AI in Phishing Response: Healthcare Use Cases
Post Summary
Phishing attacks are a growing threat in healthcare, targeting sensitive patient data and disrupting critical operations. AI-powered solutions are transforming how organizations detect and respond to these attacks by analyzing email content, user behavior, and system interactions. Here's a quick breakdown of how AI is improving phishing defenses in healthcare:
- Pre-Delivery Detection: Stops phishing emails before they reach inboxes by analyzing content, sender behavior, and links. AI models tailored for healthcare achieve up to 97% accuracy.
- Post-Delivery Analytics: Monitors inboxes for threats that bypass initial filters, using user behavior patterns and anomaly detection to flag risks.
- Automated Incident Response: Speeds up threat containment with real-time actions like quarantining emails, blocking domains, and resetting credentials.
These tools are essential as attackers increasingly use AI to create sophisticated phishing campaigns. By integrating AI with healthcare systems like EHR platforms and identity management tools, organizations can protect patient data, comply with regulations like HIPAA, and minimize disruptions to care delivery.
Key fact: Over 82% of phishing emails now use AI-generated content, making traditional defenses less effective. AI-driven solutions provide the precision and speed needed to counteract these evolving threats.
1. Pre-Delivery Phishing Detection
Pre-delivery phishing detection leverages AI and machine learning to stop harmful emails before they land in clinicians' inboxes. These advanced systems scrutinize email content, sender behavior, URLs, and attachments in real time at the email gateway. This proactive approach is especially important in healthcare, where 82.6% of phishing emails now use AI-generated content that can easily slip past older security measures[5].
Detection Accuracy
A study conducted in 2025 examined 18,354 emails, including synthetic messages crafted by ChatGPT-4o and Llama-3.1. The results showed that healthcare-focused AI models achieved an impressive 96.4% to 97.3% accuracy, with ROC-AUC scores exceeding 99%. These models used BERT-based embeddings combined with ensemble classifiers to deliver such precision[1]. General phishing detectors often fail to capture the subtle differences in healthcare-specific emails, such as patient portal notifications, lab results, or medical device alerts. This can lead to either missing threats or disrupting essential care workflows.
Integration with Healthcare Systems
For pre-delivery detection to be effective, it must seamlessly integrate with the platforms clinicians rely on daily, such as Microsoft 365 and Google Workspace. The system also needs to understand EHR workflows, including appointment reminders, e-prescribing notifications, and lab results, so it can differentiate legitimate messages from platforms like Epic or Cerner from sophisticated phishing attempts[2].
Third-party visibility is another crucial factor. Healthcare organizations work with vast vendor networks for billing, telehealth, imaging, and supply chain operations, making trusted domains potential targets for impersonation. Solutions like Censinet RiskOps™ enhance pre-delivery detection by centralizing vendor risk data and mapping PHI exposure. This allows organizations to determine which external senders require stricter scrutiny.
Matt Christensen, Sr. Director GRC at Intermountain Health, emphasizes: "Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare."
Response Speed
Clinicians depend on near-instant email and messaging to provide timely patient care, so pre-delivery systems must process emails in milliseconds to a few seconds. AI engines achieve this speed by employing lightweight inference pipelines and risk-based decision-making. For instance, clearly malicious emails are blocked immediately, medium-risk messages are placed in soft quarantine for quick review, and low-risk emails are delivered with warning banners. The system also caches reputations and uses incremental updates, ensuring decisions are based on pre-learned patterns for near-real-time performance[2][6]. This approach maintains the flow of communication while effectively screening for AI-generated phishing at scale.
Regulatory Compliance
To meet HIPAA requirements, email security services must include a BAA, strong encryption, minimal data processing through de-identification, and comprehensive logs of all activity[1][2]. Platforms like Censinet RiskOps™ assist by centralizing compliance assessments and managing risks related to email, third-party vendors, and supply chains involving PHI. Additionally, pre-delivery detection systems should integrate with incident response and privacy breach protocols, ensuring that blocked threats are documented and analyzed as part of a broader risk management strategy[3][4]. These measures lay the groundwork for a strong defense against phishing attacks while supporting post-delivery detection and response efforts.
2. Post-Delivery Detection and User Behavior Analytics
While pre-delivery measures act as the first line of defense, post-delivery detection takes over to monitor inbox content and catch any threats that slip through initial filters. Rather than blocking emails at the gateway, AI-driven tools keep a vigilant eye on messages already delivered to mailboxes - like those in Microsoft 365 or Google Workspace. These tools continuously analyze content, sender behavior, URLs, attachments, and even user interactions after delivery. This approach is crucial for addressing vulnerabilities tied to human behavior.
Detection Accuracy
Post-delivery detection systems in healthcare are impressively precise, with detection accuracies exceeding 96% and ROC-AUC scores reaching as high as 99% by focusing on behavioral patterns instead of relying solely on static rules[1]. These systems are designed to pick up contextual signals - like specific medical terminology, urgency cues, and subtle language patterns - that attackers often exploit when targeting healthcare professionals. User and Entity Behavior Analytics (UEBA) enhances this process by flagging anomalies, such as a phishing link click followed by suspicious login attempts or unusual access to large volumes of patient records. These alerts enable swift responses to potential threats[6].
Integration with Healthcare Systems
For post-delivery detection to work effectively, it needs to blend seamlessly with the tools and systems healthcare professionals use daily. Key integrations include identity and access management platforms like Azure AD and Okta, which link phishing events to account logins and multi-factor authentication prompts in real time[6]. Similarly, EHR and EMR systems such as Epic or Cerner benefit from AI monitoring, which can detect unusual record queries or irregular data exports after a phishing incident[3]. Tools like Censinet RiskOps™ further enhance this process by consolidating vendor risk data and third-party assessments, helping organizations evaluate risks tied to sender profiles and access to sensitive patient information. These integrations ensure that responses are both swift and effective, a topic explored further below.
Response Speed
Speed is critical when responding to threats, particularly in the healthcare sector where patient care is at stake. Unified AI platforms are designed to minimize detection and response times, often reclassifying and quarantining malicious emails in seconds or minutes after a user report or a high-risk score is flagged[6]. Automated actions, such as quarantining similar emails across multiple inboxes, adding warning banners, resetting passwords for compromised accounts, or temporarily restricting access to systems with sensitive data, help contain threats quickly. By tailoring response policies to the needs of clinical and administrative staff, these systems ensure that operations continue with minimal disruption.
Regulatory Compliance
Healthcare organizations must meet strict regulatory requirements, like those outlined in HIPAA, which mandate technical safeguards to protect sensitive patient information (PHI)[6]. Post-delivery detection and UEBA play a key role in meeting these requirements by providing detailed audit trails of email threats, user actions, automated responses, and access anomalies. These tools also support risk-based access controls, such as adaptive authentication or step-up verification for risky activities, aligning with HIPAA's security rule. Platforms that centralize telemetry, alerts, and reporting streamline evidence collection for compliance purposes. Additionally, healthcare-focused solutions like Censinet offer capabilities to document vendor risk profiles, incident histories, and mitigation strategies, contributing to a broader governance framework. Together, these measures form a robust, AI-powered cybersecurity foundation tailored to the unique needs of the healthcare industry.
3. Automated Incident Triage and Response
Once a phishing threat is identified - whether before or after reaching its target - the focus shifts to prioritizing alerts and taking quick action. Manual triage simply can’t keep up. Automated triage steps in by pulling data from email, endpoint, and network logs, automatically linking, categorizing, and ranking incidents. It determines which users received a suspicious email, who interacted with links or attachments, and assigns a risk score based on factors like the user’s role, message details, sender credibility, and threat intelligence. From there, automated workflows can quarantine emails, block harmful domains or URLs, isolate compromised devices, and alert the appropriate security and compliance teams.
Detection Accuracy
Building on earlier detection efforts, automated triage sharpens the process of prioritizing and managing incidents. In healthcare, AI models tailored to industry-specific needs have shown impressive results, with detection accuracy exceeding 96% and ROC-AUC scores nearing 99% [1]. These models are trained to distinguish legitimate clinical communications from advanced phishing attempts, making them particularly effective in this context. To maintain high performance, organizations should track key metrics like true and false positive rates, the precision of flagged incidents, and the average response time. Regular validation through controlled phishing tests and incident reviews ensures the system remains reliable.
Integration with Healthcare Systems
Automated triage doesn’t operate in isolation - it integrates with key healthcare systems to provide a comprehensive response. These AI-driven tools connect seamlessly with platforms like Microsoft 365, Google Workspace, EHR access logs, identity and access management systems, endpoint protection, SIEM/SOAR platforms, and ticketing systems. This integration enables the system to detect patterns across multiple channels, such as phishing links followed by unusual EHR activity, and respond with measures like enhanced authentication or session restrictions. Many integrations rely on standardized protocols commonly used in U.S. healthcare, including SSO/SAML for identity, SCIM for provisioning, and HL7/FHIR for clinical data. Tools like Censinet RiskOps™ enhance these capabilities by consolidating risk data from email systems, clinical applications, and medical devices, allowing for more nuanced triage scoring. The aim is to apply safeguards - like step-up multi-factor authentication or session containment - without disrupting essential clinical workflows.
Response Speed
In healthcare, speed is everything when dealing with phishing threats. Delays can lead to ransomware attacks, data breaches, or interruptions to patient care. Advanced AI platforms have drastically cut detection and response times from hours - or even days - to just minutes or seconds. Automated workflows can remove malicious emails from inboxes, block related domains, and isolate affected devices almost instantly. These systems can also group similar phishing attempts, quarantine threats, and initiate password resets in record time. Key metrics to monitor include the time from a user’s interaction with a phishing email to its removal and the interval from detecting unusual activity to implementing access restrictions.
Regulatory Compliance
Automated triage and response processes must align with HIPAA and other U.S. healthcare privacy and security regulations. AI systems play a critical role by documenting every step of an incident - from the arrival of a phishing email to its detection, user interactions, and the automated actions taken. This detailed timeline supports root-cause analysis, HIPAA breach risk assessments, and, if necessary, notifications to patients or regulatory agencies. It’s vital that AI systems managing PHI operate under proper Business Associate Agreements (BAAs) and provide explainable, reviewable decision-making processes, especially when sensitive data access is involved. By flagging incidents that may require regulatory reporting and alerting privacy or compliance officers, these systems ensure human oversight remains intact. Additionally, they simplify audits by generating standardized reports and maintaining unalterable logs for investigations.
sbb-itb-535baee
Pros and Cons
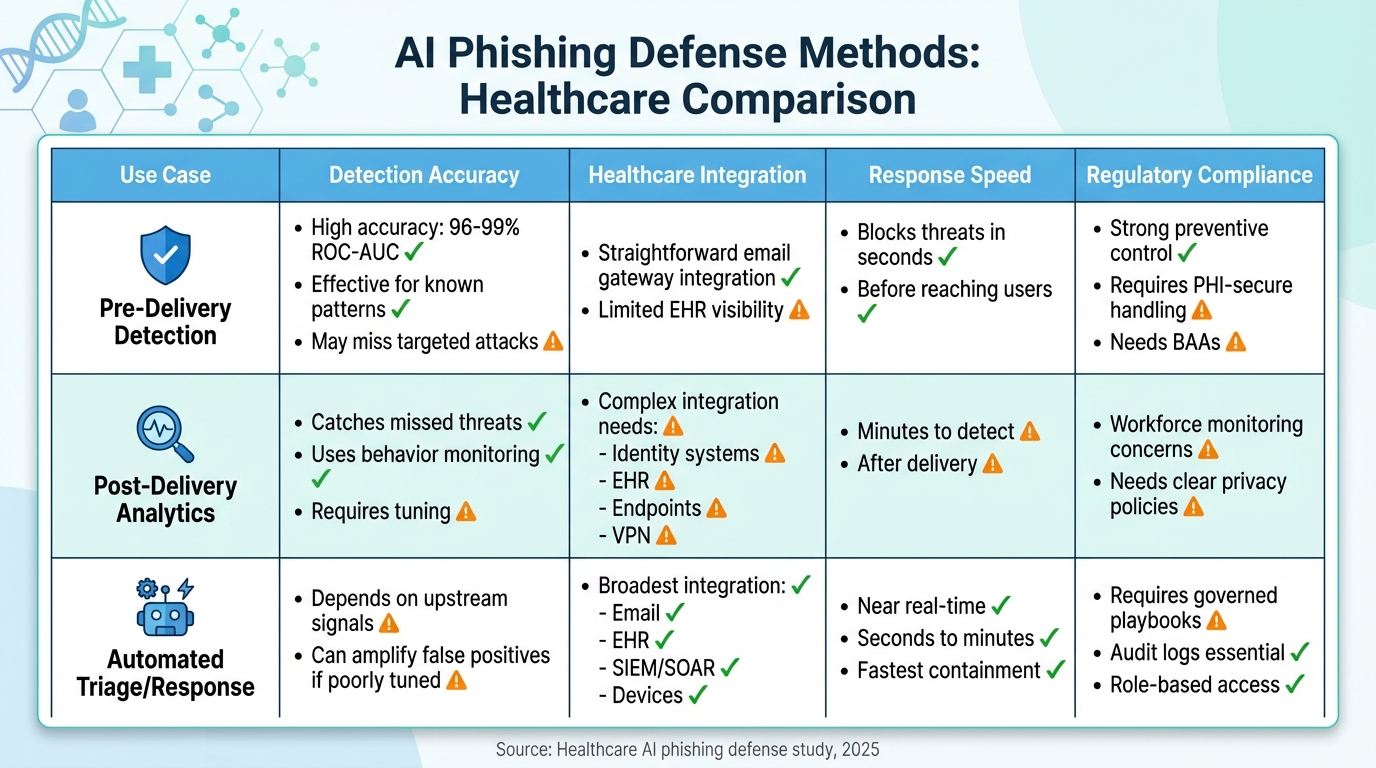
AI Phishing Defense Methods in Healthcare: Accuracy, Integration, Speed & Compliance Comparison
After reviewing the AI approaches in healthcare, here’s a breakdown of their key strengths and challenges.
Each method offers distinct advantages and trade-offs when applied in U.S. healthcare systems. Pre-delivery detection is highly effective at stopping threats before they even reach clinicians, boasting an impressive accuracy rate of 96% and a 99% ROC-AUC score [1]. This scalable solution significantly reduces exposure to harmful content and lowers click-through rates. However, it’s not without flaws. Over-aggressive settings can lead to false positives, which might quarantine legitimate communications like lab results, referrals, or vendor updates. This could delay care and cause frustration among healthcare staff [1][11]. While its integration with email systems is relatively simple, this approach struggles with more sophisticated, low-volume attacks that mimic trusted sources and offers limited visibility into EHR workflows [11].
Post-delivery detection and user behavior analytics act as a safety net, catching threats that slip past pre-delivery filters. By monitoring unusual clicks, logins, and device activity, it enhances overall security and provides an opportunity for targeted training based on actual risky behaviors [11][8]. However, this method comes with its own set of challenges. It requires deep integration with identity systems, EHR logs, and endpoint telemetry, which can be complex and occasionally less precise in shared accounts [6][12]. Clinicians, often pressed for time, may overlook warnings unless the user interface and workflow integration are optimized [12].
Automated incident triage and response offers lightning-fast reactions, reducing response times from hours to mere seconds. Features like real-time quarantines, domain blocking, and credential resets are particularly effective. Unified AI platforms also help reduce false positives and ease the burden on security operations centers (SOCs) by correlating data across email, endpoints, and networks [6][7]. However, over-automation can inadvertently block legitimate access to critical systems, which could disrupt care delivery [7][12]. To mitigate this, organizations must implement tiered response levels, provide exception paths tailored for clinicians, and rigorously test systems before automating high-impact processes [6].
From a regulatory compliance standpoint, all three approaches must align with HIPAA Security Rule safeguards, including audit and access controls [1][6]. Protecting PHI remains a top priority. Pre-delivery detection offers strong preventive measures but requires encryption and solid Business Associate Agreements (BAAs) [1][11]. Post-delivery analytics, while effective, raises privacy concerns around workforce monitoring, necessitating clear policies and adherence to HHS guidelines on balancing security and privacy [6][10]. Automated triage and response must follow governed playbooks, enforce role-based access controls, and maintain detailed logs to meet HIPAA audit requirements and support incident investigations under HITECH [6][7]. Recent initiatives from HHS and the FDA emphasize the importance of transparent, risk-managed AI systems. While these directives provide clarity, they also add governance requirements, such as explainability and bias monitoring, for all three methods [10].
| Use Case | Detection Accuracy | Healthcare Integration | Response Speed | Regulatory Compliance |
|---|---|---|---|---|
| Pre-Delivery Detection | High (96–99% ROC-AUC) for known patterns; may miss targeted attacks [1] | Straightforward email gateway integration; limited EHR visibility [11] | Blocks threats in seconds before reaching users [11] | Strong preventive control; requires PHI-secure handling and BAAs [1][11] |
| Post-Delivery Analytics | Catches missed threats via behavior monitoring; requires tuning [6][11] | Complex - needs identity, EHR, endpoint, VPN integration [6][12] | Minutes to detect risky actions after delivery [12][8] | Raises workforce monitoring concerns; needs clear privacy policies [6][10] |
| Automated Triage/Response | Depends on upstream signals; amplifies false positives if poorly tuned [6] | Broadest - integrates email, EHR, SIEM, SOAR, devices [3][6] | Near real-time containment (seconds to minutes) [6][7] | Requires governed playbooks, audit logs, and role-based access [6][7] |
This analysis highlights the importance of maintaining balance in AI-driven controls to safeguard patient data without disrupting care. Censinet RiskOps™ takes this a step further by integrating third-party risk assessments and aligning AI controls with HIPAA and CMS requirements [3][6].
Conclusion
No single AI solution can fully address the challenge of phishing in healthcare. The most effective strategy involves combining multiple layers of defense. Pre-delivery filtering plays a key role in stopping high-volume phishing attempts before they even reach clinicians. This is especially important for large hospital systems and integrated delivery networks, where email is critical for scheduling, prior authorizations, and coordinating care. On the other hand, post-delivery analytics and user behavior monitoring are essential for detecting more sophisticated, targeted attacks that may slip through initial defenses. These tools are particularly valuable for high-risk users like executives, CMIOs, and revenue-cycle staff, whose compromised accounts could result in severe breaches of protected health information (PHI). Additionally, automated triage and response systems help contain threats quickly, a significant advantage for resource-limited Security Operations Centers (SOCs) in smaller hospitals and clinics.
To build an effective defense, it’s essential to align AI strategies with the specific needs of your organization. For example:
- Small practices benefit from cloud-native AI email protection with basic auto-quarantine features.
- Mid-sized hospitals should combine pre-delivery filters with post-delivery analytics to secure high-risk departments.
- Large healthcare centers require fully integrated systems that unify email security with identity management, EHR systems, and endpoint telemetry.
Beyond preventing breaches, well-implemented AI defenses deliver measurable results. Tools like Censinet RiskOps™ can strengthen vendor risk assessments and boost overall cybersecurity posture [3]. To gauge the effectiveness of your approach, track metrics such as phishing simulation click rates, the number of threats blocked pre- and post-delivery, detection and response times, and the financial impact of avoided breaches. These metrics not only justify investments but also help fine-tune your defenses over time.
However, technology alone isn’t enough. Pair AI tools with ongoing phishing simulations, role-based training tailored to emerging threats (like AI-generated or deepfake attacks), and well-documented escalation playbooks that staff can easily understand and trust [8][9][12].
FAQs
How does AI enhance phishing detection in healthcare?
AI plays a crucial role in improving phishing detection within the healthcare industry by analyzing vast amounts of real-time data to pinpoint patterns and anomalies that indicate phishing attempts. It excels at identifying subtle threats that might otherwise go unnoticed, all while reducing the number of false positives. This enables organizations to respond more quickly and with greater precision.
By integrating AI, healthcare providers can strengthen the security of sensitive patient data, meet regulatory requirements, and mitigate the dangers posed by phishing attacks. This forward-thinking strategy is key to safeguarding critical systems and preserving trust in the healthcare field.
How does AI help detect and respond to phishing threats in healthcare?
AI plays a crucial role in helping healthcare organizations combat phishing threats. By keeping a constant watch on systems, AI can spot unusual activities, analyze patterns, and take automated actions to neutralize threats before they escalate.
This forward-thinking strategy safeguards sensitive patient information, keeps clinical operations running smoothly, and drastically cuts down response times. It allows healthcare professionals to concentrate on providing excellent care, all while ensuring strong security measures are in place.
How does AI help healthcare organizations meet HIPAA requirements for phishing protection?
AI-driven phishing defense systems are essential for healthcare organizations aiming to meet HIPAA requirements. They help protect sensitive patient data and protected health information (PHI) by identifying threats in real time, automating responses to potential breaches, and constantly evaluating risks to close security gaps.
These tools simplify tasks such as monitoring secure communications and addressing threats before they escalate. By doing so, they support HIPAA's rigorous rules for safeguarding electronic health information. This not only helps healthcare providers stay compliant but also minimizes the chances of expensive data breaches, reinforcing patient confidence in their services.


