Anesthesia System Vendor Risk: Patient Safety in the Operating Room
Post Summary
Anesthesia systems are critical for patient care, but they come with risks tied to vendor reliability and cybersecurity. Hospitals face challenges like equipment failures, cyber vulnerabilities, and compliance issues, all of which can jeopardize patient safety during surgery.
Key Points:
- Vendor Risks: Problems like device recalls or outdated systems can lead to equipment malfunctions. For example, Draeger's 2024 recall of 3,713 anesthesia systems highlighted the dangers of battery defects causing unexpected shutdowns.
- Cybersecurity Threats: Network-connected devices, such as anesthesia machines and infusion pumps, are vulnerable to hacking. Attackers could alter settings, disable alarms, or disrupt workflows, potentially endangering lives.
- Regulatory Challenges: Many devices operate on outdated systems without proper security updates, making compliance and risk management difficult.
Solutions:
- Conduct regular vendor risk assessments, including technical testing like penetration scans.
- Use cyber risk platforms to streamline risk management and ensure faster issue resolution.
- Implement strict configuration standards and incident response plans to mitigate risks.
Bottom line: Hospitals must stay vigilant by addressing vendor risks and cybersecurity gaps to protect patients and maintain trust in critical care systems.
Cyber Vulnerabilities in Anesthesia Systems
Devices in operating rooms are increasingly vulnerable to cybersecurity threats, raising serious concerns for patient safety. Federal advisories and research have pointed to exploitable weaknesses in anesthesia machines, monitors, and related medical devices. These vulnerabilities are not just technical issues - they directly impact clinical risk and the reliability of life-support systems. Here’s a closer look at some key examples of these risks.
Anesthesia Machines and Ventilators
In July 2019, the U.S. Department of Homeland Security's Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) issued a warning about a vulnerability in GE Healthcare's Aestiva and Aespire anesthesia machines (models 7100 and 7900). This flaw allowed hackers with network access to remotely modify gas settings, time records, and alarm functions. Notably, attackers didn’t need to know the specific location of the devices to exploit this weakness. Cybersecurity firm CyberMDX assessed the vulnerability with a CVSS score of 5.3, categorizing it as moderate. However, when viewed in the broader context of operating room risks, it was considered far more dangerous. Jon Rabinowitz from CyberMDX noted:
If this vulnerability were to be scored on a more holistic scale for risk, it would be considered critical.
While GE Healthcare acknowledged the issue, their internal investigation concluded there was "no introduction of clinical hazard or direct patient risk." [2]
Infusion Pumps in the Operating Room
Infusion pumps, essential for delivering precise medication doses during surgeries, are another area of concern. These devices often connect to hospital networks for data sharing and monitoring. Although public advisories specific to infusion pump vulnerabilities in operating rooms are scarce, the broader trend of network-connected devices highlights the potential risks. Any device integrated into a network can become an entry point for attackers.
Physiological Monitoring and Alarm Systems
The vulnerability in GE anesthesia machines also revealed how attackers could manipulate monitoring and alarm functions, leading to serious documentation and safety concerns. Elad Luz, Head of Research at CyberMDX, elaborated:
The potential for manipulating alarms and gas compositions is troubling. More subtle but just as problematic is the ability to alter timestamps that reflect and document what happened in surgery... Once the integrity of time and date settings has been compromised, you no longer have reliable audit trails. That's a very serious problem for any medical center. [3]
Nadir Izrael, CTO and Co-founder of Armis, underscored the broader implications:
The real concern when hacking medical devices [is] it only takes one hacked device to hurt or, forbid, kill a patient... They are about data and device manipulation; whether that is delivering too much anesthesia or stopping a respiratory device. [2]
These examples highlight the urgent need to address cybersecurity vulnerabilities in medical devices to ensure patient safety and maintain trust in critical healthcare systems.
How Cyber Vulnerabilities Affect Patient Safety
Cybersecurity gaps in anesthesia systems pose serious risks to patient safety, going far beyond just data breaches. When attackers exploit these systems, they can disrupt critical clinical workflows and tamper with medical data, putting patients' lives at risk during care.
Clinical Risks from Cyber Incidents
These vulnerabilities have the potential to cause immediate harm to patients. Hackers can remotely alter device settings, disable alarms, or manipulate medication delivery rates without the medical team's awareness. As Anthony James Cartwright from Cleveland Clinic Abu Dhabi highlighted:
It has already been proven that anaesthesia machines and infusion pumps can be hacked and their settings changes without the knowledge of the physician.[5]
A real-world example involves the Alaris Gateway Workstation, a system used to control multiple medication delivery devices. Researchers uncovered a security flaw that allowed malicious firmware to be installed. This vulnerability enabled attackers to change infusion rates for critical drugs, potentially leading to fatal outcomes.[5]
Even though some manufacturers downplay the risks - GE Healthcare, for instance, claimed there is "no direct patient risk" for its Aestiva and Aespire machines because anesthesiologists are present - the reality is more complex. Masked vital signs or silenced alarms could delay the detection of life-threatening complications during surgery.[5][6]
These clinical risks not only jeopardize individual patients but also disrupt the overall workflow in surgical settings, creating a ripple effect throughout the healthcare system.
Operating Room Disruptions
The impact of cyberattacks extends beyond individual patient care, often paralyzing entire surgical departments. Take the WannaCry ransomware attack in May 2017, for instance. This attack affected 600 organizations within the British National Health Service (NHS), forcing ambulances to reroute and surgeries to be canceled across 150 countries. The NHS alone faced an estimated loss of nearly $7.8 million.[7][4]
Another example occurred on October 28, 2020, when the University of Vermont Health Network suffered a cyberattack that shut down its electronic medical record system across six hospitals. This disruption left cancer patients without timely access to chemotherapy because providers couldn’t retrieve essential treatment protocols. It took almost a month to restore the system.[4]
Such attacks force healthcare teams to rely on manual processes, increasing the likelihood of errors. Without electronic medical records, coordinating services like blood banks, labs, and pharmacies becomes far more difficult - especially for patients in urgent need of surgical care. These disruptions not only compromise patient safety but also strain healthcare resources to their breaking point.
Vendor Risk and Regulatory Requirements
Vendor-related risks add another layer of complexity to the already significant challenges of patient safety in the face of cyber vulnerabilities. These risks often stem from technical weak points that can serve as gateways for cyberattacks. Issues like outdated operating systems and inconsistent patch management not only heighten security risks but also make it harder to comply with regulations aimed at safeguarding patient safety.
Common Vendor Risk Factors
A significant number of anesthesia devices still operate on outdated systems that no longer receive security updates. This leaves them exposed to emerging vulnerabilities, creating an open door for cyberattacks. Beyond security concerns, these legacy systems can also lead to clinical errors, especially when patches are delayed or fail to resolve issues effectively. Replacing these systems is often avoided due to the high costs involved, leaving healthcare facilities reliant on technology that may not meet modern security standards.
Patch management is another critical challenge. While some vendors respond quickly to address vulnerabilities, others are slower to act. Even when patches are available, applying them can be tricky, as healthcare providers must carefully balance the need for updates with the risk of disrupting clinical operations. Regulatory guidelines for patch management and device updates play a significant role in shaping how healthcare organizations handle these risks. Striking the right balance between maintaining compliance and ensuring patient safety remains a constant challenge.
The following section will delve into strategies for assessing and mitigating these risks to better protect patient care.
sbb-itb-535baee
How to Manage Anesthesia System Vendor Risk
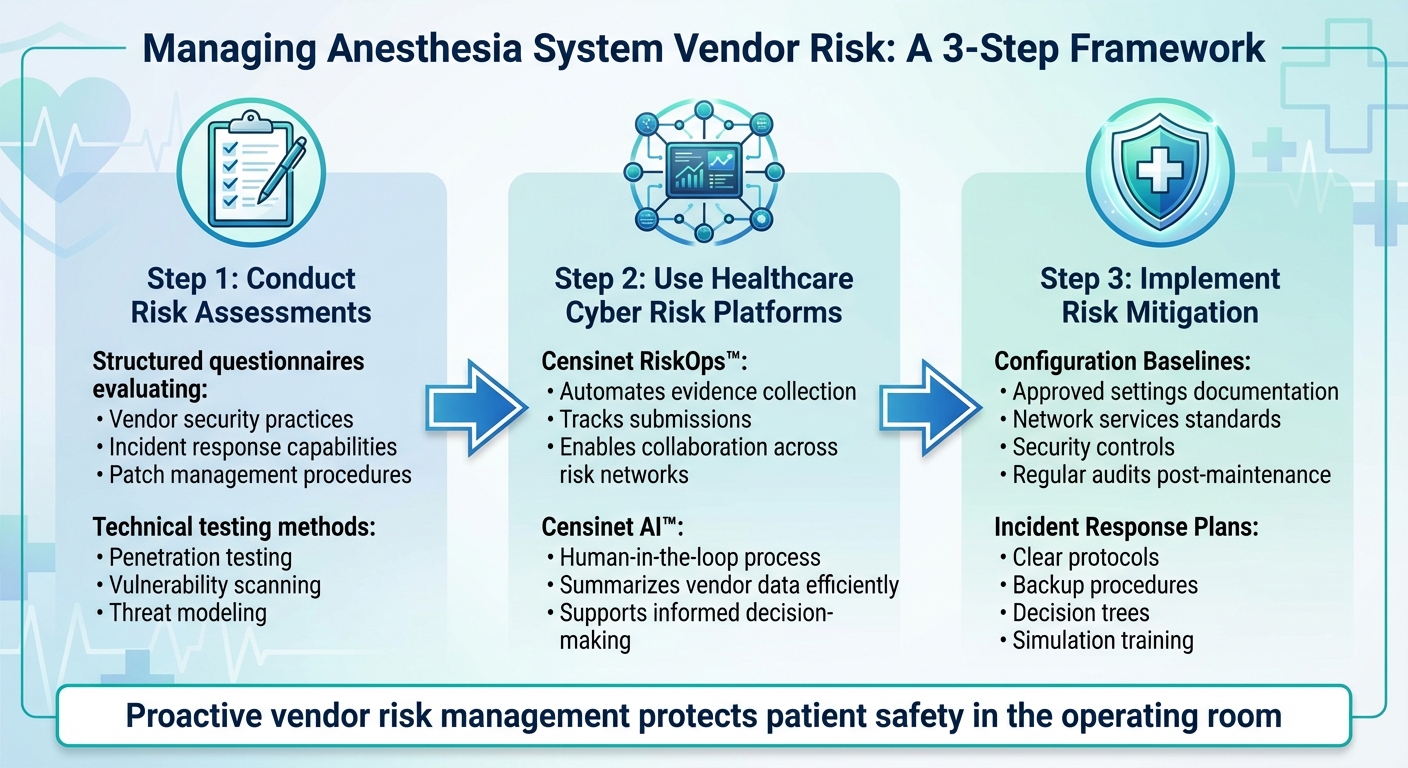
3-Step Framework for Managing Anesthesia System Vendor Risk in Healthcare
Effectively managing vendor risks tied to anesthesia systems is crucial for safeguarding patient safety and maintaining compliance with regulatory standards. Rather than relying on reactive measures, healthcare organizations need to adopt proactive strategies that address vulnerabilities head-on.
Conducting Risk Assessments
The first step in managing vendor risk is conducting a thorough assessment. This process often starts with structured questionnaires designed to evaluate key areas like vendor security practices, incident response capabilities, and patch management procedures. These questionnaires can provide insight into critical factors such as how quickly vendors respond to issues, how they deliver patches, and whether their update documentation is clear and reliable.
Beyond questionnaires, technical testing is essential to confirm the security of anesthesia devices before they are deployed. Techniques like penetration testing, vulnerability scanning, and threat modeling can help identify and prioritize risks that need immediate attention.
Using Healthcare Cyber Risk Platforms
Healthcare cyber risk platforms can significantly streamline vendor risk management. For example, Censinet RiskOps™ automates tasks like evidence collection, submission tracking, and collaboration across risk networks, reducing redundant efforts. Meanwhile, Censinet AI™ uses a human-in-the-loop process to summarize vendor data efficiently, ensuring that automated insights are complemented by the expertise of risk management teams. This combination of automation and human oversight supports more informed decision-making.
Implementing Risk Mitigation for Patient Safety
Once assessments are complete, the next step is implementing risk mitigation strategies. One key approach is setting configuration baselines for all anesthesia equipment. These baselines outline approved settings, network services, and security controls that are essential for safe operation. Any deviations from these standards should prompt an immediate review. Regular audits are also critical to ensure that devices remain securely configured, even after routine maintenance or software updates.
Incident response plans are another vital component of risk mitigation. These plans should include clear protocols, backup procedures, and decision trees to guide actions during a cyber incident. Simulation training can help identify weaknesses in these plans by exposing gaps in response procedures. Such drills not only improve preparedness but also reinforce patient safety by addressing potential vulnerabilities before they lead to disruptions in the operating room.
Conclusion
Vendor risks in anesthesia systems pose a serious threat to patient safety in the operating room. The recent recall of the Draeger Perseus A500 serves as a stark reminder of the dangers tied to vendor vulnerabilities [1].
Modern anesthesia machines are intricate, networked systems with integrated components, making them increasingly susceptible to cybersecurity threats [8]. For healthcare organizations, overlooking vendor risk management is not an option - these systems play a direct role in patient outcomes.
To manage these risks effectively, healthcare providers must conduct thorough vendor evaluations, implement technical testing protocols, and establish strict configuration standards. Regular audits and incident response drills are also crucial to maintaining system security, especially after routine maintenance or software updates.
Creating a safer operating room environment requires both regulatory oversight and operational diligence. Vendors need to prioritize safety features and provide strong support services, while healthcare providers must focus on device testing, regular maintenance, and adherence to professional standards. These combined efforts help build resilience and safeguard patients during critical moments.
Ultimately, protecting patient safety in the operating room hinges on rigorous, ongoing risk management. By staying vigilant, healthcare organizations can ensure that every patient receives the care they deserve without compromise.
FAQs
What steps can hospitals take to protect anesthesia systems from cyber threats?
Hospitals can protect anesthesia systems from cyber threats by keeping these systems isolated from external networks and securing them behind robust firewalls. Restricting access to only authorized personnel and using strong encryption methods, like VPNs, for remote access are key steps in maintaining security.
Keeping firmware up to date and applying security patches regularly helps close potential vulnerabilities. Additionally, performing thorough risk assessments and monitoring for suspicious activity can provide an extra layer of vigilance. Implementing a defense-in-depth strategy, which uses multiple security layers, further reduces the likelihood of breaches.
What are the essential steps to assess vendor risks for anesthesia systems?
To properly evaluate vendor risks for anesthesia systems, start by identifying the key areas where risks might arise. These can include compliance issues, operational challenges, financial instability, or potential damage to your organization's reputation. Setting clear evaluation criteria - like specific risk categories and a scoring method - will help ensure your assessments are consistent and thorough.
The next step is to dive into the vendor's offerings. This means looking at their security measures, adherence to regulations, and their overall financial and operational health. Gather critical data, such as certifications, records of past incidents, and financial reports, to build a well-rounded view of their risk profile.
Once the evaluation is complete, classify each vendor by their risk level - high, medium, or low. For those with higher risks, create mitigation strategies. This might involve regular monitoring, audits, or adding specific safeguards into contracts. To keep everything on track, establish a system for continuous monitoring and schedule periodic reassessments. This approach helps protect patient safety and ensures your operations run smoothly.
Why is it important to keep anesthesia devices updated and properly maintained in healthcare settings?
Keeping anesthesia devices in top condition is crucial for maintaining patient safety during medical procedures. Regular updates and maintenance serve multiple purposes: they fix known vulnerabilities, prevent malfunctions, and minimize the chances of critical issues like leaks, system errors, or problems with ventilation.
Failing to keep these devices updated can have dire consequences. Issues such as insufficient oxygen delivery or equipment failure could result in severe injuries or even fatalities. By staying proactive with maintenance, healthcare providers can ensure safer, more dependable care in the operating room.
Related Blog Posts
- Anesthesia System Vendor Risk: Patient Safety in the Operating Room
- Surgical Equipment Vendor Risk Management: Operating Room Safety and Reliability
- ICU and Critical Care Vendor Risk Management: Life Support System Reliability
- Rehabilitation Hospital Vendor Risk Management: Specialized Equipment and Patient Safety


