Vendor Breaches: Risks for Healthcare Networks
Post Summary
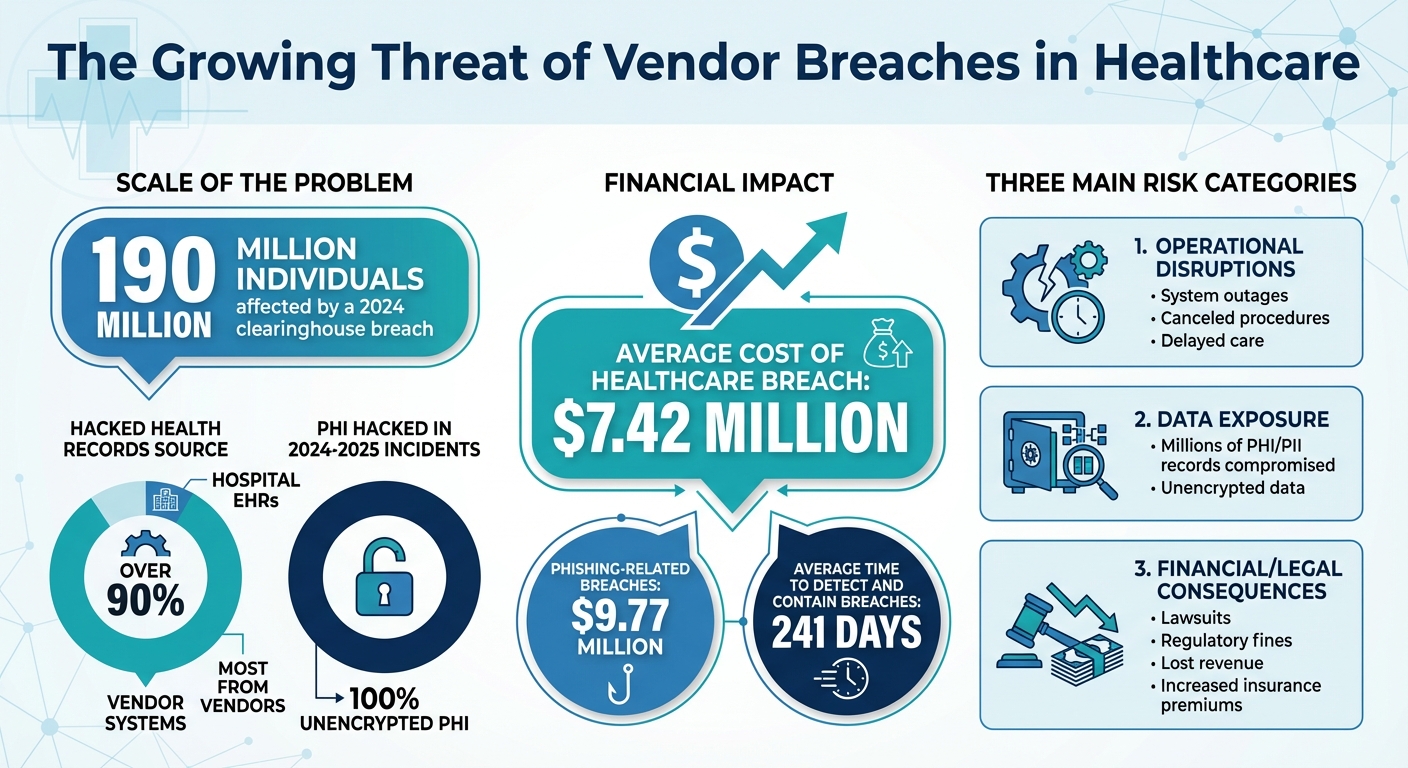
Vendor breaches in healthcare are a growing concern. These occur when third-party vendors, like IT providers or billing companies, are compromised, exposing sensitive patient data or disrupting operations. Recent statistics highlight the scale of the problem:
- 190 million individuals were affected by a 2024 clearinghouse breach.
- Over 90% of hacked health records come from vendor systems, not hospital EHRs.
- The average cost of a healthcare breach is $7.42 million.
Healthcare organizations face unique challenges, including outdated systems, excessive vendor access, and unencrypted data. These vulnerabilities not only lead to financial losses but also jeopardize patient safety and trust.
Key takeaways:
- Operational disruptions: Breaches can halt critical systems, delay care, and increase risks for patients.
- Data exposure: Vendors often store unencrypted PHI, making breaches more damaging.
- Financial/legal impact: Costs include lawsuits, regulatory fines, and lost revenue.
To reduce risks, healthcare providers must adopt stricter vendor access controls, enforce security standards, and establish joint incident response plans. Tools like centralized risk management platforms can streamline assessments and monitoring, helping organizations stay ahead of threats.
Healthcare Vendor Breach Statistics and Financial Impact
Risks Vendor Breaches Create for Healthcare Networks
Disruptions to Operations and Patient Care
When a vendor is compromised, the ripple effects can bring healthcare operations to a standstill. Imagine dealing with sluggish or completely offline electronic health records (EHR), lab systems grinding to a halt, scheduling failures, or supply chain delays. These disruptions often force hospitals to revert to manual workflows, cancel procedures, reroute ambulances, and stretch emergency room wait times to frustrating lengths [5].
The clinical consequences, however, go far beyond inconvenience. If a breach impacts clinical applications or connected medical devices, it can delay critical tasks like administering medication, reviewing lab results, or interpreting radiology scans. These delays increase the risk of diagnostic errors or missed signs of patient deterioration. Without real-time access to decision-support tools, historical records, or cloud-based imaging archives, clinicians are left making life-or-death decisions with incomplete information. This can lead to adverse events, repeated tests, and treatment delays. Beyond that, extended outages at billing, referral, or authorization vendors can create further chaos for patients with chronic or complex conditions, potentially interrupting their care plans and delaying essential treatments [5]. On top of these operational challenges, vendor breaches also threaten the integrity and privacy of patient data.
Patient Data and Privacy Exposure
As healthcare operations falter, the exposure of sensitive patient data becomes an even greater concern. Vendors often store massive amounts of protected health information (PHI) and personally identifiable information (PII) - like names, addresses, Social Security numbers, and medical details - outside the main EHR system [4][6]. A single breach can expose millions of records. In some recent cases, tens of millions of individuals were affected. Alarmingly, over 90% of hacked health records come from vendor-managed systems rather than the primary EHR, such as ancillary applications, data warehouses, or file-sharing platforms. Even worse, 100% of the PHI hacked in incidents from 2024–2025 was unencrypted, leaving it immediately usable by bad actors [6][7].
Under HIPAA, healthcare organizations are still responsible for managing the aftermath of a breach, even when the vendor is at fault. This includes notifying affected individuals, the Department of Health and Human Services (HHS) Office for Civil Rights, and sometimes the media. If the breach spans multiple states, organizations may also face investigations from state attorneys general and have to navigate various state-specific notification laws, piling on more regulatory headaches and costs [4].
The damage doesn’t stop there. Patients often hold healthcare providers accountable, even if the breach originated with a vendor. This can severely erode trust. High-profile breaches often spark class-action lawsuits, intense media scrutiny, and social media backlash, all of which can tarnish a provider’s reputation. To recover, organizations frequently invest heavily in public relations campaigns, patient outreach programs, call centers, and long-term identity protection services - a stark reminder of how exposed healthcare providers are when it comes to data breaches [2][3].
Financial and Legal Consequences
Vendor breaches also bring significant financial and legal challenges, further straining healthcare organizations. The financial toll is staggering. Healthcare consistently ranks as the industry with the highest average cost per breach in the U.S. - around $7.42 million per incident. Phishing-related breaches can be even costlier, averaging $9.77 million per incident [3][5][8].
These costs cover a wide range of expenses, including forensic investigations, legal fees, regulatory fines, patient notifications, call center operations, credit monitoring, IT recovery efforts, lost revenue from canceled procedures, delayed billing cycles, and increased insurance premiums. Long-term impacts, like patient churn and diminished trust, further add to the financial burden [3][4][8].
Legal consequences can be equally severe. Vendor breaches often lead to class-action lawsuits citing negligence or insufficient security measures [3]. Settlements from these lawsuits can run into the tens of millions of dollars, typically including cash payouts, extended identity protection services, and commitments to improve security. Additionally, organizations may face disputes with vendors over indemnification clauses, as well as lawsuits from shareholders or bondholders if financial performance takes a hit [3].
The financial strain doesn’t end with the immediate fallout. Breaches can drive up cyber insurance premiums and deductibles, or even limit future coverage options, making it more expensive to manage risk moving forward [8]. They also create long-term inefficiencies, such as the need for redundant systems, stricter vendor onboarding processes, and manual verification steps that slow down innovation. Over time, reputational damage can lead to reduced patient volumes, lost partnerships, and more conservative terms from lenders or investors, ultimately raising the cost of doing business and stifling growth [3][8].
Why Vendor Breaches Happen
Inadequate Third-Party Risk Assessments
Healthcare organizations often rely on static questionnaires during vendor onboarding, which fail to account for evolving security risks. This outdated approach overlooks critical updates, such as new subcontractors, system changes, emerging threats, or a vendor's declining security practices [4]. Additionally, many organizations neglect to investigate their vendors' downstream partners, leaving significant blind spots in their data supply chain. A striking example is the 2023 PJ&A transcription vendor breach, where the vendor remained compromised for weeks. Alarmingly, some healthcare providers only learned about the incident months later, highlighting gaps in oversight and vague notification terms in contracts [9].
Vendors frequently provide unverified documentation - like SOC 2 reports, penetration test results, or encryption proof - as evidence of their security posture. However, contracts often lack enforceable security requirements such as mandatory encryption, multi-factor authentication (MFA), timely patching schedules, or strict incident notification deadlines. Without these safeguards, vendors have little motivation to maintain robust security measures, leaving healthcare organizations with limited options when breaches occur [4].
Weak Vendor Access Controls
In healthcare, vendor access to networks is often excessive and poorly managed. Many organizations grant broad VPN or remote desktop access, rather than limiting vendors to specific applications. This issue is compounded by the use of shared or generic accounts, which makes it nearly impossible to trace actions back to an individual. When MFA isn't enforced, a single stolen password - often obtained through phishing or reused credentials - can grant attackers direct access to sensitive systems [2].
Research shows that compromised credentials and phishing are among the leading methods attackers use to gain access in healthcare breaches. Phishing alone accounts for about 16% of incidents, while user account compromises impact over 70% of cloud-based healthcare environments [2]. Once inside, attackers exploit weak network segmentation in vendor-managed systems to move laterally, escalate privileges, and steal protected health information (PHI). Implementing measures like account segmentation, enforcing MFA, and conducting regular access reviews can significantly limit the damage from such breaches. However, these vulnerabilities are often exacerbated by outdated systems.
Outdated Systems and Insufficient Monitoring
Many vendors rely on outdated systems - such as legacy billing platforms or imaging archives - that run on unsupported operating systems. These systems often lack critical updates and modern security features like MFA, detailed logging, or endpoint detection and response (EDR) tools [2][5]. Attackers commonly exploit known vulnerabilities in these systems, taking advantage of weak authentication protocols or poorly configured remote desktop setups to gain an initial foothold. Once inside, ransomware attacks can cripple healthcare operations.
The lack of proper monitoring in vendor-managed environments makes matters worse. Many vendors operate without 24/7 security teams, centralized logging, or clear procedures for identifying suspicious activity, such as unusual data transfers or logins from unexpected locations [9]. These gaps allow intrusions to go unnoticed for weeks or even months. Prolonged breaches not only expose more records but also lead to higher regulatory penalties and increased remediation costs. Delayed detection and notification by vendors slow down healthcare providers' ability to respond, notify patients, and coordinate with regulators, amplifying both legal and reputational fallout [9].
How to Reduce Vendor Risks in Healthcare Networks
Build a Vendor Risk Management Program
Healthcare organizations need a centralized vendor risk management program supported by executive leadership to bring together security, compliance, and supply chain teams. Start by creating a comprehensive inventory of vendors who have access to PHI (Protected Health Information) or critical systems. From there, implement risk-based tiering to classify vendors into high, medium, or low-risk categories based on factors like PHI exposure, network connectivity, and their role in patient care [2][4].
High-risk vendors often include EHR providers, cloud hosting services, medical device manufacturers, and billing companies that process PHI or connect directly to clinical systems. These vendors should undergo thorough due diligence, such as completing security questionnaires (aligned with HIPAA and frameworks like NIST or HITRUST), SOC 2 audits, and documenting data flows [4]. Vendor contracts, including BAAs (Business Associate Agreements), should outline enforceable security standards like encryption, multi-factor authentication (MFA), patching protocols, and incident notification requirements.
Ongoing monitoring is just as important as initial assessments. High-risk vendors should be reviewed at least annually or whenever significant changes occur, such as acquisitions, new hosting regions, or security incidents [2]. Tools like Censinet RiskOps™ can simplify this process by centralizing risk data, automating security questionnaires, and benchmarking vendor performance. These platforms calculate risk scores, track remediation efforts, and flag vendors requiring closer scrutiny.
Terry Grogan, CISO at Tower Health, highlighted the efficiency of such platforms: "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required" [1].
Once the risk management program is in place, the next step is to limit vendor access to critical systems and networks.
Strengthen Vendor Access and Network Security
Adopt the principle of least privilege by granting vendors only the minimum access required for their tasks, and ensure that access is time-limited. Require unique, individual accounts for vendor personnel to avoid shared or generic credentials, which make it difficult to trace activities back to specific individuals [2]. Additionally, enforce MFA for all remote access points, such as VPNs and remote desktops, as compromised user accounts are responsible for over 70% of cloud-related breaches [2].
Network segmentation is another essential measure to reduce the impact of potential breaches. Vendor connections should terminate in isolated, monitored zones with strict firewall rules rather than providing unrestricted access to the entire hospital network [5]. This setup helps protect critical systems like EHRs, PACS, and pharmacy applications by restricting lateral movement. Use centralized security monitoring tools like SIEM or XDR to aggregate logs from VPNs, identity systems, and critical applications. These tools can detect unusual vendor activities - such as off-hours access, large data exports, or attempts to access unauthorized subnets - and trigger alerts.
Vendor contracts should also mandate baseline security measures, including encryption for data in transit and at rest, timely patch management, and the use of endpoint detection and response (EDR) tools. Organizations should maintain an up-to-date inventory of all vendor-managed systems, regularly scan them for vulnerabilities, and verify that security controls like encryption and logging are properly configured [6][7].
While limiting access reduces risk, having a solid plan for incident response ensures swift containment and recovery.
Improve Incident Response and Recovery Planning
To complement strong risk management and access controls, healthcare organizations need joint incident response playbooks with key vendors. These playbooks should outline how and when vendors must report suspected incidents, initial triage procedures, containment steps, and communication protocols. Clearly define roles: the vendor typically handles forensic investigations, while the healthcare team manages containment and clinical workarounds. Include regulatory requirements, such as notifying the HHS Office for Civil Rights in the event of PHI breaches, and specify who is responsible for preparing and approving these notifications [4].
Customizing recovery plans for critical vendors is equally important. These plans should detail key applications, recovery objectives, and dependencies. For clinical systems, include procedures for handling downtime, such as manual order entry or medication administration, to ensure patient safety during system failures. Document strategies for switching to redundancy options like secondary vendors, mirrored environments, or local read-only data copies.
Regularly conduct tabletop exercises and live failover tests with vendors to confirm the reliability of backups, the restart process for interfaces, and staff readiness for manual workflows. This is especially crucial given the high cost of healthcare breaches in the U.S., which average $7.42 million per incident [3][8], with phishing-related breaches reaching as high as $9.77 million [5]. These tested recovery capabilities are essential for minimizing both patient safety risks and financial losses.
sbb-itb-535baee
How to Measure Vendor Risk Management Success
Track Key Performance Metrics
To evaluate how well vendor risk management is working, start by focusing on measurable outcomes. One critical metric is the incident rate attributed to vendors, which tracks the number of security breaches or incidents per 100 active vendors each quarter. This metric provides a clear picture of whether your vendor ecosystem is becoming safer over time. Additionally, keep an eye on Mean Time to Detect (MTTD) and Mean Time to Recover (MTTR) for vendor-related incidents. These metrics are vital because the average time to detect and contain breaches currently sits at 241 days [2]. Reducing these timelines year after year should be a priority.
Other key metrics include vendor risk assessment coverage (the percentage of vendors that have completed initial and annual reassessments), remediation SLA adherence (how often vendor issues are resolved within agreed timelines), and vendor security control maturity (the percentage of vendors meeting minimum standards like MFA, PHI encryption, and regular patching). These metrics aren’t just about compliance - they directly tie to financial risk. For example, the average cost of a healthcare breach in the U.S. is $7.42 million, while phishing-related breaches can climb to $9.77 million. Tools like Censinet RiskOps™ can streamline tracking by centralizing data, calculating risk scores, and generating dashboards that highlight vendors needing immediate attention. Comparing your metrics to industry standards can further refine your risk management approach.
Use Benchmarking for Program Improvement
Metrics alone don’t tell the full story - they need context. That’s where benchmarking comes into play. Comparing your performance to industry peers helps you understand how your program measures up and where it might need improvement. External benchmarks, such as breach frequency per 10,000 patients, average containment times, and cost per breach, highlight why healthcare remains one of the most targeted and financially impacted industries.
Frameworks like NIST CSF, HITRUST, or HHS 405(d) Health Industry Cybersecurity Practices offer structured ways to evaluate your program across areas like governance, assessment, monitoring, and response. Many healthcare-specific platforms also provide cybersecurity benchmarking tools, enabling organizations to anonymously compare metrics like assessment completion rates and response times with others in the industry.
Brian Sterud, CIO at Faith Regional Health, emphasized: "Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters" [1].
This type of peer comparison not only highlights gaps in your program but also strengthens your case for investing in additional vendor risk management capabilities.
Assess Impact on Operations and Patient Care
Ultimately, the success of a vendor risk management program is reflected in its impact on daily operations and patient care. Track downtime hours of critical clinical systems - like EHR, PACS, lab, and pharmacy systems - caused by vendor-related issues each quarter. Additionally, document the number of canceled or rescheduled appointments, procedures, or admissions due to vendor system outages or security incidents. These metrics tie directly to patient outcomes and operational efficiency.
Improved efficiency is another sign of success. For example, Tower Health experienced tangible benefits after adopting Censinet RiskOps™:
Terry Grogan, CISO at Tower Health, shared: "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required" [1].
When vendor risk management programs reduce downtime, accelerate recovery, and free up staff for other priorities, the benefits extend beyond security. These improvements translate into better care delivery, smoother operations, and more effective resource use.
Conclusion: Building Resilient Healthcare Networks
Vendor breaches pose a serious threat to healthcare operations and, more importantly, patient safety. With third-party incidents now responsible for some of the largest data breaches in the industry - and the average U.S. healthcare breach costing a staggering $7.42 million - managing vendor risks is no longer optional. It’s a critical function tied directly to patient safety and the resilience of healthcare organizations.
To build resilient networks, healthcare providers need to focus on several key strategies: standardized vendor assessments, continuous monitoring, restricted access, and well-practiced incident response plans. These measures are essential to protecting vital clinical workflows, ensuring critical systems like EHRs and pharmacy platforms remain operational, and maintaining the trust patients place in their care teams.
By adopting proven risk management practices, healthcare organizations can safeguard both their operations and the quality of care they deliver. Success in this area requires more than just policies - it demands action. Leading organizations link vendor risk management directly to patient care by mapping critical workflows to the vendors supporting them, involving clinical leaders in decision-making, and conducting vendor-related incident drills to prepare for potential crises. They also track meaningful metrics, such as downtime caused by vendor issues, remediation timelines, and breach costs, benchmarking this data against industry peers to drive improvements and justify necessary investments.
Tools like Censinet RiskOps™ simplify these efforts by streamlining assessments, enabling collaborative remediation, and providing continuous monitoring across areas like PHI, medical devices, and supply chains. The focus isn’t on achieving perfection but on maintaining constant vigilance and adapting to evolving threats.
Resilient healthcare networks understand that every vendor connection is a potential vulnerability. Proactive risk management is the foundation for preventing crises and protecting patients. Safeguarding the ecosystem that supports patient care is not just a strategy - it’s a responsibility. Together, these measures form a robust approach to securing the future of healthcare.
FAQs
What steps can healthcare organizations take to manage vendor risks effectively?
Healthcare organizations can tackle vendor risks more effectively by embracing continuous and proactive risk management strategies. Tools like Censinet RiskOps™ can simplify third-party assessments, provide benchmarks for cybersecurity performance, and facilitate collaboration with vendors to address weaknesses.
Key steps include conducting regular risk assessments, fostering transparent communication with vendors, and embedding risk management into broader cybersecurity plans. These actions play a crucial role in protecting sensitive patient information, PHI, and essential systems from breaches, creating a stronger and more secure healthcare network.
What are the main causes of vendor breaches in healthcare networks?
Vendor breaches in healthcare often arise from poor security practices, like weak access controls, outdated software, or inadequate data encryption methods. Another frequent cause is the failure to conduct comprehensive vendor risk assessments, leaving potential vulnerabilities unchecked. On top of this, insufficient cybersecurity training for vendor employees and flaws in third-party systems connected to healthcare networks can further expose sensitive data.
To address these challenges, healthcare organizations should focus on strong risk management strategies. This includes routinely assessing vendor security protocols and ensuring all partners meet industry standards for safeguarding patient information.
What risks do vendor breaches pose to patient care and safety?
Vendor breaches pose serious challenges for healthcare organizations. They can reveal sensitive patient information, disrupt essential clinical systems, and interfere with the delivery of care. The consequences? Delayed treatments, risks to patient safety, and a potential erosion of trust in the organization.
To counter these threats, healthcare providers must tackle vulnerabilities head-on and adopt strong risk management strategies. Doing so helps safeguard their operations while ensuring the well-being and trust of their patients.


