SOC 2 Privacy Checklist for Healthcare Vendors
Post Summary
Protecting patient data isn't just a legal requirement - it’s a business necessity for healthcare vendors. SOC 2 Privacy compliance offers a structured way to safeguard Protected Health Information (PHI) while meeting both HIPAA and global privacy standards like GDPR.
Here’s what you need to know:
- SOC 2 Privacy focuses on how personal data is collected, stored, shared, and deleted.
- It complements HIPAA by providing measurable, auditable privacy controls.
- A clear privacy framework reduces vendor risks and builds trust with healthcare organizations.
This guide walks you through defining your scope, managing data flows, setting privacy policies, handling third-party risks, and preparing for audits. By following these steps, you can align with SOC 2 standards and ensure comprehensive patient data protection. Let’s dive into the details.
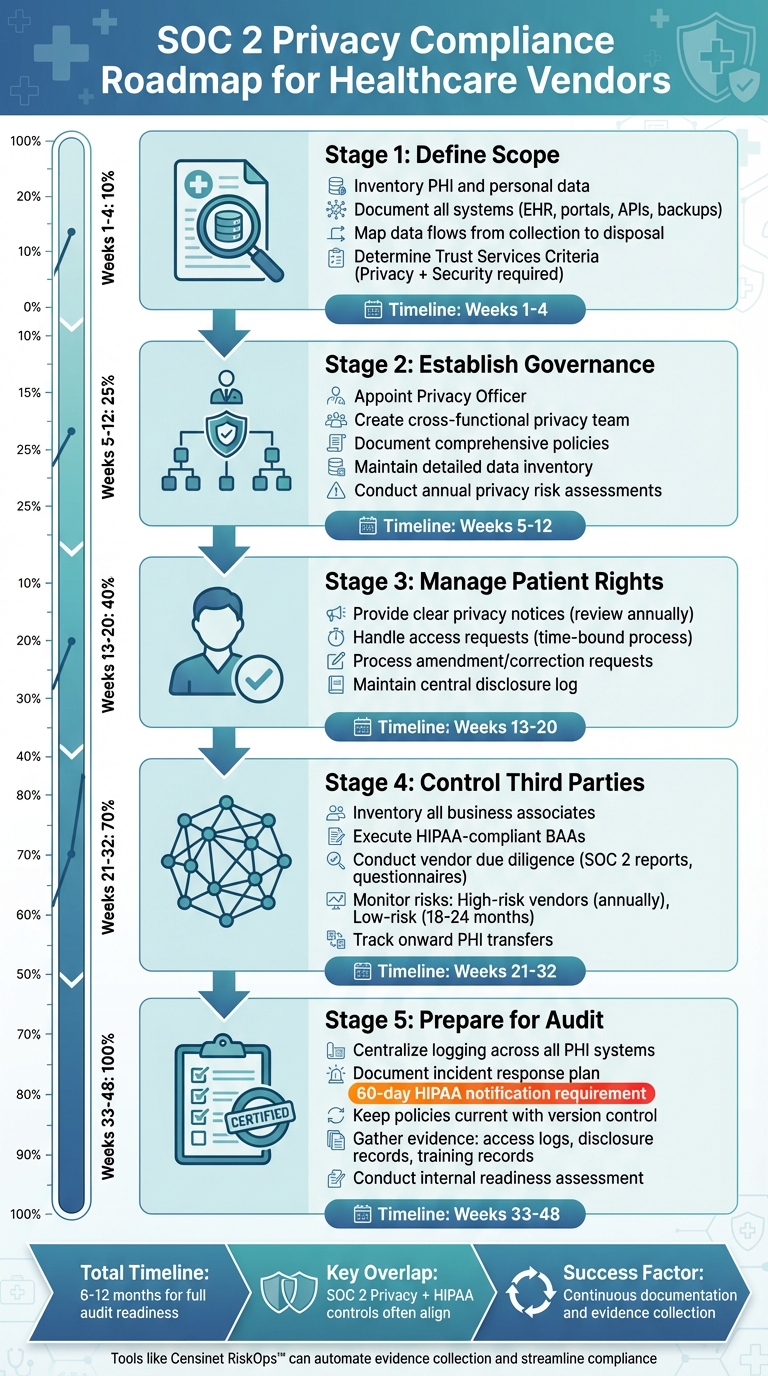
SOC 2 Privacy Compliance Roadmap for Healthcare Vendors
Defining Scope for SOC 2 Privacy Compliance
Identifying In-Scope Data and Systems
Before tackling privacy controls, it’s crucial to define which data and systems fall under your SOC 2 Privacy scope. Start by creating a detailed inventory of all PHI (Protected Health Information) and personal data. This includes patient demographics, clinical records, billing information, device-generated data, and unique identifiers. Be thorough - document every system processing this data, such as EHR integrations, patient portals, APIs, analytics platforms, backup systems, support ticketing tools, and even non-production environments like staging servers or development databases.
Matt Christensen, Sr. Director GRC at Intermountain Health, highlights the challenge: "Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." [1]
This complexity means you need to look beyond the obvious clinical systems. Include research data, medical devices, and supply chain systems that handle patient information in your scope. Once you’ve built a comprehensive inventory, the next step is to trace how data flows through its lifecycle.
Mapping Data Flows and Lifecycle Management
With your in-scope data identified, map out its entire journey - from collection to disposal - capturing every detail along the way [2].
Start by documenting collection points. This could include HL7 or FHIR feeds from EHRs, submissions through patient portals, device-generated data streams, and API integrations. For each intake mechanism, specify what data elements are being collected, who is responsible for collecting them, and the legal basis for doing so (e.g., a Business Associate Agreement or patient consent).
Next, track how the data is used and shared. Does it support patient care, operational analytics, research, quality improvement, or customer support? Make sure these uses align with your privacy notices and any contractual obligations. Also, record all storage locations - primary databases, backup systems, log repositories, and business intelligence tools - to ensure you have a complete picture of your data handling practices.
Finally, focus on data disposal. Define retention periods and outline how data is securely deleted, de-identified, or archived across production systems, backups, and third-party environments. Include verification steps to confirm that data is no longer accessible. This comprehensive mapping lays the groundwork for selecting the applicable Trust Services Criteria.
Determining Trust Services Criteria in Scope
While Security is a standard requirement for every SOC 2 audit, you’ll need to decide if additional Trust Services Criteria should be included alongside Privacy. For many healthcare vendors, adding Confidentiality is a logical choice since it focuses on protecting sensitive data, especially information classified as confidential by agreements.
You might also consider including Availability if your service has uptime commitments or if downtime could directly impact patient care. Processing Integrity could be relevant if your platform transforms clinical data, billing records, or quality metrics - particularly if these processes influence diagnoses, claims decisions, or reporting accuracy.
To align your SOC 2 scope with HIPAA requirements, include systems that manage patient rights, privacy notices, and access controls. At the same time, explicitly exclude systems that aren’t relevant, such as internal IT tools, marketing platforms, or sandbox environments. By narrowing your focus to only the systems that matter, you can streamline compliance efforts while maintaining a robust privacy framework.
Governance and Privacy Management Framework
Establishing Privacy Roles and Responsibilities
Appoint a dedicated Privacy Officer to oversee compliance with SOC 2 Privacy and HIPAA standards. This individual should have clearly outlined responsibilities, including managing privacy policies, conducting risk assessments, coordinating incident responses, and handling audits. To support their efforts, assemble a cross-functional privacy team to address various aspects of privacy management.
Create an oversight committee that convenes quarterly to evaluate privacy risks, review incidents, address third-party concerns, and update policies. Clearly document the committee's purpose, membership, and decision-making authority. Integrate privacy-related duties into job descriptions, performance reviews, and training programs. By defining these roles and responsibilities, you lay a strong foundation for effective policy management and risk oversight.
Documenting Policies and Data Inventories
Develop comprehensive written policies that govern the handling of PHI, covering every stage from collection to secure disposal, including cross-border data transfers. These policies should align with SOC 2 Privacy criteria and HIPAA requirements to ensure consistency across your privacy program.
Maintain a detailed data inventory that identifies, categorizes, and tracks all PHI and personal information within your organization. Link each data element to the systems and vendors that manage it. Centralize key governance documents - such as privacy notices, Business Associate Agreements, consent forms, and disclosure logs - in an easily accessible repository. These policies and inventories serve as critical tools for conducting focused privacy risk assessments.
Conducting Privacy Risk Assessments
Perform privacy risk assessments at least once a year or after significant changes to your systems or processes. These assessments should identify potential threats to PHI, evaluate their likelihood and impact, and document mitigation plans. Each plan should include specific remediation steps, assign responsibility to team members, and set deadlines for completion. Map the results of these assessments to Trust Services Criteria and HIPAA controls for comprehensive oversight.
Tools like Censinet RiskOps™ can streamline this process by standardizing risk assessments across vendors and internal systems. They also help track remediation efforts, collect audit evidence, and support continuous improvement, making SOC 2 audit preparation more efficient and effective.
Managing Patient Rights and Privacy Commitments
Providing Clear Privacy Notices
Your privacy notice should clearly outline what Protected Health Information (PHI) you collect, why you collect it, how it’s used, and who it’s shared with. This transparency helps build trust with patients. It’s also important to include details about patient rights - such as access to their data, requesting amendments, imposing restrictions, obtaining an accounting of disclosures, and filing complaints. Provide clear contact options for these inquiries, like an email address, phone number, mailing address, or a portal link.
Review your privacy notice regularly - at least once a year or whenever there’s a change in your data practices. Implement strict version control by dating revisions, tracking changes, and archiving older versions. This helps avoid audit issues, as discrepancies between what your notice promises and what you actually do are common triggers for enforcement actions. To prevent this, ensure your operational teams, legal counsel, and compliance officers work together to align the notice with your workflows, contractual obligations, and compliance standards like SOC 2 Privacy and HIPAA.
Each commitment in your privacy notice should correspond to a specific type of consent, such as HIPAA authorizations for marketing or treatment-related disclosures. Use standardized forms to collect and store consent records, ensuring they are validated against patient identity. Regularly reconcile disclosures with documented consents and retain these records for SOC 2 audits.
Once your notices are clear, establish strong mechanisms to enforce patient data rights effectively.
Supporting Patient Data Subject Rights
Empowering patients with well-defined rights is a cornerstone of SOC 2 Privacy compliance.
Start by creating a documented, time-bound process for handling patient access requests. Clearly define how requests can be submitted - whether through a portal, email, mail, or phone. Include steps for verifying identity, routing requests, setting approval criteria, meeting response deadlines, and delivering data securely (e.g., via an encrypted email or a secure portal). Your process should also address when access may be denied under HIPAA, how denials are reviewed, and how reasons are communicated to patients. Auditors will look for policy documents, examples of request logs (with dates, identity verification details, outcomes, and timelines), response templates, and evidence of workforce training on handling these requests.
Similarly, document a clear procedure for managing amendment and correction requests. Outline how patients can submit these requests, the necessary documentation, criteria for review, timelines for responses, and valid reasons for denial. Verify the identity of the requester and confirm their ownership of the data. Keep records of all reviews and decisions. If a correction is approved, ensure the updates are reflected across all systems and notify any affected third parties. Maintain a central disclosure log that tracks recipients, disclosure details, the authority behind the disclosure (e.g., patient consent or a Business Associate Agreement), and the purpose. This log is critical for supporting disclosure accounting during audits or assessments.
Third-Party Management and Onward Transfers
Managing Business Associates and Subprocessors
Effective third-party management strengthens your privacy controls and ensures compliance with SOC 2 criteria over time.
Healthcare vendors that handle PHI (Protected Health Information) must keep a detailed record of all third-party relationships. This inventory should include each third party's name, the type of data they access, the purpose of the relationship, and the legal basis for sharing data. Common examples include cloud hosting providers, payment processors, and analytics vendors.
Before sharing PHI, establish a HIPAA-compliant Business Associate Agreement (BAA) with each third party. The BAA should clearly outline permitted uses and disclosures of PHI, require the business associate to implement proper safeguards, mandate timely notification of any breaches, give you the right to audit their controls, and specify how PHI will be returned or destroyed when the relationship ends. SOC 2 Privacy criteria also require obtaining privacy commitments from third parties with PHI access and regularly evaluating their compliance. If issues arise, you’ll need to take corrective action to address them.[2]
When onboarding a new business associate or subprocessor, standardized due diligence is key. Request their SOC 2 Type II report (including Privacy criteria), completed security questionnaires, evidence of HIPAA compliance, proof of cyber liability insurance, and details of their incident response procedures. Document your risk assessment findings, including any gaps and planned mitigation steps, to create a clear audit trail that supports SOC 2 Privacy compliance.
Keep track of onward transfers of PHI throughout its lifecycle by maintaining a disclosure log. This log should include details about which vendors receive PHI, the legal authority for sharing it (such as a BAA or patient authorization), the purpose of the transfer, and the date it occurred. Both HIPAA and the AICPA Privacy Management Framework, which underpins SOC 2 Privacy, require such detailed accounting of disclosures.[2]
Once third-party relationships are in place, ongoing monitoring becomes essential for maintaining compliance.
Monitoring and Auditing Third-Party Risks
Managing third-party risks doesn’t stop after onboarding. Set regular review schedules based on the risk level of each vendor. For example, high-risk vendors handling large amounts of PHI might require annual reassessments, while lower-risk vendors could be reviewed every 18–24 months. Continuously monitor for changes in a vendor’s security posture, such as breach disclosures, expired certifications, or updates to their subprocessor arrangements.
During each review, request updated SOC 2 reports, completed security questionnaires, and attestations of ongoing HIPAA compliance. If a security incident or contractual breach occurs, document the issue, your response, and any corrective actions taken. Include your business associates in your incident response plan by requiring them to notify you immediately of any suspected or actual unauthorized PHI disclosures.[2]
Leverage platforms to streamline vendor documentation, automate assessments, and monitor your third-party ecosystem. For instance, Censinet’s collaborative risk network, which includes over 50,000 vendors and products in the healthcare industry, allows vendors to share completed security questionnaires and supporting evidence early in the sales process.[1]
Terry Grogan, CISO at Tower Health, shared: "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."[1]
Prepare audit evidence for SOC 2 examiners by organizing a complete vendor inventory, executed BAAs, initial and periodic risk assessments, vendor SOC 2 reports, disclosure logs, incident communications, and documentation of any corrective actions. This thorough approach demonstrates that you’re actively managing third-party privacy risks, not just collecting paperwork.
sbb-itb-535baee
Incident Response and Breach Notification
Logging and Monitoring Privacy Events
Centralized logging plays a crucial role in catching privacy incidents before they spiral out of control. For healthcare vendors, this means ensuring logging is active across all systems that handle Protected Health Information (PHI). This includes electronic health records, clinical applications, data warehouses, and cloud services. These logs should capture every access, modification, export, and disclosure of PHI, creating a comprehensive audit trail.
The AICPA Privacy Management Framework emphasizes the need to "create and retain a complete, accurate and timely accounting of disclosures and a record of detected or reported unauthorized disclosures (including breaches) of PHI" [2]. Your logging system should monitor both significant security events and everyday access patterns that might signal unauthorized activity, like unusual data downloads or access attempts during odd hours. Setting up alerts for bulk data downloads, after-hours access, or repeated failed logins can help you catch issues early.
It’s important to define thresholds that align with your specific environment to avoid unnecessary noise while still identifying real threats. Regularly revisiting these criteria ensures they remain effective and relevant. SOC 2 auditors will expect evidence that your organization can manage both large-scale breaches and smaller privacy incidents with mature detection systems. Strong logging practices lay the groundwork for a swift and effective breach response.
Breach Notification Responsibilities
Once logging systems are in place, the next step is ensuring immediate breach notifications. A centralized logging system empowers your team to detect and respond to breaches quickly, which is critical for compliance. Under HIPAA, healthcare vendors acting as business associates must notify their covered-entity customers without unnecessary delay - no later than 60 days after discovering a breach that impacts 500 or more individuals [2]. Your incident response plan should clearly outline who needs to be notified, when, and how. This includes affected individuals, the U.S. Department of Health and Human Services (HHS), and, in cases of major breaches, possibly the media.
An effective incident response plan assigns clear responsibilities to key team members, such as your privacy officer, security officer, legal team, and compliance staff. The plan should document every step of the process, from reporting and classifying incidents by severity to escalating them as needed. Pre-approved notification templates, internal escalation procedures, and timelines should align with both HIPAA requirements and any contractual obligations with customers. Business associate agreements should also specify the maximum timeframe for notifying customers of potential incidents.
Every privacy incident should be meticulously documented, including the discovery date, the number of affected individuals, the root cause, containment measures, and notifications sent. This level of detail not only ensures compliance but also demonstrates to SOC 2 auditors that your incident response process is thorough and reliable. Using risk management tools like Censinet RiskOps™ can streamline the detection, management, and documentation of privacy incidents, helping you stay organized and efficient.
Preparing for SOC 2 Privacy Audits
Keeping Policy and Control Documentation Current
Having a well-organized documentation library is crucial when preparing for a SOC 2 Privacy audit. Auditors will want to see current policies that address every part of your privacy management process - from how you collect and store data to how you handle patient rights and respond to breaches. This includes outlining the responsibilities of your privacy officer, detailing approval workflows for policy updates, and setting a regular review schedule (usually annually) [2]. Additionally, update your data flow diagrams to clearly show how Protected Health Information (PHI) moves through your systems, from its creation to its eventual disposal. Training records are equally important - they demonstrate that your team understands and adheres to these policies.
The AICPA Privacy Management Framework emphasizes the need for clear governance processes [2]. This means you need to document not only what your policies cover but also how they’re communicated, approved, and enforced. Keep records of policy version histories, leadership approvals, and proof that employees have completed privacy training and acknowledged the policies. Auditors will want to see that your documented practices align with your actual operations.
Gathering Evidence to Prove Controls Are Effective
Policies alone won’t cut it - you need to show that your controls are actually working. For SOC 2 Privacy, some of the most critical evidence includes logs of patient access and amendment requests, your responses (including any denials with documented reasons), and timelines proving you’ve met HIPAA’s requirements [2]. You’ll also need comprehensive records of both authorized and unauthorized disclosures of PHI, as the AICPA framework prioritizes tracking the entire lifecycle of data [2].
Evidence collection should go beyond the basics. Include access logs showing who has viewed or modified PHI, system-generated reports of privacy-related events, incident response documentation, and results from third-party audits. Don’t wait until the last minute to gather this material. Instead, create a centralized evidence repository where documentation is continuously updated throughout the year. Link each piece of evidence directly to the relevant SOC 2 Privacy criteria to ensure it’s easy to retrieve when the audit begins. Using specialized technology can simplify this process and keep your evidence collection organized and audit-ready.
Leveraging Technology for Efficient Audit Preparation
Manually collecting evidence can quickly become overwhelming, especially for vendors managing complex PHI workflows. Tools like Censinet RiskOps™ can help by automating much of this process. These platforms centralize risk data, streamline third-party assessments, and maintain ongoing compliance monitoring. Designed specifically for the healthcare industry, such technology allows vendors to securely share completed security questionnaires and other supporting documents with healthcare organizations, making audit preparation faster and more collaborative.
Before your formal audit, it’s wise to conduct an internal readiness assessment to spot any gaps. Map your existing controls to each Privacy criterion and focus area, then identify missing policies, weak evidence, or inconsistent practices. Use this assessment to create a control matrix that aligns SOC 2 Privacy requirements with HIPAA standards and develop a prioritized plan to address any deficiencies. This proactive approach ensures you can resolve issues ahead of time, making the audit process smoother and more predictable.
Conclusion and Key Takeaways
Achieving SOC 2 Privacy compliance demands a consistent focus on protecting patient data at every stage of its lifecycle [2]. Each step in the process - whether it's defining controls, monitoring activities, or proving their effectiveness - requires thorough documentation and evidence [2]. The checklist provided here offers a straightforward, repeatable framework: map your data flows, define your scope, establish governance and privacy policies, address third-party risks, and ensure audit readiness with systematic documentation [2].
Once your data flows are mapped and policies are in place, securing leadership support becomes the next critical step. For organizations just starting out, appointing an executive sponsor, such as a CISO, CIO, or compliance officer, can provide the leadership needed to drive the initiative forward [2]. Set a practical timeline of 6–12 months to prepare for an audit, allowing sufficient time to gather evidence and demonstrate consistent control operations for a Type II report [3]. Keep in mind that SOC 2 Privacy and HIPAA often overlap, so implementing controls for one can frequently address the requirements of the other, simplifying compliance efforts.
Adopt a patient-first, risk-based approach by embedding privacy responsibilities across all departments that handle PHI. Platforms like Censinet RiskOps™ can help by centralizing risk management data and automating evidence collection, which streamlines the compliance process.
Effective documentation is the backbone of audit readiness. Keep policies up-to-date, maintain a well-organized evidence repository, and ensure each document directly supports specific SOC 2 Privacy criteria. This disciplined approach not only simplifies audits but also establishes your organization as a reliable steward of patient privacy. By maintaining robust documentation and continuously refining your processes, you can turn audit preparation into a predictable, stress-free task while reinforcing your commitment to safeguarding patient data.
FAQs
What’s the difference between SOC 2 Privacy and HIPAA when it comes to protecting patient data?
SOC 2 Privacy emphasizes the importance of operational controls and policies to protect data. It focuses heavily on ongoing risk management and the assessment of third-party vendors, aiming to uphold robust data protection and privacy standards.
HIPAA, in contrast, outlines specific legal requirements for managing protected health information (PHI). These include detailed rules for privacy, security, and breach notifications, all designed to meet federal guidelines and safeguard sensitive patient information.
While both frameworks share the goal of protecting patient data, SOC 2 leans toward enhancing operational processes, whereas HIPAA strictly enforces compliance within the healthcare sector.
How can healthcare vendors prepare for a SOC 2 Privacy audit?
Healthcare vendors aiming for a SOC 2 Privacy audit need to prioritize safeguarding patient data and meeting the SOC 2 privacy criteria. Here’s how to get started:
Begin with a comprehensive risk assessment to uncover potential vulnerabilities. Once identified, put robust privacy policies and controls in place to address them. Make sure to document everything - data handling processes, access protocols, and incident response plans should all be clearly detailed.
It’s crucial to keep privacy policies up to date. Regulations evolve, and regular reviews ensure your policies remain compliant. Conducting internal audits and gap analyses can pinpoint weaknesses, while ongoing staff training ensures everyone understands and follows privacy best practices.
Using tools like Censinet RiskOps™ can simplify the process. A platform like this can help you conduct efficient risk assessments, monitor compliance, and manage third-party risks - all in one place. These efforts not only prepare you for the audit but also highlight a strong commitment to patient privacy.
What steps can healthcare vendors take to manage third-party risks while meeting SOC 2 Privacy requirements?
Healthcare vendors can address third-party risks under SOC 2 Privacy requirements by using tools designed for continuous risk assessment and automated monitoring. These tools simplify vendor evaluations, deliver real-time updates on third-party security measures, and help maintain compliance with SOC 2 standards.
By embracing collaboration and using technology to minimize manual effort, vendors can take a more efficient and proactive stance in safeguarding patient data and upholding privacy standards.


