Benefits of Regular Risk Reviews in Healthcare
Post Summary
Because threats, systems, and regulations change constantly—making periodic, structured reviews necessary to maintain security and compliance.
Organizations stay exposed to new vulnerabilities in telehealth, cloud EHRs, medical devices, and vendor ecosystems.
Updates to HIPAA, ISO 27001, and state privacy laws require refreshed controls, documentation, and risk assessments.
Spreadsheets create inconsistencies, delays, ownership gaps, and incomplete asset inventories.
Stronger PHI protection, improved compliance, better visibility into risks, faster decision‑making, and lower breach costs.
Set clear scope and triggers, use standardized metrics, adopt risk platforms like Censinet, and schedule recurring audits.
Healthcare organizations face constant risks, from data breaches to evolving regulations. Regular risk reviews are the key to staying secure and compliant. These reviews ensure updated defenses, protect sensitive patient data, and help meet requirements like HIPAA and ISO 27001. Here's why they matter:
Switching to structured, frequent reviews - supported by specialized platforms - keeps healthcare systems resilient, compliant, and better equipped to handle emerging threats.
The Risks of Outdated Risk Treatment Plans
Relying on outdated risk treatment plans can leave healthcare organizations vulnerable, especially as telehealth, cloud-based EHRs, and connected medical devices continue to expand the attack surface faster than static documentation can keep up.
Changing Threats in Healthcare Technology
Since the COVID-19 pandemic, the healthcare industry has seen a rapid rise in telehealth, cloud-based EHR systems, and connected medical devices, significantly broadening its attack surface. Clinical networks now include home networks, personal devices, video conferencing platforms, and IoT equipment like infusion pumps and imaging scanners. Many of these devices run on outdated operating systems with weak security measures.[2][5] This makes healthcare a prime target for ransomware attacks. Common vulnerabilities include insecure remote access, unpatched systems, misconfigurations, and weak vendor controls.[5] Outdated risk treatment plans often fail to account for these emerging threats, leaving critical gaps in security.
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare."
Matt Christensen, Sr. Director GRC at Intermountain Health[1]
The ever-evolving threat landscape highlights the importance of regularly updating risk treatment plans to address new vulnerabilities and maintain robust defenses.
Regulatory Changes and Third-Party Risks
Regulations in the healthcare sector are constantly evolving. The Office for Civil Rights (OCR) has increased its focus on third-party business associate agreements, encryption standards, and audit logging requirements.[3][4] Additionally, the ISO/IEC 27001:2022 update introduced new Annex A controls that emphasize cloud services, threat intelligence, and ICT readiness for business continuity. Organizations that fail to adapt risk plans to these changes risk weakening their certification posture and face higher penalties in the event of a breach.[2][7] On top of this, state-level privacy laws now mandate stricter breach notification timelines and data minimization standards, further complicating compliance requirements.[3][6] Keeping risk treatment plans current is essential to navigating these regulatory shifts and avoiding costly consequences.
Problems with Manual Risk Management
Managing risks manually - often through spreadsheets - introduces a host of challenges, such as fragmented data, inconsistent scoring, and missed review cycles. These disconnected files obscure critical risk information, make it unclear who owns specific assets, and slow down incident response.
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with."
James Case, VP & CISO at Baptist Health[1]
Manual processes make it nearly impossible to maintain an up-to-date asset inventory that ties each system - including cloud services and connected devices - to documented risks, controls, and responsible owners.[2] Regularly reviewing and modernizing these processes can significantly improve risk management and strengthen overall security efforts.
Benefits of Regular Risk Reviews
In the fast-evolving landscape of healthcare, risks are constantly shifting, making regular risk reviews an essential part of staying ahead. These reviews help safeguard patient data, enhance compliance, and provide a clearer understanding of risks, all while empowering leadership to make informed decisions.
Better Protection for PHI and Clinical Systems
Frequent risk reviews help healthcare organizations quickly identify and address control gaps. By regularly assessing high-risk assets, they can uncover vulnerabilities that might go unnoticed during one-time evaluations - like misconfigured remote access, unpatched devices, or weak vendor controls [2][7]. Leveraging specialized risk management platforms further streamlines this process, allowing for more frequent assessments without straining resources.
"
allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."
Terry Grogan, CISO at Tower Health [1]
This enhanced efficiency ensures critical systems are reviewed more often, significantly reducing the time sensitive data and clinical operations are left exposed.
Stronger Compliance with ISO 27001 and HIPAA
ISO 27001 mandates ongoing risk monitoring and periodic reassessments, making regular reviews essential for maintaining compliance [7]. These reviews ensure risk treatment plans align with updated controls and regulatory changes, keeping practices in step with ISO standards. Additionally, a consistent review process demonstrates a "good faith effort" toward HIPAA Security Rule compliance, which can help mitigate penalties during breach investigations [4].
By maintaining structured review cycles, organizations also reduce audit findings, as current and accessible evidence simplifies the audit process. This proactive approach not only meets regulatory requirements but also fosters a deeper understanding of risks across all operations.
Clearer View of Cyber and Operational Risks
Beyond compliance, regular reviews provide a sharper lens into ongoing cyber and operational risks. Each review cycle answers critical questions: What is the current risk rating? Have new threats emerged? Are any controls failing? This structured approach offers leadership a detailed view of risks and the performance of controls organization-wide [2][7].
Collaborative risk networks further enhance this process by enabling the secure exchange of threat intelligence and control benchmarks.
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."
Brian Sterud, CIO at Faith Regional Health [1]
By tying every critical asset to measurable controls, organizations gain a more precise understanding of their risk landscape.
Better Leadership Decision-Making
For leadership, actionable insights are key. Regular risk reviews translate technical vulnerabilities into business-focused terms, such as patient safety concerns, care continuity risks, regulatory exposure, and financial impact. When conducted on a consistent schedule, these reviews provide trend-based reporting, helping leaders track changes over time - whether risks are rising, controls are improving, or new investments are needed.
Given that healthcare remains the most expensive industry for data breaches, with an average cost of $10.93 million per breach in 2023 [4], this kind of clear, trend-driven reporting supports proactive security measures while justifying critical investments in risk management.
sbb-itb-535baee
How to Implement Regular Risk Reviews
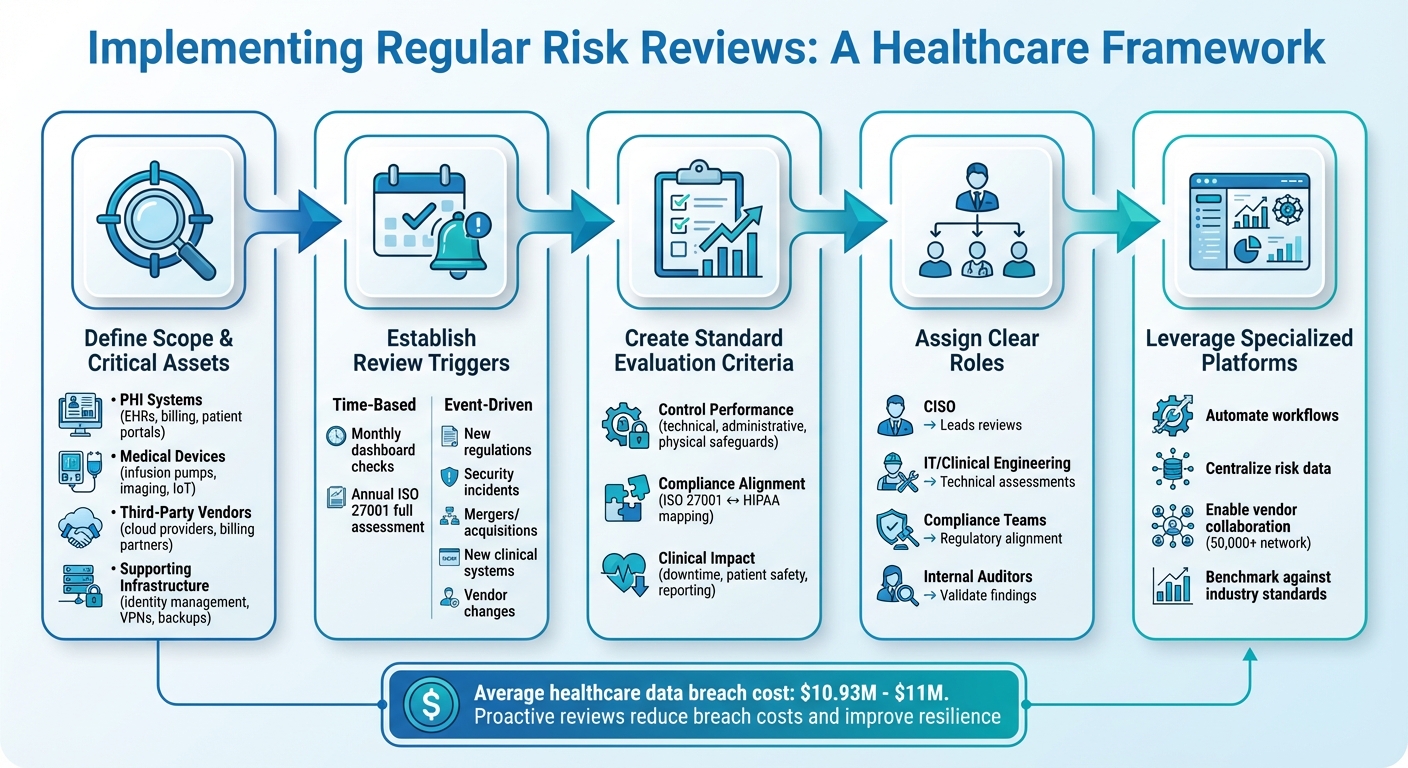
How to Implement Regular Risk Reviews in Healthcare: A Step-by-Step Framework
Regular risk reviews are key to staying ahead of evolving threats and maintaining ISO 27001 compliance. To make this process effective, it's important to establish a structured approach. This includes defining the review's scope, setting a clear schedule, and identifying metrics that ensure the process is both comprehensive and efficient.
Setting Scope and Review Triggers
Start by pinpointing the critical areas where Protected Health Information (PHI) and clinical operations are most vulnerable. These areas typically include:
Focus on assets with the highest risk first.
Next, establish both time-based and event-driven triggers to keep reviews timely and relevant. For time-based reviews, conduct monthly dashboard checks to monitor key indicators like patching status and unresolved vulnerabilities. Also, carry out a full ISO 27001 risk assessment at least once a year [2]. Event-driven triggers should prompt immediate reviews when major changes occur, such as:
Creating Standard Evaluation Criteria
To ensure consistency across reviews, develop standardized metrics. Key areas to monitor include:
Assign specific roles to team members for clarity and accountability. For example:
Formal documentation of these responsibilities helps prevent gaps, especially during staff transitions.
Using dedicated platforms can make these evaluations even more efficient and consistent.
Using Healthcare Risk Management Platforms
Specialized platforms designed for healthcare risk management can simplify the entire review process. For instance, Censinet RiskOps™ automates workflows, centralizes risk data, and supports collaboration with a network of over 50,000 vendors and products. Its cybersecurity benchmarking tools allow organizations to measure program maturity against industry standards, providing the consistency needed for ISO 27001 compliance.
Switching from manual spreadsheets to an automated platform offers significant efficiency improvements. With automation, organizations can conduct reviews more frequently without overburdening their security teams, ensuring that assessments stay on track and up to date.
Conclusion
Regular risk reviews play a crucial role in healthcare by safeguarding patient data, ensuring uninterrupted clinical operations, and meeting ever-changing regulatory demands. The ISO 27001 framework, with its Plan–Do–Check–Act cycle, mandates periodic risk assessments, helping healthcare organizations spot and address vulnerabilities before they become major issues [7]. With the average cost of a data breach reaching $11 million, proactive risk management not only prevents financial losses but also builds resilience [5].
The operational advantages are just as compelling. Automated tools for risk management have significantly reduced manual workloads, allowing teams to focus their efforts elsewhere. More importantly, these reviews equip leadership with actionable insights, enabling smarter strategic decisions. Consistent benchmarking further refines resource allocation, helping organizations prioritize investments to enhance their cyber defenses and overall resilience.
These benefits highlight how essential continuous, adaptive risk reviews are in the modern healthcare environment.
Key Takeaways
Recurring risk reviews aligned with ISO 27001 deliver tangible improvements in security, compliance, and operational efficiency. Healthcare organizations with advanced security programs that include ongoing monitoring consistently report lower breach-related costs compared to those that rely on outdated, static assessments [5]. The shift from annual assessments to dynamic, event-driven reviews - supported by specialized healthcare risk management tools - ensures that risk strategies stay in step with the fast-changing digital healthcare landscape. Ultimately, this approach prioritizes what matters most: protecting patient safety and securing sensitive data.
FAQs
Why are regular risk reviews important for healthcare compliance?
Regular risk reviews play a key role in ensuring healthcare compliance. They help organizations stay prepared for new threats and shifting regulations. By regularly evaluating and updating risk management strategies, healthcare providers can align with standards like ISO 27001 while protecting sensitive patient information and essential systems.
These reviews encourage a forward-thinking approach to managing risks. This not only lowers the chances of penalties, data breaches, or operational hiccups but also helps healthcare organizations strengthen their cybersecurity defenses. Regular assessments allow providers to address emerging challenges effectively and maintain confidence among patients and stakeholders.
How does the rise of telehealth influence risk management in healthcare?
The rise of telehealth is transforming how healthcare organizations approach risk management, bringing fresh challenges to the table. Protecting patient data and ensuring secure remote access have become top priorities as telehealth continues to grow, particularly after its rapid expansion during the COVID-19 pandemic. This shift has also introduced heightened cybersecurity risks, including potential weaknesses in device security and the transmission of sensitive data.
To keep up with these evolving threats, conducting regular risk assessments is crucial. These reviews help organizations stay aligned with standards like ISO 27001 while addressing potential vulnerabilities. By adopting advanced risk management tools, healthcare providers can take a proactive stance - identifying risks early, protecting patient safety, and preserving the security of critical information in an increasingly digital healthcare landscape.
What challenges do manual risk management processes pose in healthcare?
Manual risk management in healthcare is riddled with challenges. These processes often demand a lot of time and can be prone to mistakes, which increases the risk of errors that may jeopardize patient safety. Handling large amounts of data becomes a daunting task, and without the ability to deliver real-time insights, it’s tough to react swiftly to new risks or maintain compliance with standards like ISO 27001.
On top of that, relying on manual methods can lead to inefficiencies that delay critical decisions and slow down resource allocation - something no healthcare system can afford in its fast-moving environment. To address these issues, modern tools and technologies are necessary to streamline operations and manage risks more effectively.
Related Blog Posts
- How to Conduct Effective Third-Party Risk Assessments
- ISO 27001 Risk Assessment: Ultimate Guide for Healthcare
- Incident-Driven Risk Assessments for HIPAA Compliance
- ISO 27001 for Healthcare: Risk Management Explained
{"@context":"https://schema.org","@type":"FAQPage","mainEntity":[{"@type":"Question","name":"Why are regular risk reviews important for healthcare compliance?","acceptedAnswer":{"@type":"Answer","text":"<p>Regular risk reviews play a key role in ensuring healthcare compliance. They help organizations stay prepared for new threats and shifting regulations. By regularly evaluating and updating risk management strategies, healthcare providers can align with standards like ISO 27001 while protecting sensitive patient information and essential systems.</p> <p>These reviews encourage a forward-thinking approach to managing risks. This not only lowers the chances of penalties, data breaches, or operational hiccups but also helps healthcare organizations strengthen their cybersecurity defenses. Regular assessments allow providers to address emerging challenges effectively and maintain confidence among patients and stakeholders.</p>"}},{"@type":"Question","name":"How does the rise of telehealth influence risk management in healthcare?","acceptedAnswer":{"@type":"Answer","text":"<p>The rise of telehealth is transforming how healthcare organizations approach risk management, bringing fresh challenges to the table. Protecting patient data and ensuring secure remote access have become top priorities as telehealth continues to grow, particularly after its rapid expansion during the COVID-19 pandemic. This shift has also introduced heightened <a href=\"https://www.censinet.com/blog/5-ways-to-reduce-3rd-party-cybersecurity-risks-per-18-experts\">cybersecurity risks</a>, including potential weaknesses in device security and the transmission of sensitive data.</p> <p>To keep up with these evolving threats, conducting regular risk assessments is crucial. These reviews help organizations stay aligned with standards like ISO 27001 while addressing potential vulnerabilities. By adopting advanced risk management tools, healthcare providers can take a proactive stance - identifying risks early, protecting patient safety, and preserving the security of critical information in an increasingly digital healthcare landscape.</p>"}},{"@type":"Question","name":"What challenges do manual risk management processes pose in healthcare?","acceptedAnswer":{"@type":"Answer","text":"<p>Manual risk management in healthcare is riddled with challenges. These processes often demand a lot of time and can be prone to mistakes, which increases the risk of errors that may jeopardize patient safety. Handling large amounts of data becomes a daunting task, and without the ability to deliver <strong>real-time insights</strong>, it’s tough to react swiftly to new risks or maintain compliance with standards like ISO 27001.</p> <p>On top of that, relying on manual methods can lead to inefficiencies that delay critical decisions and slow down resource allocation - something no healthcare system can afford in its fast-moving environment. To address these issues, modern tools and technologies are necessary to streamline operations and manage risks more effectively.</p>"}}]}
Key Points:
Why are regular risk reviews so important for healthcare organizations?
- Threats evolve quickly due to telehealth expansion, cloud adoption, and IoT device growth
- Static documentation cannot keep pace, creating security gaps
- Regulators expect continuous monitoring, not one‑time assessments
- Patient safety depends on secure clinical operations and uninterrupted workflows
- Data breaches are costly, averaging over $10M per incident
What risks arise when organizations rely on outdated risk treatment plans?
- Unpatched systems and weak remote access expose PHI through telehealth and cloud EHR platforms
- Connected medical devices running legacy OS introduce attack vectors
- Vendor misconfigurations go unnoticed, creating cascading vulnerabilities
- Threat actors exploit outdated documentation, leading to ransomware and operational shutdowns
- Clinical disruptions occur, affecting patient care delivery
How do regulatory changes increase the need for ongoing reviews?
- ISO/IEC 27001:2022 introduces new Annex A controls around cloud and business continuity
- OCR focuses on encryption, logging, and BAAs, requiring updated safeguards
- State privacy laws tighten breach notifications and data minimization
- HIPAA investigations demand current evidence, not outdated policies
- Falling behind regulatory changes risks penalties and weakened certification posture
Why are manual risk management workflows problematic?
- Spreadsheet-based tracking creates fragmented data with no single source of truth
- Inconsistent scoring and missed review cycles undermine governance
- No clear asset ownership, causing accountability gaps
- Slow incident response due to scattered documentation
- Inefficiency strains teams, especially with hundreds of systems and vendors
What benefits do regular risk reviews provide for healthcare organizations?
- Improved PHI and clinical system protection through timely control updates
- Better ISO 27001 and HIPAA compliance, reducing audit findings
- Clear visibility into cyber and operational risks, enabling stronger leadership decisions
- Trend-based reporting that ties vulnerabilities to business impact
- Reduced exposure windows, lowering breach likelihood and cost
How can organizations implement effective, ongoing risk review processes?
- Define scope and triggers, using both time-based and event‑based reviews
- Set standardized evaluation criteria covering threats, controls, and incident patterns
- Assign clear roles across security, compliance, and leadership teams
- Adopt risk management platforms like Censinet RiskOps™ for automation and benchmarking
- Integrate monitoring into daily workflows, ensuring continuous improvement


