Ultimate Guide to Continuous Vulnerability Scanning in Healthcare
Post Summary
Continuous vulnerability scanning is a must-have for healthcare organizations. Why? It keeps your systems safe from cyber threats, protects sensitive patient data, and ensures compliance with regulations like HIPAA. Unlike outdated annual checks, this approach uses automation to monitor and address vulnerabilities in real-time, reducing risks in environments filled with legacy systems, medical devices, and cloud services.
Here’s what you need to know:
- Why It’s Important: Healthcare is a top target for cyberattacks, with protected health information (PHI) and medical devices at risk. Continuous scanning closes security gaps left by periodic testing.
- Regulations: By 2025, HIPAA will require vulnerability scans every six months and annual penetration tests, making continuous scanning a compliance necessity.
- How It Works: It involves asset discovery, regular scans, risk prioritization, remediation, and validation. Tools like Censinet RiskOps™ simplify the process.
- Best Practices: Maintain an updated asset inventory, set clear Service Level Agreements (SLAs), and use non-disruptive scanning methods for critical medical devices.
This proactive approach ensures patient safety, operational continuity, and regulatory compliance while giving healthcare organizations the tools to manage risks effectively.
Regulatory and Risk Requirements for Continuous Scanning
Meeting HIPAA, NIST CSF, and HHS Requirements
The HIPAA Security Rule emphasizes the need for regular risk analysis and management to safeguard electronic protected health information (ePHI). Specifically, §164.308(a)(1)(ii)(A) mandates covered entities and business associates to conduct risk analyses to identify potential threats to ePHI. Meanwhile, §164.308(a)(1)(ii)(B) requires implementing risk management strategies to mitigate those risks to an acceptable level. Vulnerability scanning, coupled with timely remediation, plays a critical role in meeting these obligations [8].
By 2025, healthcare organizations will need to conduct vulnerability scans at least every six months, along with annual (or more frequent) penetration tests as dictated by their risk assessments [4].
The NIST Cybersecurity Framework (CSF) offers additional guidance for continuous scanning programs. The Identify function, particularly ID.RA (Risk Assessment), relies on updated vulnerability data for informed risk assessments and asset prioritization. The Protect function, which includes PR.IP and PR.MA, ensures that patching and configuration management are effective and timely [10]. Both the Department of Health and Human Services (HHS) and the FBI have warned that unpatched vulnerabilities in internet-facing systems and outdated medical technology are among the primary entry points for healthcare breaches. This underscores the importance of continuous monitoring and rapid response [11].
| Regulatory Area | Core Expectation | How Continuous Scanning Supports It |
|---|---|---|
| HIPAA Security Rule – Risk Analysis & Risk Management (§164.308) | Ongoing risk identification and management for ePHI; document assessments and mitigation efforts | Continuously identifies vulnerabilities in ePHI systems, supports risk analysis, and tracks remediation and residual risks [4][8] |
| HIPAA Technical Safeguards (§164.312) | Implement technical protections for ePHI (e.g., access control, transmission security) | Detects unpatched systems, misconfigurations, and insecure services that could compromise safeguards [8] |
| NIST CSF – Identify (ID.RA) | Assess cybersecurity risks to operations and assets | Provides updated vulnerability data for risk assessments and asset prioritization [10] |
| NIST CSF – Protect (PR.IP, PR.MA) | Maintain effective security policies and procedures | Validates the effectiveness and timeliness of patching and configuration management [10] |
| HHS/OCR Enforcement Expectations | Ensure reasonable safeguards, including technical controls | Demonstrates due diligence through regular scans, timely fixes, and documented decisions [4][8] |
These regulatory frameworks outline the need for continuous scanning to address healthcare-specific risks effectively.
Healthcare-Specific Risk Factors
Healthcare environments face unique challenges that require tailored vulnerability management strategies. Many hospitals still rely on legacy systems that cannot be easily patched due to vendor limitations or clinical needs. These systems become high-risk targets if vulnerabilities are exploited [2][6]. Continuous scanning helps identify these risks, monitor exposure over time, and implement compensating controls - like network segmentation, access restrictions, or virtual patching - when direct patching isn’t feasible [2][7].
Connected medical devices bring another layer of complexity. Often running on proprietary or outdated systems, these devices require network-based scanning and specialized security measures to ensure patient safety [2][6]. Since device downtime can directly impact patient care, continuous monitoring enables informed decisions about maintenance schedules, compensating measures, and vendor escalation [6].
Third-party services, cloud platforms, and external integrations also demand ongoing oversight. Vulnerability scanning identifies misconfigurations and unpatched components, helping organizations maintain due diligence with their vendors [2][4]. Third-party breaches remain a leading cause of healthcare data incidents, and regulators increasingly expect organizations to actively monitor their vendors' security practices [4]. Regular scans of interfaces, VPN gateways, APIs, and other external assets reveal potential risks tied to third-party integrations [2][7]. When paired with tools like Censinet RiskOps™, scan data can enhance vendor risk assessments, contract negotiations, and ongoing monitoring of critical suppliers - providing essential evidence for managing business associate risks.
While identifying risks is crucial, documenting these efforts is equally important for compliance and audits.
Creating Audit Trails and Compliance Documentation
A strong continuous scanning program requires detailed documentation to meet HIPAA and other regulatory standards. Time-stamped logs should capture scan details such as the date, time, scope, engine, and initiator, along with reports that include CVE identifiers, severity ratings, and evidence of vulnerabilities [4][7]. Workflow records should show how findings are triaged, assigned, remediated, and verified, proving that vulnerabilities are actively managed rather than just logged [4][7].
Scan results should feed into a formal risk register that includes risk ratings, mitigation plans, residual risks, and acceptance decisions [4][8]. Organizations should also maintain version-controlled policies and procedures outlining scanning schedules, triggers for ad-hoc scans, exception handling, and escalation paths [7]. Modern compliance guidance often specifies documentation requirements, such as scope definitions, methodologies, timestamps, vulnerability classifications, remediation timelines, and evidence of fixes, along with approvals for risk acceptance [4].
Exportable reports showing trends - like average remediation times or the percentage of critical vulnerabilities resolved within service-level agreements (SLAs) - can demonstrate systematic vulnerability management [4][7][8]. Platforms like Censinet RiskOps™ centralize these results, correlating vulnerabilities with specific vendors and clinical applications. This approach prioritizes fixes based on patient safety and business impact, streamlining compliance reporting and providing the evidence needed for audits or Office for Civil Rights (OCR) investigations.
Core Components of a Continuous Vulnerability Scanning Program
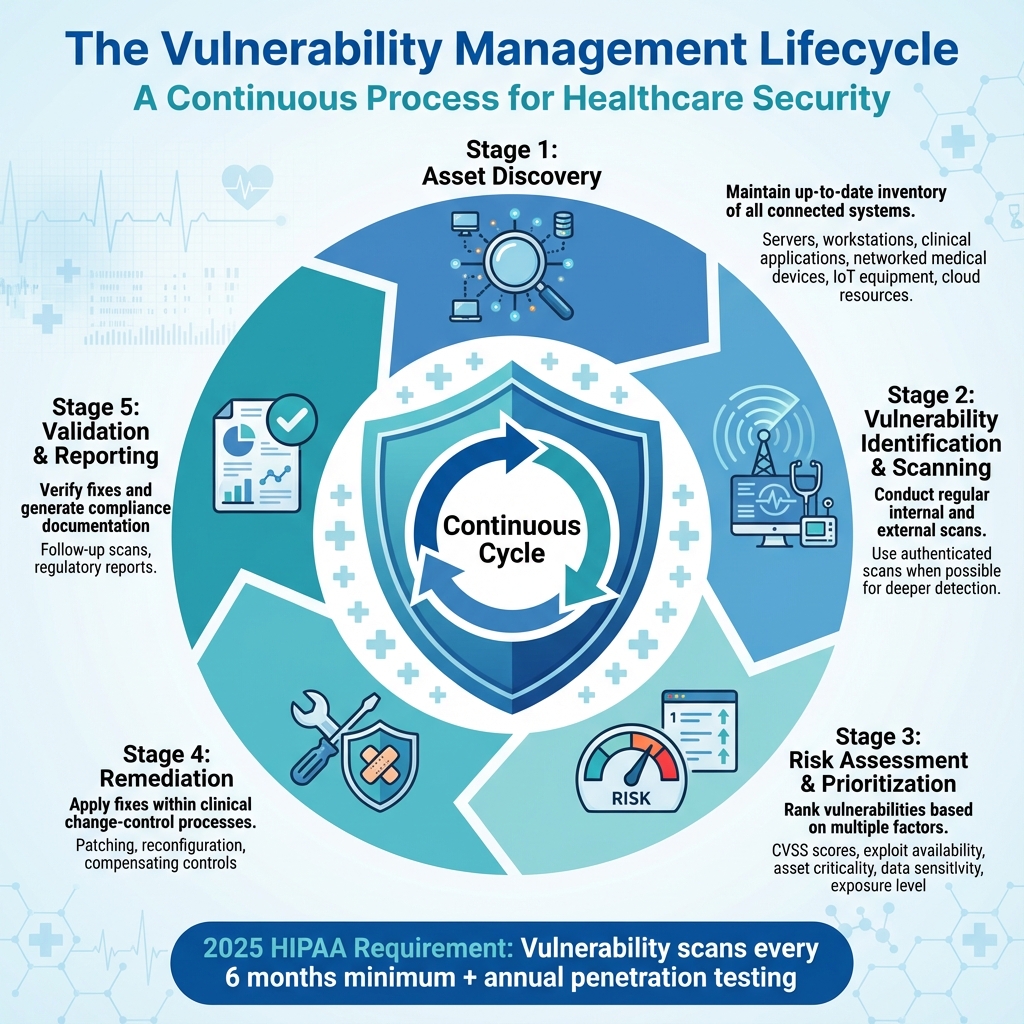
5-Stage Vulnerability Management Lifecycle for Healthcare Organizations
The Vulnerability Management Lifecycle
Continuous vulnerability scanning in healthcare operates through a structured, recurring process with five key stages: asset discovery, vulnerability identification and scanning, risk assessment and prioritization, remediation, and validation and reporting [14][15]. Each step seamlessly transitions into the next, creating a continuous loop of security oversight.
In the asset discovery phase, healthcare organizations maintain an up-to-date inventory of all connected systems - such as servers, workstations, clinical applications, networked medical devices, IoT equipment, and cloud resources [11]. During vulnerability identification, both internal and external scans are conducted on a regular schedule. Whenever possible, authenticated scans are used, as they can uncover vulnerabilities that require administrative credentials to detect [12].
Risk assessment and prioritization follows, where vulnerabilities are ranked based on factors like CVSS scores, exploit availability, the criticality of the affected asset (e.g., life-support systems versus office computers), data sensitivity, and exposure [14][15].
The remediation phase involves applying patches, reconfiguring systems, or implementing compensating controls, all within strict change-control processes tailored for clinical environments [11]. Finally, the validation and reporting stage ensures fixes are effective through follow-up scans and generates documentation to meet regulatory requirements. Recent updates to regulatory guidelines now call for more frequent scans to maintain constant security monitoring [4][13].
This cyclical process lays the groundwork for specific scanning techniques, which are covered in the next section.
Asset Discovery and Scanning Methods
A complete, continuously updated inventory of all assets is the cornerstone of effective vulnerability scanning in healthcare. Automated tools are essential for identifying all IP-connected devices, including shadow IT and unmanaged clinical systems, ensuring that no critical equipment is overlooked [11]. Once identified, assets should be categorized by type and importance [14][15].
From this inventory, scanning methods should be carefully tailored to the sensitivity and criticality of each asset. For highly sensitive medical devices, where even minor disruptions could impact patient care, passive scanning is the preferred method. Passive scanning monitors network traffic without directly interacting with devices, allowing it to identify outdated protocols, insecure configurations, and known vulnerabilities without causing interruptions [11].
On the other hand, active scanning directly probes systems for vulnerabilities. While more intrusive, it can be highly effective when tuned properly and scheduled thoughtfully - especially for medical devices and operational technology. To minimize disruptions, vendor-approved scan profiles designed for medical environments are recommended, and active scans should be conducted during maintenance windows.
For external-facing systems, HIPAA-aligned guidance suggests using qualified external vendors for scans, with scanner databases updated frequently to detect new vulnerabilities [8]. Internal scans should also be triggered after significant changes, such as new VLAN configurations, mergers, or major application rollouts. This ensures comprehensive coverage of all attack surfaces, including data centers, cloud environments, remote sites, third-party connections, and vendor-hosted applications that handle protected health information [8][10].
Using Automation and AI in Continuous Scanning
Automation and AI have transformed vulnerability scanning into a more scalable and efficient process. Automated systems handle tasks like scheduling, credential management, ticket generation, notifications, and retesting, significantly reducing the workload for security teams [5][14]. As Terry Grogan, CISO at Tower Health, noted:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required" [1].
AI takes this further by enhancing vulnerability management with advanced analytics. It can correlate findings across multiple scanners, eliminate duplicate issues, and prioritize vulnerabilities based on factors like exploitability and potential business impact [4][10]. AI tools also integrate threat intelligence, identifying vulnerabilities actively exploited in the wild, and can perform attack-path analysis to map how multiple vulnerabilities could be chained to compromise critical systems.
For healthcare organizations, AI-driven platforms like Censinet RiskOps™ streamline the process by integrating scan results into broader risk management workflows. These platforms connect vulnerabilities to specific vendors and clinical applications, helping teams focus on fixes that align with patient safety and organizational priorities [1].
How to Implement Continuous Vulnerability Scanning in Healthcare
Setting Up Governance and Ownership
Launching a continuous vulnerability scanning program in healthcare starts with establishing clear responsibilities and governance. Healthcare organizations should create a multidisciplinary team - think of it as a vulnerability management committee. This group should include members from IT security, network operations, clinical engineering, biomedical teams, compliance officers, and risk management. The team’s purpose and scope should be clearly defined in a formal charter. This charter should outline the program’s objectives, such as reducing risk and adhering to regulatory requirements, while covering all relevant areas: IT systems, operational technology, medical devices, cloud services, and third-party connections.
Each function within the program needs a designated owner. For example, specific individuals should oversee asset inventory, scanner configuration, triage, and medical device reviews. A CISO or Director of Information Security should lead the overall strategy, tool selection, and executive reporting. Compliance teams play a crucial role too - they ensure the program aligns with the HIPAA Security Rule, NIST Cybersecurity Framework, and HHS guidance. They must also maintain detailed, audit-ready documentation of scans, findings, and remediation efforts.
Once governance is in place, the next step is to design a scanning schedule that prioritizes high-risk assets.
Building a Risk-Based Scanning Framework
The scanning schedule should be tailored to how critical each asset is, how sensitive its data might be, and its exposure to threats. Start by classifying assets into tiers:
- Tier 1: High-risk assets like internet-facing systems, VPN gateways, electronic health records, and life-supporting medical devices.
- Tier 2: Internal applications handling protected health information (PHI) and non-critical medical devices.
- Tier 3: Low-risk internal IT assets that don’t handle PHI or affect clinical operations.
For Tier 1 assets, scans should be conducted daily or weekly. Tier 2 assets might need weekly or monthly scans, while Tier 3 assets can be scanned monthly or quarterly. The proposed 2025 HIPAA Security Rule suggests scanning at least every six months, with annual penetration testing - or more frequent testing based on risk assessments [4]. External scans by third-party experts and internal authenticated scans should both be part of the plan to catch configuration issues and patch gaps. Additionally, scans should be triggered by major system updates, network changes, or critical vulnerability disclosures.
Special care is required for medical devices and clinical systems. Work with clinical engineering teams to determine which devices can handle active scanning and which need passive monitoring or low-intensity scans during maintenance windows. For older or sensitive devices that can’t be scanned, document exceptions and apply compensating measures like network segmentation and strict access controls.
To simplify this process, platforms like Censinet RiskOps™ offer tools tailored to healthcare’s unique needs.
Using Censinet RiskOps™ for Scanning Programs
Managing continuous scanning in healthcare is no small task, but platforms like Censinet RiskOps™ make it more manageable. This AI-powered platform centralizes data from vulnerability scans, asset inventories, and third-party assessments, creating a streamlined solution designed specifically for healthcare organizations.
One of its key benefits is automation. The platform routes scan results to the right teams - whether IT security, clinical engineering, or compliance - based on the asset type and risk level. It also tracks remediation progress until validation, cutting down on manual tasks like managing spreadsheets. As Terry Grogan, CISO at Tower Health, explained:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required" [1].
Censinet RiskOps™ also helps prioritize vulnerabilities by linking them to specific vendors, clinical applications, medical devices, and supply chain components. This ensures that teams focus their efforts on the issues that matter most for patient safety and compliance. With built-in benchmarking tools, organizations can evaluate their vulnerability management maturity against industry standards and advocate for the resources they need. Plus, the platform provides audit-ready documentation and a comprehensive view of risk, making it easier to manage the entire vulnerability scanning lifecycle in healthcare settings.
sbb-itb-535baee
Best Practices for Continuous Vulnerability Scanning in Healthcare
Building on essential scanning methods and implementation strategies, these practices help maintain operational security and compliance in healthcare environments.
Keeping Asset Inventories and Risk SLAs Current
A reliable Configuration Management Database (CMDB) is critical for managing all assets - clinical and non-clinical alike. This includes servers, endpoints, medical devices, IoT sensors, cloud workloads, and third-party SaaS applications. Each entry in the CMDB should capture details like the asset owner, location, data sensitivity, and its role in business operations [2]. Use automated tools for device discovery and supplement them with manual reviews to spot shadow IT or unmanaged devices [2][6].
Integrate asset updates into daily workflows by making CMDB updates mandatory during procurement, onboarding, decommissioning, and change management processes [2][3]. Schedule quarterly reviews with teams from security, IT, and clinical engineering to ensure the database reflects current conditions. Continuous monitoring tools can also help by flagging new devices on the network or alerting teams when existing devices go offline [2][6].
Set Service Level Agreements (SLAs) that tie vulnerability severity to asset criticality and patient safety [2][7]. For example, critical systems might need fixes within 24–72 hours, while lower-risk assets can have a longer window of 7–14 days if compensating controls are in place [4][17]. Some medical devices, especially those that are hard to patch, may require interim measures like network segmentation or enhanced monitoring, followed by a longer SLA for vendor-coordinated updates [6]. Regularly track SLA performance and adjust timelines based on new threat intelligence, recent incidents, and operational needs [2][7].
Reducing Disruption to Healthcare Operations
In a 24/7 healthcare setting, scanning and patching require careful planning to avoid service interruptions. Work with clinical leadership to establish off-peak scanning windows [2][6]. Use non-invasive or credentialed scans that run continuously with minimal impact, and reserve more intensive scans for scheduled maintenance periods [5].
For high-risk or sensitive systems - like imaging devices, lab analyzers, or legacy equipment - test scan profiles in a controlled environment before rolling them out fully [6]. Adjust scan settings based on these tests to balance security needs with operational stability. Clear communication is key: notify department heads in advance, provide on-call support contacts, and establish escalation paths for handling unexpected issues [3][17].
Coordinate maintenance by clinical area or technology stack to minimize disruptions [2][7]. Use staged rollouts - starting with development and testing, followed by pilot deployments, and finally full implementation - to catch potential issues early and reduce the risk of widespread outages [16]. Automation tools that link vulnerability scanners with IT Service Management (ITSM) platforms can make routine updates more efficient, while still allowing manual oversight for critical systems [2][5].
Tracking and Reporting Program Performance
Once processes are in place, measuring their effectiveness is the next step. Key performance indicators (KPIs) to track include mean time to remediate (MTTR) by severity and asset type, the percentage of vulnerabilities addressed within SLA deadlines, and recurrence rates for previously resolved vulnerabilities [17][7]. Other metrics to monitor include the percentage of assets scanned regularly, high-risk assets scanned at least weekly, and the ratio of unknown to known assets discovered through scanning [2][5]. Pay close attention to exploitable internet-facing vulnerabilities, risks on systems containing ePHI, and unresolved critical issues that exceed defined thresholds [4][17].
Reports for executives should translate technical findings into business and patient safety terms. Highlight metrics like risks to systems containing ePHI, potential impacts on clinical operations, and how these align with regulatory frameworks such as HIPAA, NIST CSF, and HHS guidelines [3][4][17]. Dashboards and quarterly reports should focus on a concise set of KPIs - such as MTTR, SLA compliance, and critical vulnerabilities on high-value systems - while also including summaries of major initiatives, remaining risks, and resource gaps [17][7]. Use visualizations to make risk concentrations clear for non-technical stakeholders [3][16].
Platforms like Censinet RiskOps™ can provide high-level views of vulnerability and third-party risks, offer benchmarking against peers, and generate documentation for regulatory and insurance purposes. Brian Sterud, CIO of Faith Regional Health, emphasized:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters" [1].
Continuous improvement involves regular program reviews - quarterly and annually - that compare current performance against targets, NIST CSF maturity levels, and updated HIPAA or HHS guidelines [3][17]. Post-incident and post-change reviews can also reveal gaps, such as missed vulnerabilities, unrealistic SLAs, or communication breakdowns. Use these insights to refine scan configurations, processes, and training [2][9].
Conclusion and Key Takeaways
Why Continuous Scanning Matters
Continuous scanning plays a critical role in safeguarding electronic protected health information (ePHI), maintaining smooth clinical operations, and adhering to HIPAA and NIST standards. Federal guidance has shifted from one-time assessments to an ongoing approach to risk management, emphasizing the importance of continuous vigilance [4][10].
By identifying vulnerabilities in electronic health records (EHRs), connected medical devices, and clinical workflows before they can be exploited, continuous scanning directly enhances patient safety. This proactive approach helps mitigate ransomware risks that could disrupt essential treatments like surgeries, chemotherapy, or radiology services [2][6][17]. Additionally, it reduces downtime, ensures operational predictability, and provides key performance indicators (KPIs) to guide decisions on staffing, patch schedules, and capital investments [2][7][18]. Given that healthcare is one of the most targeted sectors for cyberattacks, continuous scanning is indispensable for managing cyber risks, ensuring business continuity, and protecting an organization’s reputation [4][10].
These advantages highlight the urgency for healthcare organizations to act swiftly.
Next Steps for Healthcare Organizations
Healthcare organizations can take the following steps to fully harness the benefits of continuous scanning:
- Designate an executive sponsor and establish a cross-functional team that includes IT, security, compliance, and clinical operations.
- Update asset inventories to include servers, applications, EHRs, medical devices, IoT devices, and cloud services that handle ePHI.
- Set risk-based scopes and remediation SLAs that align with your organization’s risk tolerance and regulatory obligations.
- Implement advanced scanning tools capable of performing authenticated scans, offering visibility into medical devices, and integrating with IT service management (ITSM) systems for frequent or continuous scanning.
- Develop clear workflows and documentation to define responsibilities for triage, ticket creation, and change control while aligning with clinical schedules. Ensure audit-ready evidence for HIPAA and NIST compliance.
- Start with a pilot program - targeting a specific data center segment or critical applications - refine the processes, and then scale across the organization.
- Monitor key metrics such as the number of unresolved critical vulnerabilities, mean time to remediate (MTTR), and SLA compliance. Regularly report these metrics to leadership to drive ongoing improvements.
Healthcare-focused platforms like Censinet RiskOps™ can simplify this process by consolidating vulnerability data, streamlining governance and reporting, and generating audit-ready documentation [1]. As Brian Sterud, CIO of Faith Regional Health, explains:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters" [1].
FAQs
How does continuous vulnerability scanning help protect patients in healthcare?
Continuous vulnerability scanning plays a crucial role in protecting patients by spotting and addressing security weaknesses before they can be exploited. This proactive approach helps reduce the chances of data breaches and system failures, allowing healthcare organizations to operate securely while keeping sensitive patient information safe.
It also ensures clinical workflows run smoothly, minimizing disruptions that could affect patient care. By staying one step ahead of ever-changing cyber threats, healthcare providers create a more secure environment for both patients and their data.
What is the difference between passive and active vulnerability scanning?
Passive vulnerability scanning operates by monitoring and analyzing network traffic or system behavior without making direct contact with the systems under observation. Instead of sending probes or tests, it identifies vulnerabilities by examining existing data and activity patterns within the network.
In contrast, active vulnerability scanning takes a more hands-on approach. It involves directly testing systems, applications, or networks to uncover potential weaknesses. This method actively interacts with devices, running scans and probes to detect vulnerabilities in a more thorough manner.
Each method offers distinct advantages, and using both together can provide a more rounded understanding of security risks, especially in sensitive environments like healthcare.
What’s the best way for healthcare organizations to address vulnerabilities in outdated systems and medical devices?
Healthcare organizations can tackle weaknesses in outdated systems and medical devices by implementing continuous vulnerability scanning designed specifically for healthcare settings. Tools like Censinet RiskOps™ provide real-time risk analysis, proactive threat monitoring, and efficient management of potential security issues.
With this strategy, older systems and devices are consistently checked for vulnerabilities, ensuring sensitive patient information remains secure, compliance standards are met, and operational security is strengthened. Early detection and resolution of risks help protect critical systems and uphold trust in healthcare services.


