Anomaly Detection in EHRs: Preventing Data Breaches
Post Summary
Cyberattacks on healthcare are rising, and electronic health records (EHRs) are prime targets. Anomaly detection systems help safeguard sensitive patient data by identifying unusual behavior, such as excessive record access, odd login times, or unfamiliar device usage. These tools use machine learning to detect patterns that might indicate credential misuse, insider threats, or external attacks.
Key points:
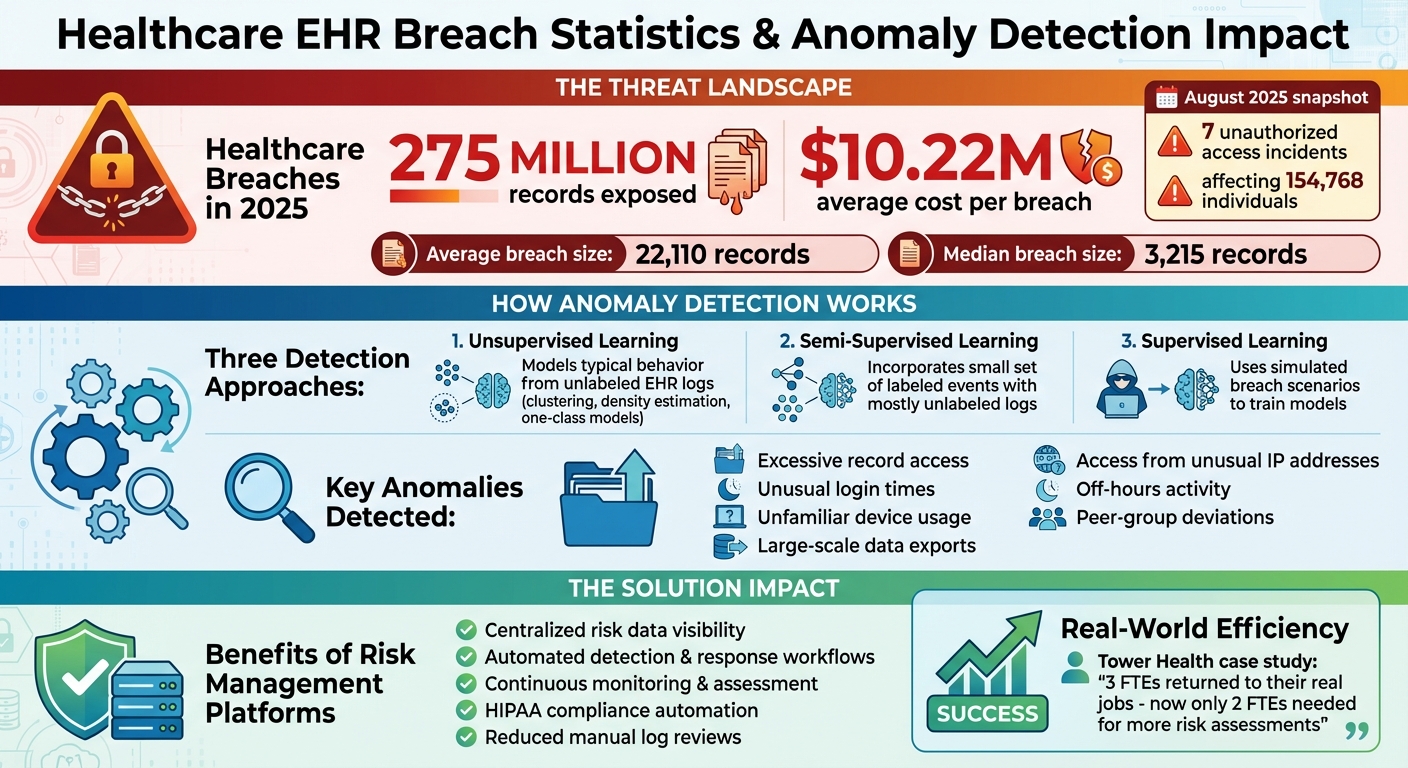
- Why it matters: Healthcare breaches exposed 275 million records in 2025, with an average cost of $10.22M per breach.
- How it works: Machine learning models analyze EHR logs to flag deviations from normal user behavior.
- Challenges: Data fragmentation, false positives, and compliance hurdles can complicate implementation.
- Solutions: Centralized risk management platforms like Censinet RiskOps™ streamline detection, automate responses, and maintain compliance.
Anomaly detection is critical for protecting patient data, reducing breach costs, and meeting HIPAA requirements. However, success depends on integrating these tools with broader risk management strategies.
Healthcare Data Breach Statistics and Anomaly Detection Impact 2025
Anomaly Detection Techniques for EHR Security
Healthcare organizations use various machine learning and statistical methods to spot unusual patterns in electronic health record (EHR) access. These techniques not only identify anomalies but also act as preventive tools to help stop data breaches in sensitive EHR environments. Generally, these methods fall into three categories - unsupervised, semi-supervised, and supervised learning - each designed to tackle specific challenges, such as insider threats or compromised credentials. Since many U.S. health systems have extensive EHR audit logs but relatively few confirmed breach cases, approaches that establish baseline behaviors without needing explicit breach labels are particularly useful.
Unsupervised and Semi-Supervised Learning Methods
Unsupervised methods focus on modeling typical behavior from unlabeled EHR logs. Techniques like clustering (e.g., k-means, hierarchical clustering) and density estimation (e.g., Gaussian Mixture Models) are used to identify outliers, while one-class models (such as Support Vector Machines, isolation forests, or autoencoders) detect deviations through metrics like reconstruction error or isolation scores. For example, anomalies such as large-scale data exports, access from unusual IP addresses, or repeated views of high-profile patient records outside standard clinical practices might trigger alerts based on these methods.
Semi-supervised methods take this a step further by incorporating a small set of labeled events - like known policy violations - into the analysis of mostly unlabeled logs. Autoencoders, when conditioned on factors such as role, department, and time, can improve detection accuracy. To meet HIPAA audit requirements, some implementations include explainability tools like SHAP or LIME to help security teams understand which specific factors - such as access during odd hours or from an off-site IP address - triggered an alert. These insights make it easier to investigate and document incidents.
This unsupervised foundation also creates opportunities to use controlled, simulated data for supervised learning approaches.
Supervised Learning with Simulated Datasets
Because confirmed breach cases are rare and often under-reported, U.S. health systems increasingly turn to simulated or synthetic breach scenarios to train supervised models. These scenarios combine benign log data with fabricated misuse cases to help models - such as random forests, gradient boosting, or deep neural networks - learn to differentiate between legitimate activities and potential misuse.
To make these models effective, having access to strong data sources and selecting the right features is critical.
Data Sources and Features for Detection
EHR audit logs typically capture details like user ID, role, patient ID, action type, module accessed, and session duration. When combined with additional data from network activity, endpoints, and HR systems, these logs can help identify anomalies such as unusual login times, large-scale record retrievals, or offsite access.
Key features that improve detection include patterns like unexpected activity during off-hours, high-volume or diverse record access (e.g., accessing many patient records outside the user’s usual scope), and location mismatches (such as logins from unfamiliar networks or remote locations). Peer-group comparisons also play a crucial role by measuring a clinician’s behavior against that of their colleagues. For instance, if a clinician accesses significantly more sensitive records than their peers, this could indicate either an unusual but legitimate workflow or a potentially suspicious activity that warrants further investigation.
How Anomaly Detection Prevents Data Breaches
Research Results and Case Examples
Real-time monitoring has proven to be a game changer in identifying threats faster than traditional periodic log reviews. This approach significantly reduces the time attackers can linger undetected in a system, often referred to as "dwell time" [7]. By continuously analyzing normal patterns of clinician activity - like login behavior, record access, and documentation - anomaly detection systems can quickly flag unusual actions. For example, unexpected logins or a sudden spike in bulk record views raise red flags, allowing security teams to step in before sensitive data is compromised [4][5].
Automated systems are especially effective in catching unusual behavior. Imagine a clinician who typically works in pediatrics but suddenly accesses hundreds of oncology records - this triggers an alert for immediate investigation and possibly suspending the account [4][7]. In multi-hospital networks, graph-based detection tools go even further by identifying patterns across facilities, such as repeated failed login attempts or simultaneous access spikes at different locations. These tools enable a coordinated response to potential threats [2][3]. Beyond access monitoring, studies show that anomaly detection can also uncover fraudulent billing practices or unusual test-ordering patterns, pointing to broader misuse of electronic health record (EHR) systems and internal weaknesses [5].
Modern anomaly detection systems streamline the entire process. They generate high-quality alerts that prioritize the most critical issues, cutting down the need for manual log reviews [4][5][7]. By including additional context - like the user's role or cross-system activity - these tools help security teams quickly differentiate between harmless deviations and actual breaches. This reduces investigation times significantly [5][6]. Integration with other tools, such as ticketing systems and identity management platforms, allows for automated responses like locking accounts or enforcing password resets when risk thresholds are breached [4][5].
In short, these proactive measures not only protect sensitive data but also bring compliance and cost advantages.
Compliance and Financial Impact
Real-time monitoring plays a key role in meeting HIPAA requirements by bolstering technical safeguards. These include unique user identification, automatic logoff, audit controls, and tools to authenticate and monitor access to electronic protected health information (ePHI) [7]. Automated detection of suspicious activity fulfills the obligation to "regularly review records of information system activity", a task that would be nearly impossible to handle manually at scale [7]. It also supports risk analysis and management by providing ongoing evidence of abnormal ePHI access, helping organizations refine their risk controls and mitigation strategies [4][5].
Quick detection of threats significantly reduces the time attackers or insiders have to access and exfiltrate sensitive data. This minimizes the number of affected records and the chances of reportable breaches [7]. For instance, a report from the HIPAA Journal in August 2025 highlighted 7 unauthorized access or disclosure incidents that impacted 154,768 individuals, with an average breach size of 22,110 records and a median of 3,215 records [9]. By preventing or limiting such breaches, anomaly detection helps organizations avoid hefty financial penalties tied to HIPAA violations, as well as the additional costs of breach notifications, credit monitoring, legal fees, and reputational harm [7]. Automating detection also reduces the labor-intensive work of manual log reviews and investigations, freeing up security teams to focus on more strategic risk management tasks [4][5].
Challenges in Implementing Anomaly Detection for EHRs
Data Quality and Integration Problems
One of the biggest hurdles in anomaly detection for electronic health records (EHRs) comes down to fragmented and inconsistent data. Hospital systems often rely on a mix of EHRs, identity management tools, VPNs, and clinical applications, each with its own log formats, timestamps, and user identifiers. This lack of uniformity makes it tough to establish accurate baselines for normal activity. Add in missing fields, inconsistent audit policies, and short log retention periods, and you’ve got a recipe for unreliable models that churn out false positives and negatives.
In the U.S., healthcare organizations frequently operate a hybrid of older, on-premises EHR systems and newer cloud-based applications. The absence of standardization - like inconsistent HL7 or FHIR implementations or proprietary log formats - complicates the integration of data pipelines that security analytics depend on. Without seamless integration, creating reliable behavioral baselines becomes nearly impossible. This, in turn, slows down anomaly detection, which is critical for preventing breaches.
Workflow and Operational Barriers
Data fragmentation isn’t the only issue. Real-world workflows and operations introduce their own set of challenges. High false-positive rates can overwhelm security teams and clinicians alike, leading to a loss of confidence in system alerts. For example, routine activities like covering for a colleague, consulting across departments, or reviewing charts after hours often trigger unnecessary alerts. Over time, staff may begin to ignore or override these alerts, much like they might with poorly tuned clinical decision support systems. This desensitization can leave genuine insider threats unchecked, especially when security operations centers are buried under non-actionable alerts.
Clinical workflows further complicate matters. In a fast-paced, 24/7 care environment with rotating staff, emergency overrides, and constant time pressures, the definition of "normal" is anything but static. Models need constant adjustment to account for shifting staffing patterns, temporary hires, and seasonal fluctuations in patient volume. Security measures that slow down or block EHR access are often viewed as risks to patient safety, leading organizations to err on the side of caution. This conservative tuning can reduce the effectiveness of anomaly detection and result in policy exceptions that weaken overall security.
Meeting Compliance and Governance Requirements
On top of technical and operational challenges, compliance with regulations adds another layer of complexity. Under HIPAA’s Security Rule, healthcare organizations are required to implement audit controls, monitor access, and establish procedures to protect electronic protected health information (ePHI). Anomaly detection systems must log and retain detailed audit trails without compromising data integrity or availability. Decisions about what events to log, how long to keep the data, and how to escalate alerts need to align with HIPAA’s risk-based safeguards, as well as stricter state laws or Business Associate Agreement requirements.
Regulators often scrutinize logging practices and audit trails during investigations of major healthcare breaches to determine whether reasonable safeguards were in place. Any gaps in monitoring can lead to both technical vulnerabilities and legal liabilities. Organizations must maintain thorough documentation of risk analyses, monitoring policies, and incident responses. Tools like Censinet RiskOps™ can help healthcare providers centralize risk data from EHR vendors, medical devices, and cloud services, streamline security assessments, and show continuous improvement to both boards and regulators.
sbb-itb-535baee
Risk Management Platforms for Anomaly Detection
Centralizing Risk Data for Better Visibility
Healthcare organizations rely on a variety of security tools, including EHR audit logs, IAM systems, SIEM, network monitors, and DLP solutions. Each of these generates its own alerts and anomaly signals. But when these outputs remain isolated in separate systems, security teams face a tough challenge: sorting out genuine threats from background noise. Risk management platforms tackle this issue by consolidating anomaly alerts into a single data model. They normalize signals - like unusual access patterns, failed logins, or atypical data exports - against an organization-wide inventory of assets and vendors, creating a clearer picture of potential risks.[4][7]
Platforms such as Censinet RiskOps™ take this a step further by mapping anomalies to specific EHR systems, external vendors, and business processes. They assign attributes like likelihood, PHI impact, and control gaps to these signals, helping teams link anomalies to specific applications, devices, or vendors.[4] This centralized approach eliminates blind spots, offering a single source of truth for EHR-related cyber risks. For example, a security team can connect an unusual EHR access event to a vendor's known vulnerabilities or failed controls, making it easier to prioritize critical PHI-related threats over less pressing alerts.[4][5]
Real-time dashboards enhance this process by quantifying risk exposure in financial terms, tracking incidents over time, and simplifying audit reporting for leadership.[7]
Terry Grogan, CISO at Tower Health, highlighted the efficiency gains, stating, "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."[1]
This streamlined, centralized system also lays the foundation for swift, automated responses to detected anomalies.
Automating Detection and Response Workflows
Modern platforms go beyond aggregation - they automate the entire detection and response process. By setting up rules that trigger when anomaly thresholds or risk scores are exceeded, these systems can handle incidents proactively. Imagine a scenario where a user in a non-patient-care role attempts to export thousands of EHR records. The platform can automatically flag this as a high-priority incident, notify the security operations center, and initiate actions like access reviews, account suspension, or forensic log collection.[4][5][7] Built-in templates guide analysts through root-cause analysis, evidence gathering, and corrective measures. Integration with ticketing and communication tools ensures smooth collaboration across IT, security, privacy, compliance, and clinical leadership.
Practical features include dashboards that highlight top anomalous users, departments with the highest anomaly rates, and vendors linked to unusual data flows over a given period.[4][7] Automated workflows can restrict access, enforce additional authentication, or escalate incidents like unauthorized VIP record access to privacy officers. For instance, in a potential data exfiltration case, the platform can correlate EHR anomalies with network logs, flag affected PHI categories, estimate financial exposure, and prepare summaries for breach evaluations under HIPAA.
Additionally, these platforms document every step taken during incident management, creating an auditable trail that supports HIPAA compliance and internal reviews.[7] This level of automation not only speeds up detection and response but also reduces the burden of alert fatigue.[8][10][11]
Enabling Continuous Monitoring and Risk Assessment
Once automated responses are in place, continuous monitoring ensures that risk assessments stay relevant and effective. Risk management platforms achieve this by constantly collecting anomaly data from EHRs and other systems, updating risk scores and dashboards in near real-time.[4][7] Key metrics include anomalous access rates per 1,000 users, detection-to-containment times, anomaly trends by vendor or application, and unresolved high-risk events. Platforms also evaluate their own performance, tracking false positives, false negatives, and system coverage - such as how many EHR systems and vendors are actively feeding data into the platform. Monitoring these factors helps organizations refine thresholds, improve models, and allocate resources to high-risk areas like remote access points or critical EHR modules.
Censinet RiskOps™ also supports ongoing risk assessments by standardizing vendor and system evaluations. It captures details on access controls, encryption, audit logging, and anomaly detection capabilities tied to PHI protection.[4][5] The platform maps these controls to regulatory frameworks, such as HIPAA Security Rule safeguards, and keeps them updated as new anomalies, incidents, or audit findings arise. For example, if repeated inappropriate access is detected in a vendor-supported system, the platform can adjust the vendor’s risk score, document the issue under relevant regulatory requirements, and track remediation efforts. Compliance teams benefit from dashboards that outline control effectiveness, gaps, and audit-ready evidence.[7]
Conclusion
Anomaly detection plays a critical role in safeguarding patient data across U.S. healthcare organizations. By leveraging AI-driven tools, unusual activities like unauthorized access, excessive data exports, or insider misuse can be flagged in real time. This enables swift action to secure Protected Health Information (PHI) while adhering to HIPAA requirements for access control and audit logging. To put the stakes into perspective, healthcare data breaches in 2025 exposed around 275 million records, with an average cost of $10.22 million per breach[12]. These numbers highlight the urgent need for robust detection as a foundational layer in any cybersecurity strategy.
However, anomaly detection alone is not enough. To truly protect patient data, it must work as part of a centralized risk management platform. This integration allows healthcare organizations to contextualize anomalies, automate responses, and continuously monitor risks across electronic health records (EHRs), vendors, and connected devices. Solutions like Censinet RiskOps™ are designed to address this challenge, linking flagged anomalies to specific vendors, applications, and PHI exposure levels.
The benefits of this approach extend beyond security. For example, Tower Health has reported efficiency gains through streamlined operations[1]. By reducing operational bottlenecks, healthcare teams can shift their focus toward strategic risk mitigation efforts. Combining anomaly detection with centralized governance not only strengthens defenses but also reduces the financial impact of breaches, ensures ongoing compliance, and minimizes the need for manual processes like managing alerts and spreadsheets.
As cyber threats and regulatory demands grow more complex, embedding anomaly detection into a continuously monitored risk management framework is no longer optional. With the right tools and governance, healthcare organizations can better protect sensitive patient data, meet evolving compliance standards, and build the resilience needed to navigate today’s challenging cybersecurity landscape.
FAQs
How do anomaly detection systems help prevent data breaches in electronic health records (EHRs)?
Anomaly detection systems play a crucial role in safeguarding electronic health records (EHRs) by keeping an eye on activities that stray from typical patterns. Powered by advanced AI algorithms, these systems scrutinize user behavior, access logs, and data transfers to pinpoint irregularities that could signal insider threats or unauthorized access attempts.
By identifying these anomalies as they occur, healthcare organizations can act swiftly to investigate and resolve potential security issues. This proactive approach helps protect sensitive patient data while ensuring the integrity of their records.
What challenges do healthcare organizations face when using anomaly detection in EHRs?
Healthcare organizations face a range of hurdles when trying to implement anomaly detection in electronic health records (EHRs). One of the biggest challenges is seamlessly integrating this technology into their current systems. EHR data is massive and incredibly complex, making it tricky to manage effectively. On top of that, the detection process needs to work in real-time without interfering with daily workflows.
Another key concern is reducing false positives. Too many unnecessary alerts can overwhelm staff, making it harder to focus on actual issues. At the same time, protecting patient privacy and ensuring strong data security are non-negotiable. Healthcare environments deal with highly sensitive information, so keeping it safe is always a top priority.
How does anomaly detection support HIPAA compliance in healthcare organizations?
Anomaly detection is essential for healthcare organizations striving to meet HIPAA requirements. It works by spotting unusual or suspicious behavior in electronic health records (EHRs), such as unexpected access patterns or irregular data usage. These alerts allow organizations to respond quickly to potential data breaches or insider threats.
By taking these proactive measures, healthcare providers can better protect sensitive patient information, comply with HIPAA's strict privacy and security rules, and reinforce trust in the safeguarding of health data.


