BAA Requirements for PHI Sharing
Post Summary
A BAA is a legally binding contract required under HIPAA that governs the sharing of Protected Health Information (PHI) between covered entities and business associates.
A BAA is required whenever a covered entity shares PHI with a business associate or subcontractor for purposes other than treatment, payment, or healthcare operations.
Key elements include permitted uses of PHI, safeguards to protect PHI, breach notification requirements, and compliance with HIPAA privacy and security rules.
Risks include regulatory penalties, data breaches, and non-compliance with HIPAA requirements.
By maintaining a repository of signed BAAs, conducting periodic reviews, and ensuring vendors meet HIPAA standards.
Subcontractors who access PHI must also sign BAAs with the business associate to ensure compliance.
A Business Associate Agreement (BAA) is a mandatory contract under HIPAA that ensures Protected Health Information (PHI) is shared securely and legally between healthcare organizations (covered entities) and their vendors or partners (business associates). Without a signed BAA, both parties risk noncompliance and hefty fines. Here's what you need to know:
- What is PHI? Any health information that identifies an individual, such as names, medical records, or contact details.
- Who needs a BAA? Vendors like EHR platforms, cloud storage providers, billing companies, and IT support that handle PHI on behalf of covered entities.
- Key requirements of a BAA:
- Define how PHI can and cannot be used.
- Mandate security measures like encryption and access controls.
- Require breach reporting within strict timelines.
- Specify how PHI is returned or destroyed after the contract ends.
- Common scenarios requiring BAAs: Using cloud services, telehealth platforms, or analytics tools that process PHI.
Failing to establish a BAA before sharing PHI can lead to severe penalties, with enforcement by the HHS Office for Civil Rights. To stay compliant, organizations should maintain an updated inventory of business associates, conduct security assessments, and centralize BAA management. Tools like Censinet RiskOps™ can help streamline this process by integrating risk assessments and documentation.
BAAs are more than just contracts - they're critical for protecting patient data and managing compliance risks effectively.
Required Elements of a HIPAA-Compliant BAA
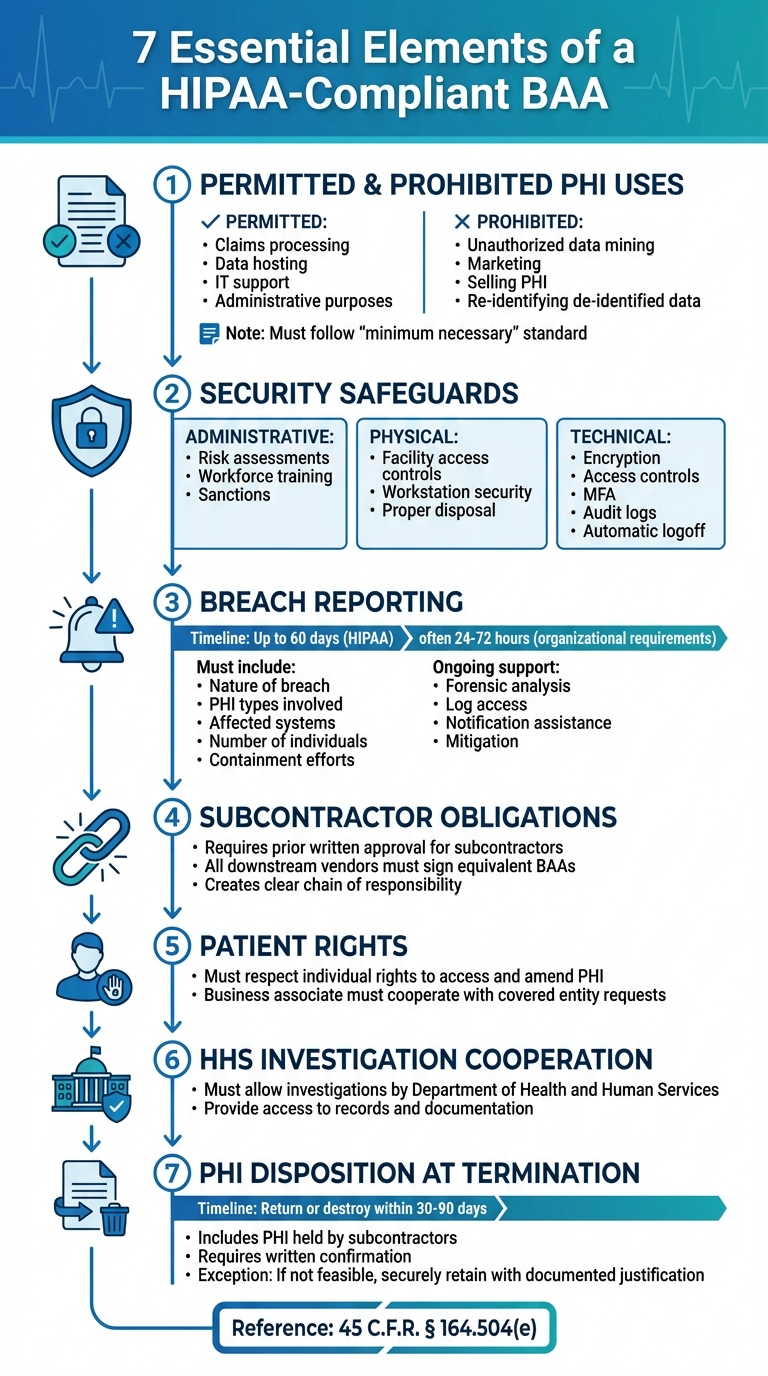
7 Essential Elements of a HIPAA-Compliant Business Associate Agreement
HIPAA regulations ensure that Business Associate Agreements (BAAs) provide clear guidelines for managing and protecting Protected Health Information (PHI). According to 45 C.F.R. § 164.504(e), every BAA must meet specific legal requirements to safeguard both parties and guarantee proper PHI handling. A compliant BAA outlines authorized uses of PHI, mandates security measures, requires breach reporting, extends obligations to subcontractors, respects patient rights, allows investigations by the Department of Health and Human Services (HHS), and specifies how PHI should be handled when the agreement ends. Beyond these essential elements, well-crafted BAAs often include additional details like breach notification timelines, defined security protocols, audit rights, and documentation requirements to make compliance more actionable.
Permitted and Prohibited Uses of PHI
A BAA must clearly define how PHI can and cannot be used. Permitted uses typically cover activities necessary to fulfill the contract, such as claims processing, data hosting, or IT support. Additionally, the agreement may allow limited uses for the business associate’s internal needs, such as administrative or legal purposes. Importantly, the agreement enforces the "minimum necessary" standard, ensuring PHI use is restricted to what’s essential for these purposes.
Equally critical are prohibited uses. The BAA must explicitly state that the business associate "shall not use or further disclose PHI other than as permitted or required by this Agreement or as required by law." This includes banning unauthorized activities like data mining, analytics across customers, or product development unless the data is appropriately de-identified. Marketing and selling PHI are strictly forbidden without HIPAA-compliant authorization, and re-identifying de-identified data is not allowed. For example, a vendor managing revenue cycles cannot use one hospital’s patient data to create analytics tools for another health system unless explicitly permitted and compliant with HIPAA’s data aggregation rules. These usage restrictions tie directly to the safeguards outlined in the next section.
Required Safeguards and Breach Reporting
To ensure PHI is protected, the BAA mandates comprehensive administrative, physical, and technical safeguards in line with the HIPAA Security Rule. These include measures like regular risk assessments, workforce training, sanctions for violations, controlled facility access, secure workstation setups, proper disposal procedures, and access controls featuring unique user IDs and multi-factor authentication. Additionally, encryption of electronic PHI (ePHI) during transmission and storage, audit logs, automatic logoff features, and secure communication protocols are essential components.
For breach reporting, the BAA must require the business associate to notify the covered entity of any unauthorized use or disclosure of PHI, including security incidents and breaches involving unsecured PHI. While HIPAA allows up to 60 days for notification, many healthcare organizations set stricter deadlines, often requiring initial notice within 24 to 72 hours. These notices should include key details such as the nature of the breach, the types of PHI involved, affected systems, the approximate number of individuals impacted, and initial containment efforts. The agreement should also ensure the business associate provides ongoing support, such as forensic analysis, access to logs, assistance with notifications to individuals and HHS, mitigation efforts like credit monitoring, and full documentation for regulatory purposes.
Handling PHI at Contract Termination
When a contract ends, the BAA must address the proper disposition of PHI. Typically, the business associate is required to return or securely destroy all PHI received or created on behalf of the covered entity, including any PHI held by subcontractors, within a specified timeframe (commonly 30 to 90 days). Written confirmation detailing which PHI was returned or destroyed and verifying the completion of the process is usually required.
However, HIPAA acknowledges that return or destruction may not always be feasible. In such cases, the business associate must securely retain the PHI and limit its use to storage or legal retention, providing documented justification for this exception. The agreement should also include survival clauses to ensure confidentiality, restrictions on use, and cooperation in breach investigations continue even after the formal end of the contract.
Common PHI Sharing Scenarios and BAA Structure
PHI Sharing Use Cases Requiring BAAs
Before any Protected Health Information (PHI) is shared, certain vendors and service providers must sign a Business Associate Agreement (BAA). This includes cloud hosting providers like AWS, Azure, and Google Cloud, which have system-level access to environments containing electronic PHI (ePHI) [2]. Similarly, BAAs are essential for telehealth platforms that combine video consultations with scheduling systems, mobile health apps transmitting vital signs, and dashboards used for remote patient monitoring [1][2]. Communication tools like secure messaging services, appointment reminder systems, and patient engagement platforms that handle PHI also fall under this requirement [1][3].
Medical device integrations - such as networked imaging systems, infusion pumps, and connected devices that transmit PHI to vendor-hosted clouds or monitoring centers - must have agreements in place before deployment [3]. Managed IT service providers, including help desk vendors, backup services, and SOC/SIEM providers, are often overlooked but also require BAAs due to their system-level access to environments containing PHI [1][3]. The rule is straightforward: if a vendor creates, receives, maintains, or transmits PHI while performing services for or on behalf of a covered entity, a BAA is mandatory [1][2][3]. These scenarios highlight the importance of tailoring BAAs to address the specific risks associated with each service.
De-Identification and Limited Data Sets
Once PHI is de-identified using HIPAA's safe harbor method or expert determination, the data no longer qualifies as PHI and can be shared without a BAA [2]. However, if a vendor assists with the de-identification process, they must first access PHI, which means a BAA is required for that activity [1][2].
Limited data sets represent a middle ground. These datasets exclude direct identifiers like names, street addresses, phone numbers, and Social Security numbers but may retain certain details such as dates and geographic information (e.g., city, state, ZIP code) [2]. Since limited data sets are still considered PHI under HIPAA, their use requires a Data Use Agreement (DUA). The DUA must outline permitted uses, who can access the data, restrictions on re-identification, and the safeguards that must be in place [2]. For example, if an analytics vendor creates quality dashboards using a limited data set, the organization can address this through a standalone DUA or incorporate a DUA section within the BAA. This approach helps clarify how full PHI and limited data sets are handled differently [1][2].
Best Practices for Structuring BAAs
A well-crafted BAA goes beyond generic templates to address the unique risks and workflows of each vendor relationship. These agreements should include detailed provisions, such as encryption standards, requirements for audit log retention, vulnerability management processes, and incident response Service Level Agreements (SLAs) that align with HIPAA Security Rule standards [1][3].
To ensure clarity, organizations should attach a scope of services exhibit that specifies the systems, data types, and PHI uses. The agreement should tie permitted uses directly to this scope while explicitly prohibiting unauthorized secondary uses, such as cross-customer analytics or product development, unless explicitly approved [1][2]. Additionally, BAAs should address technical standards, cross-border data transfer protocols, and subcontractor accountability. For example, the agreement should require prior written approval before adding subcontractors and mandate that all downstream vendors sign equivalent BAAs, creating a clear chain of responsibility [2][3]. These elements help ensure that BAAs are not only compliant but also effective in safeguarding PHI.
Implementing BAA Compliance
Vendor Risk Assessments and Monitoring
Once BAAs are in place to safeguard PHI, the next step is implementing robust compliance measures. Before finalizing a BAA, ensure the vendor qualifies as a business associate. After confirmation, conduct a detailed security and privacy risk assessment. This should cover areas like administrative, physical, and technical safeguards, including access controls, encryption standards, incident response plans, audit logging, business continuity strategies, and oversight of subcontractors. To validate the vendor’s security practices, request independent evidence such as SOC 2 Type II reports, HITRUST certifications, or results from recent penetration tests. For vendors handling large volumes of sensitive ePHI or providing critical services, reassessments should occur annually. Moderate-risk vendors can follow a reassessment cycle of one to two years. Major incidents, changes in service scope, or control failures should also trigger immediate reassessments.
Monitoring doesn’t stop after the initial assessment. BAAs should require vendors to report any unauthorized access or disclosures of PHI, including breaches of unsecured PHI. Vendors must also make security and privacy records available for audits or investigations. Maintain a risk-based schedule to periodically distribute security questionnaires, monitor incident and breach reports involving PHI, and review significant changes like acquisitions or platform migrations. Track vendor performance against SLA and BAA requirements, including breach notification timelines and support for access and amendment requests. If a vendor shows repeated or significant noncompliance, escalate to formal remediation plans - or terminate the contract if allowed under the BAA.
Centralized BAA Management
Decentralized vendor management can lead to compliance gaps. To mitigate this, designate a single system of record for all BAAs. This system should capture essential details like the contract owner, vendor name, services provided, types of PHI handled, execution and renewal dates, and termination status. Standardizing BAA templates across the organization - with clear instructions on non-negotiable clauses - ensures consistency and minimizes the risk of weakening critical protections. It’s also crucial to integrate BAA tracking into procurement and onboarding workflows. No vendor should be activated or paid until their BAA status is verified and documented.
Assign clear ownership of BAAs to legal, compliance, or the business sponsor to maintain accountability for monitoring and renewal. Conduct periodic reconciliations across departments - legal, supply chain, IT, security, and accounts payable - to identify vendors that should have BAAs but don’t. This issue is especially common in U.S. health systems with decentralized purchasing processes. BAAs should also be reviewed during major contract changes, expansions, or technology updates to ensure permitted uses, PHI categories, and safeguards remain accurate. Contract management tools can help flag BAAs for review before renewal dates, while staying updated on HHS regulatory changes ensures standard BAA language remains compliant. Platforms like Censinet RiskOps™ can further simplify these processes by integrating compliance workflows with specialized tools.
How Censinet RiskOps™ Supports BAA Compliance
BAA compliance requires ongoing risk management, and Censinet RiskOps™ provides a cloud-based platform to streamline this process. It helps healthcare organizations manage third-party risk assessments, cybersecurity benchmarks, and collaborative oversight of PHI and related assets. Using Censinet RiskOps™, healthcare delivery organizations can distribute security and privacy questionnaires tailored to HIPAA and BAA standards, collect supporting evidence like policies and certifications, and automatically score vendor risk. This helps determine if a BAA is necessary and identifies the safeguards required.
The platform also supports continuous monitoring by tracking remediation tasks, reassessment timelines, and risk trends across vendors. It creates a shared workspace for privacy, security, and compliance teams, making it easier to document due diligence and show that BAAs are backed by a structured risk management process. By centralizing these efforts, Censinet RiskOps™ simplifies compliance and strengthens the organization’s overall approach to managing vendor relationships.
sbb-itb-535baee
Risks and Consequences of Noncompliance
Regulatory Penalties and Enforcement Trends
Failing to establish a required Business Associate Agreement (BAA) before sharing Protected Health Information (PHI) is a clear HIPAA violation. The HHS Office for Civil Rights (OCR) has the authority to enforce penalties, which can range from a few hundred dollars to tens of thousands per violation. These penalties are tiered based on the level of responsibility, from "did not know" violations to cases of "willful neglect not corrected." Annual caps on fines also vary depending on the severity of the misconduct. Between 2003 and 2023, OCR received over 300,000 HIPAA complaints, conducting thousands of investigations that often resulted in settlements reaching hundreds of thousands or even millions of dollars.
Recently, OCR has focused more on holding business associates accountable for violations of the Security Rule and for failing to protect electronic PHI (ePHI). Common issues identified during audits include missing or outdated BAAs, inadequate risk assessments of vendors handling ePHI, weak security measures (such as lack of encryption or poor access controls), and delays in breach notifications. In some cases, organizations cannot even provide a complete list of their business associates or the corresponding BAAs, exposing significant governance failures. Additionally, OCR treats missing or deficient BAAs as an aggravating factor when calculating penalties, and each unauthorized disclosure of PHI can be counted as a separate violation. These enforcement patterns make it clear that strong contractual safeguards are essential.
Reducing Liability Through Well-Structured BAAs
A well-crafted BAA isn't just about HIPAA compliance - it’s also a critical tool for limiting financial risk. As discussed earlier, a strong BAA includes clear provisions for incident reporting and security safeguards. Contracts with robust clauses - such as indemnification, insurance requirements, and limitation-of-liability terms - help ensure that the party responsible for a breach covers the associated costs, including investigation, notification, and remediation expenses. Without these protections, covered entities may end up bearing the brunt of breach-related costs, such as class-action settlements, legal fees, and indemnity payments.
Detailed reporting timelines and cooperation clauses in a BAA can help organizations meet HIPAA and state-specific breach-notification deadlines, reducing the risk of higher penalties for delays or incomplete reporting. By requiring safeguards that align with the Security Rule, regular risk assessments, and subcontractor controls, a well-structured BAA demonstrates that the organization has taken "reasonable and appropriate" steps to protect PHI. Key elements of an effective BAA include:
- Clear definitions of permitted and prohibited PHI uses
- Minimum administrative, physical, and technical safeguards
- Detailed breach reporting procedures
- Subcontractor BAA requirements
- Audit rights
- Data return or destruction protocols upon contract termination
This level of clarity and detail strengthens an organization’s ability to manage risks effectively.
Risk Mitigation Strategies
Managing risk starts with keeping an up-to-date inventory of all business associates and their BAAs. Before entering into a contract, organizations should conduct thorough, risk-based due diligence on vendors, requiring proof of strong security practices. This might include certifications like SOC 2 or HITRUST, or reports from penetration tests, depending on the sensitivity and volume of PHI involved.
Technical safeguards are another critical component. Measures like role-based access controls, encryption (both during transmission and storage), multi-factor authentication, and centralized logging help protect against unauthorized access. Comprehensive staff training and strict adherence to the "minimum necessary" principle further reduce the chances of accidental or unauthorized disclosures.
Organizations should also establish clear internal policies outlining when a BAA is required, who has the authority to approve them, and how contracts are reviewed for HIPAA compliance. Regular internal audits can ensure that all signed BAAs are up to date, meet regulatory standards, and accurately reflect how PHI is being used and shared.
Tools like Censinet RiskOps™ can simplify this process by centralizing vendor risk assessments. These platforms allow healthcare organizations to map out each vendor’s role and access to PHI, ensuring that a current and compliant BAA is in place before any PHI is shared. This centralized method not only streamlines documentation but also supports OCR audits, internal reviews, and reporting to leadership.
Conclusion
Key Points Recap
A Business Associate Agreement (BAA) isn't just a regulatory requirement - it's a critical document that ensures the lawful and secure sharing of Protected Health Information (PHI). Before any vendor interacts with PHI on your behalf, a written BAA must be in place. This agreement should clearly outline what the vendor can and cannot do with PHI, mandate safeguards (administrative, physical, and technical), and establish obligations like breach reporting and cooperation. Strong BAAs also cover individual rights (such as access and amendment), extend HIPAA responsibilities to subcontractors, and define how PHI will be returned or destroyed when the partnership ends.
Failing to secure proper BAAs can result in steep penalties and enforcement actions. The Office for Civil Rights (OCR) has repeatedly flagged the lack of a BAA as a major compliance failure [2][4].
To avoid these risks, organizations need practical strategies for BAA compliance. This involves keeping an up-to-date list of all business associates, integrating BAA reviews into vendor onboarding processes, using standardized templates with pre-approved legal language, and conducting thorough due diligence before signing agreements. Regular audits ensure that BAAs stay current, meet HIPAA standards, and accurately reflect how PHI is managed.
Many healthcare organizations are turning to centralized risk management platforms to simplify these efforts. Tools like Censinet RiskOps™ consolidate vendor risk assessments, PHI workflows, and BAA documentation into a single system, improving oversight and accountability. As Tower Health Chief Information Security Officer Terry Grogan explained:
Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required.
This kind of integration supports a more streamlined and thorough approach to PHI security.
A well-structured BAA framework, combined with robust vendor risk management and centralized oversight, can significantly reduce regulatory, financial, and reputational risks. BAAs are just one piece of your broader HIPAA compliance strategy; they must align with your policies, training, technical safeguards, and incident response plans. By treating BAAs as strategic tools for managing risk - not just paperwork - you can confidently share PHI in a secure and compliant manner. Incorporating BAAs into your overall risk management approach ensures that every PHI-sharing initiative is handled responsibly and strategically.
FAQs
What happens if a Business Associate Agreement (BAA) is not in place?
Failing to establish a Business Associate Agreement (BAA) can have serious consequences. Without this critical agreement, organizations may find themselves in violation of HIPAA regulations, potentially facing hefty fines, legal challenges, and harm to their reputation.
Moreover, not having a BAA in place raises the risk of unauthorized disclosures of Protected Health Information (PHI). In such cases, the covered entity bears responsibility for compliance violations. This can erode patient trust and leave the organization vulnerable to additional penalties and operational disruptions.
What steps can organizations take to stay compliant with BAA requirements when sharing PHI?
To comply with the requirements of a Business Associate Agreement (BAA), organizations need to take consistent and well-planned actions. Here are some key practices to consider:
- Review and update BAA terms regularly: Ensure agreements reflect the latest regulatory changes and requirements.
- Train staff periodically: Provide employees with clear guidance on their responsibilities related to protected health information (PHI).
- Leverage specialized tools: Use platforms designed to automate risk assessments and track PHI data sharing to streamline compliance efforts.
- Document compliance activities: Maintain thorough records to showcase accountability and readiness for audits.
Focusing on these measures helps organizations protect sensitive patient information while staying aligned with regulatory expectations.
What’s the difference between a Business Associate Agreement (BAA) and a Data Use Agreement (DUA)?
A Business Associate Agreement (BAA) is a legal contract required under HIPAA that defines the obligations of a business associate when handling protected health information (PHI) on behalf of a covered entity. The agreement emphasizes maintaining HIPAA compliance and protecting patient data from unauthorized access or breaches.
On the other hand, a Data Use Agreement (DUA) is commonly used in research or data-sharing contexts. It outlines how data, including PHI, can be accessed, shared, and utilized. The focus here is on setting clear boundaries for what is allowed and ensuring the data is used only for specified purposes.
In short, while both agreements involve PHI, a BAA prioritizes compliance and security measures, whereas a DUA centers on the appropriate use and sharing of data.
Related Blog Posts
Key Points:
What is a Business Associate Agreement (BAA)?
- Definition: A Business Associate Agreement (BAA) is a legally binding contract required under HIPAA that governs the sharing of Protected Health Information (PHI) between covered entities (e.g., healthcare providers) and business associates (e.g., vendors or subcontractors).
- Purpose: It ensures that business associates adhere to the same HIPAA privacy and security safeguards as the
covered entity.
When is a BAA required?
- Requirement: A BAA is required whenever a covered entity shares PHI with a business associate or subcontractor for purposes other than treatment, payment, or healthcare operations.
- Examples: This includes vendors providing billing, IT services, cloud storage, or data analytics that involve PHI.
What are the key elements of a BAA?
- Permitted Uses of PHI: Specifies how the business associate can use or disclose PHI.
- Safeguards: Requires the business associate to implement appropriate safeguards to protect PHI.
- Breach Notification: Mandates that the business associate notify the covered entity of any breaches involving PHI.
- Compliance: Ensures adherence to HIPAA privacy and security rules.
What are the risks of not having a BAA?
- Regulatory Penalties: Non-compliance with HIPAA can result in significant fines and legal action.
- Data Breaches: Without a BAA, there is a higher risk of mishandling PHI, leading to breaches.
- Reputational Damage: Breaches or non-compliance can erode patient trust and damage an organization’s reputation.
How can healthcare organizations ensure BAA compliance?
- Maintain a Repository: Keep an organized repository of signed BAAs for easy reference and audits.
- Periodic Reviews: Conduct regular reviews and risk assessments to verify that business associates comply with HIPAA requirements.
- Vendor Screening: Evaluate vendors’ security practices and compliance certifications before sharing PHI.
What role do subcontractors play in BAAs?
- Subcontractor Agreements: Subcontractors who access PHI must also sign BAAs with the business associate to ensure compliance.
- Accountability: This ensures that all parties handling PHI are contractually bound to HIPAA standards.


