Anonymization vs. Pseudonymization: Impact on Data Security
Post Summary
Anonymization and pseudonymization are two key methods used to protect sensitive data, especially in healthcare. Here's the difference:
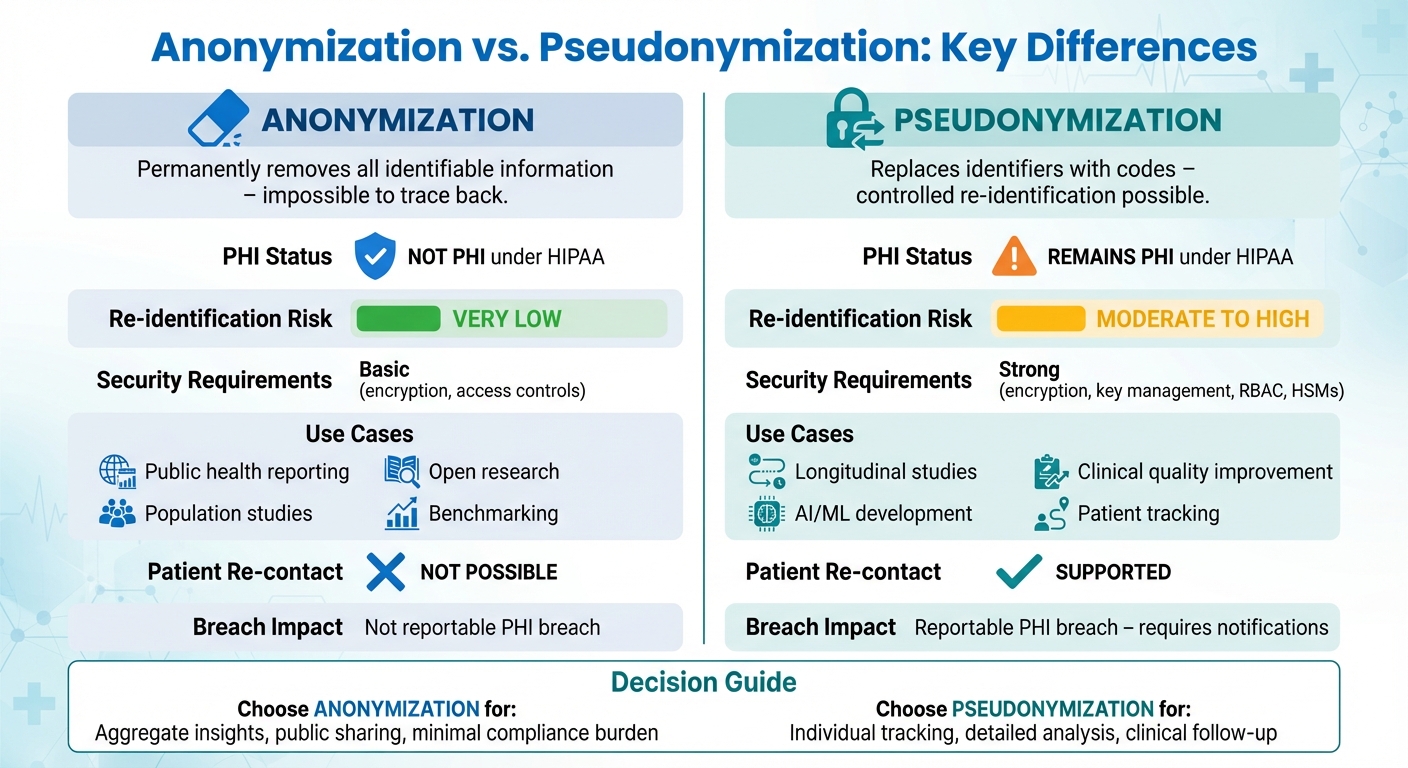
- Anonymization: Permanently removes all identifiable information, making it impossible to trace the data back to individuals. This is ideal for public health reporting and research where individual tracking isn't needed.
- Pseudonymization: Replaces identifiable details with codes, allowing controlled re-identification when necessary. This method is used for longitudinal studies, AI development, and situations requiring patient tracking.
Key Takeaways:
- Anonymized data is no longer considered Protected Health Information (PHI) under HIPAA, reducing compliance burdens.
- Pseudonymized data remains PHI and requires strict security measures, as it retains a reversible link to individuals.
- Choose anonymization for aggregate insights and pseudonymization for detailed, patient-level analysis.
Quick Comparison:
| Factor | Anonymization | Pseudonymization |
|---|---|---|
| Re-identification Risk | Very low | Moderate to high |
| PHI Status | Not PHI under HIPAA | Remains PHI under HIPAA |
| Use Cases | Public health reporting, open research | Longitudinal studies, AI, clinical use |
| Security Requirements | Basic (encryption, access controls) | Strong (encryption, key management) |
Both methods play distinct roles in balancing privacy, compliance, and data usability. Selecting the right approach depends on whether individual-level tracking or broader aggregate insights are required.
Anonymization vs Pseudonymization: Key Differences in Healthcare Data Protection
Anonymization and Pseudonymization Explained
Protecting patient privacy is a cornerstone of healthcare operations. Two key methods - anonymization and pseudonymization - play a vital role in safeguarding patient information, but they differ significantly in how they function and what they are used for.
What is Anonymization?
Anonymization is a process that ensures data cannot be traced back to an individual, even when combined with other data sources [1][4]. Once data is anonymized, the connection to a specific person is permanently removed, making re-identification impossible.
Healthcare organizations use various techniques to anonymize data. These include:
- Suppression: Removing sensitive details.
- Generalization: Replacing specific information, like exact birth dates, with broader categories such as age ranges.
- Aggregation: Combining individual records into summary statistics.
Another approach is differential privacy, which introduces controlled noise into datasets. This method ensures that the inclusion or exclusion of a single patient has minimal effect on the results while maintaining overall trends [1][2]. For example, a health system might release national COVID-19 statistics by state, age group, and week, suppressing rare data combinations to prevent individual identification [1][7].
Because anonymized data cannot be linked back to individuals, it often falls outside the scope of Protected Health Information (PHI) regulations, allowing for broader use in public health initiatives and research [1][2][4].
While anonymization completely removes personal identifiers, pseudonymization offers a way to retain controlled re-identification for specific purposes.
What is Pseudonymization?
Unlike anonymization, pseudonymization allows for re-identification under strict controls. This method replaces direct identifiers - like names, Social Security numbers, or medical record numbers - with artificial identifiers, such as tokens or codes. However, a separate, securely stored mapping system maintains the ability to reconnect the data to the individual when necessary [1][3][6]. For instance, a dataset might use "PAT_000123" instead of a patient's name, with a separate linkage table securely stored to map that code back to the individual [1][3].
Pseudonymization requires robust security measures, including tokenization, key management systems, and governance protocols, to ensure only authorized personnel can access re-identification tools. For example, in a long-term diabetes study, patient names and Social Security numbers might be replaced with unique codes. Researchers could then analyze lab results, medications, and treatment timelines while maintaining the ability to re-identify patients if necessary for clinical interventions [2][5]. If a high-risk pattern is detected, clinicians with proper authorization could use the mapping table to identify and assist the affected patient [2][5].
A key distinction is that pseudonymized data is still classified as PHI under HIPAA because it retains a link to the individual [1][2][3]. This means organizations must enforce stringent security controls for both the pseudonymized data and the re-identification keys [3][8]. Platforms like Censinet RiskOps™ help healthcare organizations evaluate third-party tools handling pseudonymized PHI, assess cybersecurity risks, and manage remediation plans to minimize re-identification risks and breaches across systems.
Choosing between anonymization and pseudonymization, along with implementing strong risk management strategies, is essential for balancing data security with the need for meaningful healthcare insights.
How Each Method Affects Healthcare Regulations
In the U.S., anonymization and pseudonymization are treated differently under healthcare regulations, which impacts data sharing and breach notification requirements. Here’s how each method aligns with HIPAA and other key rules.
Anonymization and HIPAA Compliance
HIPAA provides two pathways for de-identifying data: the Safe Harbor method and the Expert Determination method.
- Safe Harbor: This approach requires removing 18 specific identifiers, such as names, full-face photos, phone numbers, email addresses, Social Security numbers, medical record numbers, and all date elements except the year. By eliminating these details, the likelihood of identifying individuals is significantly reduced.
- Expert Determination: In this method, a qualified expert uses scientific principles to confirm that the risk of re-identification is very minimal. This option allows organizations to keep more detailed data - like age ranges, three-digit ZIP codes, or limited dates - while still meeting HIPAA standards. This retained granularity is especially useful for healthcare analytics and studies that rely on detailed data, such as real-world evidence research.
Once data is de-identified using either method, it is no longer classified as Protected Health Information (PHI). This means it falls outside the scope of HIPAA’s Privacy Rule, Security Rule, and breach notification requirements. As a result, organizations face fewer compliance burdens and legal risks. Moreover, anonymized data can be shared externally without requiring patient consent, offering greater flexibility for research and collaboration efforts [1][2][4].
Unlike pseudonymization, anonymization completely severs the link to individuals, removing HIPAA obligations entirely.
Pseudonymization and PHI Status
Pseudonymization, on the other hand, replaces personal identifiers with codes but keeps a reversible link to individuals. Because re-identification is still possible, pseudonymized data remains classified as PHI under HIPAA [2][8]. This means all HIPAA and HITECH requirements - such as the Privacy Rule, Security Rule, breach notification obligations, and Business Associate Agreements - continue to apply [4][7].
Organizations handling pseudonymized data must implement stringent safeguards. These include:
- Strict access controls to limit who can view or use the data
- Strong encryption to protect information
- Detailed audit logs to track data access and usage
- Secure and separate management of re-identification keys
When sharing pseudonymized data with vendors or business associates, healthcare organizations must ensure these partners maintain equally rigorous security measures. Tools like Censinet RiskOps™ can help standardize third-party security assessments and monitor compliance for systems handling pseudonymized PHI. This ensures that re-identification risks are effectively managed across the entire vendor network.
The regulatory implications of pseudonymization are significant. If anonymized data is compromised, it typically does not trigger HITECH breach notification requirements because the information is no longer tied to individuals [2][4]. However, any unauthorized disclosure of pseudonymized PHI is considered a reportable breach, requiring notifications to affected individuals, the Department of Health and Human Services (HHS), and sometimes even the media [2][6][8]. These distinctions are critical when shaping an organization’s data security and compliance strategies.
Security and Risk Management Differences
Understanding the nuances of security and risk management between anonymization and pseudonymization is key to protecting sensitive data effectively.
Re-Identification Risks and Security Controls
One of the biggest differences lies in re-identification risk. Properly anonymized data is designed to minimize this risk to a very low level. However, outdated or weak anonymization techniques can be vulnerable to advanced linkage attacks. For example, hospital discharge data that hasn't been anonymized effectively can be re-identified by cross-referencing dates, ZIP codes, and demographic details with voter records or commercial databases [1][3].
Pseudonymized data, on the other hand, is inherently more vulnerable to re-identification because the connection to individuals is deliberate and reversible. Anyone with access to the mapping table or re-identification key can restore the dataset to its original, identifiable form. For instance, in a diabetes study, patient records might be coded as "PAT_12345", with a secure lookup table enabling the care team to re-link data for follow-up. If an attacker gains access to this key or table, the entire dataset can be re-identified [1][2][5].
To manage this risk, pseudonymized data requires robust technical safeguards. Organizations must encrypt both the pseudonymized data and re-identification keys using state-of-the-art encryption standards. Role-based access control (RBAC) and least-privilege principles should ensure that only a small, auditable group can perform re-identification. Additionally, key management practices - such as segregated key storage, hardware security modules (HSMs), regular key rotation, and separation of duties - are critical to prevent unauthorized access. Continuous monitoring and detailed logging of data access and re-identification activities further reduce the chances of misuse [1][2][8].
While anonymized data carries less risk, it still requires encryption and access controls to defend against emerging re-identification techniques. These measures also protect organizations from business risks, such as intellectual property theft, model inversion attacks on training data, or reputational harm from sensitive patterns being exposed [1][3][7]. Typically, healthcare organizations apply less stringent controls to anonymized data - allowing broader access within research networks - while reserving the strictest measures for pseudonymized data and protected health information (PHI) [1][2].
Censinet RiskOps™ simplifies these risk management efforts by enabling assessments of both enterprise and third-party risks. It benchmarks security controls for PHI and clinical applications, while also providing tools for collaborative remediation plans with vendors handling anonymized or pseudonymized healthcare data. This approach ensures security measures are tailored to the specific re-identification risk profile of each dataset.
Comparison Table: Anonymization vs. Pseudonymization
| Factor | Anonymization | Pseudonymization |
|---|---|---|
| PHI/Personal Data Status | Not PHI when de-identified under HIPAA Safe Harbor or Expert Determination [4][7] | Remains PHI under HIPAA; personal data under GDPR [1][2][4][8] |
| Re-Identification Possibility | Practically irreversible with proper techniques; residual risk from auxiliary data linkage [1][3] | Intentionally reversible with access to mapping key or lookup table [1][2][9] |
| Re-Identification Risk Level | Very low (often targeting thresholds below 0.05–0.09 per record) [3] | Moderate to high; single point of failure (key compromise) restores full identity [1][2][8] |
| Required Security Controls | Baseline encryption and access control to protect aggregate patterns and IP [1][3][7] | Strong encryption, RBAC, HSMs, key segregation, audit logging, and separation of duties [1][2][8] |
| Breach Impact | Typically not a reportable PHI breach; reduced regulatory exposure and notification obligations [4][7] | Treated as PHI breach; triggers HIPAA breach notification, OCR investigations, potential fines [1][2][8] |
| Data Utility | Reduced granularity; suitable for public research, benchmarking, open datasets [1][2][3] | High granularity preserved; enables longitudinal tracking, clinical follow-up, fraud detection [1][2][4] |
| Long-Term Risk Trajectory | Risk may increase as new auxiliary datasets and analytics techniques emerge [1][3] | Risk persists as long as re-identification keys exist; requires ongoing key management [1][2] |
sbb-itb-535baee
Use Cases and Data Usability
Choose anonymization for broad, aggregated insights and pseudonymization when individual-level data tracking is essential.
When to Use Anonymized Data
Anonymized data works best for analyzing trends at the population level, where individual tracking isn't required. For example, public health reporting often relies on anonymized data to provide de-identified statistics like influenza case counts or opioid overdose rates. Metrics such as hospitalization rates per 100,000 people or mortality rates by age group and county are commonly used. State health departments and the CDC use these aggregated insights to monitor disease patterns without needing to identify or re-contact specific patients [1][7].
This approach is also valuable in population health research. Studies on chronic disease prevalence, vaccination coverage, or preventive screening rates often use anonymized claims or EHR data that meet HIPAA de-identification standards. To maintain privacy, data is generalized - exact dates of birth become age ranges, full addresses are replaced with three-digit ZIP codes, and rare diagnoses are excluded. While this reduces the risk of re-identification, it also limits the granularity of the analysis [1][2][4][7].
Health systems also use anonymized data for benchmarking and quality reporting. Metrics like 30-day readmission rates, lengths of stay, and complication rates are compared across institutions, with small data groups suppressed to avoid re-identification. Since anonymized data is not considered PHI under HIPAA, it can be shared freely in open data portals and research datasets without triggering breach notifications [1][2][4][7].
On the other hand, pseudonymization is the better option when individual-level analysis is required.
When to Use Pseudonymized Data
Pseudonymization is ideal for linking records over time or across systems, making it essential for longitudinal clinical studies. For instance, tracking diabetes patients' A1c levels, medication adherence, and complications over several years requires consistent pseudonyms like "Patient_001" to connect data points across multiple encounters [1][2]. Without this linkage, studying disease progression or treatment outcomes at the individual level would be impossible.
Similarly, AI and machine learning models depend on pseudonymized data. For example, readmission prediction models require multi-year patient histories, including comorbidities, lab results, and medication data, all tied to the same individual. Sepsis early warning systems also rely on detailed, time-sensitive data linked to specific patient episodes. Pseudonymization replaces direct identifiers with tokens, ensuring that rich, patient-level details remain intact for accurate predictions [1][2][6].
Clinical quality improvement efforts benefit significantly from pseudonymized data. Hospitals use it to measure granular performance metrics, such as door-to-balloon times for heart attack patients or surgical complication rates. When needed, secure mapping tables allow quality teams to re-identify specific patients for follow-up, something anonymized data cannot support [2][4].
The table below highlights the differences in data usability for anonymization and pseudonymization:
Comparison Table: Data Usability
| Use Case | Anonymization | Pseudonymization |
|---|---|---|
| Public health reporting | Great for rates and trends without patient re-contact [1][2][7] | Possible but unnecessary; adds more risk than needed for public data [1][2] |
| Population health studies | Suitable for incidence and prevalence analysis [1][2][4] | Overkill unless individual tracking is required [1][2] |
| Longitudinal research | Limited; lacks stable patient links [1][2] | Ideal; allows tracking over time with stable pseudonyms [1][2][5] |
| AI/ML model training | Works for some models but sacrifices detail [2][7] | Preferred; retains detailed features for better accuracy [2][6][7] |
| Clinical quality improvement | Useful for high-level benchmarking but weak for case-level analysis [1][2] | Strong fit; supports detailed case tracking and follow-up [1][2][6] |
| External data sharing | Easier to share; not PHI under HIPAA when de-identified [1][2][4][7] | Requires strong safeguards; remains PHI [1][2][4] |
| Patient re-contact capability | Not possible [1][2][4] | Supported through secure re-identification [1][2][4][5] |
Many healthcare organizations in the U.S. adopt a tiered approach: anonymized datasets for external research and public reporting, pseudonymized datasets for internal research and quality improvement, and fully identified data only for direct patient care. Tools like Censinet RiskOps™ help align security measures with the re-identification risks of each dataset, ensuring appropriate safeguards for every use case.
Conclusion
Deciding between anonymization and pseudonymization in healthcare data management comes down to balancing privacy, regulatory requirements, and the specific needs of your workflow. Anonymization permanently removes identifiable information, meaning the data is no longer considered PHI under HIPAA. This reduces the risk of breaches and compliance obligations [4][7], but it also eliminates the ability to track individuals. On the other hand, pseudonymization retains patient-level details, enabling longitudinal studies and advanced analytics. However, because pseudonymized data is still classified as PHI, it requires strict safeguards like encryption, secure key management, and controlled access [8].
Anonymization works best for situations like public data sharing, producing population-level insights, or minimizing compliance risks over time. Pseudonymization is ideal when patient tracking is essential, such as for AI model development, advanced analytics, or issuing safety alerts that may require selective re-identification.
These choices directly shape an organization’s risk management strategy. A practical approach is to use anonymized data for external research and public reporting, pseudonymized data for internal analytics and clinical studies, and fully identified data only for direct patient care. This tiered strategy ensures data is used effectively while minimizing risk for each purpose. To support this, organizations should adopt a formal data classification and protection policy that clearly defines when anonymization or pseudonymization is appropriate. Tools like Censinet RiskOps™ can help integrate these de-identification methods into a centralized, auditable framework.
As part of this strategy, continuous monitoring and policy updates are critical. Regularly reviewing security incidents, staying informed about re-identification risks, and learning from experience allow organizations to refine their policies. This adaptability ensures healthcare providers can align their practices with evolving regulations and risk tolerance.
FAQs
What’s the difference between anonymization and pseudonymization when it comes to re-identification risks?
Anonymization works by stripping away or modifying personal identifiers, making it difficult to trace data back to an individual. While this approach greatly reduces the chances of someone being re-identified, it’s not an absolute guarantee in every situation.
Pseudonymization, on the other hand, swaps out personal identifiers for pseudonyms - like codes or aliases. This method protects privacy to an extent, but since the original data can still be reconnected if additional details are available, it’s not as secure as anonymization in preventing re-identification.
Both techniques are essential for ensuring data security and meeting compliance standards, particularly in sensitive areas like healthcare, where protecting patient information is crucial.
What’s the difference between anonymization and pseudonymization when it comes to HIPAA compliance?
Anonymization and pseudonymization play distinct roles when it comes to HIPAA compliance.
Anonymization involves stripping away all identifiable information from data, rendering it unrecognizable as Protected Health Information (PHI) under HIPAA. This means the data is no longer subject to HIPAA regulations. However, while this approach removes compliance burdens, it often comes at the cost of reducing the data’s value for purposes like research or analysis.
Pseudonymization, in contrast, substitutes identifiers with codes or pseudonyms that can be reversed if needed. This method strikes a balance by preserving the data’s usefulness while still requiring safeguards to prevent re-identification. HIPAA’s Security Rule mandates that organizations implement robust measures to protect pseudonymized data, ensuring it remains secure and compliant.
The choice between these methods depends on your organization’s priorities - whether the focus is on maximizing data utility or ensuring the highest level of security.
When is pseudonymization a better choice than anonymization for managing healthcare data?
Healthcare organizations often turn to pseudonymization when they need to keep the option of re-identifying data for critical tasks like patient care, clinical research, or fulfilling regulatory obligations. Unlike anonymization - which permanently strips away identifying details - pseudonymization retains the ability to link data back to individuals, but only under tightly controlled conditions. This method strikes a balance between preserving data usability and ensuring security.
Pseudonymization proves especially useful in cases where patient information must stay accessible for ongoing treatments or research. At the same time, it helps protect sensitive data from unauthorized access, lowering the chances of potential breaches.


