Top Medical Device Security Training Providers 2025
Post Summary
Medical device security training equips healthcare professionals and organizations with the skills to protect devices from cyber threats, ensuring patient safety and regulatory compliance.
Leading providers include TRIMEDX CE Cyber Academy, University of Minnesota’s CMDC, UL Solutions’ Medical Cybersecurity Assurance Program, and Tonex Training.
Topics include risk assessment, vulnerability management, regulatory compliance (e.g., HIPAA, FDA), secure design, and incident response.
Professionals in IT, clinical engineering, product development, and regulatory compliance, as well as healthcare administrators, benefit from these programs.
Programs often align with standards like IEC 81001-5-1, UL 2900, and ISO 27001, and address HIPAA and FDA requirements.
Organizations should evaluate providers based on course content, industry relevance, certifications offered, and alignment with regulatory standards.
Medical device security training is critical for healthcare professionals to address rising cybersecurity threats and meet strict FDA regulations. These programs focus on securing devices like infusion pumps and imaging systems, emphasizing patient safety and compliance. By 2025, organizations must prioritize training to manage risks, prevent ransomware attacks, and align with FDA's Section 524B requirements.
Key providers include:
- TRIMEDX CE Cyber Academy: Focuses on hands-on, lifecycle-based training tailored to roles like clinical engineers and IT teams.
- Crothall Medical Device Cybersecurity Training: Integrates training into daily hospital operations with flexible formats.
- IEEE Medical Device Cybersecurity Certification Program: Offers an independent certification, though details are limited.
- NSF Medical Devices and IVDs Training: Covers regulatory compliance and integrates cybersecurity into device lifecycle management.
- BSI Medical Device Regulation Training: Emphasizes global standards like ISO 14971 and FDA alignment.
- Biopharma Institute Medical Device Training: Provides online, self-paced courses for regulatory and quality assurance professionals.
- Censinet RiskOps™: Combines risk management tools with hands-on training for lifecycle security.
Each provider addresses unique needs, from role-specific tracks to practical, scenario-based learning. Below is a quick comparison of their offerings.
Quick Comparison
| Provider | Key Features | Formats | Focus Areas |
|---|---|---|---|
| TRIMEDX CE Cyber Academy | Hands-on training with real-world data; role-specific tracks | Self-paced, live workshops | Lifecycle security, FDA compliance |
| Crothall | Integrated into hospital workflows; flexible training formats | Onsite, virtual modules | Daily operations, FDA alignment |
| IEEE Certification | Independent assessment; limited public details | Contact IEEE for details | Certification-based approach |
| NSF | Regulatory compliance; lifecycle integration | Instructor-led, workshops | ISO 14971, FDA submissions, risk management |
| BSI | Global standards focus; tailored tracks | Classroom, virtual, on-demand | ISO 13485, FDA alignment, post-market security |
| Biopharma Institute | Self-paced online courses; QR-validated certificates | Asynchronous eLearning | FDA compliance, quality systems |
| Censinet RiskOps™ | Platform-based training; hands-on risk management | E-learning, workshops, labs | FDA compliance, lifecycle risk management |
For healthcare organizations, selecting the right provider ensures improved device security, compliance, and patient safety.
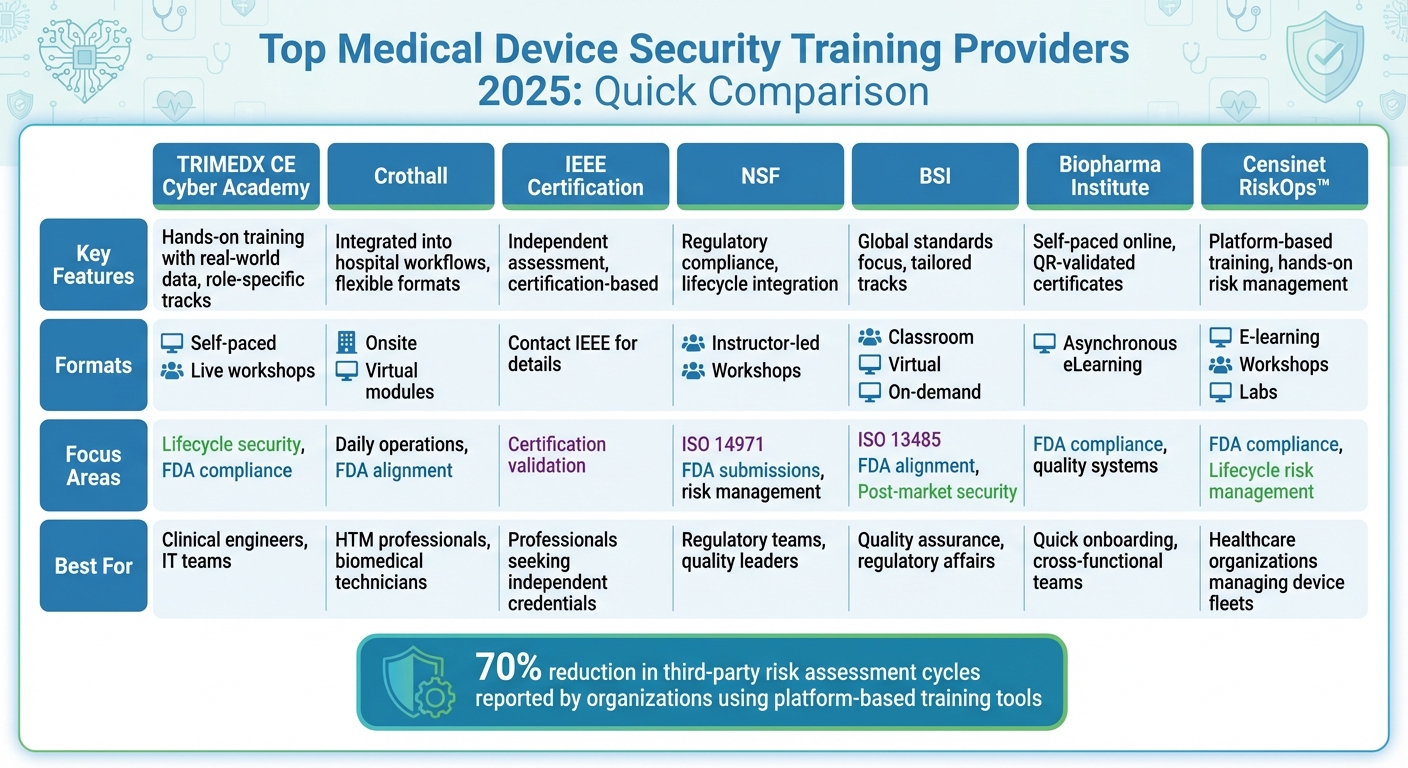
Top 7 Medical Device Security Training Providers 2025 Comparison Chart
How To Evaluate Medical Device Security Training Providers
Choosing the right medical device security training provider requires careful consideration, starting with ensuring regulatory alignment. The training should address FDA cybersecurity guidance for both premarket and postmarket medical devices. Key topics include threat modeling, SBOM (Software Bill of Materials), vulnerability management, and quality systems. Look for courses that reference critical frameworks like AAMI TIR57, AAMI SW96, and ISO 14971 for cybersecurity risk management. Additionally, ensure the curriculum incorporates relevant ISO/IEC security standards used in medical device evaluations. Don’t hesitate to request syllabi that detail which regulations and standards are covered in each module and how frequently the content is updated to reflect new FDA or standards body guidance.
Another critical factor is lifecycle coverage. Strong training programs go beyond basic compliance and cover the entire device lifecycle. This includes secure development practices, premarket risk assessment, deployment and configuration in clinical environments, postmarket monitoring, and incident response for connected devices. Providers offering incident response training and tabletop exercises demonstrate a commitment to comprehensive lifecycle education. Ask if they provide a clear lifecycle map that spans from concept to retirement, complete with relevant hands-on exercises.
For healthcare delivery organizations (HDOs), HDO-focused training is essential. Training should address unique challenges such as shared devices, legacy equipment, EHR integration, and limited patching opportunities. It should also cover managing third-party device inventories and coordinating with biomedical and clinical engineering teams while aligning cybersecurity measures with clinical workflows. Look for sample case studies involving hospitals or health systems, references from U.S.-based provider organizations, and examples of how the training enhances the security posture of device fleets - not just achieving product approval.
Tailoring content to specific roles within your organization is equally important. Role-specific training paths ensure that clinical engineers, IT staff, regulatory teams, and R&D professionals receive material relevant to their responsibilities. Effective programs validate learning outcomes through quizzes or performance-based labs, ensuring that participants can apply what they’ve learned.
Finally, consider the delivery formats and practical learning methods offered. U.S.-based HDOs often benefit from a mix of self-paced modules, live virtual Q&A sessions, and on-site workshops featuring hands-on labs. The best programs use device-specific case studies to illustrate real-world vulnerability mitigation strategies. Confirm that the exercises reflect current attack methods and simulate cross-team coordination. Recognized certificates of completion tied to clear learning objectives are a plus, particularly if they include CE, CME, or CEU credits for professional development in fields like clinical engineering, healthcare IT, and regulatory compliance.
1. TRIMEDX CE Cyber Academy
TRIMEDX CE Cyber Academy takes a hands-on, data-centered approach to training, focusing on real-world scenarios and practical application. As the educational branch of TRIMEDX - a company known for managing medical device inventories and identifying vulnerabilities for U.S. healthcare providers - the academy equips clinical engineering and technology teams with the tools they need to tackle actual challenges in device security. By using real fleet data and vulnerability scenarios, the academy ensures its training aligns with the regulatory standards discussed earlier [4].
Alignment with FDA Medical Device Cybersecurity Expectations
The academy builds its curriculum around FDA guidelines, applying those principles to real-world situations. Participants gain expertise in interpreting manufacturer cybersecurity documentation, Software Bills of Materials (SBOMs), and security bulletins. These skills directly support FDA requirements, such as coordinated vulnerability disclosures, timely issue resolution, and documenting risk decisions for connected medical devices [3]. This training lays the groundwork for developing a robust, lifecycle-focused security strategy.
Coverage of Device Lifecycle Security
The program addresses cybersecurity across every stage of a device's lifecycle - planning, procurement, deployment, maintenance, and even decommissioning. By working with real inventory data, participants learn how to evaluate and remediate security risks effectively [4]. This comprehensive approach reflects the FDA's emphasis on continuous cybersecurity management rather than limiting efforts to the point of purchase or approval.
Role-Specific Training Tracks
To meet the diverse needs of healthcare organizations, the academy offers tailored training tracks for various roles:
- Biomedical technicians and clinical engineers: Hands-on training in secure device configuration and troubleshooting for networked devices [4].
- Clinical engineering (CE) and healthcare technology management (HTM) leaders: Guidance on creating risk-based remediation plans, integrating cybersecurity into capital planning, and effectively communicating risks to executives.
- IT and information security teams: Training on incorporating medical devices into broader hospital security frameworks, including network segmentation, monitoring, and identity management.
- Risk, compliance, and quality leaders: Skills in documenting cybersecurity measures for policies, audits, and incident reports to meet the expectations of the FDA, CMS, and accrediting bodies.
Each track incorporates operational data and dashboards to simulate decision-making scenarios typical in U.S. hospitals [4].
Training Formats and Practical Application
The academy offers a mix of self-paced modules, live workshops, and tabletop exercises to help teams address vulnerabilities, coordinate with manufacturers, and assess clinical impacts [2][4]. Simulated incidents provide interdisciplinary teams with the experience needed to handle real-world risks. Participants work with anonymized datasets that include device models, software versions, known CVEs, and clinical criticality ratings. These datasets mirror how TRIMEDX's algorithms and experts prioritize cybersecurity efforts, giving learners a realistic and practical foundation for managing device security [4].
2. Crothall Medical Device Cybersecurity Training
Crothall Healthcare Technology Solutions weaves cybersecurity training into its clinical engineering and healthcare technology management (HTM) services. This training equips a broad range of professionals - biomedical technicians, clinical engineers, HTM managers, IT security teams, and clinical staff - with the tools they need to secure connected medical devices. By embedding this training into daily operations, Crothall ensures it not only supports routine tasks but also aligns with regulatory requirements.
Alignment with FDA Medical Device Cybersecurity Expectations
Crothall’s training approach is closely tied to the FDA’s cybersecurity guidelines for medical devices. The program helps healthcare professionals navigate these federal standards, focusing on the key principles and protocols necessary to secure connected devices. By emphasizing the importance of these guidelines, Crothall aids hospitals in staying compliant while prioritizing patient safety.
Training Formats and Practical Application
Training is offered through onsite sessions as part of HTM services and virtual modules for flexibility. To enhance learning, Crothall incorporates hands-on elements like tabletop exercises and walk-throughs that mimic real-world scenarios in hospital settings. These sessions are designed to integrate seamlessly with daily workflows, ensuring staff can build critical cybersecurity skills without interrupting their routines.
3. IEEE Medical Device Cybersecurity Certification Program
The IEEE Medical Device Cybersecurity Certification Program is gaining attention as a newer option in the industry. While public details are sparse, the program is described as an independent conformity assessment centered on medical device cybersecurity. However, specifics regarding its evaluation criteria, alignment with FDA guidelines, and tailored training for different roles have not been shared publicly. To fully understand how this certification might fit into your cybersecurity and regulatory plans, it's best to reach out to IEEE directly for the latest information.
4. NSF Medical Devices and IVDs Training
NSF International offers a comprehensive training program for Medical Devices and IVDs, focusing on regulatory compliance and quality management while integrating cybersecurity into every aspect. Their curriculum covers key standards like ISO 13485, ISO 14971, FDA requirements, and EU MDR/IVDR compliance. Cybersecurity is treated as an essential component of product risk management, technical documentation, and post-market surveillance. This ensures that cyber risks are effectively addressed in areas like risk files, design controls, and FDA premarket submissions, establishing a consistent approach to compliance throughout the device's lifecycle [1][6].
Alignment with FDA Medical Device Cybersecurity Guidelines
NSF's cybersecurity-focused courses align closely with FDA expectations by connecting cyber risks to a Secure Product Development Framework (SPDF). These courses emphasize critical topics like threat modeling, implementing risk controls, maintaining Software Bill of Materials (SBOMs), integrating cybersecurity into design controls, and planning for ongoing vulnerability monitoring and timely updates. This approach supports comprehensive security practices across the entire product lifecycle.
Incorporating Cybersecurity Across the Device Lifecycle
NSF training ensures cybersecurity is embedded at every stage of the product lifecycle - from the initial concept and design phase to post-market surveillance and eventual decommissioning. Cybersecurity considerations are integrated into user needs, design inputs, verification plans, and software update management, creating a robust framework for lifecycle security.
Role-Specific Training Options
NSF customizes its training to meet the needs of different roles within an organization. Regulatory professionals, quality leaders, design teams, and post-market personnel can all find courses tailored specifically to their responsibilities. For instance:
- Regulatory courses focus on incorporating cybersecurity measures into FDA and EU submission documents.
- Risk management courses guide teams on integrating cyber threats into ISO 14971-compliant frameworks.
- U.S. manufacturers can send their regulatory teams to courses that clarify documentation requirements for both FDA and EU regulations, while risk teams focus on embedding cyber risks into established processes.
Flexible Training Formats with Practical Focus
NSF offers its training in various formats to suit different needs, including instructor-led public courses (both virtual and in-person), in-house workshops customized for specific organizations, and modular programs. Practical learning is a key focus, with case studies, hands-on exercises, and scenario-based workshops. Participants gain experience in creating compliant technical documentation, mapping security issues into design controls, and managing risk files and post-market procedures. To further support their learning, attendees receive useful tools like checklists and templates for risk management documentation.
sbb-itb-535baee
5. BSI Medical Device Regulation Training
BSI offers specialized training for medical device professionals, focusing on global regulatory standards and quality management systems. As the first national standards body and a Notified Body under EU MDR and IVDR, BSI brings a practical regulatory perspective to its courses. Their training portfolio includes ISO 13485, ISO 14971 risk management, EU MDR/IVDR compliance, clinical evaluation, and post-market surveillance - all critical frameworks for managing security and risk throughout a device's lifecycle. This foundation also supports alignment with FDA cybersecurity standards.
Alignment with FDA Medical Device Cybersecurity Expectations
BSI’s training integrates global standards, such as ISO 13485 and ISO 14971, which are recognized by the FDA. While their courses don’t delve into highly technical areas like threat modeling or SBOMs, they focus on building a strong quality framework. This approach equips manufacturers with the tools to develop FDA-compliant quality management systems and risk files, ensuring processes meet both international standards and FDA guidelines.
Focus on Device Lifecycle Security
BSI’s courses address security across the entire device lifecycle, emphasizing areas like design controls, risk management, clinical evaluation, and post-market surveillance. These programs guide organizations in embedding cybersecurity considerations into their existing risk management practices. This includes maintaining security documentation, monitoring vulnerabilities, and planning secure updates as part of ongoing post-market surveillance activities.
Tailored Role-Specific Training Tracks
BSI structures its training into role-specific tracks to meet the needs of various teams, such as regulatory affairs, quality assurance, design teams, and post-market surveillance staff. These tracks include implementer courses, internal auditor programs, lead auditor certifications, and MDR/IVDR specialist training. For instance, internal auditor courses teach participants to evaluate not just quality systems but also how cybersecurity measures are integrated into QMS and risk management. This tailored approach ensures that training aligns with the real-world responsibilities of each role.
Flexible Training Formats with Practical Applications
BSI offers its training in various formats to suit different learning needs: classroom sessions, live virtual training, on-demand eLearning, and custom in-house programs. Many courses incorporate hands-on workshops and practical exercises, using real-world documentation like risk management files and clinical evaluation reports. Course fees typically range from $800 to $2,500 per person for advanced multi-day classes, with U.S. pricing available upon request. These programs provide a governance foundation that organizations can enhance with tools like Censinet RiskOps™ for more comprehensive cyber risk management.
6. Biopharma Institute Medical Device Training
Biopharma Institute offers online, self-paced training and certification programs tailored to professionals in quality assurance, regulatory affairs, manufacturing, and clinical roles. Their courses emphasize FDA compliance, global regulatory standards, and quality systems, with over a dozen certification paths covering topics like GMP, FDA 21 CFR Parts 11 & 820, ISO 14155, and validation. These programs are designed to help teams prepare for regulatory requirements and maintain proper compliance documentation, providing a well-rounded approach to medical device training.[5]
Alignment with FDA Medical Device Cybersecurity Expectations
Biopharma's training focuses on FDA 21 CFR compliance and quality system regulations, laying the groundwork for cybersecurity governance in both premarket submissions and post-market monitoring. While these courses don't delve into technical security aspects like threat modeling or software bill of materials (SBOMs), they emphasize the process controls and documentation necessary to manage cybersecurity throughout the device lifecycle.[5]
Training Formats and Practical Application
All training programs at Biopharma are delivered as asynchronous eLearning, allowing professionals to complete courses at their own convenience. One standout offering, the "Introduction to the Regulation of Medical Devices", can be finished in under 60 minutes and includes a certificate with QR-code validation.[5] This quick-start format is ideal for onboarding new team members or equipping cross-functional teams with a regulatory foundation. The QR-verifiable certificates make it simple for employers and auditors to confirm credentials during FDA inspections, MDSAP audits, or ISO assessments. For a more comprehensive approach, pairing Biopharma's regulatory training with tools like Censinet RiskOps™ can help integrate basic compliance with advanced cybersecurity and risk management workflows for medical devices and third-party vendors.
7. Censinet RiskOps for Medical Device Security Training

Censinet RiskOps™ is a cybersecurity and risk management platform tailored specifically for healthcare organizations. It simplifies how healthcare providers manage risks tied to connected medical devices. With its intuitive workflows and real-time dashboards, the platform offers hands-on training scenarios for medical device security. Organizations using Censinet RiskOps have reported cutting third-party risk assessment cycles by over 70% [KLAS], doubling their annual assessments without increasing staff. This efficiency allows teams to focus on strategic security initiatives and workforce development.
Alignment with FDA Medical Device Cybersecurity Expectations
Censinet RiskOps is designed to align with FDA cybersecurity guidelines, incorporating these expectations directly into its risk management processes. It supports key areas such as premarket submission readiness, SBOM (Software Bill of Materials) transparency, vulnerability management, and incident response coordination. The platform's standardized security questionnaires and control frameworks collect evidence that meets FDA requirements while also adhering to NIST, HIPAA, and HICP guidelines. Training programs can use real vendor questionnaires and scoring workflows within RiskOps to teach participants how to create FDA-compliant cybersecurity documentation.
Coverage of Device Lifecycle Security
RiskOps provides tools to manage the entire lifecycle of connected medical devices, from vendor selection to decommissioning. Training can be structured around these workflows, including tasks like conducting third-party risk assessments during procurement, managing cybersecurity clauses in contracts, performing onboarding checks before clinical deployment, and tracking risk decisions throughout the device’s lifecycle. The platform's dashboards, which can be filtered by device type, manufacturer, service line, or risk level, allow trainers to highlight lifecycle risk trends and demonstrate how an organization’s risk profile changes over time.
Role-Specific Training Tracks
The detailed risk data captured by RiskOps enables tailored training for various roles within an organization. For instance, clinical engineering teams can learn to analyze device risk scores and prioritize fixes based on clinical impact. IT and security teams can focus on incorporating RiskOps data into existing vulnerability management and incident response workflows. Supply chain professionals can use vendor assessment results to guide procurement and contracting decisions, while compliance and risk leaders can be trained to create reports that show adherence to internal policies and FDA regulations.
Training Formats and Practical Application
Censinet RiskOps supports a range of training formats to suit different learning needs. These include short, role-based e-learning modules and instructor-led workshops - either virtual or in-person - that walk participants through common device risk scenarios. Lab-style sessions allow users to explore a training or sandbox version of the platform, while tabletop exercises integrate RiskOps data, such as vendor contacts and remediation tracking, into broader incident-response drills. To reinforce key tasks, short micro-learning videos (5–10 minutes) can be used during orientations or annual training sessions, ensuring users stay familiar with the platform’s essential features.
Using Censinet RiskOps in Medical Device Security Training Programs

Incorporating Censinet RiskOps into medical device security training programs allows learners to engage in realistic, hands-on exercises that reflect real-world scenarios. For instance, a hospital's biomed security team could simulate the entire workflow of device onboarding and vendor reviews. This might include launching a risk questionnaire, analyzing responses, importing vulnerability data or SBOMs, scoring risk levels, and documenting controls. By doing so, theoretical knowledge transforms into practical skills aligned with NIST and HIPAA risk management frameworks. These exercises naturally flow into interpreting real-time dashboards for actionable insights.
The platform's dashboards double as instructional tools. Instructors can showcase a device fleet overview, highlighting high-risk devices that access PHI. This visualization helps explain critical concepts like asset importance, risk scoring, and identifying "crown jewel" systems. Additional dashboards can illustrate regulatory alignment, such as tracking the percentage of devices with completed risk assessments or comparing open versus closed remediation tasks. Trainees can then use these tools to answer practical questions like, “Which device category should be prioritized for mitigation funding?” - building their ability to make data-driven security decisions.
RiskOps also integrates policy requirements into its workflows, offering trainees real-world practice. For example, a policy mandating that all internet-connected Class II devices undergo annual security reviews can be configured as either mandatory controls or conditional questions within the platform. During training, learners can design or refine these policies and run mock assessments to see how written guidelines translate into actionable requirements for vendors, IT teams, and clinical engineering staff.
Beyond policy exercises, instructors can simulate complex risk scenarios to deepen understanding. For instance, they might pre-configure situations like a vulnerability in an implantable device or a compromise in remote monitoring systems. Trainees would then assess the affected devices and vendors, evaluate the current control measures, and use RiskOps to propose mitigation strategies. These could include actions like network segmentation, emergency patching, procedural controls, or updating vendor contracts. Trainees can assign tasks, track progress, and monitor outcomes via dashboards - mirroring real-world incident response workflows while reinforcing a risk-based approach to problem-solving.
RiskOps also facilitates joint training sessions between healthcare delivery organizations (HDOs) and vendors, promoting shared responsibility. Vendors can access the same assessment environment as their HDO partners, respond to security questionnaires, upload supporting evidence, and engage in real-time discussions about risk findings. Meanwhile, HDO trainees - spanning roles in security, supply chain, and clinical engineering - can practice evaluating vendor evidence, asking clarifying questions, and negotiating remediation timelines. This collaborative setup mirrors the teamwork required for device hardening, secure deployment configurations, and including PHI protection clauses in contracts.
Conclusion
Selecting the right medical device security training providers is a critical step in protecting patient safety, maintaining smooth clinical operations, and meeting the stringent requirements of FDA and HIPAA regulations. Healthcare organizations face challenges that go far beyond standard IT security concerns - devices like infusion pumps, imaging systems, and implantable technologies introduce unique cybersecurity risks that demand specialized, healthcare-focused training solutions.
An effective training strategy needs to address three key elements: role-specific programs, regulatory and certification alignment, and platform-based workflows. Tailoring training to specific roles - whether for clinical engineers, IT security teams, or frontline staff - ensures that everyone understands and fulfills their part in maintaining device security. Courses aligned with FDA guidance, ISO 14971, and IEEE 2621 standards provide the regulatory knowledge needed to stay compliant. Meanwhile, platform-based workflows embed these lessons into everyday operations, ensuring that security principles are not just learned but also consistently applied throughout the device lifecycle - from procurement to deployment, maintenance, and eventual retirement.
Platform-based training takes this a step further by turning theory into practical, repeatable actions. For instance, tools like Censinet RiskOps™ empower teams to manage device inventories, monitor vulnerabilities, document risk decisions, and produce regulatory evidence using standardized workflows.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."
– Terry Grogan, CISO at Tower Health
This type of operational efficiency, combined with continuous monitoring, ensures healthcare organizations can maintain a robust security posture across thousands of interconnected devices.
Given the ever-changing threat landscape and evolving FDA requirements, training must be an ongoing process. Annual refresh cycles for all roles involved in device security are essential, with more frequent updates when significant vulnerabilities or regulatory changes occur. Incorporating real-world incident analyses into training and tracking recovery metrics can help identify weaknesses and improve programs over time.
Ultimately, medical device security training should be seen as a long-term investment in both patient safety and risk management. By aligning training with role-specific responsibilities and the various stages of the device lifecycle, healthcare organizations can create a secure environment for care. Leveraging specialized platforms and committing to regular updates ensures the development of consistent, policy-driven capabilities that protect patients and support operational resilience in an increasingly connected healthcare ecosystem.
FAQs
What should healthcare organizations look for in a medical device security training provider?
When choosing a medical device security training provider, healthcare organizations should focus on those that deliver specialized training designed for the healthcare sector. The program should address the unique challenges of medical devices and clinical settings while adhering to established industry standards for reliability and practical relevance.
It's equally important to find providers that offer adaptable learning formats to fit the varied schedules and learning styles of healthcare staff. Additionally, take time to assess their experience and reputation - look for testimonials and evidence of successful outcomes with other healthcare organizations to ensure the training provides meaningful, actionable results.
Why is role-specific training important for improving medical device security in healthcare?
Role-specific training plays a key role in equipping healthcare professionals with the tools they need to handle the unique demands of their positions. By customizing training for specific roles - like clinicians, IT staff, and risk managers - organizations can ensure that every team member acquires the practical knowledge necessary to recognize and combat cybersecurity threats effectively.
This targeted strategy not only improves awareness of medical device vulnerabilities but also strengthens understanding of compliance requirements. The result? Better risk management practices and a safer, more secure environment for delivering patient care.
Why is it important to address the entire lifecycle in medical device security training?
Focusing on the entire lifecycle of medical device security is essential to keep devices protected from the moment they're developed until they're decommissioned. This comprehensive approach allows organizations to stay proactive against emerging threats, apply updates promptly, and manage risks effectively during the device's entire operational period.
By prioritizing lifecycle security, healthcare providers can safeguard patient safety, ensure regulatory compliance, and keep pace with the ever-evolving challenges of the cybersecurity landscape.
Related Blog Posts
Key Points:
Why is medical device security training important?
- Cyber Threat Mitigation: Training equips professionals with the knowledge to identify and mitigate vulnerabilities in medical devices, reducing the risk of cyberattacks.
- Patient Safety: Ensures that medical devices operate securely, protecting patient data and maintaining trust in healthcare systems.
- Regulatory Compliance: Helps organizations meet HIPAA, FDA, and other regulatory requirements for medical device security.
What are the top providers of medical device security training?
- TRIMEDX CE Cyber Academy: Offers comprehensive training for clinical engineering and cybersecurity professionals, focusing on bridging gaps between IT and biomedical teams.
- University of Minnesota’s CMDC: Provides short courses on medical device cybersecurity, covering regulatory requirements, risk assessment, and secure design.
- UL Solutions’ Medical Cybersecurity Assurance Program: Focuses on certification, testing, and compliance with standards like UL 2900 and IEC 81001-5-1.
- Tonex Training: Offers a 2-day workshop on medical device cybersecurity, exploring vulnerabilities and risk assessment techniques.
What topics are covered in medical device security training?
- Risk Assessment: Identifying and prioritizing vulnerabilities in medical devices.
- Regulatory Compliance: Understanding HIPAA, FDA, and international standards like IEC 81001-5-1 and UL 2900.
- Secure Design: Implementing security-by-design principles in medical device development.
- Incident Response: Preparing for and responding to cybersecurity breaches.
- Vulnerability Management: Monitoring and remediating device vulnerabilities.
Who should attend medical device security training?
- IT Professionals: Focused on securing healthcare networks and devices.
- Clinical Engineers: Responsible for maintaining and managing medical devices.
- Product Developers: Involved in designing and developing secure medical devices.
- Regulatory and Compliance Teams: Ensuring adherence to HIPAA, FDA, and other standards.
- Healthcare Administrators: Overseeing cybersecurity strategies and risk management.
What certifications or standards are addressed in these training programs?
- IEC 81001-5-1: Security activities in the product lifecycle for health IT systems.
- UL 2900: Cybersecurity standards for network-connectable healthcare products.
- ISO 27001: Information security management systems.
- HIPAA and FDA Compliance: Ensuring data protection and regulatory adherence.
How can organizations choose the right training provider?
- Course Content: Ensure the program covers relevant topics like risk management, compliance, and secure design.
- Industry Relevance: Look for providers with experience in healthcare and medical device security.
- Certifications Offered: Check if the program aligns with recognized standards like UL 2900 or IEC 81001-5-1.
- Flexibility: Consider online or in-person options based on organizational needs.


