How to Build a TPRM Team That Actually Reduces Healthcare Risk (Step-by-Step Guide)
Post Summary
Building an effective Third-Party Risk Management (TPRM) team is essential for healthcare organizations to protect patient data, comply with regulations like HIPAA, and minimize vendor-related risks. Here’s a quick breakdown of the process:
- Secure Executive Support: Gain leadership buy-in by demonstrating the financial and operational risks of vendor breaches, like the 2024 Change Healthcare cyberattack.
- Define Risk Tolerance: Establish risk appetite and governance frameworks to manage vendor risks systematically.
- Assemble a Cross-Functional Team: Include experts from IT, legal, compliance, procurement, and clinical operations for a well-rounded approach.
- Conduct Risk Assessments: Create a vendor inventory, identify vulnerabilities, and prioritize high-risk vendors.
- Leverage Automation Tools: Use platforms like Censinet RiskOps™ to streamline workflows, automate assessments, and monitor vendor performance in real time.
- Implement Continuous Monitoring: Track vendor risks proactively to address issues before they escalate.
- Train Your Team: Provide regular training on cybersecurity, compliance standards, and incident response through hands-on drills and audits.
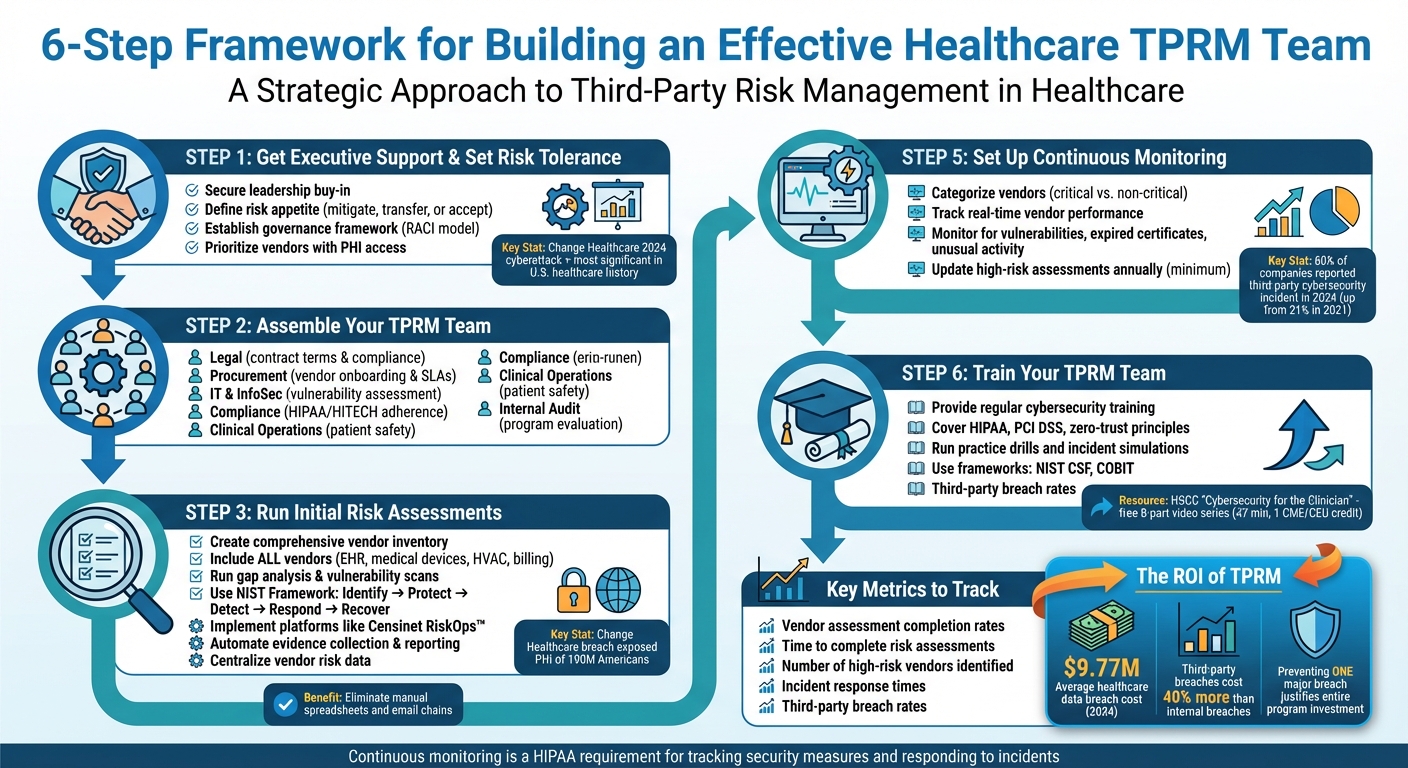
6-Step Framework for Building an Effective Healthcare TPRM Team
Step 1: Get Executive Support and Set Risk Tolerance Levels
Get Leadership Approval
For your TPRM program to succeed, securing executive buy-in is non-negotiable. Leadership must recognize that third-party risks can have a direct and severe impact on the organization. A stark example is the 2024 Change Healthcare cyberattack, labeled by the American Hospital Association as the most significant cyberattack in U.S. healthcare history. This incident underscores the devastating consequences of a vendor breach [1].
"Begin at the top; management must grasp the full impact of third-party risks." - Zuzana Rebrova, Head of Third-Party Cyber Risk Management, Swiss Re [2]
When presenting to the board and key stakeholders, focus on clear objectives for your TPRM program. Highlight the financial and operational advantages, such as how HITRUST inheritance can streamline certification processes by reusing validated controls. As Jason Kor, Principal of Third Party Cyber Risk at HITRUST, explains: "Inheritance is a powerful feature in HITRUST MyCSF that can make your certification journey far more efficient." Stress how the program safeguards the organization from breaches, regulatory fines, and operational disruptions.
Once you’ve secured leadership support, the next step is to establish well-defined risk tolerances.
Set Risk Tolerance and Governance Framework
With leadership backing in place, it’s time to define your organization’s risk appetite. This involves deciding which risks your team will mitigate, transfer, or accept [2][3]. Start by setting clear program goals and pinpointing specific areas of risk, such as information security, privacy, financial stability, and reputation [2].
"The more you coordinate and socialize your intended outcome with the leaders and stakeholders in the organization, the more you're able to set resource levels, measure whether you're actually achieving the value you want, and structure your program accordingly." - Matthew Solomon, VP of Technology and Cyber Risk Management, Humana [2]
Build a governance framework to manage vendor risks effectively. Models like RACI (Responsible, Accountable, Consulted, Informed) are great tools to clarify who owns each aspect of the program. Prioritize vendors based on their access to Protected Health Information (PHI) or critical services, ensuring your efforts are concentrated on the highest-risk relationships [2]. Make sure your framework integrates compliance with regulations such as HIPAA, HITECH, GDPR, and relevant state laws from the outset [2]. This proactive approach shifts your organization from reacting to risks to managing them strategically.
Step 2: Assemble Your TPRM Team
Define Team Roles and Responsibilities
To effectively manage third-party risks, it's essential to assign clear roles and responsibilities within your team. A structured framework, often referred to as the "three lines of defense", can help organize your approach to risk management. This ensures every team member understands their role in safeguarding the organization against third-party threats.
"Established roles and shared responsibilities within an organization are fundamental to an effective TPRM program. Well-defined positions ensure a resilient, effective, and secure operational ecosystem, laying the foundation for success amid evolving threats and challenges. Understanding who owns which activities is essential to executing a well-structured TPRM process." – Aravo [5]
Your team should include experts from areas like operations, clinical services, finance, IT, legal, and auditing. These individuals bring specialized knowledge to the table - whether it's risk analysts conducting vulnerability assessments, vendor managers negotiating service level agreements (SLAs), or compliance professionals ensuring adherence to regulations like HIPAA and HITECH [6].
Internal audit functions also play a critical role, offering independent assessments of your TPRM program's effectiveness and identifying areas for improvement. Each role contributes to aligning third-party risk management efforts with your organization's broader risk strategy and objectives [5].
After defining roles, expand your framework by incorporating insights from various departments to create a well-rounded team.
Include Multiple Departments
Collaboration across departments is crucial because third-party risks touch every part of the organization. Representatives from Legal, Procurement, IT, and Compliance should all have a seat at the table to address vendor-related risks comprehensively [5].
- Legal teams handle contract terms and ensure compliance with regulatory requirements.
- Procurement specialists focus on detecting risks during vendor onboarding and negotiating SLAs [5].
- IT and information security professionals assess vulnerabilities in technology and safeguard sensitive data, such as electronic protected health information (ePHI).
- Compliance teams ensure adherence to state and federal healthcare laws [5].
- Clinical operations staff can provide insight into patient safety concerns, while credentialing experts vet provider qualifications and certifications [7].
Regular cross-departmental meetings and centralized reporting are key to maintaining clear communication [5]. A shared platform for risk assessments ensures everyone stays in sync. Training internal teams on information security risks empowers them to handle vendor-related challenges effectively and track remediation efforts [4].
It’s also important to recognize that different departments may have varying approaches to risk. For example, your CFO and Chief Compliance Officer might prioritize financial and regulatory risks, while your Chief Medical Officer may focus on patient safety. Balancing these perspectives ensures a well-rounded strategy [6].
| Role/Department | Responsibilities | Connection to Enterprise Risk Management |
|---|---|---|
| Executive Leadership | Set strategy, define risk tolerance, promote compliance, and encourage teamwork [5] | Oversees third-party risk management to align with company values and regulatory requirements [5] |
| Vendor Managers & Procurement | Identify risks during onboarding, negotiate SLAs, and monitor vendor performance [5] | Ensures vendor relationships align with organizational goals and reduce operational risks [5] |
| Risk Analysts & Information Security | Assess and mitigate risks, prevent data breaches, and develop incident strategies [5] | Supports overall risk assessment and strengthens organizational defenses [5] |
| TPRM Leads | Coordinate across departments and guide risk management processes [5] | Ensures activities align with enterprise-wide governance and risk tolerance [5] |
| Internal Audit | Evaluate TPRM practices, test processes, and conduct post-incident reviews [5] | Drives ongoing improvements and enhances organizational resilience [5] |
Step 3: Run Initial Risk Assessments
Now that your TPRM team is in place, it's time to dive into risk assessments. These assessments are essential for identifying vulnerabilities within your vendor network. By doing this early, you gain a clear understanding of potential risks and can address them before they escalate into major problems.
Create a Vendor and Asset Inventory
Begin by cataloging all third-party vendors connected to your organization. This includes obvious partners like electronic health record (EHR) providers and medical device manufacturers, but don’t overlook less obvious ones, such as HVAC contractors, billing services, and software vendors. The infamous Target breach is a cautionary tale - attackers used credentials from Fazio Mechanical Services, an HVAC vendor, to infiltrate Target's network, compromising the data of over 100 million customers [9].
Your inventory should include key details like vendor names, the services they provide, the type of data they access (especially ePHI), contract terms, and their integration points with your network. Make sure this list is centralized and regularly updated so all departments can access it. This inventory lays the groundwork for identifying gaps and prioritizing fixes. After all, you can't address risks you aren't aware of.
Run Gap Analysis and Vulnerability Scans
Once your inventory is complete, the next step is identifying weaknesses in your defenses. The HHS Assistant Secretary for Technology Policy provides a Security Risk Assessment (SRA) Tool tailored for healthcare providers, especially smaller practices [8]. While HIPAA compliance doesn't mandate NIST Standards, they are widely recognized as best practices for assessing IT risks [8].
Focus on high-priority threats like stolen credentials. For instance, in February 2024, a ransomware attack on Change Healthcare exploited stolen employee credentials and the lack of multi-factor authentication. This attack disrupted prescription processing for weeks and exposed the PHI of 190 million Americans. To mitigate the fallout, UnitedHealth issued $8.5 billion in emergency loans to stabilize hospitals and pharmacies [9]. Other critical vulnerabilities include outdated backup systems, compromised VPNs, and software supply chain threats like the SolarWinds breach, which affected roughly 18,000 customers through malware in legitimate software updates [9].
Use established frameworks to organize your findings. For example, the NIST Cybersecurity Framework breaks down into five key functions: Identify (catalog assets and risks), Protect (implement safeguards), Detect (monitor for threats), Respond (develop incident response plans), and Recover (restore operations after an incident). This structure ensures your approach is methodical and actionable, helping you move from identifying risks to actually solving them.
"It's not enough to know the risks. We have to push vendors to fix them. That's where real risk reduction happens." – Tamra Durfee, vCISO, Fortified Health Security [10]
Demand thorough assessments, especially for medical devices, which come with unique security challenges due to their network integration [10]. Focus on vulnerabilities that could expose personally identifiable information (PII) and protected health information (PHI), as these carry hefty regulatory and financial penalties. Go beyond ticking compliance boxes - actively engage vendors to address issues. Use continuous follow-ups and contractual obligations to ensure they take action [10].
Step 4: Use Automation Tools to Save Time
Relying on manual processes for Third-Party Risk Management (TPRM) can drain both time and resources. Tools like spreadsheets, endless email threads, and manual follow-ups often create bottlenecks that slow down risk assessments and leave gaps in oversight. When you're managing dozens - or even hundreds - of vendors, automation becomes a game-changer. It helps you move away from outdated methods and adopt a more efficient, real-time approach to vendor management.
Simplify TPRM with Censinet RiskOps™

Censinet RiskOps™ is a platform designed specifically for healthcare organizations to centralize and streamline TPRM workflows. It offers a unified command center that provides a clear view of risks across your vendor network. From initial assessments to ongoing monitoring, the platform automates tasks and ensures they’re assigned to the right team members, cutting down on inefficiencies.
With Censinet Connect™, vendor risk assessments become much easier. Vendors can directly upload their security documents and respond to questionnaires in a collaborative environment. This eliminates the endless back-and-forth of emails and keeps all assessment data in one accessible location.
Censinet AITM takes automation a step further by accelerating the processing of vendor questionnaires. Its AI capabilities summarize vendor evidence, highlight key product integration details, identify fourth-party risks, and generate risk summary reports. This approach speeds up evaluations while keeping human oversight in place, ensuring that the process remains thorough and reliable. By automating these steps, organizations not only save time but also enhance their ability to manage healthcare-related vendor risks effectively.
Automation doesn’t stop at assessments - it also transforms evidence collection and reporting.
Automate Evidence Collection and Reporting
AI-powered tools can simplify tasks like validating evidence, drafting policies, and generating risk reports. Censinet AI integrates configurable rules and review processes into its automation, ensuring that critical decisions remain under human control. Through a human-in-the-loop approach, your risk team reviews AI-generated summaries and approvals before finalizing assessments.
The platform centralizes oversight of AI-related policies and risk management. It organizes assessment findings and assigns tasks to the appropriate stakeholders, all while real-time data is displayed in an intuitive AI risk dashboard. This centralized hub makes it easier to maintain continuous oversight and accountability. While automation tackles the heavy lifting, your team can focus on more strategic tasks, like mitigating risks and planning for future challenges.
sbb-itb-535baee
Step 5: Set Up Ongoing Monitoring and Reporting
Relying solely on periodic reviews won't cut it when it comes to staying ahead of fast-moving security challenges. New vulnerabilities, leaked credentials, and the constant evolution of ransomware threats make continuous monitoring a necessity. A vendor that cleared your assessment a few months ago could now be in the middle of a security incident. Continuous monitoring fills the gap between scheduled reviews by keeping you informed in real time.
By building on your initial risk assessments, continuous monitoring takes your risk management efforts to the next level. It provides real-time updates on your vendors' security posture, alerting you to potential issues before they escalate into breaches. Imagine the difference between discovering compromised vendor credentials months later during a scheduled review versus receiving an alert that allows you to act within hours. For healthcare organizations handling sensitive patient data and critical systems, this real-time visibility is essential - not just for regulatory compliance but for ensuring the safety and security of your operations. It’s about staying proactive and maintaining constant oversight.
Monitor Vendor Risks in Real Time
Start by categorizing your vendors based on their importance and risk level. Divide vendors into critical and non-critical groups according to their impact on your business. Then, assess their risk level - high, medium, or low - by considering factors like regulatory requirements. Pay close attention to inherent risks, especially if vendors have access to sensitive information like non-public personal information (NPI) or protected health information (PHI). Such access automatically increases their risk profile.
AI-powered dashboards can help you track vendor performance continuously, flagging potential issues like new vulnerabilities, expired security certificates, configuration changes, or unusual network activity. To handle these alerts effectively, define roles and responsibilities ahead of time. For instance, determine who will address security concerns, compliance violations, or other flagged issues like environmental or social governance risks.
When an alert comes in, assess its severity first. For critical issues, take immediate steps: contact the vendor, investigate the problem, and apply protective measures such as temporarily revoking their system access. Require the vendor to provide a corrective action plan, and only restore access once they’ve provided verifiable proof that the issue has been resolved. This approach ensures you respond decisively but avoid overreacting to less serious concerns.
Track Metrics and Share Progress Reports
Monitoring is only effective if it leads to measurable improvements. Tailor your reporting to match your program's stage of development. For newer programs, focus on high-level metrics like the number of vendors assessed, compliance rates, and major risks identified. Jose Costa, Sr. Director of GRC Labs & Research at OneTrust, explains:
"If you're just starting to implement a TPRM program, you may report how many vendors have gone through the process, how many are compliant, etc. Or you may report the major risks you've assessed, how you mitigated them, and how you plan to evaluate them on a regular basis."
For more established programs, shift the focus to demonstrating the program's impact. Matthew Solomon, VP of Technology and Cyber Risk Management at Humana, highlights the challenge:
"In information security, there are very rarely precise and actual estimates of real risk. So we have to look for indicators of risk, proxies for risk, or even more lagging indicators of the actual number of incidents. In terms of showing the actual impact of the program, the trick is really to get as close to the quantification of your risk level as you can and how you're driving that down."
Key metrics to track include assessment duration, risk tier distribution, incident volume, remediation time, and overdue actions. Use these metrics to showcase reductions in third-party risk, and highlight these achievements in reports to senior management and the board. For high-risk or critical vendors, update risk assessments at least annually, or more often if circumstances change - such as new contracts, data-sharing agreements, mergers, or newly identified risks.
Finally, plan for routine program reviews whenever significant changes occur. Reassess your vendor management policies, taking a broad look at issues flagged with other vendors in similar categories. This systematic approach not only strengthens your program but also helps justify its costs and secure future investments by clearly demonstrating its value.
Step 6: Train Your TPRM Team
Even the most advanced TPRM tools won’t succeed without a team that’s properly trained. Healthcare organizations face unique challenges, from maintaining HIPAA compliance to safeguarding patient data, making it essential for every team member to have specialized knowledge.
Provide Regular Training
Training should be tailored to each team member’s specific responsibilities. Start with the basics of cybersecurity hygiene, such as identifying phishing attempts, malware risks, and social engineering tactics. It’s equally important for your team to have a strong understanding of HIPAA, PCI DSS, and other data protection standards.
Introduce zero-trust principles and well-established frameworks like NIST CSF and COBIT into your training sessions. These frameworks provide a structured approach that helps your team make consistent and defensible risk decisions. Beyond just meeting compliance requirements, training should emphasize how TPRM processes actively contribute to overall security. Mark Jarrett, Chairman of the Healthcare and Public Health Sector Coordinating Council (HSCC), highlights the importance of leadership support:
"Every hospital C-Suite executive needs to support a good cybersecurity program, which includes training clinical staff on the basics." [11]
In April 2023, the HSCC released "Cybersecurity for the Clinician," a free 8-part video training series totaling 47 minutes. This program, which offers one CME/CEU credit hour, was developed by the HSCC Cybersecurity Working Group - a coalition of over 400 industry and government organizations - with funding from Health Care Service Corporation and Health-ISAC. The series, endorsed by leading cybersecurity experts, delivers practical advice for clinicians. Erik Decker, Chief Information Security Officer for Intermountain Health and Chair of the HSCC Cybersecurity Working Group, remarked:
"This video series articulates simple cybersecurity basics for the frontline technology user. The fact that the on-camera host is an emergency room physician and a self-trained hacker demonstrates the credibility of the message that clinicians and students need to hear: cyber safety is patient safety." [11]
While theoretical knowledge is valuable, it’s the hands-on practice that ensures these concepts are truly understood.
Run Practice Drills and Audits
Practical drills are essential for preparing your team to handle real-world incidents. Start by developing an incident management strategy that enables your team to quickly identify, respond to, and mitigate vendor security issues. Use incident questionnaires that are regularly updated to ensure simulations gather all the necessary data. During these drills, monitor team performance to identify any bottlenecks or communication breakdowns.
Create scenarios where your team practices using consolidated dashboards to assess risk ratings and flagged responses. Introduce automated workflow playbooks that adapt to different levels of incident severity, and have your team follow these protocols under time-sensitive conditions. These drills help reinforce existing procedures and build the muscle memory needed for real incidents. Assign clear risk ownership roles with automated reminders to ensure accountability, and practice proactive vendor reporting during the exercises. By running these drills, you can uncover weak points in your processes and strengthen your team’s ability to manage healthcare vendor risks effectively.
How to Measure TPRM Program Success
Once you've established a solid TPRM framework, the next step is proving its effectiveness. Building a TPRM team is just the beginning - you need to show that your efforts are actively reducing risk. Healthcare executives are looking for hard data that demonstrates the value of your program, especially when you're asking for more budget or resources. Without clear metrics, it's tough to prove whether your program is genuinely impactful or just meeting compliance requirements.
Track Key TPRM Metrics
Start by setting baseline metrics and monitoring how they change over time. Some key metrics to focus on include:
- Vendor assessment completion rates
- Time to complete risk assessments
- Number of high-risk vendors identified and addressed
- Incident response times
Pay close attention to third-party breach rates. A recent Health3PT survey (April–June 2023) found that 55% of healthcare organizations experienced a third-party breach within the past year. Even more alarming, 60% of companies reported a third-party cybersecurity incident in 2024, a sharp increase from 21% in 2021 [4][12].
Instead of relying on one-time cybersecurity ratings, track trends over several months. A steady improvement in ratings is far more meaningful than a single snapshot score [9]. Keep an eye on how many vendors transition from high-risk to medium- or low-risk categories after remediation. Other useful metrics include the average time to detect vendor vulnerabilities and the percentage of vendors with continuous monitoring in place. These indicators reveal whether your team is becoming more efficient and whether automation tools are delivering the expected time savings.
When presenting your program's value to leadership, be ready to quantify its financial impact. For example, the healthcare industry saw an average data breach cost of $9.77 million in 2024 [4]. If your TPRM program prevents even one major breach, the return on investment is undeniable. These metrics also lay the groundwork for benchmarking your efforts against industry leaders.
Use Benchmarking for Improvement
Automated monitoring and continuous assessments make it easier to benchmark your program and fine-tune your risk management strategies. Compare your metrics to industry standards and established TPRM programs to identify areas where you excel and where you might need improvement. Are your assessment completion times competitive? Are your risk remediation rates on par with top-performing programs? Benchmarking can uncover these insights.
Internal benchmarking is just as important. Compare your performance quarter over quarter to spot trends. For example, if your team completed 50 vendor assessments in Q1 but only 35 in Q2, dig into the reasons. Did you introduce more thorough assessments, or are resource constraints slowing you down? Centralized GRC/TPRM reporting can provide a clear, consolidated view of risk impacts [12]. This kind of reporting helps you identify patterns across your vendor network and understand how interconnected risks might ripple through your organization.
Conclusion
Building a strong Third-Party Risk Management (TPRM) team demands ongoing effort, executive support, smart use of technology, continuous monitoring, and regular training. Without leadership backing, TPRM risks becoming just another compliance task. However, with executive sponsorship, it transforms into a strategic priority that gains the attention it deserves at the board level. This leadership not only ensures a clear focus but also drives investments in the technology and training essential for success.
Consider this: third-party breaches cost 40% more to address than internal ones. Preventing even one incident can justify the entire program’s investment [13]. That’s where automation tools like Censinet RiskOps™ come into play. These tools simplify workflows, allowing your team to concentrate on reducing risks strategically.
Continuous monitoring isn’t just a best practice - it’s a HIPAA requirement for tracking security measures and responding quickly to incidents [15]. Your team should regularly reassess risks based on vendor importance and stay alert to emerging threats, like financial instability, regulatory changes, or shifts in the industry [15]. Integrating monitoring with your organization’s SIEM systems can also help detect vulnerabilities early [14].
But technology alone isn’t enough. The human factor plays a crucial role. Regular team training is essential to stay ahead of evolving threats and to make the most of new technologies. Conduct practice drills and audits to test your incident response plans. A well-prepared team with clear protocols and effective communication is your strongest defense against third-party risks [16].
FAQs
How does executive support improve the performance of a TPRM team in healthcare?
Executive backing plays a key role in the success of a TPRM team in healthcare. When leadership prioritizes the program, it signals its importance as a strategic focus. This involvement helps establish a clear understanding of the organization's risk tolerance, ensures adequate resources are allocated, and fosters a culture that values risk awareness throughout the organization.
With aligned goals and steady oversight from leadership, the TPRM team is better equipped to pinpoint, evaluate, and address risks linked to third parties - contributing to a safer and more secure healthcare environment.
What are the main roles and responsibilities of a TPRM team in healthcare?
A well-rounded Third-Party Risk Management (TPRM) team brings together essential roles such as a Program Manager, Information Security Analyst, Healthcare Compliance Officer, Vendor Relationship Manager, and an Executive Sponsor.
Each role plays a critical part in the process: identifying and assessing potential risks, maintaining strong vendor relationships, ensuring compliance with regulations, keeping a close eye on risks through ongoing monitoring, and addressing incidents promptly. By working together, these team members help protect healthcare organizations from third-party risks while ensuring smooth day-to-day operations.
What are the benefits of continuous monitoring in managing third-party risks in healthcare?
Continuous monitoring plays a key role in helping healthcare organizations manage third-party risks. By spotting potential threats as they emerge, it enables swift action to address issues before they grow into larger problems. This proactive approach ensures that vendors stick to security and privacy standards, minimizing the chances of mistakes, financial setbacks, or data breaches. In turn, it boosts patient safety and reinforces overall risk management strategies.
Related Blog Posts
- How to Conduct Effective Third-Party Risk Assessments
- How to Build a TPRM Team That Actually Reduces Healthcare Risk (Step-by-Step Guide)
- Healthcare Vendor Risk Management Framework: Templates, Tools, and Best Practices
- Healthcare Third-Party Risk Management Maturity Model: Where Does Your Organization Stand?


