Ambulatory Surgery Center Vendor Risk: Specialized Equipment and Safety Considerations
Post Summary
Ambulatory Surgery Centers (ASCs) depend on specialized equipment and vendor services to ensure safe, efficient patient care. When vendor-related issues arise - like delayed equipment delivery, cybersecurity breaches, or non-compliance with healthcare regulations - patient safety and ASC operations can be severely impacted. Here's what you need to know about managing these risks:
- Key Risks: Equipment failures, cybersecurity threats, and regulatory non-compliance are the most common vendor-related risks in ASCs.
- Challenges: ASCs often face financial pressures, outdated vendor credentialing practices, and limited resources compared to larger hospitals.
- Solutions: Implement thorough vendor evaluations, clear Service Level Agreements (SLAs), and continuous monitoring to mitigate risks.
- Tools: Platforms like Censinet RiskOps™ can streamline vendor risk management, automate assessments, and improve oversight.
Quick Overview of Vendor Risk Management Steps:
- Assess vendors for financial stability, compliance, and technical reliability.
- Establish SLAs with clear performance expectations.
- Conduct regular audits and inspections for high-risk vendors.
- Monitor cybersecurity practices, including data encryption and incident response plans.
- Use automated tools and centralized tracking to simplify evaluations and ensure compliance.
By addressing vendor risks proactively, ASCs can maintain patient safety, comply with regulations, and avoid disruptions that could harm their reputation or bottom line.
Primary Risk Factors for ASC Vendors
Risks associated with vendors in Ambulatory Surgery Centers (ASCs) generally fall into three main areas: cybersecurity vulnerabilities, equipment failures, and regulatory non-compliance. Each of these poses serious threats to patient safety and operational efficiency, making it crucial to address them head-on.
Cybersecurity Vulnerabilities in Medical Devices
With the rise of network-connected medical devices, cybercriminals have found an attractive target in healthcare settings. ASCs, often operating with smaller budgets and limited IT expertise, can be especially at risk [1]. Healthcare data is highly valuable on the black market because it can be exploited over extended periods, and fraud is often detected too late [1].
Devices connected to the Internet of Things (IoT) - like infusion pumps and anesthesia monitors - can increase the risk of cyberattacks if they aren’t isolated from corporate networks [2]. Weak access controls, such as basic username-password systems, make ASCs more vulnerable to phishing schemes, data breaches, and human errors [1][3].
"In healthcare environments, where patient data and medical records are at stake, the consequences of unauthorized access can be severe."
– Dr. Paul Alcock, Chief Information Security Officer, Surgical Information Systems [3]
Another common issue is poor patch management. When vendors fail to provide timely security updates, ASCs inherit the risks of outdated systems. Insider threats also remain a significant concern, as authorized individuals - whether through negligence or malicious intent - can compromise sensitive systems [1].
Next, let’s explore how equipment failures can jeopardize both patient safety and operational stability.
Equipment Failure and Patient Safety Risks
Equipment malfunctions during procedures can lead to immediate and severe consequences. These failures often stem from substandard, unapproved, or counterfeit products supplied by vendors [4]. Such issues directly endanger patient safety, especially during critical surgical moments.
Operational disruptions caused by equipment failures can also have a ripple effect. For example, when sterilization units or other essential systems break down during busy periods, surgeries may be delayed or canceled. This strains resources and creates financial challenges for ASCs [4].
Vendor Compliance with Healthcare Regulations
Regulatory compliance is another area where vendor-related risks come into play. Vendors must adhere to healthcare regulations such as HIPAA, CMS Conditions for Coverage, and FDA standards. Noncompliance can leave ASCs exposed to regulatory penalties, operational disruptions, and even the loss of cybersecurity insurance [5].
"Your organization's security posture is only as strong as its weakest link, which often can be an uninformed third-party."
– Dr. Paul Alcock, Chief Information Security Officer, Surgical Information Systems [3]
The increasing use of AI-driven tools for threat detection and compliance monitoring underscores the need for vigilant vendor oversight [2][5]. ASCs must ensure vendors have robust quality management systems, promptly communicate any process changes, and verify that they meet standards to avoid counterfeit parts [4]. When vendors fall short in these areas, the ASC’s operations and patient care can face serious consequences.
How to Evaluate Vendor Reliability and Safety
When it comes to evaluating vendors, it's essential to look at both their overall operations and the specific products they offer. Interestingly, while nearly 80% of organizations have formal vendor risk assessment programs, around 30% still lack dedicated staff to manage this critical task [6]. This gap can leave ambulatory surgery centers (ASCs) exposed to vendor-related issues that might affect patient care. To address this, it's important to focus on key criteria that ensure vendor reliability.
Vendor Assessment Criteria
A thorough vendor evaluation should consider six main risk categories: financial stability, compliance with laws and regulations, technical soundness (like IT and data management), operational policies and procedures, adequate resources, and reputational impact. For specialized medical equipment, additional product-specific factors come into play, such as security features, ease of use, cost-effectiveness, and adherence to data privacy and reporting standards.
Financial stability is particularly important - vendors need sufficient time, money, and personnel to fulfill their maintenance and support commitments. It's also wise to assess a vendor’s public reputation by reviewing customer feedback, any recent controversies, and their track record for reliability. Think about the potential risks if a vendor were to cease operations and how easily they could be replaced. A multidisciplinary review team can help identify risks that might otherwise go unnoticed.
Every vendor, regardless of size, deserves a thorough evaluation - especially those with access to sensitive data or physical spaces. For instance, a December 2022 breach at 365 Data Centers exposed medical information for over 271,000 patients of Avem Health Partners, illustrating the serious downstream effects of vendor failures [6].
Service Level Agreements and Maintenance Terms
After evaluating vendors, it’s crucial to establish clear contracts that hold them accountable. Service Level Agreements (SLAs) should outline specific expectations, such as guaranteed response times, timely updates, patches, and comprehensive support. Contracts should also address data storage requirements and how subcontractors are managed. Before finalizing an agreement, assess the vendor’s customer service and technical support capabilities. It’s also worth asking how they handle errors caused by software updates or device modifications and how they communicate and resolve such issues [6].
Tools and Processes for Vendor Risk Assessment
To streamline vendor evaluations, consider using a consistent scoring system to classify vendors as low, medium, or high risk based on their potential business impact. This allows you to determine the level of due diligence required for each vendor relationship. For ASCs, data privacy should be a top priority due to the sensitive nature of patient information.
Annual evaluations and continuous monitoring are essential to keep up with changes in vendor procedures, product updates, and compliance status [6]. If there are shifts in staff, processes, or equipment - or if any issues or near misses occur - make sure to review controls regularly [7]. Stay up-to-date on new regulations, and be prepared to cut ties with vendors who resist compliance updates, as ASCs can be held accountable for their breaches [6]. Using a centralized platform can simplify vendor evaluations and improve efficiency throughout the vendor lifecycle.
How to Reduce Vendor Risks in ASCs
After assessing your vendors, the next step is to put measures in place to mitigate risks. This involves leveraging advanced tools, establishing clear policies, and maintaining continuous monitoring. These efforts ensure that cybersecurity, safety, and compliance work hand in hand to safeguard patient care and your facility’s operations. Below are specific strategies to help you achieve this.
Using Censinet RiskOps™ for Vendor Risk Management
Managing vendor risks manually can quickly become overwhelming, especially when dealing with multiple specialized suppliers. That’s where tools like Censinet RiskOps™ come in. This platform simplifies vendor risk management by centralizing compliance data, certifications, and performance metrics into one streamlined system. It provides a clear view of risks, automates recurring assessments, and helps prevent critical oversights.
The integration of Censinet AI™ further enhances efficiency. Vendors can complete assessments in seconds, with the system automatically summarizing evidence, highlighting key details, and flagging additional risks. This blend of automation and human oversight ensures your team stays in control, using configurable rules and review processes to manage findings effectively. Critical issues are routed to the right stakeholders without delay.
Once automated risk insights are in place, it’s time to focus on establishing strong cybersecurity and safety standards.
Cybersecurity and Safety Requirements for Vendors
Setting clear cybersecurity and safety standards from the outset can prevent headaches down the road. Vendor contracts should explicitly outline data security measures, including encryption protocols, access controls, and incident response plans. These agreements should also require ongoing compliance with recognized certifications such as HITRUST, SOC 2 Type 2, or ISO 27001, which provide assurance beyond a one-time evaluation.
For medical device suppliers, safety protocols are equally critical. Vendors should be prepared to complete detailed security questionnaires, maintain continuous compliance certifications, and participate in scheduled security reviews.
"Vendors in high-risk areas should agree to real-time, continuous monitoring." – Compyl [10]
These standards not only protect your operations but also ensure that vendors remain accountable over time.
Ongoing Vendor Monitoring and Risk Reduction
Establishing vendor requirements is just the beginning. Continuous oversight is essential to ensure these standards are upheld and that both patient care and facility operations remain protected. For vendors in high-risk categories, particularly those supplying specialized medical equipment, real-time monitoring can help flag suspicious activities or performance issues before they escalate. As noted, continuous monitoring is "an obligation, not a luxury" for high-risk healthcare vendors [10].
Monitoring frequency should match the vendor’s risk level. For high-risk vendors, quarterly assessments may be necessary, while lower-risk partners might only require annual reviews. Incorporate vendor performance metrics into your Quality Assessment and Performance Improvement (QAPI) meetings to maintain active oversight. If a vendor underperforms, follow a structured corrective action process. This includes documenting deficiencies, notifying the vendor of specific gaps, requesting a corrective action plan to address root causes, and verifying improvements through follow-up performance data [11].
Automation can play a key role in keeping everything on track. Use calendar reminders for credentialing checks, quarterly reviews, and contract renewals. Maintain a centralized inventory of vendor contracts with clearly defined Key Performance Indicators (KPIs) to track performance. Additionally, consider independent audits of key vendors to ensure their standards align with your ASC’s specific requirements, which may vary based on your patient population and specialized equipment needs [11].
sbb-itb-535baee
Vendor Risk Management Checklist for ASC Administrators
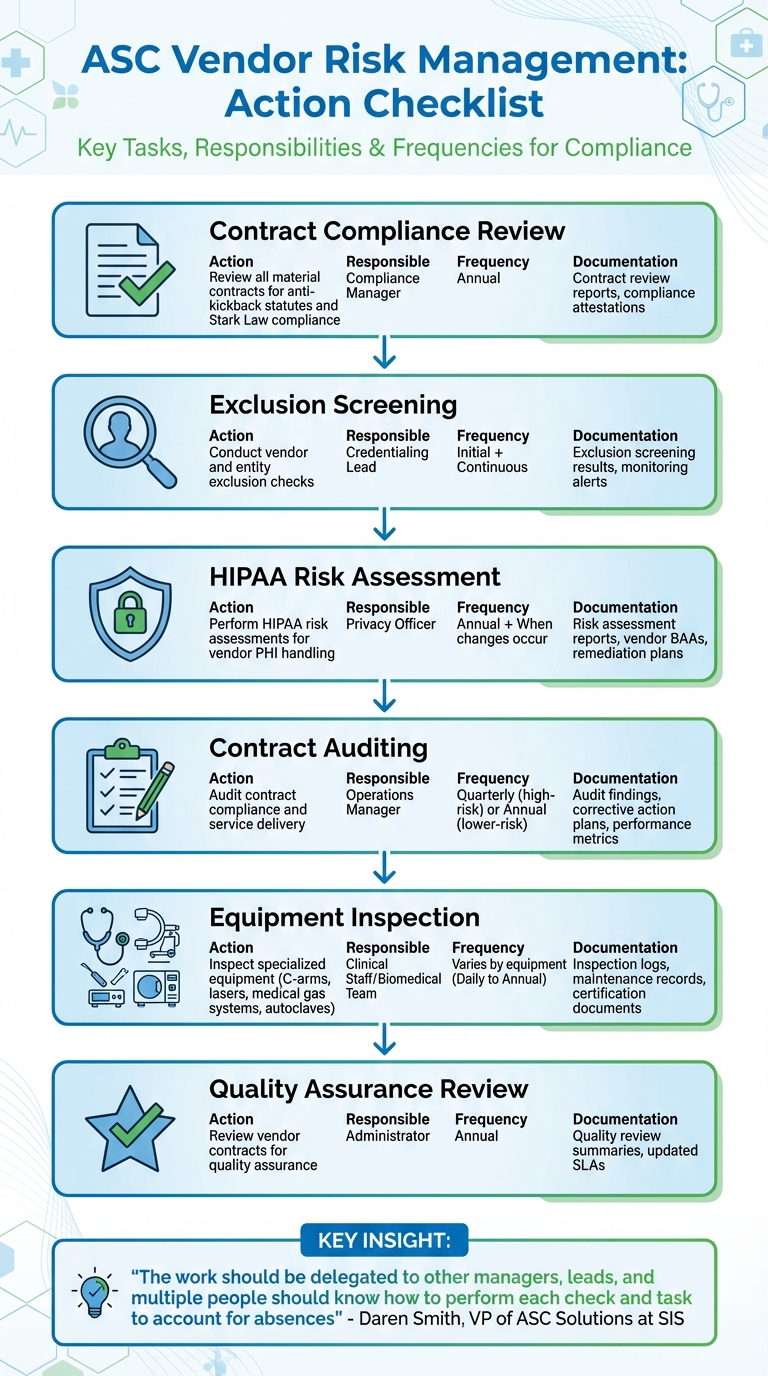
ASC Vendor Risk Management Action Checklist with Responsibilities and Frequencies
Vendor Risk Management Action Steps
The table below outlines key actions for managing vendor risks in Ambulatory Surgery Centers (ASCs). It specifies who is responsible, how often tasks should be completed, and the necessary documentation to maintain compliance and accountability.
| Action | Responsible Party | Frequency | Required Documentation |
|---|---|---|---|
| Review all material contracts (vendor agreements, equipment contracts, IT contracts) for compliance with anti-kickback statutes and Stark Law | Compliance Manager | Annual | Contract review reports, compliance attestations |
| Conduct vendor and entity exclusion checks | Credentialing Lead | Initial + Continuous | Exclusion screening results, monitoring alerts |
| Perform HIPAA risk assessments addressing vendor PHI handling | Privacy Officer | Annual + When changes occur | Risk assessment reports, vendor BAAs, remediation plans |
| Audit contract compliance and service delivery | Operations Manager | Quarterly (high-risk vendors) or Annual (lower-risk vendors) | Audit findings, corrective action plans, performance metrics |
| Inspect specialized equipment (C-arms, lasers, medical gas systems, autoclaves) | Clinical Staff/Biomedical Team | Varies by equipment (Daily to Annual) | Inspection logs, maintenance records, certification documents |
| Review vendor contracts for quality assurance | Administrator | Annual | Quality review summaries, updated SLAs |
These steps are critical for maintaining a strong vendor risk management program. Assign responsibilities across multiple team members and track tasks in a centralized spreadsheet to avoid disruptions during staff absences. As Daren Smith, VP of ASC Solutions at SIS, emphasizes:
"The work should be delegated to other managers, leads, and multiple people should know how to perform each check and task to account for absences" [13].
Building Operational Resilience
Expanding on the checklist, operational resilience ensures ASC operations remain secure and efficient. Effective vendor management not only mitigates risks but also strengthens overall performance. By conducting proactive risk assessments, you can uncover vulnerabilities and focus on areas that directly impact patient care [14].
To build resilience, spread compliance and monitoring duties across your team instead of relying on a single individual. This approach creates redundancy and safeguards continuity during staff transitions or unexpected absences [13]. Keep a centralized inventory of all vendor contracts, clearly marking expiration dates and renewal terms [12]. Use automated calendar reminders for credentialing checks, quarterly reviews, and contract renewals to ensure no critical deadlines are missed. For high-risk vendors, particularly those providing specialized medical equipment, establish real-time monitoring systems to quickly detect performance issues or compliance lapses.
Conclusion
Vendor risk management is a cornerstone of success for Ambulatory Surgery Centers (ASCs), playing a critical role in patient safety, operational continuity, and regulatory compliance. From imaging systems to medical gas components, the performance of specialized equipment directly impacts patient outcomes. When vendors fall short - whether through unreliable products, cybersecurity lapses, or regulatory non-compliance - the consequences can be severe: patient safety is jeopardized, regulatory fines loom, and the reputation of your center is at stake.
David Holt of DJ Holt Law puts it succinctly:
"Vendor and payor agreements are not mere formalities; they are the legal bedrock of your ASC's operations" [8].
Building strong vendor relationships through thorough due diligence, clear contractual agreements, and consistent monitoring is essential. This proactive strategy not only helps prevent equipment failures and data breaches but also ensures your ASC stays aligned with ever-changing healthcare regulations. Such a foundation is vital for maintaining financial stability and operational integrity.
The financial implications are no small matter. For example, hospital readmissions cost an estimated $26 billion annually [9]. Poor vendor management can erode your bottom line, while a robust approach - featuring regular evaluations, ongoing monitoring, and automated tracking tools - can significantly reduce penalties, prevent breaches, and minimize disruptions. By investing in comprehensive vendor risk management, your ASC sets the stage for long-term success and resilience.
FAQs
What steps can ASCs take to protect connected medical devices from cybersecurity threats?
To protect connected medical devices from potential cybersecurity risks, ASCs need to take a forward-thinking approach. Start by using encryption to keep data secure, establishing strict access controls to limit who can interact with devices, and performing regular vulnerability assessments to spot weaknesses before they become problems.
It’s also crucial to work with vendors who adhere to recognized cybersecurity standards, provide continuous staff training on safe practices, and have a strong incident response plan ready to handle any breaches swiftly. These measures not only safeguard sensitive patient information but also ensure the reliability and security of vital medical equipment.
What steps can ambulatory surgery centers take to ensure their vendors comply with healthcare regulations?
To maintain vendor compliance with healthcare regulations, ambulatory surgery centers (ASCs) should begin by conducting thorough due diligence. This means carefully assessing each vendor's reliability and commitment to safety standards. It's also essential to use clear, standardized contracts that outline roles, responsibilities, and expectations right from the start. Consulting with legal counsel during contract negotiations can help secure better terms and reduce the risk of future complications.
Implementing contract management systems is another key step. These systems allow ASCs to track agreements, schedule regular reviews, and ensure contracts are updated to reflect any regulatory changes. Training staff on compliance procedures and keeping detailed records of all communications with vendors are equally important for maintaining accountability. Finally, having a well-defined dispute resolution process can help resolve issues quickly and minimize disruptions to patient care.
Why is it important to continuously monitor vendors in ambulatory surgery centers?
Continuous oversight of vendors plays a key role in helping ambulatory surgery centers (ASCs) uphold top-tier patient care and safety standards. Regular monitoring allows ASCs to spot potential risks early, such as regulatory non-compliance, cybersecurity threats, or equipment malfunctions that could interfere with operations or impact patient outcomes.
By keeping a close eye on vendors, ASCs can confirm that suppliers consistently meet expectations for reliability, safety, and quality, all while adhering to industry regulations. This proactive strategy helps reduce disruptions and protects the well-being of both patients and staff.
Related Blog Posts
- Surgical Equipment Vendor Risk Management: Operating Room Safety and Reliability
- Anesthesia System Vendor Risk: Patient Safety in the Operating Room
- Surgical Equipment Vendor Risk Management: Operating Room Safety and Reliability
- Rehabilitation Hospital Vendor Risk Management: Specialized Equipment and Patient Safety


