management oversees the entire employee lifecycle - covering onboarding, promotions, and terminations - ensuring access is revoked or updated immediately when roles change [1]. These systems also monitor for unusual access patterns, inactive accounts, and shared credentials [1]. In fact, implementing automation can cut clinical authentication times by 70%, which translates to an estimated $3.2 million in annual savings for healthcare organizations [9].
Regular automated reviews help keep permissions aligned with job responsibilities, preventing privilege creep as employees transition to new roles. Identity and access management platforms that integrate automated provisioning with single sign-on (SSO) can further lower IT costs while simplifying workflows for clinical staff [1].
Privileged Access Management (PAM)
PAM adds another layer to identity governance by securing critical accounts with elevated permissions. Privileged accounts, which often access sensitive PHI, require stricter controls. Using PAM tools to manage administrative access aligns with Zero Trust principles [8].
Instead of relying on generic IAM policies, tailor governance structures to meet the specific needs of clinical, IT, and HR operations [8]. Identity governance reports can help identify orphaned accounts, unusual access activities, and inconsistent permissions before they become problems [8].
For cloud environments, avoid static, long-lived credentials - like those used in AWS or other cloud platforms. Instead, use scoped service roles to minimize potential damage if a tool is compromised. This reduces the "blast radius" of any security incident and keeps PHI safer [8].
How to Implement Identity Governance in Healthcare Organizations
Setting up identity governance in healthcare requires a detailed plan that considers existing systems, regulatory demands, and operational workflows. Healthcare organizations need to move away from manual methods and adopt automated, policy-driven frameworks to safeguard Protected Health Information (PHI) throughout the employee lifecycle. Below is a step-by-step guide to assess, integrate, and refine identity governance practices.
Evaluating Current Governance Maturity
Begin by cataloging all identities within your organization - this includes employees, contractors, and service accounts - across systems like Electronic Health Records (EHRs), billing platforms, HR software, and cloud applications. This inventory provides a baseline for governance and helps pinpoint areas where PHI might be at risk.
Next, document current permissions, access control lists, and privilege assignments. This process, known as entitlement mapping, often uncovers issues such as "privilege creep" (where users accumulate excessive access rights), orphaned accounts from former staff, and shadow IT practices that bypass official protocols. Align these findings with compliance standards like HIPAA, HITECH, and HITRUST to prepare for audits.
Take a close look at your "joiner, mover, leaver" processes to spot gaps caused by manual provisioning. Evaluate metrics like the time it takes to provision accounts, the percentage of orphaned identities, and policy exceptions. Many healthcare organizations juggling thousands of user accounts across fragmented systems - ranging from older EHRs to modern cloud platforms - find significant vulnerabilities during this stage.
| Maturity Assessment Step | Key Activity | Compliance Goal |
|---|---|---|
| Identity Inventory | Catalog employees, contractors, and service accounts | HIPAA Administrative Safeguards |
| Entitlement Mapping | Document permissions across EHR and billing systems | Technical Safeguards (Access Control) |
| Lifecycle Analysis | Review joiner/mover/leaver workflows | Prevent unauthorized access (PHI protection) |
| Risk Flagging | Identify orphaned accounts and privilege creep | Risk Management (NIST SP 800-66r2) |
| Metric Baselining | Track provisioning speed and policy exceptions | Audit Readiness and Continuous Improvement |
Once these insights are gathered, integrate them into your IT systems to strengthen your governance controls.
Connecting with Healthcare IT Systems
To ensure smooth identity lifecycle management, integrate identity governance with HR systems like Workday or Oracle. These platforms act as a "source of truth", automatically triggering updates when employees join, change roles, or leave the organization.
Directly linking identity governance with EHR platforms like Epic or Cerner simplifies onboarding and role changes for clinicians. Governance policies should also enforce separation of duties to avoid conflicts of interest. For example, no single user should have access to both billing and payment approval functions. Beyond basic roles, consider adopting Attribute-Based Access Control (ABAC), which adjusts access rights based on conditions like location or department.
Framing identity governance as a tool for both compliance and risk reduction can help secure the necessary resources for implementation. Keep in mind that while the HIPAA Security Rule is a key compliance requirement, it’s only one part of a broader data security strategy. Integration efforts must balance these regulatory needs with the organization’s day-to-day operations.
With IT systems integrated, you can leverage advanced tools like Censinet RiskOps™ to enhance your governance strategy.
Using Censinet RiskOps™ for PHI Governance
After automating access management and integrating IT controls, tools like Censinet RiskOps™ can take your identity governance to the next level. This platform combines identity governance with broader cybersecurity measures, streamlining risk assessments for both enterprise and third-party vendors - critical for managing PHI access and clinical system integrations.
Censinet RiskOps™ offers real-time monitoring and collaborative oversight, enabling healthcare organizations to track access patterns, flag anomalies, and address potential threats before they escalate. Automated workflows ease the burden on IT and compliance teams, while a centralized dashboard provides a clear view of organizational risks. By merging identity governance data with other security metrics, the platform helps healthcare leaders make data-driven decisions about resource allocation and risk management.
Its seamless integration with EHRs, medical devices, and other healthcare IT systems ensures consistent enforcement of identity governance policies across the board. This unified approach tackles the fragmentation that often weakens security in healthcare environments, providing a stronger, more cohesive framework for protecting sensitive information.
How to Measure Identity Governance Effectiveness for PHI Security
Once you've implemented identity governance, the next step is to measure how well it protects PHI. Without clear metrics, it’s tough to gauge whether the program is doing its job. The goal here is to move past simple compliance checklists and focus on reducing risks in a measurable way. This phase builds on earlier governance strategies to ensure PHI security is truly effective.
Key Metrics for Governance Success
Access Certification Completion Rates are a great indicator of how consistently an organization reviews user permissions. By tracking the percentage of reviews completed on time, you can see if managers are actively confirming that employees only have the access they need.
Audit Compliance Scores provide a snapshot of how well the organization is performing during internal and external audits. These scores reflect the ability to comply with the HIPAA Security Rule. Reviewing governance controls from an auditor's perspective can help pinpoint weaknesses before official audits take place [10].
Incident Response Times highlight how quickly the organization detects and addresses unauthorized access or security breaches involving PHI. Faster response times suggest that monitoring systems are working well and that teams can act quickly when threats emerge.
Automated tools like Censinet RiskOps™ can make tracking these metrics much easier.
Continuous Improvement and Reporting
Measuring effectiveness doesn’t stop with one review - it’s an ongoing process. Identity governance requires regular updates to keep up with new security threats and changes in regulations. Scheduling consistent assessments helps you track metrics over time, spot trends, and tweak policies to maintain strong controls as healthcare IT systems evolve.
Platforms like Censinet RiskOps™ simplify this process by centralizing all governance data and automating reports. With real-time monitoring and a unified dashboard, healthcare leaders can combine governance metrics with healthcare cybersecurity benchmarks to make smarter resource decisions and ensure governance remains effective [10].
Conclusion
By adopting practices like least privilege, automated provisioning, and role-based access control, healthcare organizations can effectively safeguard patient data and maintain HIPAA compliance. These strategies address major vulnerabilities, such as insider threats, employee turnover, and third-party vendor risks, which can lead to breaches costing an average of $4 million [11].
Strong identity governance also improves clinical workflows by ensuring that authorized staff can quickly access critical PHI while simplifying compliance reporting processes.
Censinet RiskOps™ takes identity governance a step further with its unified risk management approach. This platform helps healthcare organizations streamline risk assessments, benchmark cybersecurity performance, and effectively manage third-party risks across patient data, clinical tools, medical devices, and supply chains. With features like automated vulnerability analysis and real-time monitoring, RiskOps™ replaces outdated manual processes with adaptive, dynamic oversight that evolves alongside emerging threats. These tools work together to strengthen protection efforts.
Effective identity governance, paired with comprehensive risk management, provides a continuous safeguard for PHI. By combining secure access controls with advanced risk management platforms, healthcare organizations can build stronger defenses to protect patient trust, meet regulatory requirements, and deliver safe, efficient care.
FAQs
How is IGA different from IAM in healthcare?
When it comes to safeguarding protected health information (PHI), Identity Governance and Administration (IGA) and Identity and Access Management (IAM) play crucial but distinct roles.
IAM is all about the technical side of access control. It includes tools like multi-factor authentication (MFA) and role-based access control (RBAC) to ensure that only authorized individuals can access sensitive data. Think of it as the security guard at the door, verifying who gets in and what they can do.
On the other hand, IGA takes a broader approach by managing the entire lifecycle of digital identities. It ensures that access permissions are in sync with an individual’s role and responsibilities, preventing issues like privilege creep (when users accumulate unnecessary access over time). IGA also helps organizations stay aligned with compliance requirements, such as those outlined in HIPAA, reducing the risk of non-compliance and improving overall security practices.
Together, these systems create a strong foundation for protecting PHI while meeting regulatory demands.
What’s the fastest way to eliminate orphaned accounts?
The quickest way to address orphaned accounts is by using identity governance solutions equipped with automated access reviews and offboarding processes. These tools make it easier to spot and deactivate inactive or unowned accounts, helping to strengthen security and maintain compliance when handling protected health information (PHI).
Which metrics prove PHI access governance is working?
When assessing PHI (Protected Health Information) access governance, several critical metrics come into play. These include monitoring and auditing access logs to identify any unauthorized activity, keeping track of compliance audit scores, and conducting regular access reviews to ensure proper oversight.
Other valuable indicators to watch are the number of failed access attempts, which can signal potential security concerns, and role-based permission reviews, ensuring that access rights align with job responsibilities. Additionally, metrics such as incident response time and mean time to risk resolution provide insight into how efficiently access-related risks are identified and resolved. These measurements collectively offer a clear picture of how well PHI access is governed and safeguarded.


