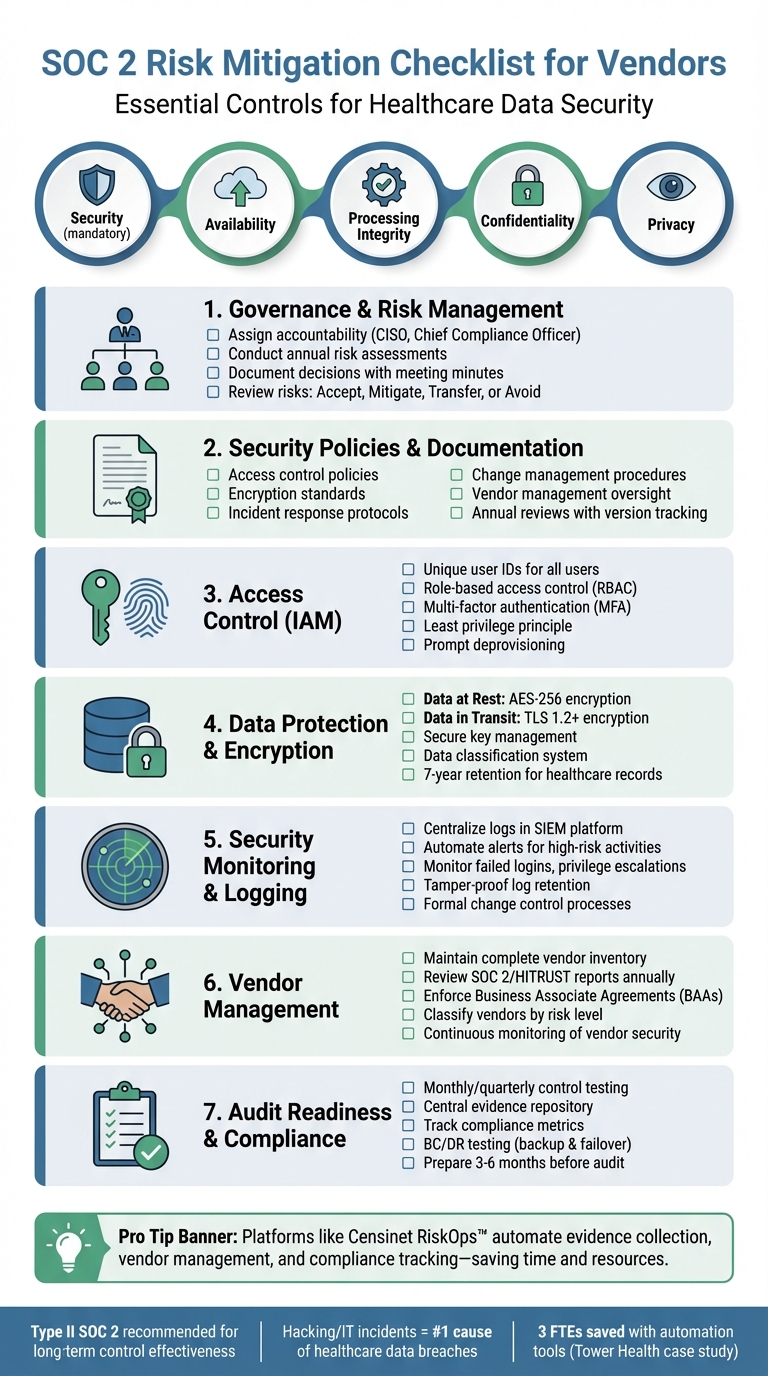
SOC 2 Risk Mitigation Checklist for Vendors
Post Summary
SOC 2 compliance is essential for healthcare vendors handling sensitive data like PHI. It demonstrates your commitment to security, aligns with HIPAA requirements, and builds trust with healthcare clients. This guide breaks down key areas to focus on, including governance, risk management, access controls, and incident response.
Key Takeaways:
- SOC 2 evaluates security controls based on five criteria: Security (mandatory), Availability, Processing Integrity, Confidentiality, and Privacy.
- Vendors should prioritize Type II SOC 2 reports to showcase long-term control effectiveness.
- Align SOC 2 efforts with HIPAA requirements, such as encryption, access control, and breach notification.
Checklist Highlights:
- Governance: Assign accountability, conduct annual risk assessments, and document decisions.
- Policies: Establish clear security policies covering access, encryption, and vendor management.
- Access Control: Use role-based access, enforce MFA, and deprovision promptly.
- Data Protection: Encrypt PHI (AES-256 for data at rest, TLS 1.2+ for data in transit) and securely manage encryption keys.
- Monitoring: Centralize logs in a SIEM, automate alerts, and test incident response plans regularly.
- Vendor Management: Maintain an inventory of third-party vendors, review SOC reports annually, and enforce BAAs.
- Audit Readiness: Use tools to automate evidence collection, track compliance metrics, and prepare for audits.
Pro Tip: Platforms like Censinet RiskOps™ can streamline compliance, evidence collection, and vendor management, saving time and resources.
Start by identifying relevant SOC 2 criteria for your services, then follow this checklist to strengthen your security posture and maintain healthcare client trust.
SOC 2 Compliance Checklist for Healthcare Vendors
Governance and Risk Management Controls
Security Governance and Risk Assessment Processes
When addressing SOC 2 requirements, your governance framework should clearly outline who holds accountability for security decisions and how risks are communicated within the organization. Create a formal charter that assigns responsibilities for protecting PHI, overseeing clinical operations, and managing vendors - these roles are often designated to a CISO, Chief Compliance Officer, or a dedicated risk committee. To provide audit evidence, maintain detailed meeting minutes and decision logs. Auditors will expect to see that your leadership team actively reviews risk assessments and formally approves major security-related decisions.
Conduct risk assessments for systems that store or process PHI at least once per year, and supplement these with additional reviews following significant events such as new integrations, infrastructure changes, or security breaches. Pay special attention to healthcare-specific risks like ransomware targeting clinical systems, unauthorized access to PHI, or supply chain vulnerabilities. Document how you handle these risks - whether you choose to accept, mitigate, transfer, or avoid them. For instance, you might accept risks with a low likelihood of occurrence, mitigate high-impact risks through encryption and monitoring, transfer risks using cyber insurance, or avoid risks altogether by not storing sensitive data.
Security Policies and Documentation
SOC 2 audits require a solid foundation of security policies tailored to the needs of healthcare organizations. These should cover key areas such as:
- Access control: Who can access PHI and under what conditions.
- Encryption: Protecting data both at rest and during transmission.
- Incident response: Timelines and protocols for breach notifications.
- Change management: Safely updating clinical systems.
- Vendor management: Oversight of third-party providers.
Each policy should reference relevant HIPAA requirements and include emergency access procedures specific to healthcare settings.
Ensure your policies follow a structured lifecycle, including formal leadership approval, annual reviews with version tracking, and documented acknowledgment from employees. Keep records of employee training and signed acknowledgment forms for each policy. Auditors often sample employees to confirm that your workforce understands and adheres to these policies.
Third-Party and Fourth-Party Risk Management
Compile a complete inventory of vendors that access PHI or support critical clinical services. This list should include cloud providers, EHR hosts, billing processors, analytics platforms, and subcontractors. Classify these vendors by their risk level, considering both the sensitivity of the data they handle and the importance of the services they provide. For high-risk vendors, perform thorough due diligence, including security questionnaires, reviews of SOC 2 or HITRUST reports, and documentation of any control gaps along with compensating measures.
Establish Business Associate Agreements (BAAs) with all vendors handling PHI. These agreements should outline breach notification requirements, audit rights, and termination clauses. Beyond the initial contract, implement continuous monitoring by reviewing updated SOC reports annually, tracking vendor security incidents, and reassessing risks when vendors make significant changes to their infrastructure or ownership. Many healthcare leaders emphasize that robust third-party management is one of the most impactful SOC 2 control areas, as it significantly reduces the risk of breaches and service downtime across the ecosystem.
For vendors managing complex assessments and evidence collection across multiple healthcare delivery organizations, tools like Censinet RiskOps™ (https://censinet.com) can streamline vendor management. This platform centralizes vendor inventories, automates due diligence workflows, and maintains a library of completed security questionnaires with supporting documentation. Such tools can also help you share security information with potential customers early in the sales process. Up next, we’ll delve into access and data protection controls to further safeguard sensitive healthcare data.
Access and Data Protection Controls
Identity and Access Management (IAM)
Assign unique user IDs to every system user to maintain clear audit trails - shared accounts make tracking activity difficult. Use role-based access control (RBAC) by defining roles like clinical staff, billing administrators, and IT support. Then, assign permissions based on each role's specific job duties. Stick to the least privilege principle, ensuring users only access the data and systems necessary for their tasks. Access should be strictly limited by role.
Require multi-factor authentication (MFA) for all remote access and privileged accounts, especially those dealing with protected health information (PHI) or operating in production environments. Auditors will expect to see a formal approval process for provisioning access, which typically involves manager sign-off. Keep detailed logs showing who approved access requests and when. Similarly, your deprovisioning process should immediately revoke access when someone leaves their role or the organization. Maintain proper documentation to support these changes. Additionally, implement data labeling and encryption to safeguard sensitive information.
Data Classification and Encryption
Create a data classification system to differentiate between PHI, confidential business information, internal data, and public content. Label systems according to these classifications and apply the highest encryption standards to PHI, whether it’s in transit or at rest.
For data in transit, use TLS 1.2 or higher for web traffic and secure file transfer protocols like SFTP. For data at rest, encrypt databases, backups, and file storage using AES-256. Document your encryption key management processes, including how keys are generated, stored, rotated, and retired. Auditors will also examine your data retention and disposal policies to confirm PHI is securely deleted after the mandatory retention period, which is typically seven years for healthcare records under state and federal laws.
Endpoint, Network, and Infrastructure Security
Ensure all servers, workstations, and cloud instances follow secure baseline configurations. This includes disabling unnecessary services, enforcing strong passwords, deploying endpoint detection and response (EDR) tools, and applying critical patches without delay.
Use network segmentation to separate production environments handling PHI from development and testing systems. Firewalls and access control lists should restrict traffic between these segments, allowing only authorized services to communicate across boundaries. For remote access, require VPN connections secured with MFA and monitor all privileged sessions. Regularly review firewall rules and access logs to detect anomalies or unauthorized attempts to connect. These practices work hand-in-hand with your broader SOC 2 risk management strategies outlined earlier.
sbb-itb-535baee
Security Monitoring and Incident Response
Security Monitoring and Logging
SOC 2's Security Common Criteria emphasizes the importance of system monitoring, logging, and incident response to quickly detect and address security threats [2]. Setting up automated alerts for high-risk activities, such as failed login attempts, privilege escalations, unusual access to PHI, or configuration changes, is crucial. These alerts act as an early warning system, giving your team the chance to respond before issues spiral out of control.
Centralizing PHI logs from various sources - applications, databases, firewalls, endpoints, and cloud services - into a single SIEM platform simplifies event correlation across your infrastructure. This approach helps identify patterns that could signal an attack. Additionally, securing PHI logs ensures they remain tamper-proof, which is critical for forensic investigations and compliance with retention policies. Auditors rely on the integrity of these logs to validate their accuracy during reviews.
To further minimize risks, implement formal change control processes that include documented approvals, rigorous testing, and rollback plans. Integrating these controls with monitoring logs strengthens your ability to manage changes effectively. Poorly managed changes are a common cause of security incidents, so combining strict change management with robust monitoring is a strong defense strategy [5][2]. Together, these practices form the foundation of a reliable incident response process.
Incident Response Planning and Testing
Effective monitoring is just the start - it's essential to have a well-defined incident response plan in place. This plan should outline roles, escalation procedures, and communication strategies. Assign clear responsibilities, such as determining who will investigate incidents, notify leadership, engage legal counsel, and handle external communications. For PHI-related incidents, include breach notification protocols that comply with the HIPAA Breach Notification Rule. This rule mandates notifying affected individuals, the Department of Health and Human Services (HHS), and, in some cases, the media within specific timeframes [3][4]. Additionally, ensure your business associate agreements (BAAs) detail how and when healthcare partners will be informed about incidents involving their data.
Regular testing of your incident response plan is just as important as creating it. Conduct tabletop exercises at least once a year, simulating scenarios like ransomware attacks, insider data theft, or vendor compromises. These exercises help identify strengths and weaknesses in your plan. Use the lessons learned to make necessary updates. Data from HHS/OCR breach reports highlight that hacking and IT incidents are now the top causes of large healthcare data breaches. This underscores the critical role of continuous monitoring, log analysis, and a swift response in protecting vendor environments that handle PHI [3].
Business Continuity and Disaster Recovery
Backup strategies are a cornerstone of business continuity. Schedule regular backups for critical systems and PHI, and document the details - backup frequency, scope, and storage locations. Periodically test your ability to restore data to confirm your backups are functional. Auditors will expect proof that these backups are both performed and effective.
For systems supporting clinical workflows, establish and test failover methods, such as secondary data centers, cloud region failovers, or manual recovery procedures. Define recovery time objectives (RTOs) and recovery point objectives (RPOs) that align with the needs of patient care. Document these targets and verify that your infrastructure can meet them under realistic failure conditions [1][4]. These steps ensure you’re prepared to maintain operations and recover quickly in the face of disruptions.
Maintaining Compliance and Audit Readiness
Continuous Compliance Monitoring
Keeping SOC 2 compliance intact requires ongoing monitoring and staying prepared for audits. Earning SOC 2 certification is just the starting point - you need to ensure compliance year-round by scheduling regular control tests. For example, conduct monthly or quarterly change management sampling to confirm that any production changes involving PHI-bearing systems follow proper approval, testing, and rollback protocols. Regularly perform business continuity and disaster recovery (BC/DR) tests, which should include backup restore tests and partial failover exercises for critical hosting systems. Be sure to document these tests, outlining their frequency, methods, roles, and the evidence needed.
Track key compliance metrics to show consistent readiness. These might include access and identity stats, such as the percentage of users reviewed quarterly, or the number of orphaned and over-privileged accounts identified and resolved. Also, monitor security awareness data like training completion rates, phishing simulation outcomes, and the number of policy exceptions along with their justifications. Assign specific control owners across IT, security, engineering, and compliance teams, and define clear RACI (Responsible, Accountable, Consulted, Informed) roles, including escalation paths for exceptions. Use GRC tools to dashboard these metrics, making it easier to spot trends and highlight continuous improvements to auditors and healthcare clients. This kind of proactive oversight naturally feeds into structured evidence collection, ensuring you're always ready for audits.
Evidence Management and Audit Preparation
To stay audit-ready, managing evidence effectively is just as important as monitoring compliance. The same controls that protect PHI on a daily basis also create the foundation for solid audit trails. Avoid the last-minute scramble by organizing evidence continuously. Set up a central evidence repository - preferably within a secure GRC or compliance platform - with folders clearly mapped to SOC 2 criteria and specific controls. Keep version-controlled policies and procedures for areas like information security, incident response, vendor management, BC/DR, and data retention. Include details like approval dates, owners, and review cycles to ensure clarity and accountability.
Automate the collection of technical evidence, such as system exports, access logs, and SIEM data, to align with your SOC 2 review period. Implement retention rules that meet SOC 2 requirements, typically retaining evidence for the full Type II period plus one prior period. Start preparing for audits 3–6 months before the review period ends by confirming the scope, conducting internal mock audits to identify gaps, and freezing scope changes where possible. Assign a single audit liaison to streamline communication and pre-share evidence to make the audit process smoother.
Using Censinet for SOC 2 Compliance
Censinet RiskOps™ simplifies SOC 2 compliance monitoring and audit preparation through automation. This cloud-based risk exchange continuously collects evidence - like logs, configurations, and access lists - eliminating the need for manual spreadsheets. With Censinet Connect™, vendors can share completed security questionnaires and supporting documentation with potential customers early in the sales process, speeding up both audit readiness and sales cycles.
The platform also offers cybersecurity benchmarking, allowing vendors to measure their performance against industry standards, spot gaps, and keep improving. Terry Grogan, CISO at Tower Health, emphasized the efficiency gains:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."
James Case, VP & CISO at Baptist Health, shared how it transformed their operations:
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with."
FAQs
What’s the difference between SOC 2 Type I and Type II reports?
SOC 2 Type I reports evaluate whether the required controls are in place and properly designed at a specific moment. On the other hand, SOC 2 Type II reports go a step further by examining how well those controls function over a period - usually six months or more.
Think of Type I as a quick snapshot of your compliance setup, while Type II offers a broader perspective, showing how your controls hold up in real-world scenarios over time. Both play a key role in showcasing trust and accountability, particularly in sectors like healthcare, where safeguarding sensitive information is a top priority.
How can vendors ensure their security policies meet both SOC 2 and HIPAA standards?
To align with both SOC 2 and HIPAA standards, vendors need to establish strong controls that safeguard the confidentiality, integrity, and availability of sensitive data, including protected health information (PHI). It's essential to routinely review and update security policies to keep pace with changing compliance requirements.
A tool like Censinet RiskOps™ can simplify this process by streamlining risk assessments, ensuring consistent policy enforcement, and offering continuous monitoring. This approach helps organizations effectively manage risks while building and maintaining trust with healthcare partners.
What are the essential steps for healthcare vendors to prepare for a SOC 2 audit?
Preparing for a SOC 2 audit in healthcare requires careful planning and attention to detail. Begin with a comprehensive risk assessment to pinpoint vulnerabilities and gain a clear understanding of the requirements across key areas: security, availability, processing integrity, confidentiality, and privacy.
Once you've identified these needs, establish and implement the appropriate controls to address them. Make sure to thoroughly document all related policies and procedures. Conduct internal audits on a regular basis to uncover any gaps and address them quickly. Using tools like Censinet RiskOps™ can simplify the process, helping you manage risks effectively and keep compliance efforts on track.


