How Vendor Risk Scoring Reduces Cyber Threats
Post Summary
A numeric scoring system that measures vendor cybersecurity risk on a consistent scale, making risks easier to compare and act on.
Quantitative scoring uses standardized metrics and eliminates subjectivity, making evaluations more consistent and defensible.
By revealing high-risk vendors, enabling faster remediation, supporting financial impact analysis, and enabling continuous monitoring.
Security questionnaires, scans, certifications, incident history, benchmarking data, and evidence from platforms like Censinet RiskOps™.
Vendors with low scores or high criticality trigger targeted reviews, stricter controls, and faster intervention.
By tracking remediation rates, score improvements, incident reductions, and long‑term shifts in vendor risk tiers.
Vendor risk scoring helps healthcare organizations identify and manage cybersecurity threats from third-party vendors. With the rise in vendor-related breaches delaying treatments and compromising patient safety, healthcare providers need a systematic way to assess risks. Traditional methods like spreadsheets fail to keep up with evolving threats, prompting a shift to quantitative risk scoring.
Key takeaways:
This approach ensures healthcare organizations can protect sensitive data, maintain clinical operations, and avoid costly breaches.
How Vendor Risk Scoring Works: From Assessment to Action in Healthcare
What Is Quantitative Vendor Risk Scoring?
Quantitative vendor risk scoring takes raw vendor data and turns it into actionable insights, helping healthcare organizations make smarter decisions to minimize cyber threats. By assigning measurable values to vendor risks, organizations can pinpoint and prioritize vulnerabilities across their supply chains.
Vendor Risk Scoring Defined
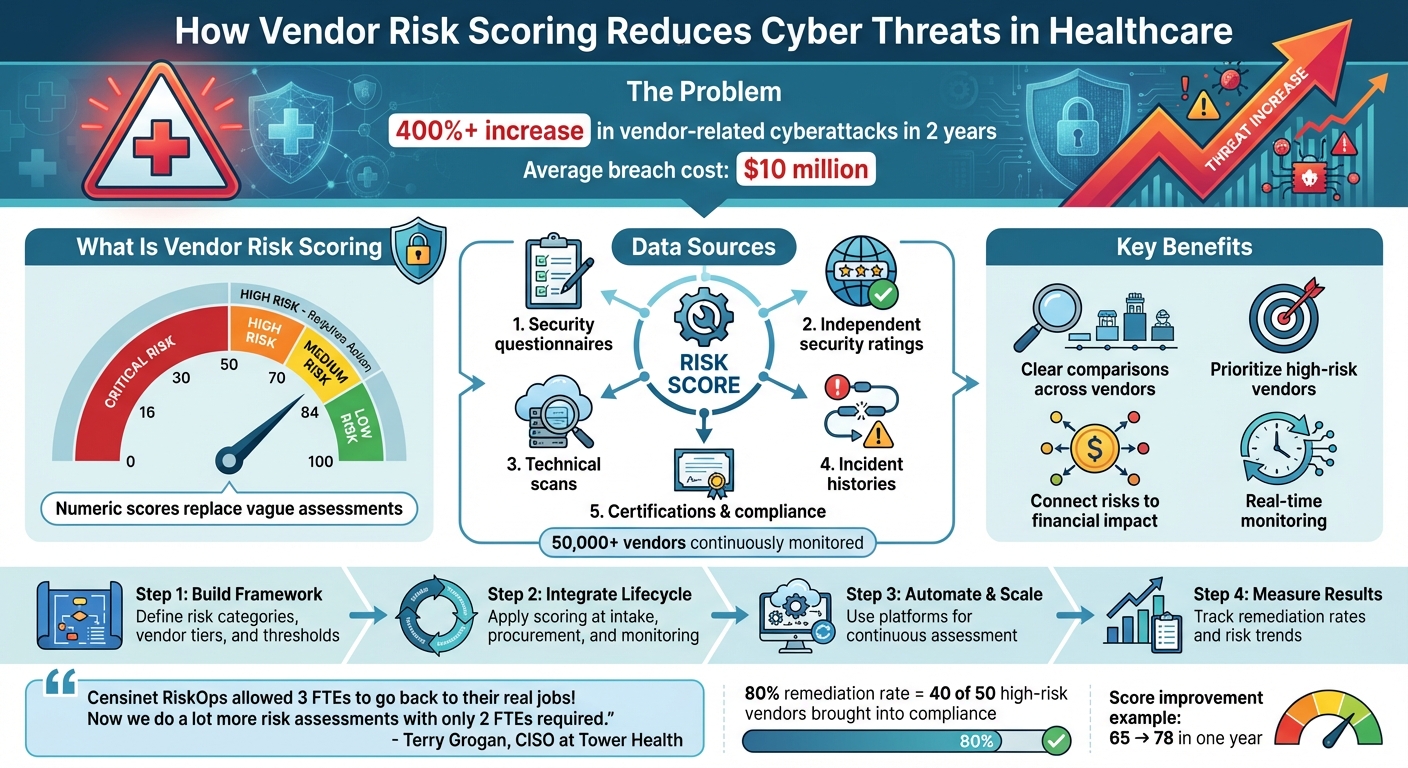
Vendor risk scoring assigns a numeric value (on a 0–100 scale) to each vendor's cybersecurity risk. Unlike categorical labels, these numbers offer a clearer way to compare risks. The score reflects factors like cybersecurity posture, regulatory compliance, and operational resilience. For instance, the Cloud Security Alliance emphasizes that a formal supplier risk rating process is one of the most effective tools for healthcare organizations to assess and manage supply chain cyber risks [2].
This numerical approach provides a solid foundation for comparing quantitative methods to more traditional, qualitative evaluations.
Quantitative vs. Qualitative Risk Scoring
The main distinction between quantitative and qualitative scoring lies in how precise and consistent they are. Qualitative methods rely on descriptive labels and narratives, which can vary depending on who’s evaluating. On the other hand, quantitative scoring uses standardized criteria and weighted formulas, ensuring consistent, unbiased evaluations. This method not only simplifies prioritization but also supports financial modeling for cyber risks. For example, cybersecurity teams can focus on fixing issues with vendors scoring below 70.
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters"
.
Now, let’s look at the variety of data sources that fuel these scores.
Data Sources for Healthcare Vendor Risk Scoring
Accurate vendor scores come from a mix of data, including security questionnaires, independent security ratings, technical scans, incident histories, and certifications. Platforms like Censinet RiskOps™ pull data from over 50,000 vendors, continuously updating scores as vulnerabilities, incidents, or certification statuses change [1]. This system allows healthcare organizations to share completed security questionnaires and evidence efficiently while integrating cybersecurity benchmarking data to improve program maturity. By quantifying risks, healthcare providers can zero in on vulnerabilities and take steps to reduce cyber threats effectively.
How Vendor Risk Scoring Reduces Cyber Threats
Quantitative vendor risk scoring is changing the way healthcare organizations tackle cyber threats by making risks more visible, comparable, and actionable. With vendor-related cyberattacks in healthcare supply chains surging over 400% in just two years[4], it’s clear that organizations need a systematic approach to pinpoint and address vulnerabilities before they lead to breaches.
Turning Complex Risks into Clear Numbers
Numeric risk scores simplify the process of assessing vendors by replacing vague evaluations with standardized metrics. Instead of relying on lengthy, subjective reports, security teams can quickly spot vendors falling below critical thresholds (e.g., a score under 70) and take immediate action. Tools like Censinet RiskOps™ ensure these scores are based on consistent criteria rather than individual interpretation[1]. For example, a score of 65 reflects the same level of risk across different vendors, allowing for straightforward, apples-to-apples comparisons that qualitative methods just can’t match.
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."
Prioritizing High-Risk Vendors
With clear numerical rankings, healthcare organizations can focus their limited security resources on vendors that pose the highest risks. This method allows teams to quickly identify and address relationships that threaten patient data or disrupt clinical operations. Terry Grogan, CISO at Tower Health, highlighted the efficiency gained from adopting Censinet RiskOps:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."
By automatically flagging high-risk vendors, organizations can implement policies that trigger targeted reviews and interventions where they’re needed most.
Connecting Cyber Risks to Financial Impact
Numeric risk scores don’t just identify vulnerabilities - they also help organizations understand the financial stakes. By linking cyber risks to potential financial losses, these scores make it easier to justify cybersecurity investments to executives who are focused on budget impacts. For instance, organizations can use these metrics to guide decisions on insurance, contract negotiations, and resource allocation. The Health Industry Cybersecurity Supply Chain Risk Management guide underscores how formal risk rating processes help healthcare organizations assess their risk tolerance and prioritize mitigation efforts across their vendor networks[2][3].
Real-Time Monitoring for Faster Action
Unlike traditional assessments that provide a one-time snapshot, continuous monitoring ensures organizations stay on top of evolving threats. Regularly updated scores reflect new vulnerabilities, incidents, or certification changes as they arise. Censinet RiskOps, for example, uses AI-driven, cloud-based technology to keep vendor scores current[1]. If a vendor’s score drops - perhaps due to a newly identified vulnerability or a failed audit - automated workflows can trigger immediate actions, such as pausing data exchanges, escalating concerns to the security team, or initiating remediation efforts.
Building a Shared Framework for Teams
Vendor risk scores create a common language that bridges gaps between cybersecurity, compliance, supply chain, and clinical teams. This shared framework simplifies decision-making across departments. For example, when everyone understands that a score below 70 signals "high risk requiring immediate action", cross-functional discussions become more focused and effective. Clinical leaders don’t need to dive into every technical detail - they just need to know that a vendor meets the organization’s safety standards. Purpose-built scoring frameworks also address healthcare-specific needs, such as patient safety, regulatory compliance, and clinical workflows, ensuring that the system resonates with all stakeholders.
How to Implement Vendor Risk Scoring in Healthcare
Building a Healthcare-Specific Scoring Framework
Healthcare organizations face unique challenges, such as protecting patient safety, safeguarding PHI (protected health information), securing medical devices, and meeting strict regulatory requirements. To address these, a tailored risk scoring framework is essential.
Start by identifying key risk areas - like data security, clinical safety, regulatory compliance, and operational continuity - and prioritize them based on your organization's risk tolerance. For instance, you might assign greater importance to risks involving PHI exposure compared to less critical operational concerns.
Next, categorize vendors by their level of criticality. According to the Health Industry Cybersecurity Supply Chain Risk Management Guide, grouping vendors based on factors like data access, clinical impact, and operational significance makes the process more manageable [3]. High-priority vendors - those with direct access to PHI or critical clinical systems - should undergo thorough assessments, while lower-tier vendors can be reviewed with less intensity. This tiered approach ensures that resources are focused where they’re needed most, without overburdening your team.
Clear governance is another critical step. Define who is responsible for scoring decisions, establish thresholds that trigger action (e.g., requiring remediation for scores below a certain level), and determine how often scores should be reviewed. The Cloud Security Alliance highlights that a formalized risk rating system helps align vendor risks with the organization's overall risk strategy [2]. Collaboration across departments - such as cybersecurity, compliance, procurement, and clinical teams - ensures that risk scores are actionable and support informed decision-making.
Once the framework is in place, integrate these metrics throughout the vendor lifecycle for consistent oversight.
Integrating Risk Scoring Across the Vendor Lifecycle
A strong framework is just the beginning. To be effective, risk scoring must be woven into every stage of the vendor lifecycle, from onboarding to ongoing monitoring.
During vendor intake, use risk scores to evaluate whether a vendor meets your organization's minimum security requirements before moving forward with contract discussions. Tools like Censinet Connect™ streamline this process by enabling vendors to share completed security questionnaires quickly [1].
In the procurement and contracting phase, align cybersecurity requirements - such as incident reporting, timely patching, encryption, multi-factor authentication, and auditing rights - with the vendor's risk tier [3]. Vendors classified as high-risk should face stricter contractual obligations and more frequent audits. The Health Sector Coordinating Council's supply chain guide offers templates for contract language and cybersecurity requirements, making it easier to integrate risk scoring into contracts.
For ongoing oversight, implement continuous monitoring to keep risk scores up to date. This includes tracking new vulnerabilities, audit results, and any security incidents that arise.
Using Censinet RiskOps™ to Scale Your Program

Managing vendor risk with spreadsheets becomes unmanageable as vendor numbers grow. Censinet RiskOps™ addresses this challenge with a platform specifically designed for healthcare organizations [1]. It automates workflows, standardizes vendor scoring, and enables near real-time monitoring - capabilities that traditional manual processes simply can’t match.
The platform’s collaborative risk network connects healthcare organizations with over 50,000 vendors and products. This network allows organizations to access pre-completed assessments and shared intelligence, reducing redundant effort and enabling teams to evaluate more vendors with fewer resources [1].
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."
Censinet RiskOps™ also helps organizations benchmark their cybersecurity efforts against industry standards, making it easier to refine vendor risk practices and secure necessary resources. Additionally, its cloud-based risk exchange simplifies the secure sharing of cybersecurity data between healthcare organizations and their vendors, ensuring smooth collaboration throughout the vendor relationship - from onboarding to offboarding.
sbb-itb-535baee
Measuring the Results of Vendor Risk Scoring
Metrics That Show Success
To gauge how well your vendor risk scoring program is performing, focus on key metrics like vendor-related security incidents, the time it takes to detect and fix issues, and the remediation rate for high-risk vendors. A successful program should result in fewer incidents quarter over quarter.
One critical metric is the percentage of high-risk vendors remediated. For example, if you've identified 50 vendors with critical security gaps and managed to bring 40 of them into compliance within six months, that's an 80% remediation rate. Additionally, keep an eye on audit and compliance results - fewer "high findings" in assessments like HIPAA audits or Joint Commission reviews indicate that your oversight efforts are effective [5]. You can also estimate cost avoidance by factoring in the average cost of a breach, which is nearly $10 million [4], and highlight reduced cyber insurance premiums as further proof of success.
Tracking Risk Reduction Over Time
Metrics tell part of the story, but trends reveal the bigger picture. Track the quarterly average vendor risk score over time. A consistent downward trend - indicating lower risk - shows real progress. Break these trends down further by vendor type (e.g., EHR systems, cloud hosting, medical device manufacturers, telehealth platforms) and data sensitivity (e.g., PHI, payment data, IoT/OT devices) to identify where improvements are happening most rapidly [4][5].
Compare current scores to historical benchmarks. For instance, if your average vendor score was 65 out of 100 a year ago and now it's 78, that's clear progress. Also, categorize vendors into risk tiers - critical, high, medium, and low - and track how many vendors shift from higher-risk tiers to lower ones over time. This approach provides a clear, data-driven way to demonstrate long-term improvements to executives and boards, showing that investments in vendor risk management are delivering tangible results.
Improving Your Scoring Model with Real Data
Keeping your scoring model accurate requires regular updates and refinements. Each time there's a vendor-related incident, document the root cause, entry point, and impact, then link this information back to the vendor's risk score. If a vendor labeled as "low risk" ends up causing a major breach, it's a sign your model may have overlooked key factors - like patch management or incident response capabilities.
To fine-tune your model, back-test it using historical data to see if it would have flagged earlier incidents. Adjust your scoring criteria as needed. Conduct targeted technical testing - such as vulnerability scans, penetration tests, or configuration reviews - on vendors whose scores have shifted significantly. This helps confirm whether a score change reflects actual security improvements or potential risks. Tools like Censinet RiskOps™ streamline evidence collection and benchmarking across similar vendors, making it easier to validate the accuracy and consistency of your scores [1].
Finally, integrate lessons from incidents and assessments into the scoring model. Regularly review thresholds and workflows during monthly operational meetings or quarterly risk committee sessions. This continuous feedback loop ensures your scoring system stays relevant and aligned with evolving threats, avoiding the pitfalls of static questionnaires.
Conclusion
Quantitative vendor risk scoring offers a structured way to tackle cybersecurity threats in healthcare. By translating complex risks into clear, actionable metrics, healthcare leaders can identify high-risk vendors, allocate resources effectively, and showcase measurable progress to executives and boards. This method goes beyond traditional static questionnaires, enabling continuous monitoring to catch potential threats before they escalate into breaches - protecting both patient safety and financial stability. Additionally, vendor risk scores create a shared language that unites security, compliance, clinical, and supply chain teams, ensuring everyone understands the risks associated with a vendor’s operations[2][3][6].
According to the Cloud Security Alliance, having a formal supplier risk rating process is essential for managing cyber risks in the healthcare supply chain[2]. By tiering suppliers based on their criticality - such as their impact on patient safety, access to sensitive data, and mission-critical services - organizations can focus their efforts where they are needed most[3].
If your organization still relies on static, qualitative assessments, it’s time to make the switch to a quantitative risk scoring system. Integrate this scoring framework with your procurement and contracting processes, use the scores to guide vendor selection and contract terms, and measure progress with tangible metrics[2][3][6]. The strategies outlined above emphasize the importance of moving from outdated qualitative methods to a more dynamic, measurable approach.
Censinet RiskOps™ supports this evolution by automating assessments while maintaining the necessary human oversight[1].
FAQs
How does vendor risk scoring help protect patient safety in healthcare?
Vendor risk scoring plays a crucial role in safeguarding patient safety by identifying and addressing cybersecurity risks within healthcare supply chains. By evaluating third-party vendors' capacity to securely manage patient data, protected health information (PHI), clinical systems, and medical devices, it helps minimize vulnerabilities that could result in data breaches or system disruptions.
This process enables healthcare organizations to ensure continuous care, protect sensitive information, and reduce risks that could negatively impact patient outcomes. The result is a more secure and dependable healthcare system.
Why is quantitative risk scoring more effective for managing vendor cybersecurity risks?
Quantitative risk scoring stands out because it relies on objective, measurable data to assess risks. This method removes the influence of personal bias, ensures uniform evaluations, and allows for real-time analysis. With clear metrics in place, healthcare organizations can make smarter, data-backed decisions to enhance cybersecurity across their supply chains.
In contrast to qualitative methods, which depend on subjective opinions, quantitative scoring offers the ability to benchmark and monitor progress over time. This makes it easier to pinpoint and address risks - like those tied to patient data or medical devices - more effectively, boosting both security and compliance efforts.
How can healthcare organizations use vendor risk scoring to strengthen cybersecurity?
Healthcare organizations can strengthen their cybersecurity defenses by incorporating vendor risk scoring into their daily operations. Tools like Censinet RiskOps™ allow organizations to move away from time-consuming manual processes by automating continuous risk assessments. These platforms align with industry standards and provide practical insights that can seamlessly integrate into procurement, onboarding, and vendor management workflows.
With vendor risk scoring, healthcare providers can take a proactive approach to spotting and addressing vulnerabilities within their supply chain. This helps safeguard sensitive patient data, protect clinical applications, and secure other essential assets.
Related Blog Posts
- Custom Vendor Risk Scoring: Key Benefits for HDOs
- Building Vendor Risk Frameworks for Healthcare IT
- 5 Common Challenges in Vendor Risk Scoring
- Ultimate Guide to Vendor Risk Scoring 2025
{"@context":"https://schema.org","@type":"FAQPage","mainEntity":[{"@type":"Question","name":"How does vendor risk scoring help protect patient safety in healthcare?","acceptedAnswer":{"@type":"Answer","text":"<p>Vendor risk scoring plays a crucial role in safeguarding patient safety by identifying and addressing <a href=\"https://www.censinet.com/blog/5-ways-to-reduce-3rd-party-cybersecurity-risks-per-18-experts\">cybersecurity risks</a> within healthcare supply chains. By evaluating third-party vendors' capacity to securely manage patient data, protected health information (PHI), clinical systems, and medical devices, it helps minimize vulnerabilities that could result in <a href=\"https://censinet.com/blog/taking-the-risk-out-of-healthcare-june-2023\">data breaches</a> or system disruptions.</p> <p>This process enables healthcare organizations to ensure continuous care, protect sensitive information, and reduce risks that could negatively impact patient outcomes. The result is a more secure and dependable healthcare system.</p>"}},{"@type":"Question","name":"Why is quantitative risk scoring more effective for managing vendor cybersecurity risks?","acceptedAnswer":{"@type":"Answer","text":"<p>Quantitative risk scoring stands out because it relies on objective, measurable data to assess risks. This method removes the influence of personal bias, ensures uniform evaluations, and allows for real-time analysis. With clear metrics in place, healthcare organizations can make smarter, data-backed decisions to enhance cybersecurity across their supply chains.</p> <p>In contrast to qualitative methods, which depend on subjective opinions, quantitative scoring offers the ability to benchmark and monitor progress over time. This makes it easier to pinpoint and address risks - like those tied to patient data or medical devices - more effectively, boosting both security and compliance efforts.</p>"}},{"@type":"Question","name":"How can healthcare organizations use vendor risk scoring to strengthen cybersecurity?","acceptedAnswer":{"@type":"Answer","text":"<p>Healthcare organizations can strengthen their cybersecurity defenses by incorporating vendor risk scoring into their daily operations. Tools like <strong>Censinet RiskOps™</strong> allow organizations to move away from time-consuming manual processes by automating continuous risk assessments. These platforms align with industry standards and provide practical insights that can seamlessly integrate into procurement, onboarding, and vendor management workflows.</p> <p>With vendor risk scoring, healthcare providers can take a proactive approach to spotting and addressing vulnerabilities within their supply chain. This helps <a href=\"https://censinet.com/perspectives/8-best-practices-for-patient-data-protection\">safeguard sensitive patient data</a>, protect clinical applications, and secure other essential assets.</p>"}}]}
Key Points:
How does quantitative vendor risk scoring work in healthcare?
- Assigns a 0–100 score representing a vendor’s overall cybersecurity posture
- Evaluates multiple factors, including controls, incidents, certifications, and resilience
- Creates apples-to-apples comparisons, eliminating subjective judgments
- Supports financial modeling, helping leadership quantify risk exposure
- Enables threshold-based decisions, like requiring remediation for scores below 70
What makes quantitative scoring more effective than qualitative scoring?
- Uses standardized, weighted criteria, not narrative opinions
- Improves evaluation consistency across teams and time periods
- Eliminates evaluator bias, making results more defensible
- Supports trend analysis for continuous improvement
- Aligns with cybersecurity frameworks, enhancing governance and reporting
What data sources feed accurate vendor risk scores?
- Security questionnaires and supporting evidence submitted by vendors
- Independent security ratings and public risk signals
- Technical vulnerability scans, SBOM data, and incident history
- Certifications, such as HITRUST, ISO, or SOC 2
- Benchmarking data from large vendor networks, such as Censinet’s 50,000+ vendor ecosystem
How does vendor risk scoring reduce cyber threats in healthcare?
- Reveals high-risk vendors quickly, enabling targeted remediation
- Highlights supply chain exposures, such as cloud and fourth-party risks
- Triggers policy-based actions, like pausing data exchange or escalating to compliance
- Supports financial impact modeling, strengthening executive buy-in
- Enhances ongoing monitoring, updating scores as conditions change
How do healthcare organizations implement scoring across the vendor lifecycle?
- Define key risk domains, including PHI access, clinical impact, and operational continuity
- Tier vendors by criticality, focusing resources on those with patient safety implications
- Embed scoring into procurement decisions, contracts, and onboarding
- Use continuous monitoring, updating scores with new vulnerabilities or incidents
- Leverage platforms, like Censinet RiskOps™, for automation and scale
How do organizations measure the success of vendor risk scoring programs?
- Remediation rates for high-risk vendors, such as percentage resolved within set timelines
- Score improvements over time, showing risk reduction
- Reduction in vendor-related cyber incidents across quarters
- Shorter detection and response times, driven by better visibility
- Financial impact avoidance, using breach cost models to quantify savings


