Ultimate Guide to Medical Device Vulnerability Scoring
Post Summary
Medical devices are increasingly exposed to cybersecurity risks, with vulnerability disclosures rising from less than 1 per month (2013–2016) to over 4 per month (2016–2019). These vulnerabilities can have severe consequences, such as incorrect dosages from infusion pumps or leaked patient data. Traditional scoring systems like CVSS are widely used but often fail to reflect the unique risks in clinical settings. This article explores tailored frameworks, like the MITRE CVSS Rubric, which incorporate patient safety and clinical workflows into vulnerability assessments.
Key takeaways:
- CVSS Framework: Scores vulnerabilities on a scale of 0.0–10.0, focusing on severity but not exploitation likelihood.
- Limitations: Standard CVSS lacks healthcare-specific metrics like patient safety impacts or workflow disruptions.
- Specialized Solutions: The MITRE CVSS Rubric adds extended vectors for healthcare risks, such as diagnosis and therapy impacts.
- Automation: Tools like Censinet RiskOps™ streamline scoring, track vulnerabilities, and prioritize remediation with clinical context.
Scoring Security Vulnerabilities in Medical Devices: Rubric for CVSS
sbb-itb-535baee
The CVSS Framework Explained
The Common Vulnerability Scoring System (CVSS) is an open framework managed by the Forum of Incident Response and Security Teams (FIRST). It simplifies complex vulnerability details into a single score ranging from 0.0 to 10.0, where 10.0 represents the most serious risk [3]. Alongside this score is a "vector string", which outlines the specific metrics used in the calculation [7]. CVSS provides a shared language for cybersecurity professionals, manufacturers, and regulators to assess vulnerabilities.
Vulnerabilities are categorized by severity: None, Low (0.1–3.9), Medium (4.0–6.9), High (7.0–8.9), and Critical (9.0–10.0) [6]. Between October 2013 and March 2019, the average CVSS score for reported medical device vulnerabilities ranged between 6.87 and 7.30, placing them in the Medium to High severity range [1]. However, it's essential to note that CVSS focuses on severity, not the likelihood of exploitation in practical scenarios [4].
CVSS Components and Metrics
CVSS evaluates vulnerabilities using three metric groups: Base, Temporal, and Environmental [6].
- Base metrics address fixed characteristics of a vulnerability, such as how an attacker gains access (Attack Vector), the complexity of the attack (Attack Complexity), required privileges, user interaction, and the impact on Confidentiality, Integrity, and Availability.
- Temporal metrics account for factors that may evolve, like the availability of exploit code or patches.
- Environmental metrics allow organizations to adjust scores based on their specific operational context.
In November 2023, the FDA formally recognized CVSS v4.0, with a transition period for v3.1 lasting until July 4, 2027 [3]. Version 4.0 introduces new elements like "Attack Requirements" to refine "Attack Complexity" and separates "Impact" into two categories: one for the primary system and another for secondary systems [6]. These updates reflect the increasing intricacy of healthcare IT systems.
CVSS Limitations for Medical Devices
While CVSS works well for enterprise IT systems, it falls short in addressing the unique challenges of clinical environments. As MITRE points out:
"CVSS and its associated rubric and examples were developed for enterprise information technology systems and do not adequately reflect the clinical environment and potential patient safety impacts." [2]
A study comparing evaluations from the National Vulnerability Database (NVD) and ICS-CERT revealed that only 37% of vector assignments were consistent [1]. There were significant differences in assessing Confidentiality, Integrity, and Availability metrics, underlining CVSS's shortcomings in clinical settings. For instance, a vulnerability affecting the availability of an infusion pump could have life-threatening consequences - something standard IT scoring might not fully capture.
Additionally, CVSS doesn't address factors specific to medical devices, such as disruptions to clinical workflows, the sensitivity of Protected Health Information (PHI), or the potential to cause a Potential Impact to Patient Safety (PIPS) [7]. Security measures that make sense in IT, like stringent password requirements, can backfire in healthcare, where delays during emergencies could endanger lives [9]. These gaps have led to the development of tailored scoring systems for medical devices, prioritizing patient safety above all else.
Next, we’ll look at medical device–specific scoring frameworks designed to fill these gaps.
Medical Device-Specific Scoring Frameworks
CVSS vs MITRE Medical Device Rubric Comparison for Healthcare Vulnerability Scoring
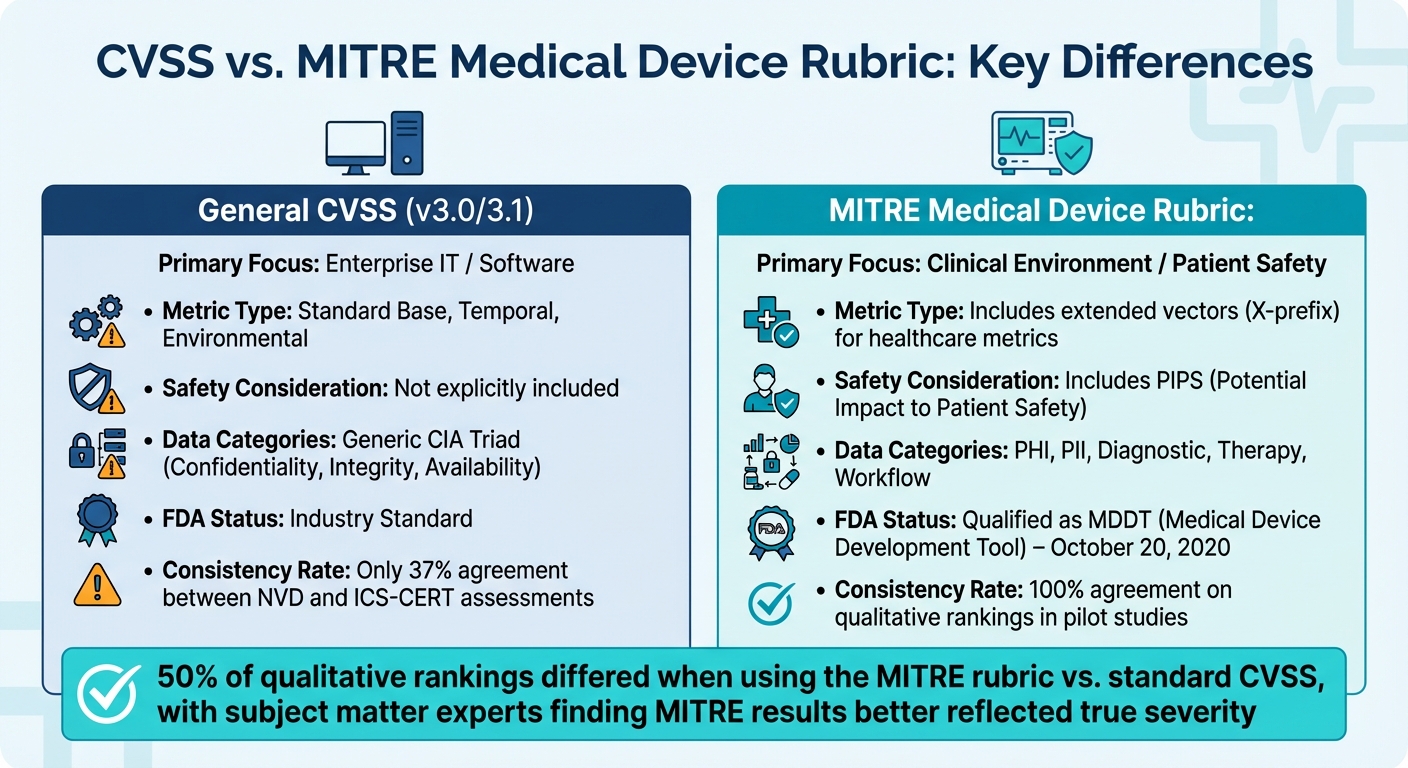
Standard CVSS methods often fall short when assessing risks in clinical settings, as they don't fully account for the unique safety and operational challenges of medical devices. To address these gaps, specialized frameworks have been developed, adding layers of clinical context, workflow considerations, and safety metrics. Among these, the MITRE CVSS Rubric for Medical Devices stands out, earning recognition from regulators.
MITRE CVSS Rubric for Medical Devices
The MITRE CVSS Rubric for Medical Devices is a key framework tailored specifically for healthcare. On October 20, 2020, the FDA officially recognized it as a Medical Device Development Tool (MDDT), giving it regulatory weight [4]. This comprehensive, 78-page guide uses structured questions and decision trees to standardize the scoring process [7].
One of its defining features is the introduction of "Extended Vectors", labeled with a prefix 'X'. These vectors capture healthcare-specific risks that standard CVSS overlooks, such as impacts on Protected Health Information (PHI), diagnostic functions, therapy delivery, and clinical workflows [4]. It also highlights "Potential Impact to Patient Safety" (PIPS), a metric that flags when a deeper safety hazard analysis is necessary [4].
For example, Deep Armor applied the rubric to a Denial of Service (DoS) vulnerability in a smart wearable device. The analysis reclassified the "Attack Complexity" from High to Low and adjusted "Attack Vector" from Adjacent to Local, based on Bluetooth LE's characteristics. This raised the score from 3.1 (Low) to 4.0 (Medium) [4]. Sunil Kumar, a Cybersecurity Analyst at Deep Armor, explained:
"The rubric provides more than a number and the vector: it documents the scoring process and accommodates the clinical end-user environment in assessing exploitability and technical impacts." [4]
The rubric's effectiveness stems from its reliance on multi-disciplinary teams, which include experts in cybersecurity, device engineering, clinical workflows, and patient health impact [4]. While more complex than standard CVSS, pilot studies revealed that 50% of the qualitative rankings differed from the original scores. Subject matter experts found the rubric's results to better reflect the true severity of medical device vulnerabilities [1].
| Feature | General CVSS (v3.0/3.1) | Medical Device Rubric (MITRE) |
|---|---|---|
| Primary Focus | Enterprise IT / Software | Clinical Environment / Patient Safety |
| Metric Type | Standard Base, Temporal, Environmental | Includes extended vectors for healthcare metrics |
| Safety Consideration | Not explicitly included | Includes PIPS (Potential Impact to Patient Safety) |
| Data Categories | Generic CIA Triad | PHI, PII, Diagnostic, Therapy, Workflow |
| FDA Status | Industry Standard | Qualified as an MDDT (Medical Device Development Tool) |
Other Frameworks and Custom Approaches
While the MITRE rubric is a benchmark, some organizations develop custom frameworks to address their specific needs. These approaches aim to refine risk assessments further, always keeping patient safety at the forefront.
Custom frameworks should involve both clinical and technical experts to ensure relevance. For instance, they must account for nuances like the distinction between Bluetooth LE (classified as "Local" due to its range) and Bluetooth Classic (classified as "Adjacent"), which can significantly impact severity scores [4].
Regulatory suitability is another critical factor. For example, the MITRE rubric is approved for post-market vulnerability disclosures but not for pre-market regulatory submissions [4]. Additionally, Environmental Metrics can help organizations communicate the impact of compensating controls, such as hospital-level mitigations, to stakeholders and customers [1].
Although specialized frameworks require more time and resources compared to standard CVSS, they deliver greater consistency and reliability. A comparison between the National Vulnerability Database (NVD) and ICS-CERT revealed that only 37% of vector assignments were identical for medical devices. The largest discrepancies were in confidentiality (66% agreement), integrity (72% agreement), and availability (74% agreement) metrics [1]. Custom frameworks address these gaps by providing structured, repeatable processes that minimize subjective interpretations.
How to Implement Vulnerability Scoring
Implementing vulnerability scoring is more than just running automated scans. It requires a structured approach that blends clinical context with technical analysis. To do this effectively, healthcare organizations need to assemble a team of experts, apply tailored frameworks, and translate vulnerability data into actionable remediation plans that consider both technical severity and clinical impact.
The first step is building a multi-disciplinary team of specialists. This group should include experts in cybersecurity and privacy, device engineering, patient health impact, clinical workflows, and IT interoperability [1][4]. Why is this so important? A single analyst typically can't fully assess how a vulnerability might affect patient safety or disrupt clinical operations. For example, deciding whether a Bluetooth Low Energy attack is "Local" or "Adjacent" requires both technical knowledge and an understanding of how the device is used in a hospital setting [4].
Once the team is in place, organizations can implement the FDA-recognized MITRE Rubric. This tool integrates clinical insights with technical scoring, evaluating vulnerabilities based on Confidentiality, Integrity, and Availability (CIA) impacts across six healthcare-specific categories: PHI/PII data, diagnosis and monitoring, therapy delivery, clinical workflows, system/user data, and other critical functions [4][8]. Vulnerabilities flagged with "Potential Impact to Patient Safety" (PIPS) should trigger immediate safety hazard analysis for FDA reporting. Additionally, "extended vectors" (labeled with an "X") should be documented to show how clinical factors influenced the final score [1][4].
Automating the Scoring Process
Automation plays a key role in making the scoring process faster and more consistent. Manual scoring can be slow and prone to errors, but automation tools - like the Deep Armor Online Calculator or MedSec's Excel-based tool - can streamline this process. These tools guide analysts through structured questions and automatically generate both a numerical score and a vector string [5][2].
As the number of vulnerabilities grows, automation becomes even more critical. Between October 2013 and March 2019, the average number of medical device vulnerabilities disclosed monthly jumped from 0.95 to 4.19 [1]. Without automation, security teams could easily fall behind. However, it’s important to remember that automation should support human judgment, not replace it. Multi-disciplinary teams must review automated results, especially for vulnerabilities flagged as PIPS, to ensure clinical context is properly considered.
Organizations should also integrate scanners with scoring tools to assess vulnerabilities as soon as they’re detected. This reduces delays between identification and prioritization. Automated systems can track changes over time, updating scores as new information or compensating controls are introduced.
Using Scores to Prioritize Remediation
Once scores are refined, the next step is turning them into actionable remediation priorities. Vulnerability scores highlight technical severity but don’t always reflect overall risk. For instance, a high base score might not represent an immediate threat if compensating controls, like network segmentation, are in place. A vulnerability with a base score of 8.5 could drop to 6.2 after accounting for these measures [1].
Organizations should avoid rigid thresholds like “only fixing scores above 7.0.” Instead, focus on patient safety and clinical impact. Vulnerabilities that affect diagnosis, therapy delivery, or clinical workflows should take precedence - even if their technical scores are moderate [1][2]. The PIPS flag is especially helpful in identifying high-priority vulnerabilities that could directly impact patient safety.
A comparison of vector assignments from the National Vulnerability Database (NVD) and ICS-CERT found that only 37% of vectors matched exactly. The greatest differences were in Confidentiality (66% agreement), Integrity (72% agreement), and Availability (74% agreement) metrics [1]. This inconsistency highlights the importance of using structured rubrics and clear prioritization criteria. By documenting the reasoning behind each score and publishing the vector string alongside the numerical value, organizations can create a transparent record that fosters collaboration between manufacturers and healthcare providers.
Pilot studies using a specialized medical device rubric have shown 100% agreement on qualitative rankings (Low, Medium, High, Critical) among different teams scoring the same vulnerability [1]. This consistency is essential for building trust in the scoring process and ensuring remediation efforts focus on the most critical threats. Regular reviews and adjustments to prioritization decisions will help organizations stay ahead as new vulnerabilities arise and clinical environments evolve.
Using Censinet RiskOps™ for Medical Device Security
Healthcare organizations are grappling with a daunting challenge: managing vulnerabilities in a landscape where there are more than 10 connected devices per patient bed. Doing this manually is practically unfeasible [10]. To make matters worse, Medical Device Security ranks at the bottom among the ten Health Industry Cybersecurity Practices (HICP) best practice areas in healthcare delivery organizations [10]. This gap leaves hospitals exposed to cyber threats, especially when device security has become a critical concern.
Censinet RiskOps™ steps in to address this challenge by offering an automated, clinically-aware approach to vulnerability scoring. The platform bridges the gaps between IT, Risk, Cybersecurity, and BioMed teams, uniting them on a single system. This eliminates the silos that often hinder effective device security management. By incorporating clinical engineering expertise into its security assessments, the platform ensures that evaluations consider both technical risks and clinical workflows. Beyond automation, Censinet RiskOps™ integrates clinical context into its scoring process, making assessments more relevant to patient safety.
It also aligns with key regulatory frameworks like HIPAA, FDA cybersecurity guidelines, and NIST standards, ensuring compliance. Additionally, it supports "Potential Impact to Patient Safety" (PIPS) considerations, helping analysts decide when a vulnerability requires a safety-oriented hazards analysis for FDA reporting.
Automated Vulnerability Scoring with Censinet RiskOps™
One of the standout features of Censinet RiskOps™ is its ability to automate vulnerability scoring, eliminating the delays caused by manual processes. The platform automatically ingests and processes Manufacturer Disclosure Statement for Medical Device Security (MDS2) forms from both 2013 and 2019 versions. This capability extracts device-specific security data without requiring manual input [10]. Given that between October 2013 and August 2019, 68 ICS-CERT advisories revealed 152 vulnerabilities in medical devices, automation is no longer optional - it's essential [1].
Using AI-powered algorithms, the platform evaluates device vulnerabilities and assigns risk scores in a fraction of the time manual methods would take. Healthcare organizations can also tap into the Digital Risk Catalog™, a robust library of previously assessed devices, to expedite scoring for equipment that has already been evaluated. This shared knowledge base ensures that organizations don’t need to start from square one with every assessment. Once vulnerabilities are scored, the system generates Corrective Action Plans automatically, tracks remediation progress, and assigns tasks to internal experts like BioMed technicians. This ensures that security patches are applied promptly without disrupting clinical workflows.
Additionally, the platform offers real-time monitoring and integrates seamlessly with existing healthcare IT systems, providing continuous visibility into device security postures and enabling smooth data exchange.
AI-Powered Risk Management and Team Collaboration
Censinet AI™ takes automation a step further, streamlining risk assessments even more. It accelerates vendor questionnaire completion, summarizes vendor evidence and documentation, and generates risk summary reports by analyzing all relevant assessment data. While automation drives efficiency, human oversight remains central, ensuring that healthcare organizations maintain control as they scale their risk management efforts.
The platform also acts as a central hub for governance, routing key findings and tasks to the appropriate stakeholders for review and action. Executive dashboards present filtered views tailored to different audiences - technical teams get detailed device data, while Boards and executives see high-level, enterprise-wide risk summaries to guide strategic decisions [10]. This targeted approach ensures that the right people address the right issues at the right time, enabling continuous oversight, accountability, and governance across the entire organization.
Conclusion
Medical device vulnerability scoring is a critical aspect of ensuring patient safety and maintaining uninterrupted healthcare operations. With the rapid increase in device connectivity and vulnerability disclosures, healthcare organizations can no longer depend on manual processes, which often leave dangerous gaps in security.
Traditional CVSS metrics, while effective for enterprise IT, fall short in addressing the unique clinical factors vital to patient safety. Specialized frameworks like the MITRE CVSS Rubric address this gap by tailoring the scoring process to reflect the real-world clinical environment, ensuring that decisions are made with patient care in mind.
However, scoring vulnerabilities is only part of the solution. True vulnerability management requires collaboration across multiple departments. When IT, Risk, Cybersecurity, and BioMed teams join forces on a unified platform, they can prioritize vulnerabilities based on their actual impact on patient care, rather than relying on generic severity scores. This approach ensures that critical vulnerabilities - those affecting life-saving devices or sensitive patient data - are addressed immediately. With more than 10 connected devices per patient bed in modern healthcare settings, this level of coordination is not optional - it’s essential [10].
Censinet RiskOps™ simplifies this challenge by automating key processes like MDS2 ingestion, generating AI-driven risk scores, and creating actionable remediation plans. Its Digital Risk Catalog™ provides a centralized, searchable library of assessed devices, reducing redundant efforts and speeding up evaluations. Executive dashboards further enhance decision-making by offering detailed technical insights for operational teams and high-level summaries for leadership. This integrated system not only accelerates remediation but also ensures continuous compliance and real-time monitoring.
In a landscape where Medical Device Security ranks at the bottom of the Health Industry Cybersecurity Practices, healthcare organizations need tools that deliver real-time visibility, automated workflows, and a focus on clinical priorities [10]. By combining specialized frameworks with intelligent automation, organizations can protect patients, secure sensitive data, and maintain operational stability. This approach bridges the gap between technical expertise and clinical needs, ensuring healthcare systems remain both secure and patient-focused.
FAQs
When should a medical device vulnerability be flagged for patient safety impact (PIPS)?
A medical device vulnerability must be flagged for Patient Safety Impact (PIPS) if it’s determined that the issue could harm patient safety. To make this determination, a safety-focused hazard analysis is essential. This analysis helps decide whether the vulnerability needs to be reported to the FDA.
How do MITRE medical device extended vectors affect CVSS scores in real hospitals?
MITRE's medical device extended vectors offer a way to fine-tune CVSS scores in hospital settings by factoring in patient safety and the clinical environment. These vectors adjust the severity rating by analyzing how a vulnerability might specifically affect patient safety and the functionality of medical devices. Depending on the context and conditions, they can either raise or lower the score to better reflect practical, real-world risks.
What’s the best way to automate vulnerability scoring without losing clinical context?
Using frameworks and tools specifically designed for healthcare is key to effective risk assessment. One standout example is the FDA-qualified MITRE CVSS Rubric for Medical Devices, which ensures that vulnerability evaluations prioritize patient safety and clinical impact.
Some advanced tools take this a step further by incorporating clinical data and aligning with regulatory standards. These tools automate scoring processes while keeping the clinical context front and center. The result? Faster, more efficient risk evaluations that never lose sight of what matters most: safety and impact.


