Virtual Reality Healthcare Vendors: Risk Management for Immersive Medical Technologies
Post Summary
Virtual reality (VR) is reshaping healthcare by improving therapy, training, and rehabilitation. However, it introduces risks like data breaches, patient safety concerns, and compliance challenges. Healthcare organizations must address these risks by evaluating vendor security, protecting sensitive biometric data, and ensuring regulatory compliance. Key strategies include:
- Data Protection: Use encryption, role-based access, and multi-factor authentication to secure biometric and patient data.
- Device Security: Regular updates, restricted permissions, and secure network integration minimize vulnerabilities.
- Governance and Training: Establish policies, train staff, and create a risk management framework tailored to VR.
- Vendor Assessment: Conduct thorough evaluations, including security audits and incident response plans.
Tools like Censinet RiskOps™ streamline vendor assessments, automate processes, and provide continuous monitoring to manage VR risks effectively. As VR adoption grows, proactive risk management is essential to protect patient safety and data integrity.
Cybersecurity and Compliance Risks of VR Healthcare Vendors
VR technology brings a new layer of complexity to healthcare security, presenting challenges that traditional risk frameworks weren’t built to handle. With features like advanced sensors, cloud integration, and connections to clinical systems, VR expands the potential for cyberattacks. This broader attack surface makes it crucial to identify and address these risks to protect patient data and meet compliance standards. A closer look reveals specific vulnerabilities in areas like data privacy, device security, and regulatory compliance.
Data Privacy and Biometric PHI Exposure
The expanded attack surface of VR systems raises serious questions about data privacy. These systems continuously collect biometric data, which is classified as Protected Health Information (PHI) under HIPAA. When this data is stored in cloud environments with weak encryption or lax access controls, it becomes a prime target for breaches [1][3][4]. Adding to the complexity, AI and machine learning models can analyze this biometric data to infer sensitive health conditions that patients may not have disclosed. This creates an urgent need for advanced protection methods to safeguard this highly sensitive information.
Immersive Manipulation and Patient Safety Concerns
The immersive nature of VR comes with risks that go beyond conventional cybersecurity threats. For example, compromised VR systems used in therapeutic settings could deliver altered or malicious content. This could lead to psychological distress, physical harm from disorientation, or even a breakdown in treatment effectiveness. Attackers might exploit these vulnerabilities to tamper with clinical protocols, introduce harmful stimuli, or disrupt rehabilitation programs. These scenarios directly threaten both patient safety and the success of medical treatments.
Device, Network, and Integration Vulnerabilities
VR devices often come with insecure default settings, delayed software updates, and weak authentication measures. These flaws can allow attackers to move laterally across connected systems. Many healthcare organizations link VR headsets to networks that house electronic health records (EHRs) and other essential systems, creating a pathway for cyberattacks. Take, for instance, the December 2021 ransomware attack on Eye Care Leaders, which compromised 3.7 million patient records and resulted in over $4 million in settlements [5]. Similarly, the April 2022 breach at OneTouchPoint affected more than 2.6 million individuals across multiple providers [5]. These real-world incidents highlight how security gaps in vendor-connected devices can open the door to large-scale cyberattacks.
Regulatory and Governance Challenges
Technical vulnerabilities aren’t the only hurdle - governance issues also complicate risk management. Many healthcare organizations struggle to align VR technologies with existing regulations like HITECH. Moreover, few have developed vendor management policies that specifically address the unique risks associated with VR and its use of biometric data. This lack of tailored governance leaves organizations exposed, as traditional risk assessment methods often fall short in addressing the challenges posed by these emerging technologies.
Building a Risk Assessment Framework for VR Vendors
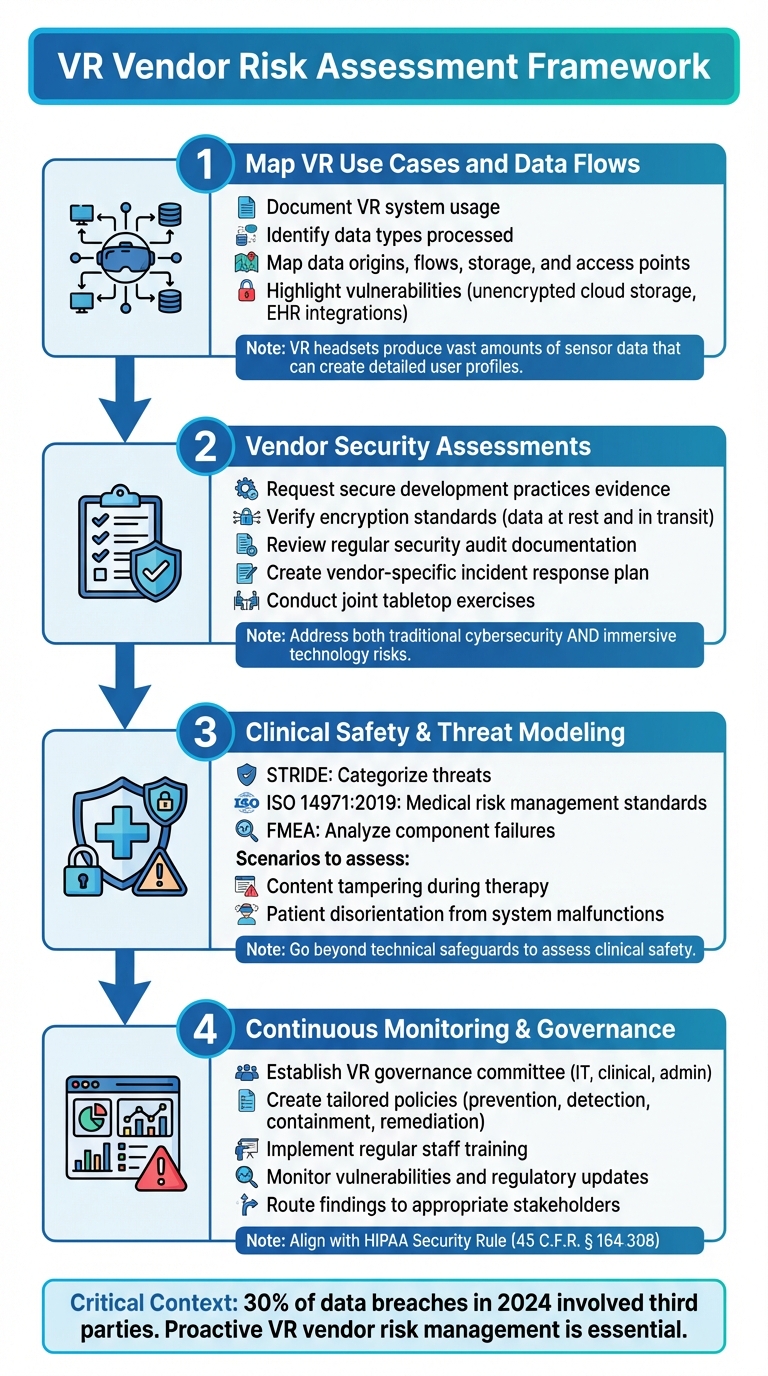
VR Healthcare Vendor Risk Assessment Framework: 4-Step Process
Healthcare organizations need a clear and structured way to evaluate VR vendors. A well-designed framework not only identifies potential vulnerabilities but also ensures that security measures align with patient safety and regulatory requirements. This approach takes into account the unique aspects of immersive technologies, addressing challenges that traditional vendor assessments might overlook.
Mapping VR Use Cases and Data Flows
The first step is to document how VR systems will be used and the types of data they’ll process. VR headsets rely heavily on sensor data, producing vast amounts of user information [3]. This data can be exploited to create detailed user profiles [3]. To mitigate risks, map out data origins, flows, storage locations, and access points. This process can highlight weak spots, such as unencrypted cloud storage or integrations with electronic health record (EHR) systems - both of which could be exploited by attackers.
Vendor Security Assessments and Evidence Collection
Evaluating VR vendors requires a tailored approach that addresses both traditional cybersecurity risks and those specific to immersive technologies. Request evidence of secure development practices, encryption standards for data at rest and in transit, and documentation of regular security audits.
A thorough assessment should also include creating a vendor-specific incident response plan. This plan should outline the steps to take in the event of a breach, including who to notify, which systems may be affected, and how to communicate with patients, stakeholders, and regulators. To strengthen preparedness, conduct joint tabletop exercises with vendors to simulate breach scenarios. These exercises can help pinpoint weaknesses in coordination and response strategies [3].
Clinical Safety and Immersive Threat Modeling
Immersive technologies introduce unique risks that traditional cybersecurity frameworks may not fully address. Beyond technical safeguards, it’s essential to assess clinical safety. Threat modeling can help identify and mitigate risks tied to VR usage in healthcare settings.
For instance, use the STRIDE framework to categorize threats, ISO 14971:2019 to meet medical risk management standards, and Failure Mode and Effects Analysis (FMEA) to analyze potential component failures that could affect patient safety. These methodologies can help anticipate scenarios such as content tampering during therapy sessions or patient disorientation caused by system malfunctions, ensuring these issues are addressed before they impact clinical care.
Risk Mitigation Strategies for VR in Healthcare
To ensure the safe integration of VR technologies in healthcare, organizations need to implement strategies that address vulnerabilities and protect patients, data, and systems.
Protecting PHI and Biometric Data
VR systems often collect sensitive biometric data, making it essential to enforce strict security measures. Start by implementing role-based access controls to ensure users can only access the information necessary for their role. Combine this with multi-factor authentication (MFA) to add a robust layer of protection against unauthorized access [1]. These measures can significantly reduce the risk of data breaches. Furthermore, securing the devices and networks that support VR systems is just as important as protecting the data itself.
Securing VR Devices and Networks
To keep VR devices secure, ensure they are regularly patched and updated to address known vulnerabilities. Limit access to developer mode and apply granular permissions to restrict device usage to authorized personnel only [4]. While technical defenses are essential, they need to be reinforced by effective governance and comprehensive training to address broader risks.
Improving Governance, Policies, and Training
Strong governance and well-trained staff are the backbone of effective VR risk management. Establish a VR governance committee that includes IT experts, clinical staff, and administrative leaders [8]. This committee can create policies tailored to your organization’s needs, ensuring they are actionable, measurable, and in line with regulatory requirements [9]. Policies should address all aspects of security breaches, including prevention, detection, containment, and remediation, as outlined in the HIPAA Security Rule (45 C.F.R. § 164.308).
Equally important is regular training for all team members. This should include both technical security practices and clinical safety protocols, ensuring that everyone understands their role in maintaining a secure and safe VR environment. Together, governance, policies, and training form a comprehensive approach to mitigating risks associated with VR in healthcare.
sbb-itb-535baee
Managing VR Risk with Censinet
When it comes to managing VR vendors, integrating them into your existing risk management program can simplify the process significantly. With Censinet RiskOps™, VR healthcare vendors can be seamlessly incorporated into your third-party risk management workflows. This centralized approach ensures that VR vendors are held to the same high standards as any other third party managing sensitive patient data. It also aligns VR vendor evaluations with your overall risk management strategy, making oversight more consistent and effective.
Integrating VR Vendors into Third-Party Risk Programs
Censinet RiskOps™ acts as a central hub for all things related to VR vendor assessments, documentation, and compliance tracking. Everything - security questionnaires, evidence documents, integration details, and compliance status - is collected and managed within a single platform. This setup ensures all VR vendors are assessed using standardized criteria while addressing the unique security challenges posed by VR technologies.
Automating VR Vendor Assessments with Censinet AITM
Censinet AITM takes efficiency to the next level by automating the vendor assessment process. What might normally take weeks of back-and-forth with questionnaires can now be completed in seconds. The AI summarizes vendor evidence and documentation, captures important integration details, and highlights potential fourth-party risk exposures - such as those from third-party cloud providers or hardware manufacturers. For VR vendors with intricate supply chains, this visibility into fourth-party risks is crucial. Additionally, the system generates detailed risk summary reports, cutting down on the manual workload for your risk management team.
Continuous Monitoring and AI-Driven Governance
As VR technology evolves, so do the risks tied to it. Censinet AI ensures continuous oversight by monitoring vulnerabilities, regulatory updates, and remediation efforts across your entire VR vendor network. The platform routes critical findings to the appropriate stakeholders, including members of your AI governance committee, for review and action. With an easy-to-navigate AI risk dashboard, your team can access real-time data on policies, risks, and tasks, ensuring the right issues are addressed by the right people at the right time. This level of accountability supports the growth and scalability of your VR program without compromising security.
Conclusion
As VR technology continues to reshape healthcare delivery, it also introduces a host of cybersecurity and compliance challenges. With nearly 30% of data breaches in 2024 involving third parties [5], healthcare organizations must adopt a structured and proactive approach to managing VR vendor relationships. The unique risks tied to biometric data, immersive manipulation threats, and intricate device integrations demand an approach tailored specifically to VR environments.
To tackle these challenges, organizations need to focus on mapping data flows, conducting thorough vendor assessments, and implementing continuous monitoring systems. Regulatory requirements, such as those from the FDA and EU MDR, now emphasize the importance of comprehensive risk management for VR applications [2][6][7][10]. These practices are critical for seamlessly incorporating VR vendors into broader risk management frameworks.
Censinet RiskOps™ offers a streamlined way to integrate VR vendors into existing third-party risk management programs. With tools like Censinet AITM, which automates assessments and provides insights into fourth-party risks across complex VR supply chains, healthcare teams can address risks more effectively while maintaining a high level of detail and accuracy.
Continuous monitoring remains a cornerstone of managing the ever-evolving risks associated with VR technology. Platforms like Censinet utilize AI-driven governance to ensure critical findings are directed to the right stakeholders, all while maintaining real-time visibility across networks. This approach not only protects sensitive patient data but also ensures compliance with healthcare regulations, enabling VR programs to grow securely and responsibly. By following this structured strategy, healthcare organizations can safeguard patient data and support the secure integration of VR into their operations.
FAQs
What are the key risks of using virtual reality in healthcare?
Virtual reality (VR) is opening up new opportunities in healthcare, but it’s not without its challenges. Some of the key risks include cybersecurity threats, where sensitive patient data could be exposed, and privacy issues, particularly around how personal health information is gathered and handled. On top of that, there are physical risks to consider, such as simulator sickness, seizures, or even injuries caused by improper use of VR hardware.
Recognizing these challenges allows healthcare organizations to take the right precautions, ensuring VR technologies are used in a way that safeguards both patients and providers.
How can healthcare organizations protect biometric data in virtual reality (VR) systems?
To keep biometric data secure in VR systems, healthcare organizations need to prioritize strong access controls. This means carefully managing who can view or alter sensitive information. On top of that, all data should be encrypted, whether it's stored or being transmitted, to block unauthorized access.
Regular security audits and assessments play a key role in spotting and addressing potential weak points. Keeping software up to date with the latest security patches is another must. Equally important is staff training on cybersecurity best practices, including proper methods for user authentication and authorization. These measures not only protect sensitive biometric data but also help organizations stay in line with privacy regulations.
How can healthcare organizations effectively evaluate VR vendors for security and compliance risks?
To thoroughly assess VR vendors, begin by requesting comprehensive security documentation and examining essential compliance reports like SOC 2, ISO 27001, or HITRUST. Take a close look at the vendor’s security controls, certifications, and any corrective actions they’ve undertaken. Pay extra attention to vendors managing sensitive data or critical services, ensuring they align with your organization’s security and privacy expectations.
Additionally, evaluate vendors during onboarding, maintain ongoing monitoring of their security practices, and establish clear incident response protocols. Implement contractual security requirements to hold vendors accountable and reduce risks associated with immersive medical technologies.


