Blockchain Healthcare Vendors: Risk Management for Distributed Ledger Technologies
Post Summary
Blockchain is transforming healthcare by improving data security and operational efficiency, but it also introduces unique risks. These include vulnerabilities in smart contracts, challenges with key management, and compliance issues with regulations like HIPAA. With healthcare data breaches costing an average of $9.8 million, managing vendor risks is essential to protect patient data and avoid significant penalties.
Key points to understand:
- Cybersecurity risks: Smart contract flaws, API exposure, and data re-identification.
- Operational risks: Scalability issues, vendor reliability, and infrastructure dependencies.
- Compliance challenges: Blockchain's immutability complicates HIPAA and GDPR adherence.
Effective vendor evaluation focuses on security practices, compliance with regulations, and blockchain-specific features like permissioned networks. Tools like Censinet RiskOps™ simplify risk assessments and monitoring, helping organizations safeguard sensitive data while leveraging blockchain's benefits.
Key Risks Associated with Blockchain Vendors
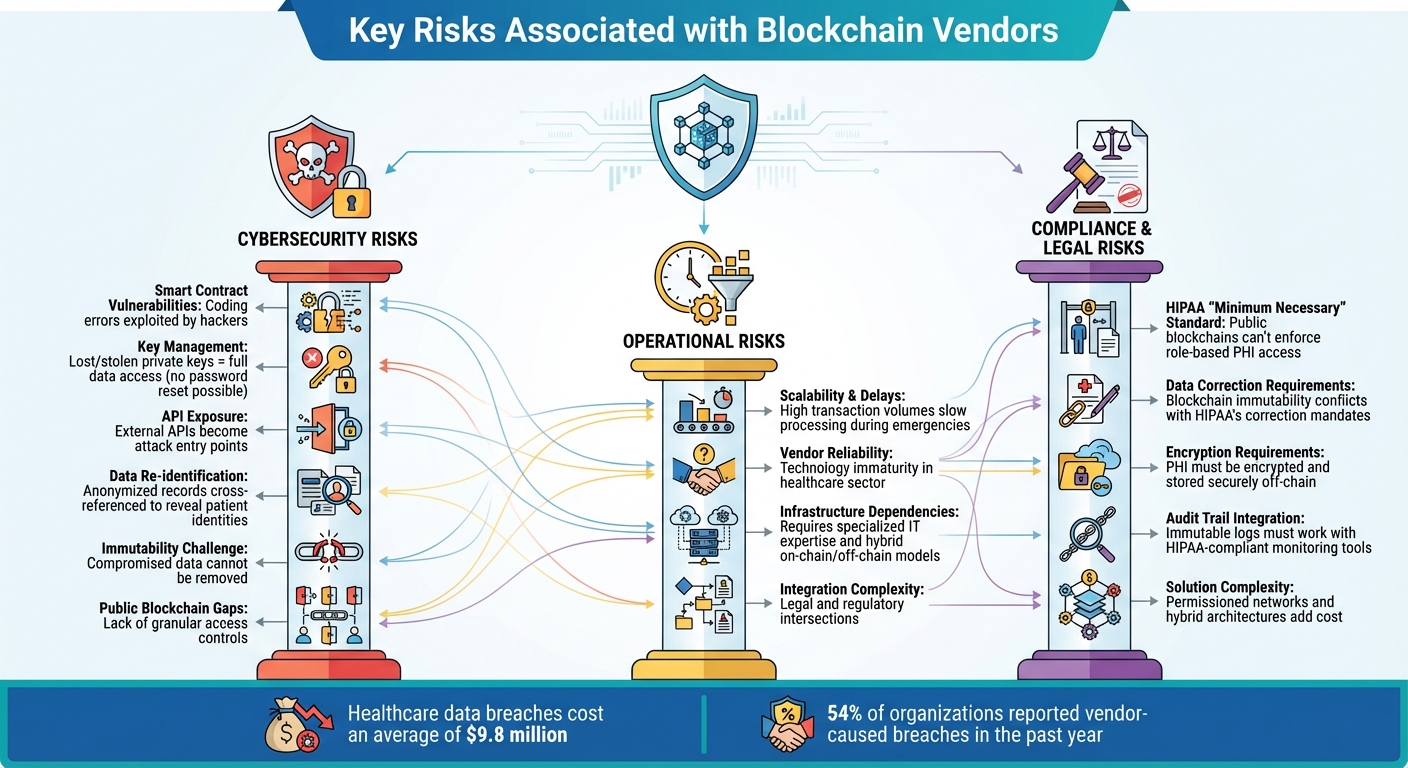
Three Primary Risk Categories for Blockchain Healthcare Vendors
Healthcare organizations exploring blockchain technology must navigate three primary risk areas before implementation. These risks, if not properly managed, can jeopardize patient safety, compromise data integrity, and lead to regulatory violations. Let’s break them down.
Cybersecurity Risks
One major concern lies in smart contract vulnerabilities. These self-executing contracts can harbor coding errors that hackers exploit to tamper with transactions or gain unauthorized access to sensitive data. Another pressing issue is key management - if private keys are lost or stolen, attackers can gain full access to blockchain-stored data and resources. Unlike traditional systems, blockchain doesn’t allow for password resets or key recovery, making this a critical weak spot.
API exposure also increases the attack surface. External APIs connected to the blockchain can become entry points for cyberattacks. Additionally, there’s the risk of data re-identification, where anonymized blockchain records can be cross-referenced with other datasets to uncover patient identities. While blockchain provides encryption and anonymity, public blockchains often lack granular access controls, leaving sensitive information potentially exposed. And because blockchain is immutable, removing compromised or breached data can be nearly impossible.
Operational Risks
Operational challenges like scalability and delays can disrupt access to vital patient information. High transaction volumes can slow down processing times, which is particularly concerning during emergencies when clinicians need real-time data. Compounding this issue is the relative immaturity of blockchain technology in healthcare, raising questions about vendor reliability.
Another challenge lies in infrastructure dependencies. Blockchain systems require specialized IT expertise and carefully designed architectures, such as hybrid on-chain/off-chain models. These operational hurdles often intersect with legal and regulatory complexities, creating additional layers of risk for healthcare organizations.
Compliance and Legal Risks
The decentralized and immutable nature of blockchain creates significant hurdles for complying with regulations like HIPAA and GDPR. For example, HIPAA’s "minimum necessary" standard requires strict, role-based access to Protected Health Information (PHI). Public blockchains, which are open to all participants, struggle to enforce such restrictions. Similarly, HIPAA mandates that PHI errors must be correctable, but blockchain’s immutability makes data deletion or modification nearly impossible.
HIPAA also requires that PHI be encrypted and stored securely off-chain. Sensitive information must be encrypted before being added to the blockchain, and immutable audit trails must integrate with HIPAA-compliant monitoring tools to track unusual access patterns or breaches. Addressing these challenges often involves implementing permissioned networks and hybrid architectures, which add complexity and cost. Healthcare organizations may also need to collaborate with HIPAA compliance experts to ensure their blockchain systems meet regulatory standards.
How to Evaluate Blockchain Vendors
Choosing the right blockchain vendor is no small task, especially for healthcare organizations. It requires a detailed evaluation of both the vendor's general capabilities and their specific approach to blockchain technology - particularly when it comes to data security and regulatory compliance. With 54% of organizations reporting a data breach caused by a third-party vendor in the past year [5], taking the time to assess vendors thoroughly is not just smart - it’s essential for safeguarding your organization and protecting patient information.
Blockchain Risk Assessment Framework
To navigate the risks associated with blockchain vendors, it's helpful to use a structured framework for evaluation. This ensures you address the cybersecurity and operational challenges that come with blockchain technology.
Start by looking at the vendor’s track record with data breaches. Investigate the scope of any incidents they’ve experienced and how they responded to them. This will give you a sense of their security maturity [4]. Next, evaluate their regulatory compliance, particularly their adherence to HIPAA and HITECH standards. As Deepti Gupta et al. emphasize:
In terms of security and privacy, it is required to conduct a thorough vendor assessment that helps to ensure that these vendors adhere to industry best practices, compliance standards (such as GDPR or HIPAA), and have robust security controls in place to safeguard against cyber threats and unauthorized access [3].
When it comes to blockchain-specific features, focus on three key areas:
- Decentralization and immutability: Ensure the vendor’s blockchain supports peer-to-peer interaction and offers cryptographic tamper resistance [2].
- Smart contracts: Evaluate how they implement smart contracts for automated processes and transparent transactions [2].
- Data protection and confidentiality: For handling Protected Health Information (PHI), vendors should use private permissioned blockchains, like Hyperledger Fabric, which support private data collections to maintain confidentiality while enabling aggregated data use [2].
Beyond technical features, assess operational factors such as service continuity and financial stability to ensure the vendor can support your organization for the long haul [4]. Also, review their integration capabilities. A strong vendor will align with HL7 FHIR standards, offer middleware for seamless EHR compatibility, and enhance existing security frameworks (e.g., SAML/LDAP single sign-on and secure network endpoints) [1].
Using Censinet for Blockchain Vendor Assessments
Managing this complex evaluation process can be streamlined with tools like Censinet RiskOps™. This platform centralizes the entire vendor assessment lifecycle, automating key steps and consolidating workflows into a single system. Instead of juggling multiple tools, you can handle everything from initial questionnaires to ongoing risk monitoring in one place.
Censinet RiskOps™ simplifies the process with AI-driven features that speed up security questionnaires, summarize vendor documentation, and highlight critical integration details and fourth-party risks. It also generates risk summary reports based on all collected assessment data. The platform ensures consistent evaluations by applying rigorous standards across all blockchain vendors, covering areas like smart contract security, key management, API risks, and HIPAA compliance.
Collaboration is another standout feature. Censinet routes critical findings and tasks to relevant stakeholders, including members of your AI governance committee, for review and approval. A real-time risk dashboard aggregates data, providing your team with instant visibility into each vendor’s risk profile. This makes it easier to compare vendors side by side and make informed decisions. By combining automation with human oversight, Censinet allows your team to scale assessments efficiently while maintaining the expert analysis needed to make sound choices.
sbb-itb-535baee
Strategies for Reducing Blockchain Vendor Risks
Once you've chosen a blockchain vendor, it's crucial to take steps to minimize risks. This involves implementing technical safeguards, establishing clear contractual terms, and maintaining ongoing oversight. Let’s break down how to secure your blockchain deployment effectively.
Technical Controls for Blockchain Security
The way you design your system’s architecture plays a vital role in protecting patient data. For healthcare organizations, a hybrid on-chain/off-chain setup is often the best choice. Here’s how it works: sensitive Protected Health Information (PHI) is stored in encrypted, HIPAA-compliant databases off the blockchain, while only cryptographic hashes or pointers are recorded on-chain. This approach not only secures sensitive data but also aligns with HIPAA's "minimum necessary" rule. Using permissioned blockchain networks like Hyperledger Fabric or R3 Corda ensures that only authenticated members with defined roles can access the network, balancing privacy with transparency requirements [1].
Smart contracts are another essential component. These automate access controls and enforce security policies, but they must be developed with security in mind, as their immutability means you can’t modify them after deployment [1].
To further strengthen security, implement strong cryptographic key management practices, such as regular key rotation and secure storage in Hardware Security Modules (HSMs). Empower patients with control over their keys. Additionally, enforce multi-factor authentication (MFA) and adopt a zero-trust model. Use strong encryption protocols like TLS/SSL and secure VPN tunnels for all data transfers between on-chain and off-chain systems [1].
While technical measures are critical, they need to be paired with robust governance and clear contractual agreements.
Governance and Contract Requirements
Contracts with vendors should clearly define security responsibilities. This includes outlining how data will be protected, detailing incident response procedures, and ensuring compliance with regulatory standards [3]. Service level agreements (SLAs) should specify performance expectations and set response time benchmarks for addressing security incidents.
Governance policies must also address key operational questions: Who is allowed to join the blockchain network? How are disputes resolved? How is patient identity verified? [1]. In some cases, these governance processes can be automated using smart contracts, which help enforce consistent security and regulatory standards [3].
But security doesn’t stop there - continuous monitoring and lifecycle management are just as important.
Ongoing Monitoring and Lifecycle Management
Managing risks isn’t a one-and-done task. It requires constant vigilance. Blockchain’s immutable nature provides a tamper-proof record of vendor interactions, data changes, and assessments, which enhances both transparency and accountability [2]. By integrating blockchain audit logs into existing HIPAA audit tools, healthcare organizations can quickly detect unusual access patterns or potential breaches in real time [1].
To streamline this process, tools like Censinet RiskOps™ can be invaluable. They provide real-time tracking of vendor activities, performance, and compliance. Continuous monitoring through such platforms can identify security incidents, contractual violations, or new risks early on. Automating compliance checks and reporting with smart contracts further reduces manual effort while ensuring vendors stay aligned with regulatory standards [3].
Conclusion: Building Resilience with Blockchain Risk Management
Blockchain technology gives healthcare organizations a powerful way to improve data security, integrity, and transparency. However, its decentralized nature and immutability also bring unique risks that demand careful oversight of vendors. As highlighted in the strategies above, managing these risks is not optional - it’s a critical part of ensuring effective cybersecurity in healthcare. The secret to successful blockchain adoption lies in treating risk management as an active, ongoing effort, not a one-time task.
To address these challenges, a well-rounded management strategy is key. From the start, healthcare organizations need to tackle cybersecurity vulnerabilities, operational hurdles, and regulatory compliance issues head-on. This includes using hybrid on-chain/off-chain architectures to safeguard PHI, establishing clear governance frameworks, and implementing automated monitoring and audit trails. Blockchain’s core strengths - transparency, traceability, and immutability - provide a solid foundation for vendor risk management by ensuring tamper-proof records of all interactions and security evaluations [3].
With so much at stake, blockchain security cannot be left to chance. Continuous monitoring throughout the blockchain’s lifecycle is essential [2]. This proactive approach ensures quick responses to emerging issues, preventing minor problems from snowballing into major security breaches.
Tools like Censinet RiskOps™ can play a key role in supporting this vigilant approach. By leveraging strong technical controls, clear contractual agreements, and automated compliance monitoring, healthcare organizations can unlock blockchain’s potential while protecting patient data and meeting regulatory requirements. Those who view blockchain risk management as a strategic opportunity, rather than a challenge, will be better positioned to strengthen their cybersecurity defenses and thrive in a rapidly evolving digital landscape.
FAQs
What are the key cybersecurity risks of using blockchain in healthcare?
Blockchain technology in healthcare brings its own set of cybersecurity challenges that need careful attention. These include threats like unauthorized access to sensitive patient data, privacy breaches, and cyberattacks such as phishing, Sybil attacks, and 51% attacks. On top of that, flaws in cryptographic keys and gaps in the digital infrastructure supporting blockchain systems can make them even more vulnerable.
To address these risks, healthcare organizations should adopt strong security measures. This means setting up rigorous security protocols, conducting regular audits of blockchain systems, and performing detailed vendor risk assessments before integrating blockchain solutions.
How does blockchain's immutability help meet HIPAA compliance requirements?
Blockchain's unchangeable nature plays a key role in supporting HIPAA compliance by safeguarding the integrity of health data. Once information is recorded, it cannot be altered or erased, ensuring a reliable and secure record. This creates tamper-resistant audit trails, which offer detailed logs of who accessed the data and any modifications made. These features align closely with HIPAA's strict requirements for maintaining secure and accurate health records.
On top of that, blockchain technology boosts transparency and accountability by securely logging every instance of patient data access. This not only helps healthcare organizations meet HIPAA's privacy and security standards but also strengthens trust in how they handle sensitive information.
What factors should healthcare organizations evaluate when choosing a blockchain vendor?
When choosing a blockchain vendor, healthcare organizations need to focus on a few essential factors. Start with the vendor's reputation - a trusted name in the industry can provide peace of mind. Equally important are their cybersecurity measures, which should include strong encryption and permission management to safeguard sensitive data. Make sure the vendor's solutions align with key regulations like HIPAA to ensure compliance.
It's also crucial to examine the vendor’s approach to risk assessment and their ability to address vulnerabilities. Look for transparency in their operations and a solid track record in managing both cybersecurity and operational risks. Vendors with proven experience in healthcare-specific applications are far more likely to deliver a secure and smooth integration process.


