Vendor Security Policies vs. Industry Benchmarks
Post Summary
Healthcare organizations face increasing cybersecurity risks, with 92% experiencing attacks in the past year and 69% reporting patient care disruptions. A major weak point? Vendors handling sensitive data like ePHI (electronic protected health information). Many fail to meet updated 2025 HIPAA requirements, which now mandate stronger safeguards like multi-factor authentication (MFA), encryption, and regular security certifications.
Why this matters: Weak vendor policies expose healthcare systems to breaches, fines, and lawsuits. Industry benchmarks like NIST CSF 2.0, HPH CPGs, and HCIP provide clear standards to evaluate and improve vendor security practices. Yet, most vendors fall short, especially in areas like vulnerability management, medical device security, and network segmentation.
Key takeaways:
- Updated HIPAA rules (2025): No more "optional" controls - MFA, encryption, and biannual vulnerability scans are now mandatory.
- Common gaps: Vendors often fail to meet standards for encryption, incident response, and medical device security.
- Industry benchmarks: Frameworks like NIST CSF 2.0 and HCIP offer structured criteria to measure and improve vendor security.
- Solutions: Tools like Censinet RiskOps™ simplify vendor assessments, replacing manual processes with automated benchmarking.
Bottom line: Aligning vendor policies with benchmarks strengthens defenses, protects patient data, and ensures compliance with stricter regulations. Without this alignment, healthcare organizations risk operational disruptions and costly breaches.
What Vendor Security Policies Cover in Healthcare
Vendor security policies in healthcare lay out the guidelines for how third-party vendors must safeguard electronic protected health information (ePHI), ensure system availability, and adhere to regulations like HIPAA, HITECH, and related HHS directives. These policies set the baseline for security measures that vendors must follow if they handle, access, or transmit PHI, clinical applications, medical devices, or connected systems. Essentially, they clarify the roles of healthcare delivery organizations (HDOs) and vendors in implementing protections, responding to incidents, and reporting breaches. The ultimate aim? To reduce business interruptions and protect patient safety from risks tied to vendor-related outages or security breaches. Evaluating these policies against industry benchmarks often reveals significant areas for improvement.
These policies span the entire healthcare ecosystem, covering a wide range of vendors, including those providing EHR systems, telehealth services, billing solutions, medical devices, AI tools, and more. Managing these relationships can be daunting - platforms like Censinet illustrate the challenge of overseeing more than 50,000 vendor connections. These relationships involve data flows related to storage, transmission, remote access, and integration with clinical systems. Below is a closer look at how these policies translate security requirements into actionable measures.
Core Elements of Vendor Security Policies
Effective vendor security policies typically emphasize access control and identity management, requiring measures like unique user IDs, strong authentication protocols, role-based access, least privilege principles, and privileged account management. They also mandate timely termination of access for employees and subcontractors. Increasingly, multi-factor authentication (MFA) is becoming a standard for all systems that interact with ePHI, aligning with proposed updates to the HIPAA Security Rule.
When it comes to data protection and privacy, policies often require encryption for ePHI both in transit and at rest, secure configurations, data minimization, and adherence to privacy-by-design principles. These rules also address data retention and destruction, specifying how long vendors can store PHI, how to securely dispose of media, and how to segregate customer data in shared environments. However, the 2025 Healthcare Cybersecurity Benchmarking Study revealed that only 58% of organizations meet data protection and loss prevention standards under Health Industry Cybersecurity Practices (HICP), signaling a need for improvement in this critical area.
Incident detection, response, and reporting is another key focus. Policies require vendors to maintain formal incident response plans that cover detection, containment, recovery, and post-incident analysis. Contracts and Business Associate Agreements (BAAs) often include strict breach notification timelines - ranging from immediate alerts to within 24–72 hours of discovery - along with specific requirements for the content of these notifications. Business continuity and disaster recovery provisions are also essential, with policies often specifying recovery time objective (RTO) and recovery point objective (RPO) commitments, as well as redundancy and backup controls to minimize downtime for critical systems.
In addition, mature policies demand annual certifications, regular risk assessments, and ongoing vulnerability scans. Vendors are expected to maintain clear documentation to demonstrate compliance with HIPAA requirements.
Common Problems in Vendor Risk Management
Even with comprehensive policies, healthcare organizations frequently encounter challenges in implementing them. According to the 2025 Healthcare Cybersecurity Benchmarking Study, third-party risk management and asset management remain among the weakest areas. For instance, the "Vendor/Supplier Cybersecurity Requirements" goal under the HPH framework showed below-average compliance, indicating that many organizations lack robust, standardized vendor requirements.
Inconsistent standards and limited visibility into vendor practices add to these difficulties. Terry Grogan, CISO at Tower Health, described how, before adopting specialized tools, vendor risk assessments consumed significant resources. After implementing Censinet RiskOps, the organization was able to reallocate three full-time employees to other tasks. Grogan explained:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."
This highlights how manual processes, such as managing spreadsheets and questionnaires, can drain resources.
Another challenge is ensuring ongoing compliance as organizations shift toward continuous risk management models. The same benchmarking study found that while many healthcare organizations excel in the "Respond" and "Recover" functions, they struggle in proactive areas like "Identify" and "Mitigate." These gaps underscore weaknesses in vendor and supply-chain risk controls. James Case, VP & CISO at Baptist Health, shared how automation and collaboration have helped:
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with."
Additionally, security coverage for network-connected medical devices remains low, with only 48% of organizations meeting HICP standards. This is yet another area where vendor policies often fall short, leaving critical vulnerabilities unaddressed.
Industry Benchmarks for Healthcare Cybersecurity
When assessing vendor security policies, industry benchmarks act as a crucial guide to measure cybersecurity effectiveness. Healthcare organizations rely on established frameworks to evaluate their cybersecurity maturity and identify potential vulnerabilities. These benchmarks provide a structured way to manage risks across clinical systems, vendor relationships, and patient data. While vendor security policies can vary significantly in scope and thoroughness, industry benchmarks offer standardized criteria that ensure consistent evaluation and improvement. With the rise in cyberattacks, adopting these frameworks has become more important than ever.
The move toward mandatory controls is gaining momentum. Proposed updates to the HIPAA Security Rule for 2025/2026 align closely with these benchmarks by removing the distinction between "addressable" and "required" controls. Instead, measures like multi-factor authentication, encryption, semi-annual vulnerability scanning, and annual penetration testing will become mandatory [2]. This shift aims to enforce uniform security practices across all vendors.
NIST Cybersecurity Framework (CSF) 2.0

The NIST Cybersecurity Framework offers a flexible, risk-based structure built around five core functions: Identify, Protect, Detect, Respond, and Recover. Healthcare organizations use these functions to map assets and data flows, implement safeguards like encryption and access controls, monitor for threats, respond to incidents, and restore operations after disruptions. Its flexibility makes it suitable for a variety of healthcare settings, from small practices to large hospital networks with extensive vendor connections.
NIST CSF 2.0 places a strong emphasis on risk assessments, helping organizations catalog devices, data flows, and access points - key factors for maintaining vendor visibility. It also encourages continuous improvement through maturity models, allowing organizations to evolve from basic protections to advanced threat detection capabilities. Many healthcare providers adopt NIST CSF as a primary benchmark because it aligns well with HIPAA requirements and other healthcare-specific standards. These criteria also serve as a foundation for evaluating vendor practices, ensuring robust security oversight.
Healthcare Provider Cybersecurity Practices (HPH CPGs)
Building on NIST's principles, HPH CPGs provide a more healthcare-focused approach to managing vulnerabilities. Developed by the Health Sector Coordinating Council (HSCC), these guidelines divide security practices into basic and advanced goals across seven key areas. Basic goals address immediate vulnerabilities such as email security, access control, and vulnerability management - areas where vendor policies often fall short. Advanced goals focus on more sophisticated defenses, including threat hunting and supply chain risk management, tailored for organizations with mature security systems.
HPH CPGs come with implementation guides, maturity models, and self-assessment tools that score security efforts on a 0–5 scale. This step-by-step approach helps healthcare providers prioritize improvements based on their current capabilities and risk levels. These assessments are often part of annual audits, with a focus on high-impact measures like deploying DMARC for email security and implementing network segmentation to reduce breach risks. The framework also serves as an effective tool for benchmarking vendor security practices against healthcare-specific threats, offering clear standards for comparison.
Health Industry Cybersecurity Practices (HCIP)
HCIP zeroes in on seven critical areas: email and web security, anti-malware, medical device security, network management, access management, vulnerability management, and incident response. These practices address healthcare-specific needs, such as mandatory multi-factor authentication, encryption of electronic protected health information (ePHI) both at rest and in transit, and regular vulnerability scanning. For email security, HCIP recommends using DMARC, SPF, and DKIM to combat phishing attacks.
Medical device security guidelines include maintaining up-to-date device inventories, applying patches promptly, and segmenting IoT networks. For instance, isolating radiology imaging devices from electronic health record (EHR) systems can prevent hackers from moving laterally within the network during a breach. Network management practices highlight the importance of segmentation policies, continuous monitoring, and anomaly detection to spot suspicious activity early. These detailed, actionable recommendations make HCIP an essential benchmark for determining whether vendor security policies provide adequate protection for critical healthcare assets. These standards set a clear foundation for evaluating vendor practices, which will be explored further in the next section.
How Vendor Security Policies Compare to Industry Benchmarks
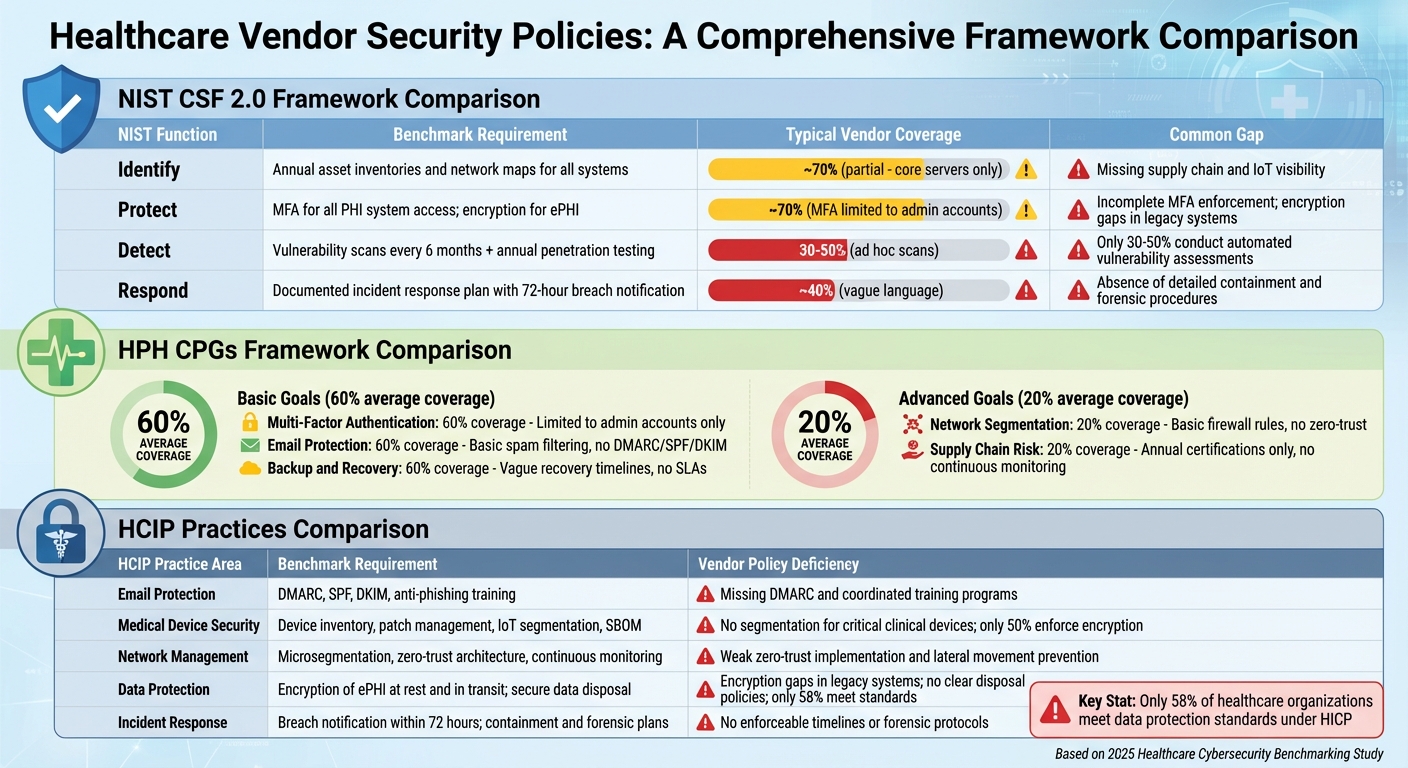
Vendor Security Policy Gaps vs Healthcare Industry Benchmarks Comparison
Vendor security policies in healthcare often fall short when measured against industry standards. While many vendors claim to "follow best practices" or "maintain secure systems", their policies frequently lack the detailed operational controls outlined in frameworks like NIST CSF 2.0, HPH CPGs, and HCIP. This lack of specificity leaves significant compliance gaps, making it essential to evaluate vendor policies against these benchmarks.
The updated HIPAA 2025 regulations now mandate encryption, multi-factor authentication (MFA), and regular vulnerability scans. Vendors must document compliance over a 12-month period to qualify for safe harbors and reduced penalties [4]. By removing the distinction between "addressable" and "required" safeguards, these updates establish a uniform baseline - one that many vendor policies currently fail to meet. Encryption, MFA, and vulnerability scanning are no longer optional, and benchmarking vendor policies against stringent industry standards can help healthcare organizations uncover vulnerabilities often hidden in vague documentation.
Vendor Policies vs. NIST CSF 2.0 Controls
Vendor policies tend to address basic access controls but often fall short of meeting the comprehensive requirements outlined in NIST CSF 2.0. This framework includes six core functions - Govern, Identify, Protect, Detect, Respond, and Recover - that require specific, documented controls and clear timelines. While vendors typically meet about 70% of basic access control requirements, their coverage for vulnerability management drops to just 30–50% [2][10].
| NIST CSF 2.0 Function | Benchmark Requirement | Typical Vendor Policy Coverage | Common Gap |
|---|---|---|---|
| Identify | Annual asset inventories and network maps for all systems | Documentation often limited to core servers, excluding supply chain and IoT devices | Missing comprehensive supply chain and IoT visibility |
| Protect | MFA for all PHI system access; encryption for ePHI at rest and in transit | Username/password methods; MFA limited to admin accounts; encryption applied inconsistently | Incomplete MFA enforcement; encryption gaps in legacy systems |
| Detect | Vulnerability scans every 6 months and annual penetration testing | Ad hoc scans; inconsistent penetration testing | Only 30–50% conduct automated vulnerability assessments |
| Respond | Documented incident response plan with 72-hour breach notification | Vague language; unclear timelines | Absence of detailed containment and forensic procedures |
One glaring issue is with the Identify function. HIPAA 2025 requires annual asset inventories and network maps, but vendors often limit their documentation to core systems, ignoring supply chain dependencies. Without full visibility, healthcare organizations face challenges in assessing their true risk exposure. This highlights the need for more thorough vendor evaluations, as explored further below.
Vendor Policies vs. HPH CPGs Goals
The HPH CPGs separate healthcare cybersecurity into basic and advanced goals. While vendor policies generally meet about 60% of basic goals - such as MFA, email protection, and anti-malware measures - they only address around 20% of advanced goals like penetration testing and supply chain risk management. This creates a concerning gap, leaving organizations with minimal foundational defenses and inadequate advanced protections.
| HPH CPGs Goal Category | Benchmark Expectation | Typical Vendor Coverage | Coverage Gap |
|---|---|---|---|
| Basic: Multi-Factor Authentication | MFA for all system access | Limited to admin accounts | Roughly 60% coverage; non-admin users often excluded |
| Basic: Email Protection | DMARC, SPF, DKIM, and anti-phishing training | Basic spam filtering; no coordinated training | Lacks advanced email security measures |
| Basic: Backup and Recovery | Regular backups with a 72-hour recovery target | Policies exist, but recovery timelines are vague | No enforceable service-level agreements |
| Advanced: Network Segmentation | Microsegmentation and zero-trust principles | Basic firewall rules with minimal segmentation | Only 20% coverage; zero-trust rarely implemented |
| Advanced: Supply Chain Risk | Continuous monitoring of vendor security posture | Relies on annual certifications without real-time monitoring | No ongoing assessments or visibility into broader risks |
While breach notification clauses are often included in vendor contracts, they rarely address continuous monitoring or dynamic risk assessments. Annual certifications offer only a static snapshot of security, which falls short of the HPH CPGs' emphasis on ongoing improvement. Similar gaps appear when comparing vendor policies to HCIP practices.
Vendor Policies vs. HCIP Practices
HCIP provides detailed recommendations for areas like email and web security, anti-malware, medical device security, network management, data protection, and incident response. Vendor policies often address email protection but show significant weaknesses in medical device security and network management. For instance, only half of vendors enforce device encryption, and few implement network segmentation to isolate IoT devices from electronic health record systems.
| HCIP Practice Area | Benchmark Requirement | Typical Vendor Policy | Specific Deficiency |
|---|---|---|---|
| Email Protection | DMARC, SPF, DKIM, and anti-phishing training | Basic spam filtering | Missing DMARC and coordinated training programs |
| Medical Device Security | Device inventory, patch management, IoT segmentation, and SBOM availability | Vague patching timelines; unclear secure configurations | No segmentation for critical clinical devices |
| Network Management | Microsegmentation, zero-trust architecture, and continuous monitoring | Basic firewall policies; limited segmentation | Weak zero-trust implementation and lateral movement prevention |
| Data Protection | Encryption of ePHI at rest and in transit; secure data disposal | TLS for data in transit; inconsistent encryption at rest | Encryption gaps in legacy systems; no clear disposal policies |
| Incident Response | Breach notification within 72 hours; containment and forensic plans | Vague timelines; incomplete response processes | No enforceable timelines or forensic protocols |
Medical device security remains a particularly weak area. HCIP recommends up-to-date device inventories, timely patch management, and strong IoT segmentation to prevent lateral movement during breaches. However, vendor policies often fail to meet these standards, forcing healthcare organizations to adopt segmentation measures on their own, often without adequate technical guidance.
To address these gaps, healthcare organizations can turn to tools like Censinet RiskOps™. These platforms align vendor responses with frameworks like NIST CSF, HPH CPGs, and HCIP, generating detailed gap analyses. This helps risk teams prioritize areas for improvement and negotiate stronger contracts using clear, data-driven insights. Such tools are invaluable for continuous vendor security assessments, ensuring healthcare organizations stay ahead of evolving threats.
sbb-itb-535baee
Closing the Gaps in Vendor Security Policies
Vendor security policies often leave critical gaps, creating significant risks for healthcare organizations, especially in areas like third-party risk management and supply chain security. While many vendors claim compliance, their policies frequently omit essential HIPAA 2025 controls such as encryption for electronic protected health information (ePHI), multi-factor authentication (MFA), and biannual vulnerability scans [2] [10] [5]. These missing safeguards can lead to regulatory penalties, costly breaches, and operational disruptions.
Supply chain vulnerabilities add another layer of risk. Many vendors rely on outdated technologies like basic VLANs and static firewalls, rather than adopting modern approaches like microsegmentation and zero-trust models. These outdated systems allow lateral movement within networks, putting electronic health records (EHRs), medical devices, and clinical applications at risk [2] [10]. Compounding the issue, vendors often lack continuous monitoring capabilities, meaning that annual certifications provide only a snapshot of security measures rather than ongoing visibility into emerging threats. To address these challenges, healthcare organizations need to rethink their risk management strategies.
A shift from reactive to proactive risk management is essential. Updated HIPAA regulations now require incident response plans capable of restoring systems within 72 hours, emphasizing the importance of continuous risk assessment and monitoring over periodic audits [10].
Healthcare organizations can take several steps to close these gaps:
- Strengthen business associate agreements to include requirements like 24-hour breach notifications, annual risk assessments, and verified security certifications.
- Mandate biannual vulnerability scans and annual penetration tests to ensure vendors comply with encryption, MFA, and network segmentation standards [3] [10] [6].
- Align vendor practices with industry standards such as the NIST Cybersecurity Framework 2.0, Healthcare Provider Cybersecurity Practices, and Health Industry Cybersecurity Practices to establish enforceable accountability.
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." – Matt Christensen, Sr. Director GRC, Intermountain Health [1]
Purpose-built healthcare platforms designed around industry benchmarks like NIST CSF 2.0 and HCIP offer a more effective way forward. These platforms integrate continuous monitoring and automated audits, eliminating the reliance on static questionnaires and manual spreadsheets. By enabling systematic gap closure and collaborative risk management across vendor networks, they address the unique demands of protecting patient data, securing medical devices, and managing supply chains. This real-time visibility is key to preventing breaches and ensuring a stronger security posture.
Using Censinet RiskOps™ for Benchmarking and Compliance
Censinet RiskOps™ simplifies the challenge of vendor benchmarking with its cloud-based risk exchange, which connects healthcare delivery organizations to a network of over 50,000 vendors. By replacing manual spreadsheets - often a major bottleneck in risk assessments - with automated tools, the platform allows organizations to tap into pre-built libraries of industry benchmarks. These benchmarks automatically evaluate vendors on critical security controls such as multi-factor authentication, encryption for ePHI, vulnerability scanning, and incident response capabilities [1].
One standout feature is the platform's automated assessment engine, which flags non-compliant vendors in real time. For example, it can identify vendors that fail to conduct mandatory annual asset inventories or neglect to perform vulnerability scans every six months, as required by evolving HIPAA standards. In addition, RiskOps™ provides continuous monitoring of vendor certifications, remediation efforts, and compliance, giving organizations an ongoing view of vendor risk.
Users have praised RiskOps™ for streamlining risk assessments and reducing manual workloads. By centralizing vendor data collection, the platform eliminates inefficiencies from repetitive tasks. Vendors can upload policies, certifications, and technical documentation just once and securely share them with multiple healthcare organizations. This approach not only minimizes assessment fatigue but also maintains high standards of security and compliance.
Beyond individual vendor evaluations, RiskOps™ offers portfolio-level benchmarking, enabling organizations to uncover systemic vulnerabilities across their entire vendor ecosystem. This broader perspective helps prioritize enterprise-wide security initiatives, ensuring resources are allocated effectively.
To further support compliance efforts, RiskOps™ generates audit-ready documentation aligned with HIPAA Security Rule requirements, NIST CSF 2.0 controls, and HCIP practices. Its centralized repository and collaborative features make it easier to track remediation efforts, deadlines, and risk decisions. This functionality is especially critical as healthcare organizations prepare for the Department of Health and Human Services' (HHS) upcoming regulations, set to take effect in late 2025 with enforcement beginning in 2026 [2][6][11].
Conclusion
Aligning vendor security policies with established industry standards isn't just a box to check - it's a critical step in safeguarding patient safety and maintaining operational stability in U.S. healthcare. The disconnect between vendor assurances and the actual requirements of frameworks like NIST CSF 2.0, HPH CPGs, and HCIP introduces serious vulnerabilities. Consider this: over two-thirds of major healthcare cyber incidents directly harm patient care, and the financial fallout from breaches often reaches into the millions [6][8].
Bridging these gaps shifts organizations from reacting to threats to actively preventing them. The 2025 Healthcare Cybersecurity Benchmarking Study highlights this: healthcare providers that align closely with frameworks like NIST CSF 2.0 report fewer critical incidents and slower growth in cybersecurity insurance premiums compared to those that fall short [7][9]. When vendors meet key standards - such as encryption protocols, multi-factor authentication, and robust incident response plans - the entire healthcare network benefits from stronger, more reliable security.
Brian Sterud, CIO at Faith Regional Health, puts it succinctly: "Benchmarking against industry standards helps organizations advocate for the right resources and ensures they are leading where it matters" [1]. This reinforces the idea that these frameworks aren't just technical checklists - they're essential tools for guiding strategic security investments and holding vendors accountable.
Addressing these gaps requires more than compliance; it demands continuous oversight of vendor practices. As HIPAA regulations evolve to impose stricter requirements for vendor security, monitoring, and breach response [3][4], healthcare organizations must view alignment with benchmarks as an ongoing effort. Implementing controls to mitigate ransomware, prevent data theft, and minimize downtime for critical systems directly supports patient care by ensuring that essential tools like EHRs and medical devices are always available when needed [2][6].
For healthcare security leaders, aligning vendor policies with benchmarks isn't just about avoiding penalties or outages - it’s about protecting patient trust and reducing financial exposure. The cost of proactive vendor management and remediation pales in comparison to the devastating impact of a major third-party breach [2][4][6]. By leveraging frameworks like NIST CSF 2.0, HPH CPGs, and HCIP, healthcare organizations can close the gaps that threaten both compliance and quality care, securing a safer future for all.
FAQs
How do vendor security policies influence patient care in healthcare organizations?
Vendor security policies are essential for safeguarding sensitive patient information, reducing cybersecurity threats, and keeping healthcare systems running smoothly. These policies act as a barrier against data breaches that could jeopardize patient privacy or disrupt critical clinical operations.
When crafted to meet established industry standards, these policies enhance the cybersecurity defenses of healthcare organizations. This not only ensures compliance with healthcare regulations but also promotes safe, continuous patient care - building trust and confidence in the healthcare system.
What challenges do healthcare organizations face when aligning vendor security policies with industry standards?
Healthcare organizations face a range of challenges when working to align vendor security policies with established industry standards. Among these hurdles are the varying levels of risk management readiness across vendors, a shortage of internal resources to conduct thorough evaluations, and the difficulty of consistently applying industry benchmarks in a practical, actionable manner.
On top of that, the ever-changing landscape of cybersecurity threats and shifting regulations often complicate efforts to keep vendor policies current and aligned with best practices. Overcoming these issues calls for a more efficient risk assessment process and close collaboration with vendors to ensure the protection of patient data and the security of operational systems.
Why is continuous monitoring essential for maintaining vendor security compliance in healthcare?
Continuous monitoring plays a key role in maintaining vendor security compliance in healthcare. It allows organizations to identify and fix vulnerabilities as they arise, ensuring they stay aligned with industry standards and can quickly address new threats.
Through ongoing monitoring, healthcare organizations can better protect sensitive patient data, like PHI, and secure critical systems, such as clinical applications, medical devices, and supply chains. This approach not only reduces risks but also strengthens trust in their vendor partnerships.


