How to Train Staff for Medical Device Security
Post Summary
Staff training is critical to prevent cyberattacks, protect patient data, and ensure compliance with regulatory requirements like FDA guidelines.
Training should include recognizing suspicious activities, proper device handling, incident reporting, and cybersecurity best practices.
By becoming a "human firewall," staff can identify threats, follow security protocols, and report vulnerabilities to IT teams.
Challenges include lack of awareness, resistance to change, and the complexity of integrating security protocols into daily workflows.
Best practices include regular training sessions, hands-on exercises, clear documentation, and fostering a culture of security awareness.
Organizations can sustain awareness by conducting regular refresher courses, rewarding compliance, and integrating security into everyday operations.
Medical device security is no longer just an IT issue - it directly impacts patient safety. Cyberattacks like ransomware can disrupt critical care systems, compromise patient data, and even endanger lives. The key to preventing these risks? Training your staff to recognize and mitigate security threats.
Key Takeaways:
- Human error is a major risk factor: Weak passwords, phishing, and mishandling devices are common vulnerabilities.
- Role-specific training is essential: Clinicians, IT teams, and biomedical staff each need tailored guidance.
- Federal regulations require action: Programs must align with HIPAA and FDA guidelines.
- Data-driven strategies work best: Use risk assessments to prioritize training based on device vulnerabilities.
Training programs should combine general awareness with specialized modules, covering phishing, secure device use, and incident reporting. Regular refreshers, scenario-based exercises, and tools like Censinet RiskOps™ can help keep your team prepared for evolving threats.
The goal? Equip every team member with the knowledge to protect devices, data, and most importantly, patients.
Identifying Staff Roles and Security Responsibilities
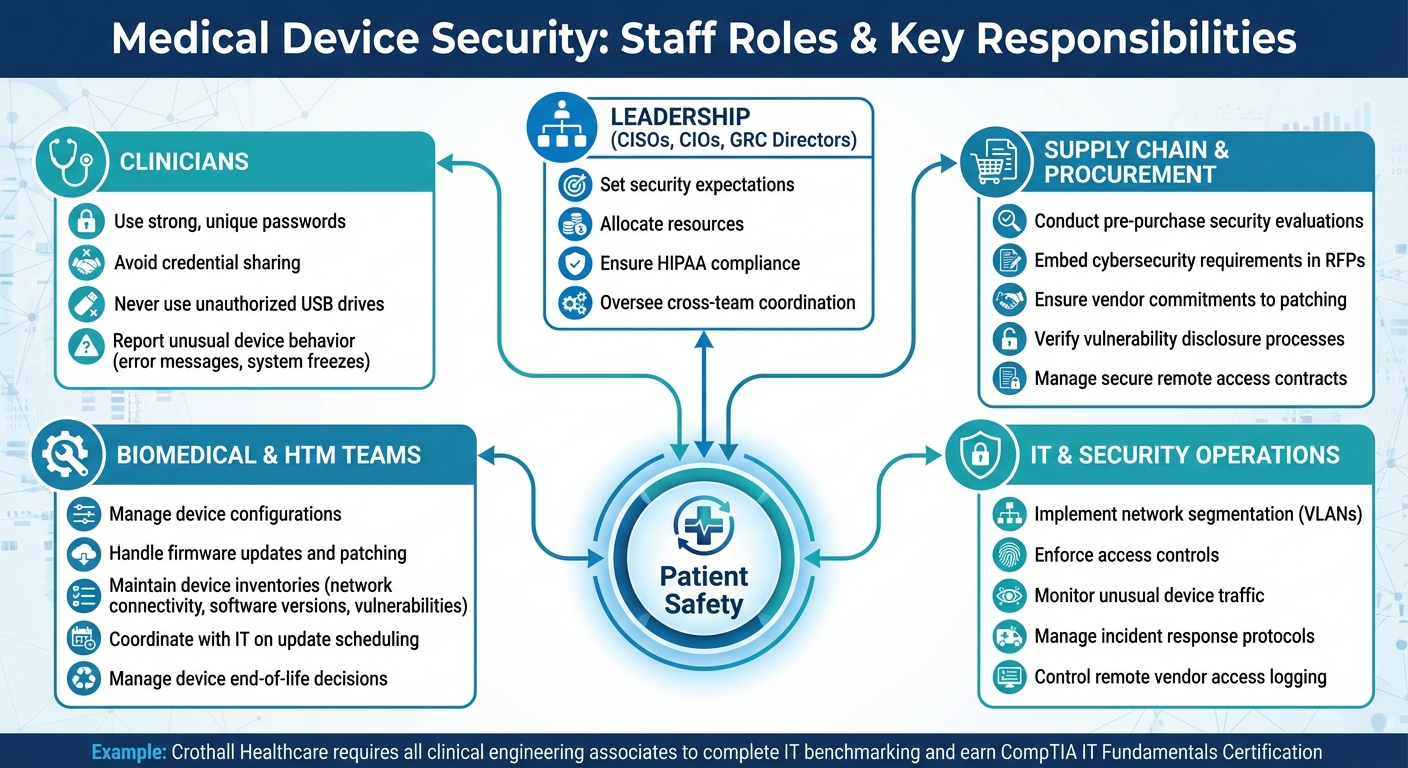
Medical Device Security Staff Roles and Responsibilities
Staff Roles in Medical Device Security
Ensuring the security of medical devices requires collaboration across various staff groups, each with specific responsibilities. Clinicians, who interact with these devices daily, play a key role in maintaining secure practices. They’re tasked with using strong, unique passwords, avoiding credential sharing, steering clear of unauthorized USB drives, and reporting any unusual device behavior - like unexpected error messages or system freezes. Even a single misstep in these protocols can open the door to potential attacks.
Biomedical and health technology management (HTM) teams act as the critical link between vendors and IT departments. Their duties include managing device configurations, firmware updates, and patching, as well as making decisions regarding device end-of-life. These teams maintain detailed inventories that track network connectivity, software versions, and known vulnerabilities. They also work closely with IT to schedule updates in ways that minimize disruptions to patient care. For instance, Crothall Healthcare mandates that every clinical engineering associate complete an IT benchmarking assessment and earn the CompTIA IT Fundamentals Certification as part of its medical device cybersecurity program [2].
IT and security operations teams focus on the broader infrastructure, implementing measures like network segmentation, access controls, and incident response protocols. They design VLANs to isolate medical devices from general networks, enforce logging and authentication for remote vendor access, and monitor for unusual traffic - especially from devices like imaging systems. Meanwhile, supply chain and procurement teams handle pre-purchase security evaluations, embedding cybersecurity requirements into RFPs and contracts. This ensures vendors commit to timely patching, vulnerability disclosures, and secure remote access. Leadership roles, including CISOs, CIOs, and GRC directors, oversee these efforts by setting expectations, allocating resources, and aligning practices with HIPAA and other U.S. regulations.
By clearly defining these roles, it becomes easier to understand how tailored threats can target specific groups.
Cybersecurity Threats Targeting Medical Devices
Medical devices in the U.S. healthcare system face numerous cybersecurity threats. Ransomware attacks, for example, can lock devices, disrupt critical systems like imaging equipment, and corrupt clinical data. In such cases, clinicians must quickly identify compromised systems, activate downtime protocols, and switch to backup devices. HTM teams need to assess whether devices have lost network connectivity or have been locally compromised, while IT teams work to isolate affected network segments to contain the threat.
Other challenges include unpatched vulnerabilities and outdated firmware, which can expose devices to remote exploitation, as well as insecure remote access - such as vendor accounts lacking multi-factor authentication or proper logging.
Training programs should tie these threats directly to specific staff actions. For clinicians, this involves recognizing the dangers of clicking suspicious links. HTM teams need to understand secure remote access procedures and know how to handle situations where patches aren’t immediately available. IT teams, on the other hand, must focus on monitoring device traffic and responding to anomalies effectively.
Using Risk Assessments to Guide Training
Risk assessments are essential for translating threats into targeted training for each staff role. These assessments evaluate factors like a device’s importance to patient care, its network exposure, known vulnerabilities, and whether it can be patched. A detailed asset inventory - covering device type, location, software versions, connectivity, and vendor support - helps rank risks. Devices like older networked imaging systems, infusion pumps, and life-support equipment often fall into high-risk categories.
Training should align with these risk profiles. For example, HTM teams might receive in-depth training on securing high-risk devices, while IT teams focus on protecting the networks and protocols tied to them. Tools like Censinet RiskOps™ centralize risk data across clinical applications, medical devices, PHI, and supply chains, helping organizations prioritize training and controls for the most vulnerable vendors and technologies.
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." – Matt Christensen, Sr. Director GRC, Intermountain Health
Risk platforms also provide valuable insights, such as vulnerability severity scores that pinpoint which systems need immediate attention. Reviewing device-level incident histories - like previous malware infections or repeated security breaches - can highlight areas where front-line staff might benefit from refresher training. Additionally, vendor risk ratings that flag issues like delayed patching or weak remote access controls can guide procurement decisions and vendor-access training for supply chain and IT teams.
Creating Role-Based Training Programs
Finding Knowledge Gaps and Training Needs
Start by evaluating your staff's current cybersecurity knowledge to identify weaknesses. Use targeted surveys to measure awareness across different departments. Include role-specific questions, like "How do you report suspicious behavior in medical devices?" or provide phishing examples to test recognition skills. Online tools can automatically score these responses and sort results by department and role, often uncovering areas like low phishing awareness among outpatient clinicians.
Structured interviews and focus groups can also shine a light on recurring security workarounds, such as shared logins or unauthorized USB use. Additionally, reviewing incidents and near-misses offers valuable insights. Analyzing past security events, help-desk tickets, and near-miss reports related to device malfunctions, unauthorized access, or phishing attempts can reveal patterns - like repeated clicks on vendor-themed phishing emails or delays in patching due to unclear responsibilities.
To organize these findings, create a gap-analysis matrix sorted by role. This tool compares the behaviors required for secure practices with the current skill levels of your staff. It serves as the groundwork for building training programs that address actual weaknesses rather than generic topics. These insights pave the way for both universal and specialized training, which are discussed next.
Building Core and Specialized Training Modules
Use the identified gaps to create training modules tailored to both general and role-specific needs. Start with a core curriculum that all staff members complete, regardless of their role. This universal training should be brief - 15 to 30 minutes annually, delivered in 5- to 10-minute micro-lessons that fit seamlessly into busy schedules. Core topics should include:
- Recognizing phishing and social engineering, using healthcare-specific examples like fake device recall notices or vendor update requests.
- Password management and multi-factor authentication.
- HIPAA basics and safe handling of protected health information.
- Essential device security practices, such as locking workstations and avoiding unauthorized USBs.
- Incident reporting procedures.
For more specialized training, create modules that go deeper into the technical needs and workflows of specific groups. For example:
- Clinicians: Training on secure use of devices like patient monitors, smart pumps, or imaging consoles, and recognizing unusual device behavior that may signal cybersecurity issues.
- Biomedical and Clinical Engineering Teams: Focus on device hardening checklists, patching processes, maintaining accurate device inventories, and collaborating with IT on network segmentation and incident response.
- IT and Security Staff: Training on medical device-specific challenges, such as long lifecycles, FDA-regulated changes, and patient safety concerns. Topics may include designing VLANs, monitoring device traffic, and creating incident response playbooks.
- Supply Chain and Procurement Teams: Training on incorporating cybersecurity requirements into RFPs and contracts, evaluating vendors with third-party risk assessments, and conducting pre-purchase security evaluations.
These specialized modules often run 30 to 60 minutes per quarter for higher-risk groups and can include hands-on labs when possible. Incorporating organizational case studies and real device examples makes the training more relatable and practical.
Using Industry Resources and Guidelines
To ensure compliance and demonstrate due diligence, align your training programs with industry standards. Free resources like the HHS 405(d) program offer healthcare-specific cybersecurity training modules and technical volumes aligned with HIPAA Security Rule requirements. Similarly, the Office of the National Coordinator for Health IT (ONC) provides guidance on securing health information exchanges and clinical systems.
Customize HHS 405(d) modules to reflect your organization's device inventory and risk priorities. Benchmarking your training program against these standards not only ensures compliance but also strengthens your case for securing necessary resources. As Brian Sterud, CIO at Faith Regional Health, explains:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."
Platforms like Censinet RiskOps™ can also be used to benchmark cybersecurity data and prioritize training topics. This data-driven approach ensures your efforts focus on areas with the highest risk and potential for improvement.
Embedding Training in Device Deployment and Daily Operations
Onboarding and Just-in-Time Training
Before devices are deployed, all relevant staff should complete a concise, role-specific onboarding session. This training covers essentials like verifying device inventory, ensuring baseline configurations are in place, and practicing secure login procedures. Staff also learn to confirm that clinical workflows and security settings align with the organization's standards and how to document acceptance with proper sign-off.
To make this seamless, integrate onboarding into the go-live checklist and change-management processes. This ensures that clinical validation and security protocols are reinforced right from the start. Using short multimedia tools - like videos or infographics - can help embed these practices effectively.
Just-in-time training focuses on delivering security guidance exactly when it's needed. Quick-reference tools, such as laminated cards or QR codes linking to short videos, can be attached to or placed near devices. These resources can cover topics like secure login and logoff procedures or handling alarms. Additionally, context-aware prompts on devices or within the EHR can serve as reminders, such as a brief notification when accessing remote viewing or exporting data for the first time. For new device types, trigger microlearning modules in your learning management system, and conduct brief team huddles or live demos when introducing new models or software updates. Training should also teach staff how to identify unusual device behavior, what actions to avoid, and the exact steps to report issues to clinical engineering or security teams.
Standard Operating Procedures for Device Security
After onboarding, secure device operations should be formalized through clear, well-defined standard operating procedures (SOPs). These SOPs should cover:
- Configuration changes: Define who is authorized to modify network, wireless, or user-access settings and outline the process for requesting, testing, documenting, and rolling back changes.
- Account management and physical security: Specify how accounts are created, updated, and terminated for clinicians, vendors, and temporary staff. Include details on session timeouts, restrictions on shared accounts, and rules for devices leaving the facility.
- Data handling and incident escalation: Explain how to store, export, and wipe protected health information (PHI), encryption requirements, and the steps to follow if staff encounter error messages, unexpected reboots, ransomware banners, or any abnormal device behavior that could impact patient safety.
- Vendor remote access: Require strict authentication, documentation, and use of approved access gateways.
Training should use real-world scenarios to connect these SOPs to daily operations. For instance, a nurse noticing repeated Wi-Fi disconnections on a device should know exactly which SOP steps to follow.
When it comes to configuration changes, SOPs should outline the roles authorized to request changes, the intake process (using a standard ticket template with fields for device ID, location, and security impact), and the need for security reviews before approval. Testing changes in a non-production environment, where possible, and securing approval from a multidisciplinary committee for higher-risk changes are also essential. Staff training should emphasize avoiding unsanctioned "quick fixes" that could create vulnerabilities.
Vendor remote access protocols should enforce strong multi-factor authentication, apply time-limited session controls, log all changes, and clearly define emergency access procedures. Staff must be trained to recognize and escalate situations where vendors attempt to bypass these established processes.
When manufacturers issue alerts - such as vulnerability notices or cybersecurity warnings - staff should know how to identify these communications, which internal teams handle them, and the steps for assessing risks. They should also understand how this information is shared with frontline staff and what specific actions they need to take, such as avoiding USB ports on certain devices until updates are applied.
Using Risk Data to Target Training
Incorporating real-time risk data can significantly enhance the ongoing training cycle. Tools like Censinet RiskOps™ can flag high-risk devices and automatically assign specialized training, such as additional modules for legacy imaging systems. Microlearning can also be triggered when new risks or compensating controls are identified. For example, if a particular device model has recurring issues, training can focus on addressing common problems like insecure default settings or frequent remote-access requirements.
Training administrators can link learning management systems to risk scores, ensuring that when risk levels change - such as after a major vulnerability disclosure - relevant users receive targeted, role-specific training instead of generic updates. Indicators to monitor include an increase in device-related security incidents, trends in vulnerabilities (e.g., CVEs affecting devices), audit results highlighting control gaps, and user behavior data, such as ignoring security prompts. By combining these insights with vendor and device risk scores, organizations can prioritize training for specific roles and units. For instance, staff working with imaging systems prone to malware alerts might need a refresher on safely handling removable media. This approach ensures training remains focused and impactful.
sbb-itb-535baee
Measuring and Improving Training Effectiveness
Setting a Training Schedule
Cybersecurity training works best when it's consistent and tailored. Begin with core training during onboarding, followed by quarterly microlearning refreshers, and annual updates that address new vulnerabilities and regulatory shifts. Keep quarterly sessions short - 10 to 15 minutes - and focus on critical topics like phishing strategies or secure handling of portable devices. Timing these sessions during less busy periods can help minimize interruptions.
Annual training should be customized based on roles. For example, clinicians benefit from workflow-specific training, such as securely using infusion pumps or managing alarm protocols during cyber incidents. On the other hand, HTM/biomed teams need technical sessions covering device hardening, patching, and network segmentation. IT and security staff require advanced training in threat detection and incident response, which could include joint exercises with clinical teams. High-risk areas, like ICUs and operating rooms, may need additional briefings when new vulnerabilities arise [3][6][7].
Testing Training Outcomes
Evaluating the effectiveness of training is crucial, and scenario-based methods are a great way to do this. Quizzes and simulations can test how staff respond to unusual device behavior or whether they know how to escalate and document suspected tampering. For technical teams, simulated exercises - like patching decisions, isolating networks, and managing incident communication - offer valuable insights into their readiness.
Phishing simulations tailored to healthcare scenarios are another powerful tool. For instance, fake emails mimicking device vendor communications, EHR upgrade notifications, or FDA alerts can test how staff handle real-world threats. Metrics like click rates, reporting rates, and time-to-report can highlight gaps in awareness across different roles and departments. Additionally, drills simulating system downtime (e.g., using paper orders when digital systems fail) can test how well teams maintain care during cyber events. Post-drill reviews are essential to ensure lessons learned are integrated into future training [4][7].
Tracking Metrics and Refining Programs
To keep training effective, it’s important to monitor key metrics like completion rates, phishing simulation outcomes, incident reports, and drill response times. High-risk areas - such as ICUs, operating rooms, and biomedical engineering - should aim for near-perfect compliance. Phishing click rates can reveal whether the training content or frequency needs adjustments, while tracking incident reports and drill performance can help refine both training materials and standard operating procedures.
Some organizations have successfully automated phishing exercises and triage, cutting the workload for threat analysts by up to 50% [4]. Tools like Censinet RiskOps™ can further streamline this process by linking training data with risk assessments. This approach not only strengthens the overall security strategy but also provides data-driven insights for leadership, making it easier to target training efforts where they’re needed most [3][4].
Conclusion
Ensuring medical device security is a continuous effort directly tied to patient safety. The FDA highlights that both device manufacturers and healthcare delivery organizations share the responsibility of addressing cybersecurity risks, as these threats can affect device performance and, ultimately, patient outcomes [7]. For instance, ransomware attacks on infusion pumps or imaging systems don’t just result in data breaches - they can delay or compromise critical patient care [3][7].
To make training effective, it’s essential to adopt role-specific strategies tailored for clinicians, biomedical engineers, IT staff, and emergency response teams. Start with thorough onboarding to establish a foundation, then reinforce it with quarterly refreshers and realistic simulations. These simulations should mimic actual incidents to prepare staff for potential challenges. By embedding security practices into everyday workflows and standard operating procedures, secure device handling becomes second nature [2][7].
Using tools like Censinet RiskOps™ and conducting targeted risk assessments can refine training efforts. This approach pinpoints vulnerabilities in devices, third-party risks, and broader enterprise-level threats, ensuring that training focuses on the areas of highest concern [5]. Shifting from generic awareness to precise, actionable strategies makes the training more impactful and relevant.
Leadership plays a crucial role in weaving cybersecurity training into the fabric of clinical quality. As Matt Christensen from Intermountain Health points out, healthcare requires tools and practices tailored to its unique complexities [1]. Treating medical device cybersecurity as an integral part of clinical quality - not just an IT issue - helps protect patients and strengthens organizational resilience. This creates a culture where every team member recognizes their role in safeguarding patients from digital threats.
FAQs
How does human error impact the security of medical devices?
Human mistakes significantly contribute to security risks in medical devices. Errors such as incorrect device configuration, improper handling, or failing to address vulnerabilities can result in breaches or even device malfunctions.
To minimize these risks, thorough staff training is essential. Educating healthcare workers on correct setup, usage, and security procedures helps create a safer and more secure environment for medical device operations.
How do risk assessments enhance medical device security training?
Risk assessments are essential for enhancing medical device security training. They help pinpoint specific vulnerabilities and potential threats within an organization, offering a clear picture of where the greatest risks lie.
With this information, training programs can be customized to address these critical security concerns directly. This means healthcare staff can develop a stronger grasp of device security protocols and practical best practices. Such focused training not only boosts staff readiness but also plays a key role in protecting patient data and staying aligned with regulatory requirements.
Why is tailored training essential for securing medical devices?
Tailored training programs are essential for helping healthcare staff grasp their unique responsibilities in safeguarding medical devices. By concentrating on the specific duties tied to each role, these programs minimize risks, enhance compliance, and ensure that staff can manage devices securely based on their assigned tasks and access levels.
This targeted approach not only bolsters the overall security measures but also plays a critical role in preventing mistakes and vulnerabilities that might jeopardize patient safety or compromise sensitive data.
Related Blog Posts
Key Points:
Why is staff training important for medical device security?
Importance:
- Staff training is essential to prevent cyberattacks that could compromise patient safety and data privacy.
- It ensures compliance with regulatory requirements, such as FDA guidelines, which emphasize the need for cybersecurity throughout a device's lifecycle.
- Proper training empowers staff to recognize and respond to potential threats, reducing the risk of breaches.
What are the key components of medical device security training?
Key Components:
- Recognizing Suspicious Activities: Staff should be trained to identify unusual device behavior or unauthorized access attempts.
- Proper Device Handling: Training should cover secure usage, storage, and maintenance of medical devices.
- Incident Reporting: Employees must know how to report vulnerabilities or breaches promptly.
- Cybersecurity Best Practices: This includes password management, multi-factor authentication, and secure network usage.
How can staff help reduce cybersecurity risks for medical devices?
Reducing Risks:
- Staff act as a "human firewall" by following security protocols and identifying potential threats.
- They can prevent unauthorized access by adhering to proper device handling and reporting suspicious activities.
- Regular training ensures that staff remain vigilant and up-to-date on the latest cybersecurity threats.
What challenges exist in training staff for medical device security?
Challenges:
- Lack of Awareness: Many staff members may not fully understand the cybersecurity risks associated with medical devices.
- Resistance to Change: Employees may be hesitant to adopt new security protocols or technologies.
- Complexity of Integration: Incorporating security measures into daily workflows can be challenging without clear guidance and support.
What are the best practices for training staff on medical device security?
Best Practices:
- Conduct regular training sessions to keep staff informed about evolving threats.
- Use hands-on exercises to simulate real-world scenarios and improve preparedness.
- Provide clear documentation of security protocols and device usage guidelines.
- Foster a culture of security awareness by emphasizing the importance of cybersecurity in protecting patient safety.
How can healthcare organizations sustain a culture of cybersecurity awareness?
Sustaining Awareness:
- Conduct refresher courses to reinforce training and address new threats.
- Reward compliance and recognize staff who demonstrate strong cybersecurity practices.
- Integrate security into everyday operations, making it a core part of the organizational culture.


