Ultimate Guide to HIPAA Audits
Post Summary
HIPAA audits are critical for healthcare organizations to ensure compliance with privacy, security, and breach notification rules. Managed by the Office for Civil Rights (OCR), these audits assess how entities protect patient data (PHI and ePHI). Noncompliance can result in fines, corrective action plans, and reputational damage.
Key points:
- Who is audited: Healthcare providers, health plans, clearinghouses, and business associates like IT vendors.
- What is evaluated: Privacy, Security, and Breach Notification rules, focusing on risk analysis, safeguards, and breach response.
- Audit types: Desk (document-based) and on-site (comprehensive).
- Preparation tips: Maintain updated policies, conduct risk analyses, train staff, and organize documentation in a centralized system.
- Common outcomes: Minor findings, corrective action plans, or penalties for severe noncompliance.
Staying prepared with robust compliance programs and regular internal audits can help organizations meet OCR's requirements and protect patient data.
How the OCR HIPAA Audit Program Works
The Office for Civil Rights (OCR), part of the U.S. Department of Health and Human Services, oversees the HIPAA Audit Program under the authority of the HITECH Act Section 13411. This section mandates periodic audits of covered entities and business associates to ensure compliance with HIPAA. The program began with a pilot phase in 2011–2012 and expanded into a larger Phase 2 audit program in 2016. The primary aim is to evaluate how organizations implement HIPAA standards, identify common compliance issues, and use these findings to provide guidance and encourage improvements across the healthcare industry. Below, we’ll dive into how OCR conducts these audits, what they focus on, and the potential outcomes.
OCR relies on a detailed audit protocol that breaks down the Privacy, Security, and Breach Notification Rules into specific standards and measurable steps. This framework allows auditors to systematically review an organization’s policies, procedures, risk analyses, training records, and technical safeguards to ensure they align with HIPAA requirements.
OCR Audit Methods and Procedures
OCR employs two main types of audits: desk audits and on-site audits.
- Desk audits are document-based reviews where OCR requests specific materials, such as policies, risk analyses, and training records. Organizations are typically required to submit these documents within 10 business days. Auditors then compare the submissions against the audit protocol and issue draft findings, giving organizations a chance to respond before finalizing the report.
- On-site audits are more comprehensive. OCR sends audit teams to an organization’s facilities to conduct interviews, review systems, observe physical safeguards, and assess how policies are applied in daily operations. These audits provide a deeper look into whether safeguards are not just documented but actively functioning.
Audit selection can happen through several channels. OCR often starts with a pre-audit screening questionnaire to gather details on an organization’s size, type, and operations. Publicly available information is also used to build the audit pool. Additionally, OCR may launch targeted reviews or investigations based on complaints, large breaches, patterns of noncompliance, or a failure to respond to information requests. These targeted reviews can resemble full audits and may lead to corrective actions or enforcement measures.
What OCR Examines During HIPAA Audits
OCR audits focus on several key compliance areas:
- Risk analysis and management: Organizations must conduct comprehensive risk assessments for electronic protected health information (ePHI), document identified risks, and implement strategies to mitigate them.
- Administrative safeguards: OCR reviews security management processes, the roles of designated security and privacy officers, workforce security measures, and sanction policies. Documentation such as charters and role descriptions is often examined.
- Technical safeguards: Auditors assess whether organizations have implemented measures like unique user IDs, role-based access, encryption, audit logs, and transmission security. Evidence such as system configurations and change-control records is reviewed.
- Physical safeguards: This includes evaluating facility access controls, workstation security, device management, and disposal procedures.
- Breach notification practices: OCR ensures entities have clear, written procedures that comply with HIPAA’s timing and content requirements. They also verify that incidents are assessed and reported within the required timeframes.
- Workforce training: Auditors review training materials, attendance records, and testing outcomes to confirm that employees receive both initial and ongoing HIPAA training tailored to their roles.
Possible Audit Results
Audit findings can vary widely, from minor observations to significant enforcement actions.
- Minor findings: Organizations may only need to make voluntary improvements.
- Deficiencies: When issues are identified, corrective actions are expected. Failure to address these can lead to further scrutiny.
- Serious noncompliance: OCR may require a formal Corrective Action Plan (CAP) or Resolution Agreement. These often include steps like updated risk analyses, revised policies, improved training, and ongoing reporting, sometimes with third-party monitoring over an extended period.
- Egregious violations: In cases of willful neglect, OCR can impose civil monetary penalties, which can reach into the millions of dollars. Even without penalties, findings may require significant remediation, strain budgets, and damage an organization’s reputation.
These outcomes highlight the importance of a strong compliance program, which will be explored further in the next section.
How to Prepare for a HIPAA Audit
The best time to prepare for a HIPAA audit is well before you receive any notification from the Office for Civil Rights (OCR). Staying on top of compliance not only reduces your audit risk but also ensures you're ready to respond effectively if the need arises. Preparation involves establishing a strong compliance program, organizing your documentation for quick access, and conducting internal audits to identify and address any weaknesses before OCR does.
Building a Compliance Program for Audit Readiness
A solid compliance program starts with clear accountability. HIPAA mandates that covered entities and business associates assign Privacy and Security Officers. In smaller organizations, one person may handle both roles, but their responsibilities must be well-defined and report directly to senior leadership.
In addition to these roles, forming a compliance committee can strengthen your program. This committee should include representatives from key areas like IT, security, legal, clinical operations, and HR. Regular meetings - ideally quarterly - should cover topics such as risk assessments, incident trends, remediation updates, and audit findings. These meetings' minutes can serve as evidence of active oversight during an audit.
At the core of audit readiness is a thorough, organization-wide risk analysis. According to HHS, failing to conduct a proper risk analysis is one of the most common HIPAA violations. Your analysis should include all systems that handle electronic Protected Health Information (ePHI) and examine threats like ransomware, lost devices, and unauthorized access. Assess vulnerabilities, estimate the likelihood and impact of risks, and document your findings. OCR will want to see both your current risk analysis and historical versions, especially after significant changes such as migrating to the cloud, replacing an EHR system, or undergoing a merger.
To complement your risk analysis, create a management plan that assigns responsibilities, outlines timelines, and tracks progress. Keep all documentation for at least six years, in line with HIPAA's retention requirements for policies, procedures, training records, and incident logs.
Another essential piece is a compliance inventory. This should include all assets and documentation relevant to HIPAA, such as systems and applications storing PHI/ePHI, medical devices, policies and procedures, risk analyses, training materials, incident logs, and Business Associate Agreements (BAAs). Whether you use a spreadsheet or a healthcare risk platform like Censinet RiskOps™, having a structured inventory ensures you can quickly locate evidence - often required within a 10-business-day timeframe for desk audits.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." – Terry Grogan, CISO, Tower Health
A well-built compliance program is only as effective as the documentation that supports it.
Organizing Audit Documentation
When OCR auditors request documents, delays in producing them can create the impression that you're unprepared or noncompliant. A centralized evidence library can solve this problem by securely storing all audit-relevant materials in an organized, searchable format, sorted by HIPAA control areas like Access Control, Training, Incident Response, and Risk Analysis.
For each area, maintain up-to-date and historical records, including policies, risk analyses, system inventories, training logs, and incident reports. Use role-based access controls to secure this repository, and log all changes to maintain an accurate version history.
HIPAA requires retaining documentation for six years, so it's essential to implement proper retention schedules. When records reach the end of their retention period, dispose of them securely, following HIPAA guidelines for PHI and ePHI disposal.
Templates and standardized workflows can streamline your audit preparation. Develop templates for key documents like risk analysis reports, corrective action plans, and incident reports. These templates ensure consistency and completeness when responding to OCR requests. Additionally, establish clear workflows for handling OCR notifications, triaging requests, locating evidence, and uploading files securely.
Platforms like Censinet RiskOps™ can centralize risk assessments, evidence, and corrective actions. By aligning assessments with HIPAA controls and generating reports tailored to OCR's typical inquiries, these tools can save time and help healthcare organizations demonstrate effective risk management practices.
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." – James Case, VP & CISO, Baptist Health
Running Internal HIPAA Audits
Internal HIPAA audits are your chance to uncover and address issues before OCR does. Conduct these audits at least annually, with more frequent reviews for high-risk areas like access control, log monitoring, and vendor management. Use a checklist aligned with HIPAA's Privacy, Security, and Breach Notification Rules to guide your scope. This should include areas like risk analysis, administrative and technical safeguards, privacy practices, breach response, and BAAs.
Assemble an audit team with members from IT, security, compliance, legal, and department leadership. If your team lacks expertise, consider bringing in an external HIPAA specialist. During the audit, review policies for alignment with HHS guidance, test technical safeguards (e.g., encryption, multi-factor authentication, and access controls), and sample access logs to ensure proper deprovisioning and appropriate access. Also, evaluate BAAs to confirm that your vendors meet HIPAA compliance requirements.
Document your findings in a corrective action plan that outlines issues, root causes, associated HIPAA requirements, and remediation steps with deadlines. Track progress and store all evidence in your central repository. Schedule follow-up audits to confirm that corrective actions have been implemented effectively. This proactive approach demonstrates a commitment to protecting patient information.
With HHS OCR's 2024–2025 audit phase set to review 50 entities for compliance with specific HIPAA Security Rule provisions, organizations that have robust compliance programs, organized documentation, and regular internal audits will be in a far better position to respond confidently and protect patient data effectively.
What to Expect During a HIPAA Audit
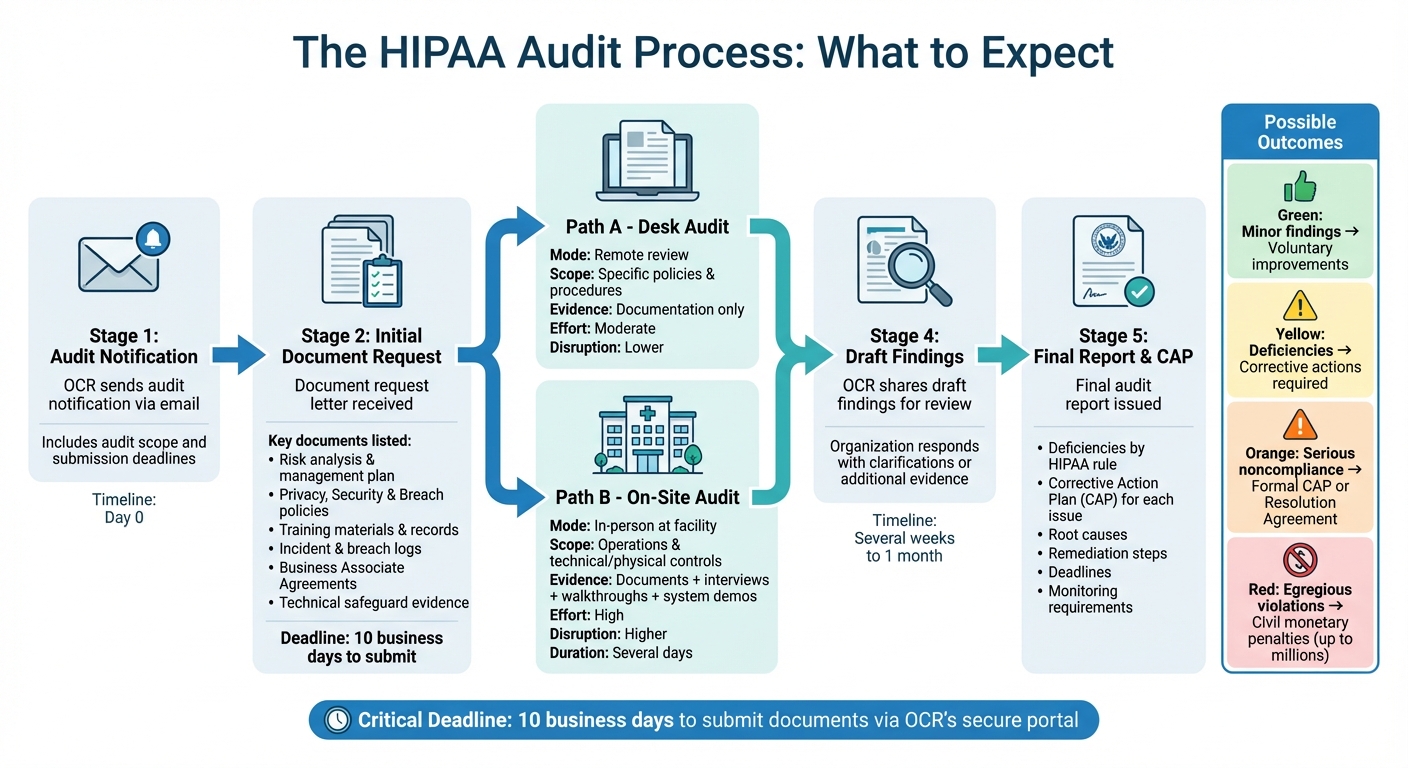
HIPAA Audit Process Timeline and Key Steps
When the Office for Civil Rights (OCR) selects your organization for a HIPAA audit, things move quickly. Understanding the process - from the initial notification to the final report - can help you stay on top of deadlines and requirements. Whether it’s a desk audit or an on-site visit, both follow a similar structure and require well-organized documentation. Let’s break down the key stages, types of audits, and how OCR communicates its findings.
Audit Notification and Initial Requests
OCR initiates the process by sending an audit notification via email to the contact information provided in your prior filings or pre-audit questionnaire. This letter lays out the audit’s purpose, scope, and submission deadlines. Alongside it, you’ll receive an initial document-request letter that specifies exactly what materials OCR needs to review. These typically include:
- Your most recent enterprise-wide risk analysis and risk management plan
- Written Privacy, Security, and Breach Notification policies and procedures
- Workforce training materials and attendance records
- Incident and breach logs, along with response documentation
- Business Associate Agreements
- Evidence of technical safeguards like encryption, access controls, audit logs, and contingency plans
OCR might also request details about your business associates and how you manage vendor risks. You’ll need to upload these documents to OCR’s secure portal within 10 business days - a tight timeline that underscores the importance of having a centralized repository for audit materials. This not only speeds up retrieval but also shows you’re prepared and capable of meeting deadlines.
Desk Audits vs. On-Site Audits
OCR conducts audits in two formats: desk audits and on-site audits, each with its own demands.
- Desk audits are conducted remotely and focus on reviewing the documentation you submit electronically. Auditors evaluate whether your written policies and risk analyses align with HIPAA standards for specific provisions. While desk audits don’t involve on-site inspections, they still require significant effort to gather and organize materials on a short timeline.
- On-site audits, on the other hand, involve OCR auditors visiting your facilities for several days. These audits are more comprehensive, as they assess how your policies are implemented in practice. Auditors may interview leadership (e.g., Privacy and Security Officers), frontline staff, and IT personnel to gauge their understanding of HIPAA requirements. They’ll also inspect physical safeguards like workstation security, access controls, and device disposal practices, and may request demonstrations of technical safeguards such as encryption and multi-factor authentication.
Here’s a quick comparison of the two formats:
| Aspect | Desk Audit | On-Site Audit |
|---|---|---|
| Interaction mode | Remote; documents submitted online | In person at your facility |
| Scope | Focused on specific policies and procedures | Broader, covering operations and technical/physical controls |
| Evidence reviewed | Documentation only | Documentation plus interviews, facility walkthroughs, and system demos |
| Effort required | Moderate | High, due to logistics and real-time evidence requirements |
| Disruption risk | Lower | Higher, as staff time and resources are required |
After reviewing your documentation, whether remotely or on-site, OCR finalizes its findings and outlines any necessary corrective actions.
Audit Findings and Required Corrective Actions
Once the audit is complete, OCR shares draft findings with you for review and comment. These findings can range from full compliance to minor areas for improvement - or even significant non-compliance with HIPAA standards, which may suggest willful neglect. Your response to the draft findings is critical; it’s your chance to clarify, provide additional evidence, or explain any discrepancies. OCR incorporates your feedback into the final audit report, a process that usually takes several weeks to a month.
The final report outlines any deficiencies, organized by HIPAA rule, and includes a corrective action plan (CAP) for each issue. A CAP details:
- The specific HIPAA requirement that was violated
- Root causes of the deficiency
- Steps to fix the issue
- Responsible parties
- Deadlines for completion
- Monitoring mechanisms to ensure ongoing compliance
For instance, if your risk analysis is incomplete, the CAP might require a comprehensive enterprise-wide risk analysis, a prioritized risk management plan, and regular progress updates to OCR. If workforce training is found lacking, the CAP could mandate a revised curriculum, annual training cycles, and evidence of completion rates.
OCR expects these plans to include clear milestones, supporting evidence (like updated policies or system configurations), and periodic status reports to confirm the effectiveness of your corrective actions. Tools like Censinet RiskOps™ can help you track CAP tasks, assign responsibilities, and generate compliance reports, making the process more manageable and transparent.
sbb-itb-535baee
Fixing Issues and Improving Compliance After an Audit
After completing an audit, the next step is addressing the identified issues and ensuring your organization stays compliant. Once the OCR delivers its final report, the focus shifts to fixing the problems uncovered. This isn’t just about quick fixes but about digging deep to resolve the root causes. Organizations that view corrective actions as a chance to enhance their entire HIPAA compliance program - rather than just patching things up - set themselves up for long-term success and readiness for future audits.
How to Address Audit Findings
Start by organizing the findings based on HIPAA rules - Privacy, Security, or Breach Notification - and their severity. Go over the report with key stakeholders to confirm the findings and prioritize the most urgent risks, such as unencrypted devices or unauthorized access. Before creating formal corrective action plans, address immediate threats to PHI by disabling problematic accounts, tightening access controls, or encrypting vulnerable devices.
Next, conduct a root cause analysis. A common method is the "5 Whys", which helps uncover deeper issues. For example, if laptops lack encryption, the real problem might stem from missing standard procedures for device setup and deployment checks. OCR expects covered entities to show that their risk analysis is thorough and that safeguards are regularly reviewed and updated, ensuring systemic issues are resolved rather than applying temporary fixes.
A strong Corrective Action Plan (CAP) should include specific actions for each finding, such as updating policies, implementing technical controls, or improving training. Each action should outline the risk level, regulatory requirements, a responsible party, milestones, and deadlines. Evidence of completion - like updated policies, system screenshots, training records, or test outcomes - is essential. For high-risk issues, it might also be necessary to update your risk analysis or revise incident response and breach notification procedures.
Here are some common deficiencies and suggested corrective actions:
| Deficiency Area | Typical Corrective Action | Evidence to Maintain |
|---|---|---|
| Incomplete risk analysis | Use a formal, organization-wide risk analysis system; inventory all systems with ePHI; assess risks; document mitigation plans; review annually | Risk analysis reports, risk registers, scoring methods, remediation logs |
| Weak access controls | Enforce role-based access, require unique user IDs and strong authentication, review access logs regularly, and remove access for departing staff promptly | Access baselines, change logs, access reviews, termination checklists |
| Inadequate workforce training | Require onboarding and annual HIPAA training, provide follow-ups after incidents, and test knowledge with quizzes or phishing simulations | Training rosters, quiz results, phishing metrics, training certificates |
| Poor documentation | Standardize and centralize policy templates, record all risk assessments and audits, and keep records for at least six years | Policy version histories, audit logs, document retention schedules, centralized repositories |
When prioritizing remediation, focus on high-impact issues like missing risk analyses, unencrypted devices, or weak incident response plans. Addressing these critical areas first is especially important when resources or time are limited.
Using Audit Results to Improve Risk Management
Once corrective actions are in place, integrate these updates into your broader risk management strategy. Incorporate audit findings into your enterprise risk management process by revising risk ratings, treatment plans, and safeguards. If certain issues - like vendor oversight gaps or repeated user errors - keep coming up, adjust governance practices, performance metrics, and internal audit plans to focus more on these high-risk areas. Tracking trends from audits alongside incident data can help confirm whether your changes are actually reducing risks or just improving documentation.
If audits uncover weaknesses in business associate agreements (BAAs) or vendor security practices, ensure your records are up-to-date. Maintain a complete list of business associates handling PHI, verify that each has a compliant BAA, and conduct standardized risk assessments for vendors. These assessments should focus on encryption, access controls, incident response, and subcontractor management. Periodically audit vendors to ensure they meet contractual and HIPAA requirements.
Redesigning your internal HIPAA audit program based on past findings can also help strengthen compliance. Use detailed audit checklists that go beyond policies to include operational practices and technical evidence, like logs and configurations. Current recommendations suggest conducting at least one documented risk assessment annually, with additional assessments for major changes, as well as regular vulnerability scans and penetration tests.
Using Censinet RiskOps™ for Ongoing Compliance

Managing corrective actions, vendor risks, and compliance efforts with spreadsheets or disconnected tools can quickly become overwhelming as an organization grows. Censinet RiskOps™ simplifies this process by centralizing risk assessments, corrective actions, policies, vendor evaluations, and audit evidence in one platform.
The tool helps map risks and controls to HIPAA requirements, offering dashboards to track remediation tasks, high-risk issues, and vendor-related risks. It fosters collaboration among compliance, security, privacy, and vendor management teams by keeping documentation and audit trails up-to-date, ensuring continuous readiness for audits.
Censinet RiskOps™ also includes cybersecurity benchmarking, allowing organizations to compare their HIPAA compliance efforts against industry standards and peers. This data-driven insight helps prioritize resources for compliance improvements effectively.
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." - Brian Sterud, CIO, Faith Regional Health
Conclusion
HIPAA audits aren't just for organizations that fall short on compliance - they can happen to any covered entity or business associate at any time. The Office for Civil Rights (OCR) has the authority to select any healthcare organization for a desk or on-site review, which means staying prepared is a must, not an option. The organizations that handle audits most effectively are those that treat HIPAA compliance as part of their daily operations. This consistent focus helps lay the groundwork for proactive measures that can make all the difference.
Early preparation can save time, money, and stress. Start with an annual documented risk analysis, keep your access and breach policies up to date, and ensure your workforce undergoes regular training. Running internal "mock audits" can be a game-changer, as they help you practice meeting OCR's typical 10-business-day deadline for documentation. Spotting and addressing gaps during these exercises is far better than discovering them during an actual audit. To keep your efforts sustainable, include HIPAA-related activities in your annual budget as recurring operational costs, rather than treating them as one-off projects.
A well-rounded compliance program should include formally appointed Privacy and Security Officers, documented safeguards, robust workforce training with attendance records, and a clear incident response plan. Centralizing your documentation - such as policies, risk assessments, audit reports, and logs - makes it much easier to provide evidence of compliance when OCR asks for it. Beyond audits, these practices also bolster patient data protection. For organizations juggling multiple vendors, centralized risk management tools can simplify third-party and enterprise risk assessments, enable ongoing monitoring of clinical applications and medical devices, and maintain organized evidence repositories.
Every audit - whether internal or from OCR - should contribute to a cycle of continuous improvement. Use audit findings to refine your security roadmap, update policies, enhance technologies, and improve training. Set a regular schedule, like quarterly reviews, to revisit previous findings, verify that corrective actions are effective, and adjust safeguards to address new threats. Keeping your documentation and safeguards current not only helps with audits but also reduces the risk of cyberattacks and data breaches, ultimately protecting your patients and strengthening your organization’s defenses.
To put this continuous improvement into action, start with these steps:
- Within 30 days: Confirm your Privacy and Security Officers are in place and centralize your policies and risk assessments.
- Within 60 days: Complete or update a documented risk analysis and launch workforce HIPAA training, ensuring attendance is tracked.
- Within 90 days: Conduct an internal desk review using an OCR-style document request list to test your readiness and identify any missing evidence.
While HIPAA audits require diligence, building steady compliance habits makes the process manageable. More importantly, it positions your organization for long-term success in meeting regulatory requirements and safeguarding patient data.
FAQs
What steps can healthcare organizations take to prepare for a HIPAA audit?
Healthcare organizations can gear up for a HIPAA audit by zeroing in on critical compliance areas. Begin with routine risk assessments to pinpoint and fix any weaknesses in your systems. Keep comprehensive documentation of all policies, procedures, and compliance-related activities, as auditors will scrutinize these records in detail.
Make sure every staff member is well-trained in HIPAA regulations and understands their responsibilities in safeguarding patient information. Regularly enhance your security protocols to address new and emerging threats. Using risk management tools can also help simplify compliance efforts and keep risks under control. Taking these proactive steps can ease the audit process and help maintain ongoing compliance.
What is the difference between desk audits and on-site audits in a HIPAA compliance review?
Desk audits are performed remotely and center around examining submitted documents to verify compliance. On the other hand, on-site audits require auditors to visit the organization in person. During these visits, they conduct interviews, inspect facilities, and carry out real-time evaluations. While both methods aim to determine how effectively an organization adheres to HIPAA requirements, on-site audits offer a deeper, more interactive review of day-to-day operations.
What should healthcare organizations do if a HIPAA audit uncovers compliance issues?
If a HIPAA audit uncovers compliance issues, taking swift and organized action is critical. Begin by tackling the specific problems identified and putting corrective measures in place. Make sure to document every step you take to resolve these issues, and if necessary, inform any affected individuals or entities. Conduct a root cause analysis to dig into the underlying reasons for the issues, and update your policies, procedures, and employee training accordingly to avoid repeating the same mistakes. To keep things on track moving forward, set up regular monitoring to maintain compliance and minimize the chance of future violations.


