Top 7 Cloud Providers for HIPAA Compliance
Post Summary
Handling sensitive healthcare data in the cloud requires strict adherence to HIPAA regulations. This means signing a Business Associate Agreement (BAA), using HIPAA-eligible services, and ensuring proper security configurations. The top cloud providers for HIPAA compliance offer tools, encryption, and services tailored for healthcare needs. Here's a quick look at the leading options:
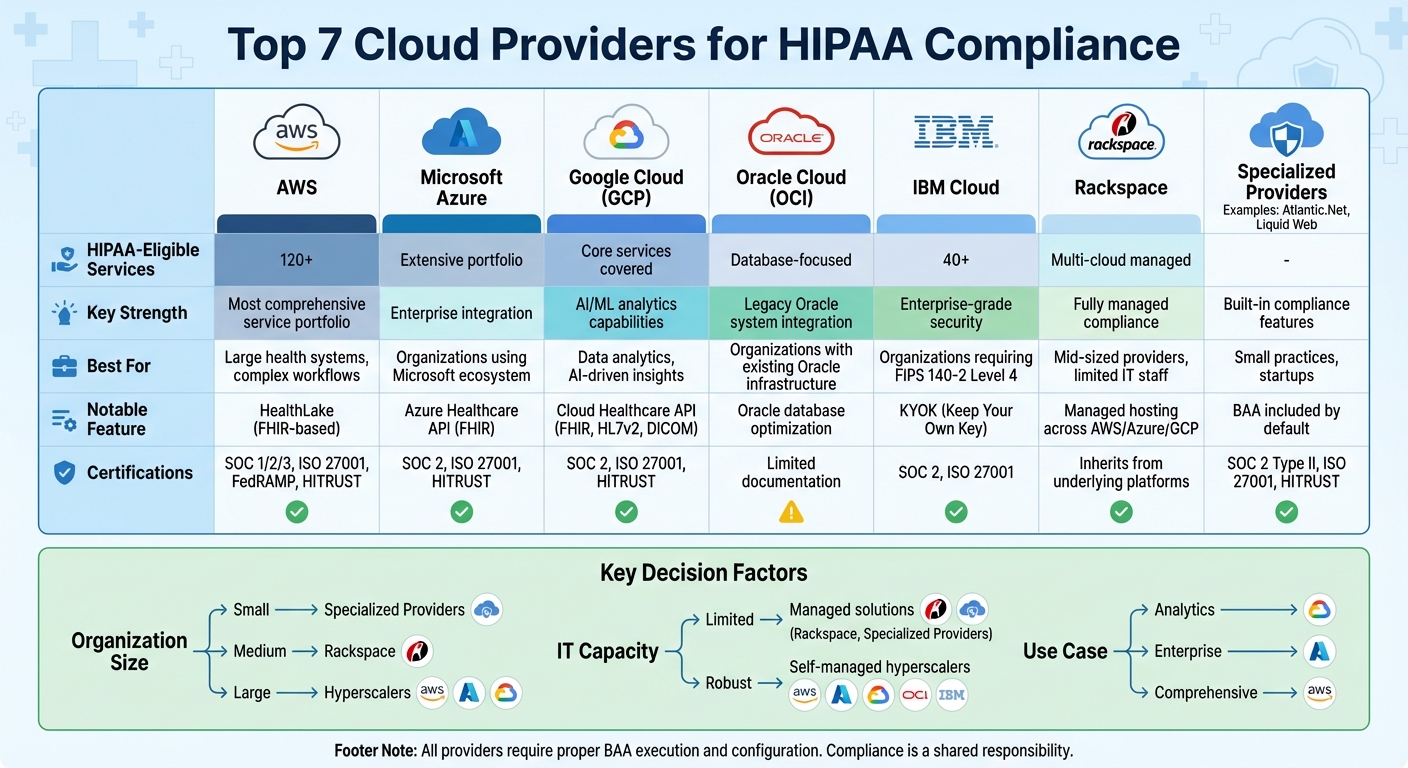
- AWS: Over 120 HIPAA-eligible services, strong encryption, and healthcare-specific tools like HealthLake.
- Microsoft Azure: Advanced security, FHIR-based API, and tools for clinical data management.
- Google Cloud Platform (GCP): AI-driven analytics, Cloud Healthcare API, and robust encryption.
- Oracle Cloud: Well-suited for organizations using legacy Oracle systems, though documentation can be unclear.
- IBM Cloud: Focus on security with FIPS-certified encryption and healthcare-specific services.
- Rackspace Technology: Managed hosting across multiple cloud platforms, reducing operational burdens.
- Specialized HIPAA Hosting Providers: Tailored solutions with built-in compliance and security features.
Key Takeaway: Choosing the right provider depends on your organization's size, IT capacity, and specific healthcare needs. Whether you opt for hyperscalers like AWS or specialized hosting providers, compliance is a shared responsibility requiring ongoing risk management and monitoring.
Top 7 HIPAA-Compliant Cloud Providers Comparison Chart
1. Amazon Web Services (AWS)
Amazon Web Services (AWS) provides a robust cloud platform tailored for healthcare organizations, offering over 120 HIPAA-eligible services as of 2025 [1]. Recognized by Gartner as a leader in healthcare cloud computing, AWS excels in areas like hybrid cloud solutions and IoMT (Internet of Medical Things) management. Its approach to HIPAA Business Associate Addendums (BAAs) highlights its strong focus on securing protected health information (PHI).
Availability of a HIPAA BAA
To handle PHI on AWS, covered entities and business associates must sign a Business Associate Addendum (BAA). This agreement, which is integrated into the AWS console as part of the standard customer agreement, ensures compliance with HIPAA regulations. However, it’s important to note that the BAA only applies to designated HIPAA-eligible services. Using non-eligible services for PHI would violate HIPAA requirements.
Encryption and Security Features
AWS offers a range of security features to protect HIPAA workloads. PHI data is secured with encryption at rest using AWS Key Management Service (KMS) for services like S3, EBS, and RDS, along with TLS 1.2+ encryption for data in transit. Identity and Access Management (IAM) enables healthcare organizations to implement least-privilege access policies, ensuring users have only the permissions they need. AWS also provides tools like CloudTrail and CloudWatch to log and monitor API and console activity. To strengthen security, organizations can enforce multi-factor authentication (MFA), isolate PHI within dedicated Virtual Private Clouds (VPCs), and use AWS Config and Security Hub for continuous compliance checks.
Healthcare-Specific Services and Reference Architectures
AWS’s healthcare offerings include Amazon HealthLake, a service built on the FHIR (Fast Healthcare Interoperability Resources) standard. HealthLake allows providers to store, normalize, and query clinical data, including electronic health records (EHR) and claims data. Once harmonized to FHIR standards, this data can be analyzed using tools like Amazon Redshift, Athena, or SageMaker - all within the HIPAA-eligible scope. AWS also provides detailed reference architectures that include multi-zone VPCs, private subnets, edge protection with services like AWS WAF and Shield, and encrypted storage solutions.
Support for Compliance Certifications
AWS holds a variety of certifications that support HIPAA compliance, including SOC 1, SOC 2, SOC 3, ISO 27001, ISO 27017, ISO 27018, and FedRAMP. Additionally, AWS maps its eligible services to the HITRUST Common Security Framework (CSF). For healthcare organizations managing complex PHI workflows and multiple vendors, AWS integrates seamlessly with tools like Censinet RiskOps, enabling continuous risk assessments and swift remediation of HIPAA-related issues.
2. Microsoft Azure
Microsoft Azure aligns with U.S. healthcare HIPAA standards through a solid Business Associate Agreement (BAA), robust encryption methods, and services tailored for clinical data management. Its HIPAA BAA covers a specific list of HIPAA-eligible services, laying the contractual groundwork for handling protected health information (PHI).
Availability of a HIPAA BAA
Healthcare organizations looking to use Azure for PHI must sign a Business Associate Addendum as part of their enterprise or qualifying agreements with Microsoft. However, it’s important to note that this BAA only applies to designated HIPAA-eligible services. Using any non-eligible services for PHI would breach HIPAA regulations. Under this agreement, health systems commonly rely on Azure for tasks like extending electronic health records (EHRs), managing patient portals, and storing imaging archives. The platform operates on a shared responsibility model: Microsoft secures the physical infrastructure and core platform, while customers handle identity management, access controls, and data protection configurations.
Encryption and Security Features
Azure employs advanced security measures to protect PHI. Data at rest is secured through Azure Storage Service Encryption and Azure Disk Encryption, both utilizing AES-256 encryption. For data in transit, Azure uses TLS to ensure secure transfers between clients, services, and regions. Azure AD (now Entra ID) enhances security with role-based access control (RBAC), conditional access policies, and multi-factor authentication. Additional tools like Azure Monitor, Log Analytics, and Azure Policy offer centralized auditing and continuous security oversight. For instance, a healthcare provider with multiple locations might store imaging data in Azure Blob Storage, restrict access through RBAC and private endpoints, encrypt all data at rest, and feed access logs into a centralized security information and event management (SIEM) system for real-time monitoring. These features make Azure a strong choice for healthcare-specific applications.
Healthcare-Specific Services and Reference Architectures
Azure’s Healthcare API, also known as Azure API for FHIR, is a managed service designed for FHIR-based data exchange and storage. This service allows organizations to build interoperable clinical applications while adhering to HIPAA requirements. Health systems use the API to aggregate EHR data from multiple sources into a unified FHIR repository. This repository can power patient-facing apps, care coordination tools, and analytics - all within the scope of the HIPAA BAA. Additionally, Azure supports healthcare analytics through data lakes and machine learning services built for HIPAA compliance. Its reference architectures provide detailed guidance on essential topics like network segmentation, key management, and logging practices that align with regulatory standards.
Support for Compliance Certifications
Azure holds key certifications such as SOC 2, ISO 27001, and HITRUST-aligned offerings, which demonstrate that its security and privacy controls have been independently evaluated against recognized standards. While these certifications don’t automatically make a workload HIPAA-compliant, they offer valuable evidence for risk assessments and vendor due diligence. Many U.S. healthcare providers reference these certifications in their third-party risk management processes to support their overall HIPAA compliance strategies. Some organizations also enhance Azure’s native controls by using platforms like Censinet RiskOps™. These tools help streamline vendor risk assessments, evaluate cybersecurity readiness, and manage risks across PHI systems, clinical applications, and medical device integrations. Next, we’ll explore other cloud providers that are advancing HIPAA compliance with specialized certifications and risk management tools.
3. Google Cloud Platform (GCP)
Google Cloud Platform (GCP) holds the third spot in Gartner's Magic Quadrant and combines advanced analytics and AI with services that meet HIPAA requirements [1]. Healthcare organizations that sign a HIPAA Business Associate Addendum (BAA) with Google gain access to specific HIPAA-eligible services. These include Cloud Storage, Cloud SQL, BigQuery, and the Cloud Healthcare API, all of which are designed to securely store and process protected health information (PHI) [1].
Availability of a HIPAA BAA
For U.S. healthcare providers, signing a Business Associate Addendum is essential before handling PHI on GCP. This agreement, arranged through Google Cloud sales or account teams, is part of an enterprise agreement and applies only to designated HIPAA-eligible services [1]. To ensure compliance, organizations must identify which workloads and datasets involve PHI and confirm that these remain within the approved services list [1]. Under Google's shared responsibility model, Google secures the infrastructure, while customers are responsible for configuring services, managing access, and adhering to internal policies [1]. With a BAA in place, GCP strengthens PHI protection through advanced encryption and access controls.
Encryption and Security Features
GCP automatically encrypts data at rest across services like Cloud Storage, Compute Engine persistent disks, and BigQuery. Customers can also manage their encryption keys using Cloud KMS. Data in transit is secured with TLS, and organizations are encouraged to enforce HTTPS-only access for APIs and web endpoints [1][5]. Role-based Identity and Access Management (IAM) ensures administrators have precise, least-privilege access. Additionally, Cloud Audit Logs track administrative actions, data access, and system events to maintain the audit trails required by HIPAA [5]. Many healthcare organizations export these logs to BigQuery or Cloud Storage and integrate them with alerting tools like Cloud Monitoring or third-party SIEM platforms for real-time monitoring [5].
Healthcare-Specific Services and Reference Architectures
The Cloud Healthcare API provides managed data stores for FHIR, HL7v2, and DICOM, enabling healthcare organizations to handle EHR, imaging, and device data in standardized formats [2][3]. This API allows health systems to consolidate data from various sources into a unified FHIR repository, which can be used for patient-facing applications, care coordination tools, and analytics pipelines - all while staying within the HIPAA BAA's scope [2][3]. Common applications include patient risk modeling, claims analysis, and radiology workflows powered by imaging AI [2][3]. Google and its partners also provide reference architectures that demonstrate end-to-end workflows, such as ingesting data through the Cloud Healthcare API, storing it in HIPAA-compliant data lakes or warehouses, and securely exposing FHIR-based APIs to clinical apps under strict IAM controls [2][3].
Support for Compliance Certifications
GCP holds several third-party compliance certifications, including SOC 2 and ISO 27001, which validate its security and availability measures [1][6]. Many healthcare organizations prioritize HITRUST CSF alignment, and GCP’s HITRUST certifications confirm its adherence to regulatory standards [2][6]. During vendor evaluations, healthcare teams often request GCP's latest SOC reports and ISO certifications under NDA. These documents are mapped to internal control frameworks and used as evidence for risk management and board reporting [1][6]. Some organizations further enhance their compliance efforts by leveraging platforms like Censinet RiskOps™ to monitor residual risks, track remediations, and compare their GCP deployments with industry benchmarks in U.S. healthcare [1][6]. These certifications underscore GCP's dedication to maintaining HIPAA compliance over time.
4. Oracle Cloud Infrastructure (OCI)
Oracle Cloud Infrastructure (OCI) is designed to work seamlessly with Oracle databases and enterprise applications, making it an attractive option for healthcare organizations already using legacy Oracle systems. Analysts often point out OCI's specialized role, which could be advantageous for those looking to migrate older clinical or billing systems. However, there’s a notable gap in OCI's documentation when it comes to HIPAA compliance. Key details, such as specifics about its Business Associate Agreement (BAA), encryption protocols, and healthcare-focused reference architectures, are not clearly outlined. This means healthcare organizations need to carefully examine Oracle’s official documentation to confirm whether their workloads meet HIPAA requirements. This lack of clarity highlights the critical need for thorough vendor risk management as part of any cloud compliance plan. Before moving sensitive data to OCI, it’s essential to ensure all HIPAA compliance measures are fully understood and verified.
To strengthen HIPAA risk management, organizations can also integrate their OCI setup with third-party tools like Censinet RiskOps™ for added security and compliance support.
5. IBM Cloud
IBM Cloud provides over 40 HIPAA-eligible services and offers a formal Business Associate Agreement (BAA) for U.S. healthcare organizations handling protected health information (PHI) [1]. This agreement ensures IBM secures its infrastructure and logging, while customers are responsible for managing access controls and application configurations. Before migrating PHI to IBM Cloud, it's essential to confirm that each planned service is HIPAA-eligible and that the BAA is properly executed.
Encryption and Security Features
IBM Cloud uses FIPS 140-2 Level 4 certified hardware security modules (HSMs) to support its 'keep your own key' (KYOK) model, giving healthcare customers full control over their cryptographic keys. It also offers encryption at rest for storage solutions like Cloud Block Storage and Cloud File Storage, along with TLS-based encryption in transit to secure network traffic. Identity and Access Management (IAM) enforces least privilege access and unique user identification, while centralized logging facilitates audits and incident investigations.
Healthcare-Specific Services and Reference Architectures
IBM Cloud's HIPAA-eligible services include Cloud Databases, Cloud App ID, Cloud Block Storage, Cloud File Storage, and IBM Cloud for VMware Solutions, which can support electronic health record (EHR) systems, imaging archives, or clinical applications. Additionally, IBM offers healthcare-focused solutions like IBM Cloud for Healthcare and IBM Health, designed to align with HIPAA requirements for clinical systems, data analytics, and interoperability. IBM Cloud's emphasis on security has also earned recognition in Gartner's Magic Quadrant.
Support for Compliance Certifications
IBM Cloud goes beyond HIPAA with a wide range of compliance standards. It holds certifications like SOC 2 and ISO 27001, which cover its core services. U.S. healthcare compliance teams can request IBM's latest SOC and ISO reports under a non-disclosure agreement (NDA) to map these controls to HIPAA's administrative, physical, and technical safeguards. While HIPAA itself isn't a certifiable standard, these audits demonstrate that IBM's security measures - such as access management, change management, and incident response - are effectively implemented and maintained.
For enhanced cybersecurity and vendor risk assessments, IBM Cloud can be integrated with Censinet RiskOps™ to streamline compliance efforts and benchmarking.
sbb-itb-535baee
6. Rackspace Technology

Rackspace provides HIPAA-compliant managed hosting services across its own infrastructure and major public cloud platforms, including AWS, Microsoft Azure, and Google Cloud. This approach offers a managed alternative to self-configured solutions provided by hyperscale cloud providers. Instead of requiring healthcare organizations to handle compliance configurations and ongoing maintenance themselves, Rackspace takes on much of the operational and security workload. This model is particularly helpful for mid-sized U.S. healthcare providers and health-tech companies that may lack extensive in-house cloud expertise.
Availability of a HIPAA BAA
Rackspace signs a HIPAA Business Associate Agreement (BAA) that outlines the shared responsibilities for protecting PHI, managing breach notifications, and configuring security controls. This agreement also specifies HIPAA-eligible services and audit requirements, clearly defining the roles of Rackspace, the customer, and the underlying cloud provider (AWS, Azure, or Google Cloud) [2][4].
Encryption and Security Features
Rackspace prioritizes robust security measures, including encryption both in transit (using TLS) and at rest (via disk and database encryption). It configures firewalls, VPNs, intrusion detection systems, and secure backups. Advanced features include strong HTTPS cipher suites, automatic key rotation (leveraging AWS KMS or Azure Key Vault), and encrypted off-site backups with strict access controls [2][4].
Additionally, Rackspace supports role-based access controls and integrates with the identity and access management (IAM) tools of its cloud partners to ensure least-privilege access for systems that handle PHI. Managed environments typically centralize system, application, and security logs into SIEM tools, enabling long-term log retention and audit readiness to meet HIPAA compliance standards [2][4].
Healthcare-Specific Services and Reference Architectures
Rackspace provides tailored reference architectures for healthcare use cases such as EHR integrations, telehealth platforms, patient portals, and healthcare SaaS solutions. These designs incorporate native cloud services and can include multi-tier VPCs or VNets with encrypted storage, HIPAA-eligible databases, private EHR connectivity, web application firewalls, and DDoS protection. Managed backups and disaster recovery solutions ensure PHI remains encrypted and recoverable in case of an incident [2][4].
For healthcare organizations looking to streamline vendor risk management, tools like Censinet RiskOps™ can be used to assess Rackspace-hosted solutions. These platforms help maintain current risk profiles and document risk mitigation strategies for audits and regulatory reviews. Rackspace also integrates with third-party risk management tools to enable continuous compliance monitoring, adding another layer of assurance for healthcare providers.
7. Specialized HIPAA Hosting Providers
Specialized HIPAA hosting providers cater specifically to U.S. healthcare organizations by offering managed environments designed to handle electronic protected health information (ePHI). Companies like Atlantic.Net, Liquid Web, and newer players such as Vercel and Netlify provide hosting solutions that are HIPAA-compliant, with built-in security features, audit trails, and consulting services. These providers stand out by including managed security and compliance services - like firewalls, intrusion detection systems, log management, patching, backups, and disaster recovery - as part of their core offerings. Below, we’ll explore how these providers address BAAs, security measures, healthcare-focused services, and compliance certifications.
Availability of a HIPAA BAA
Most specialized HIPAA hosting providers simplify the onboarding process by including a Business Associate Agreement (BAA) as part of their standard contracts. For instance, Atlantic.Net automatically provides BAAs with its HIPAA-compliant hosting packages, saving healthcare organizations from lengthy negotiations. When reviewing a BAA, it’s crucial to confirm that it covers all essential services, such as dedicated servers, managed databases, backups, disaster recovery options, and any third-party tools managed by the provider. The agreement should also clearly define the shared responsibilities between the hosting provider and the customer.
Encryption and Security Features
Security is a cornerstone of these hosting solutions. Providers like Atlantic.Net offer encryption both in transit (using TLS) and at rest, along with other critical features such as Web Application Firewalls (WAF), multi-factor authentication (MFA), intrusion prevention systems (IPS), automated patching, antivirus protection, and centralized log management. These measures align with HIPAA’s technical safeguards and reduce the risks associated with self-managed environments. Many providers also implement role-based access control (RBAC), VPN access for administrative tasks, and detailed audit trails to support regulatory compliance and investigations.
Healthcare-Specific Services and Reference Architectures
While these providers may not match the extensive healthcare-specific APIs offered by major hyperscale cloud platforms, they often make up for it with specialized architectures and expert guidance tailored to healthcare needs. Examples include pre-configured setups for patient portals, telehealth platforms, EHR systems, and healthcare SaaS applications. These configurations often incorporate network segmentation, WAF rules, and logging practices designed for PHI-heavy workflows. Additionally, some providers enable secure data pipelines for analytics on de-identified or limited datasets by integrating third-party tools with strict encryption and access controls. These managed solutions simplify infrastructure setup and strengthen risk management strategies.
Support for Compliance Certifications
Top-tier specialized HIPAA hosting providers undergo independent third-party audits to validate their security measures. For example, Atlantic.Net, with over three decades of experience, adheres to CPA-audited practices that exceed regulatory requirements. When evaluating providers, healthcare organizations should prioritize certifications like SOC 2 Type II, ISO 27001 (including cloud and privacy extensions), and HITRUST CSF. Reviewing audit reports ensures that the certifications cover the services you intend to use.
Integrating with Third-Party Risk Management
To maintain compliance, healthcare organizations must incorporate these hosting providers into their third-party risk management programs. Tools like Censinet RiskOps™ help streamline standardized risk assessments and continuous compliance monitoring. As Matt Christensen, Sr. Director of GRC at Intermountain Health, explains:
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare" [8].
Third-Party Risk Management for HIPAA-Compliant Cloud Services
Getting a signed Business Associate Agreement (BAA) is just the beginning. HIPAA compliance is a shared responsibility, and maintaining it requires ongoing vigilance. Changes in configurations, updates, and the emergence of new threats demand continuous risk oversight to ensure your cloud environment stays aligned with HIPAA standards.
Start by creating a governance framework that spans multiple disciplines. This framework should define vendor selection policies, establish BAAs, and assign clear responsibility for workloads involving Protected Health Information (PHI). U.S. healthcare organizations should also conduct formal HIPAA Security Rule risk analyses. These analyses help inventory every cloud system that stores or processes PHI, classify the sensitivity of the data, and map how data flows between providers. This step is especially critical in multi-cloud environments, where PHI might move across platforms like AWS, Azure, or specialized HIPAA hosting providers. Such a framework complements earlier evaluations of HIPAA-eligible cloud providers and strengthens your overall approach to risk management.
Continuous monitoring is another key piece of the puzzle. To effectively manage vendor risk, focus on activities like reviewing logs for unusual access patterns, detecting configuration drifts that could expose vulnerabilities (e.g., storage buckets accidentally made public), and periodically revalidating that PHI workloads remain on HIPAA-eligible services covered by your BAA. Tools like cloud security posture management systems and Security Information and Event Management (SIEM) solutions can further enhance your efforts by correlating cloud activity with endpoint and network data. This enables you to spot potential security breaches or data exfiltration attempts before they escalate into reportable incidents.
Platforms such as Censinet RiskOps™ simplify this process by automating risk assessments and centralizing vendor management. Designed specifically for healthcare, the platform helps manage cyber risks from third-party vendors, including cloud and SaaS providers that handle PHI, clinical applications, medical devices, and supply chain partners. It streamlines standardized risk assessments, consolidates vendor questionnaires and evidence collection, tracks remediation efforts, and benchmarks your security posture against peer organizations. Terry Grogan, CISO at Tower Health, shared:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."
This example highlights how the right tools can save time, improve efficiency, and help healthcare organizations stay on top of cloud-related risks while focusing on vendors with the highest potential impact on patient data and operations.
To maintain HIPAA-compliant risk oversight, keep a comprehensive inventory of third parties and cloud services that handle PHI. Categorize vendors based on their criticality and level of PHI exposure. Before finalizing contracts, require standardized security questionnaires, BAAs, and evidence of controls, such as SOC 2 or HITRUST certifications. Integrating these steps into your procurement and IT change management processes ensures a consistent approach to managing risks while safeguarding patient data.
Conclusion
AWS, Azure, Google Cloud, Oracle, IBM Cloud, Rackspace, and specialized HIPAA hosting providers all offer HIPAA-eligible services and are willing to sign Business Associate Agreements (BAAs). However, simply using these platforms doesn’t automatically make your organization compliant [1]. While these providers secure their infrastructure, the responsibility for configuring security settings and adhering to best practices rests squarely on your shoulders. Misconfigurations, in fact, remain one of the leading causes of healthcare data breaches.
Given these responsibilities, choosing the right provider is critical. The decision should align with your organization’s size, specific needs, and IT capabilities. Larger health systems often opt for hyperscalers like AWS, Azure, or Google Cloud due to their scalability and advanced analytics - provided they can handle the complexities of governance. On the other hand, smaller practices or digital health startups might find managed or specialized HIPAA hosting more suitable, as these services take on much of the configuration, monitoring, and administrative work required to stay compliant.
That said, achieving HIPAA compliance in the cloud isn’t a one-and-done task; it’s an ongoing process. This includes continuously monitoring security events, conducting regular internal audits, documenting policies thoroughly, and managing third-party risks effectively. Using standardized assessments, keeping a close eye on vendor controls, and having clear remediation plans ensures that any vendor handling protected health information (PHI) meets HIPAA requirements and broader cybersecurity standards [7].
Think of your cloud provider as the foundation for compliance - but the real work lies in building a strong internal program. This means defining a governance framework, inventorying where PHI is stored, performing and documenting risk assessments, implementing technical safeguards, and maintaining regular vendor reviews. Tools like Censinet RiskOps™ can help streamline risk assessments, benchmark your cybersecurity posture, and manage risks tied to PHI, clinical applications, medical devices, and supply chains. These tools complement, rather than replace, the security features provided by your cloud platform. Early collaboration among compliance, legal, and security teams can turn provider selection into a clear, actionable roadmap for adopting the cloud. This approach reinforces the shared responsibility model at the heart of HIPAA compliance in the cloud.
FAQs
What should I look for in a HIPAA-compliant cloud provider?
When you're choosing a cloud provider that complies with HIPAA, it's important to prioritize their ability to meet stringent healthcare security standards. Look for essential features like encryption, access controls, and audit logging to ensure sensitive patient data stays protected.
Make sure the provider has relevant certifications, such as HIPAA or HITRUST, which demonstrate their adherence to these regulations. It's also crucial that they actively manage risks to safeguard protected health information (PHI).
Opt for a provider with proven experience in the healthcare field, strong data protection protocols, and thorough compliance support. This combination ensures they can securely handle PHI while meeting all regulatory guidelines.
What is a Business Associate Agreement (BAA) and how does it help with HIPAA compliance?
A Business Associate Agreement (BAA) is a mandatory contract under HIPAA that outlines how a healthcare organization and its business associate should manage Protected Health Information (PHI). Its primary purpose is to ensure both parties take necessary steps to safeguard sensitive patient information and adhere to HIPAA standards.
The agreement specifies how PHI can be used and disclosed, details the procedures for reporting breaches, and ensures both parties are accountable for maintaining data security. By clearly defining these responsibilities, a BAA helps protect patient privacy while ensuring compliance with federal regulations.
What security features do HIPAA-compliant cloud providers typically offer?
When it comes to protecting sensitive patient information, HIPAA-compliant cloud providers offer a range of powerful security measures. These typically include data encryption (both while stored and during transmission), multi-factor authentication to strengthen access security, strict access controls to limit who can view or modify data, and audit logging to track and monitor system activity. Additionally, these providers frequently perform vulnerability assessments to identify and address potential risks. They also hold key certifications, such as HIPAA, HITECH, and SOC 2, to demonstrate adherence to regulatory requirements.


