Security Awareness Training: Healthcare vs. Other Industries
Post Summary
Because cyberattacks directly affect patient safety, clinical workflows, and access to PHI—not just finances.
High workload, outdated systems, shared devices, and third‑party exposure increase vulnerability.
HIPAA and HITECH mandate role‑specific, recurring training tied to PHI handling and ePHI safeguards.
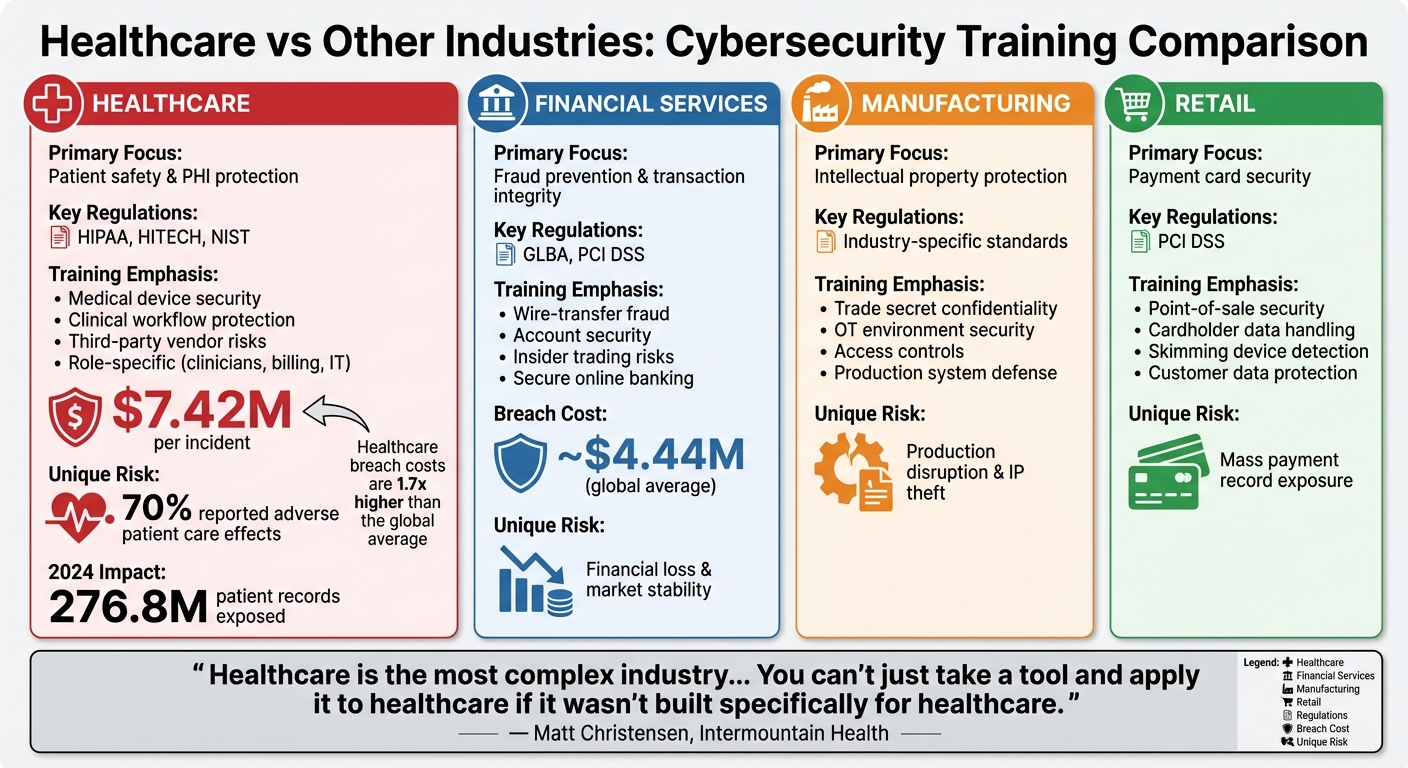
Healthcare focuses on PHI, clinical workflows, medical devices, and vendor risks; other sectors focus on fraud, PCI DSS, or IP protection.
Microlearning, scenario-based modules, hands‑on drills, simulated phishing, and training embedded into clinical workflows.
Using metrics tied to PHI incidents, phishing click rates, unauthorized access, privacy violations, vendor risks, and benchmarking.
Human error causes most cyberattacks - up to 74% across industries. Security awareness training helps reduce these risks by teaching employees to spot and respond to threats like phishing and ransomware. For example, phishing click rates can drop from 33.1% to 4.1% with consistent training.
Healthcare faces unique challenges compared to industries like finance, retail, and manufacturing. Why? Patient safety is directly tied to cybersecurity. A ransomware attack can delay treatments or even threaten lives. In 2024, healthcare breaches exposed 276.8 million patient records, costing an average of $7.42 million per breach - nearly double the global average.
Key differences in healthcare training:
Other industries prioritize financial loss prevention (finance), intellectual property (manufacturing), or payment card security (retail). However, healthcare must address a wider range of risks, including third-party vendors and outdated medical devices.
Takeaway: Healthcare leaders should prioritize continuous, role-specific training that links cybersecurity to patient outcomes. Tracking metrics like phishing simulation click rates and PHI incidents can improve programs and reduce risks.
Healthcare vs Other Industries: Cybersecurity Training Priorities and Breach Costs
Healthcare's Cybersecurity Risks and Regulatory Requirements
Risk Factors Specific to Healthcare
Healthcare organizations face unique challenges when it comes to cybersecurity. They manage vast amounts of protected health information (PHI) and personally identifiable information (PII), making them prime targets for cyberattacks. In 2024 alone, 389 U.S. healthcare institutions experienced shutdowns or delays in medical procedures due to ransomware [1]. The high value of this sensitive data creates a fertile ground for cybercriminals.
Adding to the problem, many hospitals still rely on outdated clinical systems and connected medical devices like MRI machines, infusion pumps, and pacemakers. These devices often run obsolete software, lack regular security updates, and have weak authentication protocols. For attackers, they act as entry points to infiltrate broader networks. Unlike other industries where downtime primarily hits revenue, disruptions in healthcare can delay surgeries, interrupt diagnostics, or even force ambulance diversions - directly threatening patient lives. In fact, 70% of healthcare organizations impacted by cyberattacks in 2024 reported adverse effects on patient care [1].
Ransomware remains the most pressing threat, exploiting healthcare's reliance on continuous access to systems like electronic health records (EHRs) and lab results. Attackers know that delays in care can have life-or-death consequences, which increases the pressure on organizations to pay ransoms.
Human error is another major factor. Over 90% of cyberattacks in healthcare involved phishing schemes, and 88% of employees opened phishing emails in 2024 [1]. These attacks often mimic urgent messages, such as lab results or vendor alerts, tricking staff into clicking malicious links or revealing credentials. The problem is amplified by the sector's reliance on third-party providers. In 2023, 58% of the 77.3 million individuals affected by healthcare data breaches were impacted through third-party attacks - a staggering 287% increase from the previous year [1]. Additionally, staffing shortages exacerbate the issue, with 53% of organizations lacking in-house cybersecurity expertise [1]. This highlights the need for comprehensive training that not only addresses internal risks but also covers interactions with contractors, vendors, and cloud services.
Regulatory Requirements for Healthcare Training
Strict federal regulations shape the way U.S. healthcare organizations approach cybersecurity training. The HIPAA Privacy Rule requires training on how to handle and safeguard PHI, while the HIPAA Security Rule mandates a formal security awareness program for anyone working with electronic PHI (ePHI). These programs must cover technological safeguards, threat detection, and incident response, with training provided shortly after hiring or role changes and updated regularly to reflect evolving threats.
The HITECH Act builds on these requirements by enforcing stricter breach notification rules and increasing penalties for noncompliance. This has driven organizations to document and formalize training cycles to demonstrate compliance during audits. Many healthcare organizations also follow NIST guidelines, such as the NIST Cybersecurity Framework and publications like SP 800‑53 and SP 800‑66, which recommend role-specific training based on functions like Identify, Protect, Detect, Respond, and Recover.
Training in healthcare is often tiered. General onboarding covers basics like privacy, password security, and incident reporting. More specialized modules are tailored for clinicians, billing teams, and IT staff, while security personnel receive advanced training. Most organizations track completion through learning management systems, linking it to employment or credentialing requirements. However, gaps remain: 34% of healthcare employees are unaware of their organization's cybersecurity policy, and one in four workers who feel they need training never receive it [4]. These gaps underline the importance of well-designed and accessible training programs.
How Other Industries' Risk Profiles Compare
While healthcare faces unique challenges, other industries have their own cybersecurity priorities. For example, financial services focus on fraud prevention, account security, and transaction integrity, guided by regulations like the Gramm-Leach-Bliley Act (GLBA) and PCI DSS. Their training emphasizes spotting wire-transfer fraud, insider trading risks, and secure online banking practices. The primary concern here is financial loss and protecting market stability, rather than patient safety.
In manufacturing, the emphasis is on protecting intellectual property and securing operational technology (OT) environments. Training often covers trade-secret confidentiality, access controls, and defending industrial systems from attacks that could disrupt production. While downtime in manufacturing is costly, it doesn't carry the immediate life-or-death stakes seen in healthcare.
Retail prioritizes payment card security and PCI DSS compliance, focusing on secure point-of-sale practices, handling cardholder data, and detecting skimming devices. Breaches in this sector can expose millions of payment records and result in hefty fines, but they don’t delay critical medical treatments or emergency responses. Healthcare organizations, however, must address PCI compliance alongside HIPAA requirements, EHR workflows, and the handling of PHI - balancing a wider range of concerns tied directly to patient outcomes.
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare."
This complexity extends to training programs. Healthcare organizations must incorporate scenarios that resonate with their staff, such as how phishing attacks could delay life-saving treatments or how to secure bedside computers and mobile health apps. Training also needs to address medical device security, teaching employees to recognize suspicious device behavior and avoid unauthorized connections, as well as vendor risk management, such as verifying third-party requests for PHI. Unlike other industries, where training can focus on narrower issues, healthcare must tackle a broad spectrum of interconnected challenges - spanning data privacy, operational continuity, compliance, and, most importantly, patient safety.
How Training Design and Delivery Differ
Scope and Learning Goals
In healthcare, training revolves around protecting patient health information (PHI) and ensuring patient safety. A breach in PHI security can delay treatments or compromise care quality, making these priorities critical. Staff are trained to secure electronic PHI (ePHI) in line with HIPAA regulations, avoid discussing sensitive cases in public spaces, and recognize how lapses in security can disrupt urgent care. Learning goals are tailored to specific roles within the organization. For example:
In other industries, training objectives are more geared toward preventing financial losses, reducing fraud, and safeguarding intellectual property. For instance, financial services emphasize identifying wire-transfer fraud, preventing insider trading, and complying with regulations like PCI DSS. Meanwhile, technology and manufacturing sectors focus on protecting trade secrets and securing development environments. While role-based training is common across industries, healthcare's emphasis on patient safety sets it apart. This unique focus shapes the real-world scenarios integrated into healthcare training, which will be discussed further.
Training Content and Risk Scenarios
The content and scenarios used in healthcare training are specifically designed to address its unique challenges. Curricula cover HIPAA privacy and security rules, practical PHI handling procedures, and organization-specific policies required by federal regulations. Scenarios are embedded into clinical workflows to make training relevant and actionable. Examples include:
Other scenarios tackle medical device security risks, patient privacy in shared spaces, secure clinical messaging on mobile devices, and safe telehealth practices.
In comparison, financial services focus on scenarios like payment fraud detection and PCI DSS compliance, while technology and manufacturing concentrate on intellectual property protection and data loss prevention. Although phishing, password security, and social engineering are common topics across industries, healthcare ties these threats directly to patient outcomes. For example, a phishing attack might delay life-saving treatments, or a ransomware incident could disrupt emergency care. Additionally, healthcare training often includes third-party risk scenarios, such as breaches involving billing vendors or cloud imaging providers, which are less prominent in other sectors.
Frequency and Delivery Methods
Healthcare training methods are designed to accommodate the demanding schedules of clinical staff. Cybersecurity and HIPAA training are integrated into onboarding processes, with annual updates and periodic refreshers when new threats emerge. New hires typically complete foundational training within 30 days to meet regulatory standards. Given the irregular hours many staff work - nights, weekends, and rotating shifts - training is broken into short, 5–15 minute modules that can be completed between patient care tasks. For clinicians with limited screen time, concise e-learning modules and just-in-time prompts, such as alerts when accessing sensitive records, are particularly effective. In-person sessions are also used to cover complex topics like device security or phishing for those with less IT experience.
In contrast, other industries often rely on standard web-based courses during business hours, supplemented by occasional virtual town halls or longer annual e-learning sessions lasting 30–60 minutes. While microlearning and frequent touchpoints are gaining traction outside healthcare, the constant staffing demands and time pressures in hospitals make short, flexible modules a necessity. Time-sensitive communication channels, like secure messaging to alert staff about active phishing campaigns, are vital in healthcare's 24/7 environment. However, there is room for improvement: only 41% of healthcare organizations run simulated phishing attacks, and just 37% conduct annual cybersecurity incident response exercises [1]. This suggests that many programs remain basic or compliance-focused rather than aimed at changing behaviors.
sbb-itb-535baee
Measuring Training Effectiveness and Benchmarking Results
Metrics for Evaluating Training Impact
Healthcare organizations rely on a mix of key metrics commonly used across industries, but with added clinical relevance. These metrics include phishing simulation click rates, training completion percentages, time-to-report suspicious emails, and security incidents caused by human error. What sets healthcare apart are additional indicators like PHI (Protected Health Information) incidents per 1,000 employees, unauthorized access to medical records, improper disclosures in public areas (e.g., hallways or elevators), and violations of HIPAA safeguards such as mobile device policies or privacy screen usage. These metrics link training outcomes directly to patient safety and compliance with regulations, not just financial implications.
For instance, benchmarking data shows that ongoing training can reduce phishing click rates from 33.1% to 4.1% within 12 months [2]. This is particularly critical in healthcare, where 92% of organizations faced attacks last year, and 67% reported declines in patient care quality due to phishing or business email compromise. Lower click rates in phishing simulations lead to fewer treatment delays and safer clinical operations. Breaking these metrics down by role also helps identify specific groups that need additional coaching, especially where PHI exposure risks remain high.
Benchmarking and Sector-Specific Data
Metrics become even more meaningful when organizations benchmark their performance against peers. Resources like HHS breach trend reports and data from security awareness vendors provide valuable insights, such as phishing click rates segmented by industry and organization size. In 2024, PHI exposure averaged 758,288 records per day [1][3], and healthcare breach costs reached an average of $7.42 million per incident - about 1.7 times higher than the cross-industry average of $4.44 million [1][2]. These figures help justify investments in training and security programs.
However, benchmarking in healthcare comes with unique challenges. The sector’s diversity - ranging from acute hospitals to outpatient clinics, long-term care facilities, and home health providers - means workflows and risk profiles vary widely. Additionally, the heavy reliance on third-party vendors and medical device suppliers adds layers of complexity, as does the uneven security maturity among organizations of similar size. To address this, healthcare-specific benchmarking initiatives adjust data based on factors like care setting, workforce size, and role, allowing for more relevant comparisons than generic cross-industry reports.
How Specialized Risk Management Platforms Help
Benchmarking results often reveal areas where specialized platforms can enhance outcomes. In healthcare, tools like Censinet RiskOps™ simplify risk data management and align training metrics with broader risk management efforts. These platforms integrate data across third-party vendors, enterprise systems, and clinical workflows, standardizing assessment criteria for over 50,000 vendors. This enables organizations to benchmark training-related risks, such as incidents tied to vendor access or performance on security questionnaires.
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."
Conclusion: Key Takeaways for Healthcare Organizations
Healthcare's Distinct Training Challenges
Healthcare security training comes with its own set of hurdles, shaped by the unique demands of the industry. Clinical staff often work around the clock, leaving little room for traditional training sessions. Add to that the diverse workforce - spanning physicians, nurses, billing clerks, biomedical engineers, volunteers, and contractors - all of whom interact with Protected Health Information (PHI) through a mix of legacy EHR systems, medical devices, and third-party applications. Unlike breaches in industries like retail or finance, where the primary concern is financial loss, security failures in healthcare can disrupt treatments and jeopardize patient safety. For instance, phishing attacks can delay critical care, underscoring the direct link between cybersecurity and patient outcomes.
Then there’s the regulatory landscape. Healthcare organizations must navigate the HIPAA Privacy and Security Rules, CMS requirements, and various state privacy laws, all of which demand regular, role-specific training. Generic corporate training programs often fall short in addressing these specialized needs.
Recommendations for Healthcare Leaders
To effectively address these challenges, healthcare leaders need to go beyond mere compliance. Instead, they should aim to create continuous learning programs grounded in real-world risks. Start by mapping roles to PHI access and associated risks. For example, bedside nurses should focus on secure workstation practices and medical device handling, while billing staff might need training on email security and disclosure protocols.
Replace outdated, one-size-fits-all approaches - like annual slide-deck sessions - with more dynamic methods. These could include concise onboarding modules, quarterly micro-learning sessions tailored to specific roles, and annual incident-response drills that bring together both clinical and administrative teams.
Track meaningful metrics to measure progress. This includes monitoring phishing simulation click rates, time-to-report suspicious activity, and PHI-related incidents per 1,000 employees. Use this data to continuously refine training content. Organizations that adopt this approach have seen phishing susceptibility drop from 33.1% to 4.1% in just 12 months - a significant improvement, especially when considering the $7.42 million average cost of a healthcare breach.
Finally, integrate training into your broader risk management strategy. Tie workforce behavior metrics to your enterprise risk register and ensure collaboration across compliance, privacy, and clinical leadership teams. This way, security awareness becomes part of onboarding, annual competencies, and overall performance expectations.
Why Industry-Specific Training Matters
Healthcare's operational realities - like emergency workflows, shared workstations, mobile carts, and network-connected medical devices - make generic training programs insufficient. Effective training must reflect the real-world scenarios healthcare professionals face daily. For instance, HIPAA mandates role-specific training on policies and procedures, and regulators expect updates whenever new threats or organizational changes arise.
Given the rising rates of cybersecurity threats and PHI exposure, the case for tailored training is clear. Programs like Censinet RiskOps™ integrate training data with enterprise risk assessments, ensuring that security awareness aligns with the unique challenges of the healthcare sector. Continuous, role-specific training isn’t just a regulatory requirement - it’s a critical component of protecting both patient data and care quality. By prioritizing industry-specific strategies, healthcare organizations can better safeguard their operations and, most importantly, their patients.
FAQs
Why is cybersecurity training especially important in healthcare?
Cybersecurity training holds a crucial place in healthcare, given the sensitive nature of patient information and the heavy reliance on technology in clinical settings. The industry faces unique challenges, such as vulnerabilities in medical devices, clinical software, and supply chain systems. Addressing these risks requires specialized training to ensure they are managed effectively.
Healthcare is also a prime target for cyberattacks, largely due to the high value of protected health information (PHI) and the potential consequences for patient safety. Customized training programs equip staff to identify and respond to these threats, safeguarding both sensitive data and the continuity of patient care.
What makes healthcare organizations more vulnerable to cybersecurity threats?
Healthcare organizations grapple with unique cybersecurity challenges because they manage highly sensitive patient data and protected health information (PHI). These challenges include weaknesses in medical devices, risks from supply chain attacks, and the complexities involved in overseeing third-party vendors. On top of that, strict regulations and the necessity of maintaining uninterrupted patient care add extra layers of difficulty.
With the healthcare sector heavily dependent on interconnected systems and devices, the potential for breaches is heightened. This makes implementing strong cybersecurity measures critical - not just for safeguarding patient information, but also for ensuring the smooth operation of healthcare services.
Why is role-specific cybersecurity training important in healthcare?
Role-specific cybersecurity training is essential in healthcare because it aligns learning with the specific duties of each team member. This personalized approach ensures the training feels relevant, helping employees recognize and respond to the threats they are most likely to encounter in their roles.
By focusing on risks associated with patient data, medical devices, and clinical systems, this type of training minimizes human error and bolsters the organization’s security framework. It equips staff to manage challenges effectively, safeguarding sensitive information while ensuring compliance with industry regulations.
Related Blog Posts
- How to Build Cybersecurity Awareness for Clinicians
- 5 Steps to Train Incident Response Teams in Healthcare
- Onboarding vs. Offboarding: Vendor Training Needs
- HITECH Compliance Training: Key Requirements
{"@context":"https://schema.org","@type":"FAQPage","mainEntity":[{"@type":"Question","name":"Why is cybersecurity training especially important in healthcare?","acceptedAnswer":{"@type":"Answer","text":"<p>Cybersecurity training holds a crucial place in healthcare, given the sensitive nature of patient information and the heavy reliance on technology in clinical settings. The industry faces unique challenges, such as vulnerabilities in medical devices, clinical software, and supply chain systems. Addressing these risks requires specialized training to ensure they are managed effectively.</p> <p>Healthcare is also a prime target for cyberattacks, largely due to the high value of protected health information (PHI) and the potential consequences for patient safety. Customized training programs equip staff to identify and respond to these threats, safeguarding both sensitive data and the continuity of patient care.</p>"}},{"@type":"Question","name":"What makes healthcare organizations more vulnerable to cybersecurity threats?","acceptedAnswer":{"@type":"Answer","text":"<p>Healthcare organizations grapple with unique <a href=\"https://www.censinet.com/resource/challenges-remain-for-healthcare-cybersecurity\">cybersecurity challenges</a> because they manage highly sensitive patient data and <strong>protected health information (PHI)</strong>. These challenges include weaknesses in medical devices, risks from <a href=\"https://censinet.com/third-party-risk/supply-chain\">supply chain attacks</a>, and the complexities involved in overseeing third-party vendors. On top of that, strict regulations and the necessity of maintaining uninterrupted patient care add extra layers of difficulty.</p> <p>With the healthcare sector heavily dependent on interconnected systems and devices, the potential for breaches is heightened. This makes implementing strong cybersecurity measures critical - not just for safeguarding patient information, but also for ensuring the smooth operation of healthcare services.</p>"}},{"@type":"Question","name":"Why is role-specific cybersecurity training important in healthcare?","acceptedAnswer":{"@type":"Answer","text":"<p>Role-specific cybersecurity training is essential in healthcare because it aligns learning with the specific duties of each team member. This personalized approach ensures the training feels relevant, helping employees recognize and respond to the threats they are most likely to encounter in their roles.</p> <p>By focusing on risks associated with patient data, medical devices, and clinical systems, this type of training minimizes human error and bolsters the organization’s security framework. It equips staff to manage challenges effectively, safeguarding sensitive information while ensuring compliance with industry regulations.</p>"}}]}
Key Points:
Why is cybersecurity training uniquely critical for healthcare organizations?
- Patient safety is directly impacted, not just financial systems
- Clinical workflows depend on uninterrupted access to EHRs, labs, and imaging
- PHI is highly valuable to attackers, making healthcare a prime target
- Outdated medical devices and legacy systems increase vulnerabilities
- Third‑party dependencies amplify risk, especially across cloud and vendor systems
What human-factor risks make healthcare staff more vulnerable to cyberattacks?
- High fatigue and workload pressure, leading to skipped procedures
- Shared workstations and login shortcuts, reducing accountability
- High phishing exposure, with urgent clinical messages mimicked by attackers
- Inconsistent training across roles, from clinicians to billing staff
- Limited cybersecurity staffing, raising reliance on non‑technical users
How do regulatory requirements shape healthcare security training?
- HIPAA Privacy and Security Rules require formal training for anyone handling PHI or ePHI
- HITECH adds breach notification obligations, increasing the need for documented training
- NIST CSF and SP 800‑53 guide role‑based awareness programs
- Training must update regularly, not just annually, to reflect evolving threats
- Organizations must prove training occurred during OCR investigations or audits
How does healthcare training differ from other industries’ cybersecurity priorities?
- Healthcare emphasizes PHI protection and clinical safety, unlike finance’s fraud focus
- Medical device security and IoMT risks are unique to healthcare
- Retail focuses mainly on PCI DSS, while healthcare manages PHI + PCI + device + vendor risks
- Manufacturing prioritizes intellectual property and OT, whereas healthcare prioritizes care continuity
- Healthcare has higher operational stakes, where downtime can delay treatments
What learning formats work best for healthcare’s 24/7 environment?
- Short microlearning units, completable between patient tasks
- Simulated phishing exercises tailored to clinical scenarios
- Scenario‑based modules tied to EHR use, device security, and shared workstation risks
- Mobile‑friendly training, supporting varied shifts and locations
- In‑person refreshers for device security and regulatory updates
What metrics matter most when evaluating healthcare training effectiveness?
- Phishing click rates and time‑to‑report suspicious emails
- Unauthorized access attempts and privacy violations
- PHI incidents per 1,000 employees, unique to healthcare
- Completion rates segmented by clinical role
- Benchmarking PHI exposure costs and incident trends
- Training impact on reducing care delays caused by breaches


