CCPA vs. HIPAA: Key Differences in Breach Response
Post Summary
When it comes to data breaches, CCPA and HIPAA have different rules, timelines, and penalties. Here's what you need to know:
- HIPAA protects health data (PHI) and applies to healthcare providers, health plans, and business associates. Breaches must be reported within 60 days, and penalties are managed by HHS based on the organization's responsibility.
- CCPA covers personal data of California residents beyond health information. It requires businesses to notify affected individuals "as quickly as possible" and allows consumers to sue for damages if nonencrypted data is exposed due to poor security.
Quick Overview of Key Differences:
- Scope: HIPAA focuses on PHI; CCPA covers broader personal data.
- Breach Definition: HIPAA assumes a breach unless proven low risk; CCPA ties breaches to lack of reasonable security.
- Notification Timelines: HIPAA allows up to 60 days; CCPA requires immediate action.
- Penalties: HIPAA penalties are enforced by HHS; CCPA includes fines and consumer lawsuits.
For healthcare organizations handling both HIPAA and CCPA data, having a clear breach response plan is critical. Encrypting data, aligning notification processes, and managing third-party risks are vital steps to meet both regulations.
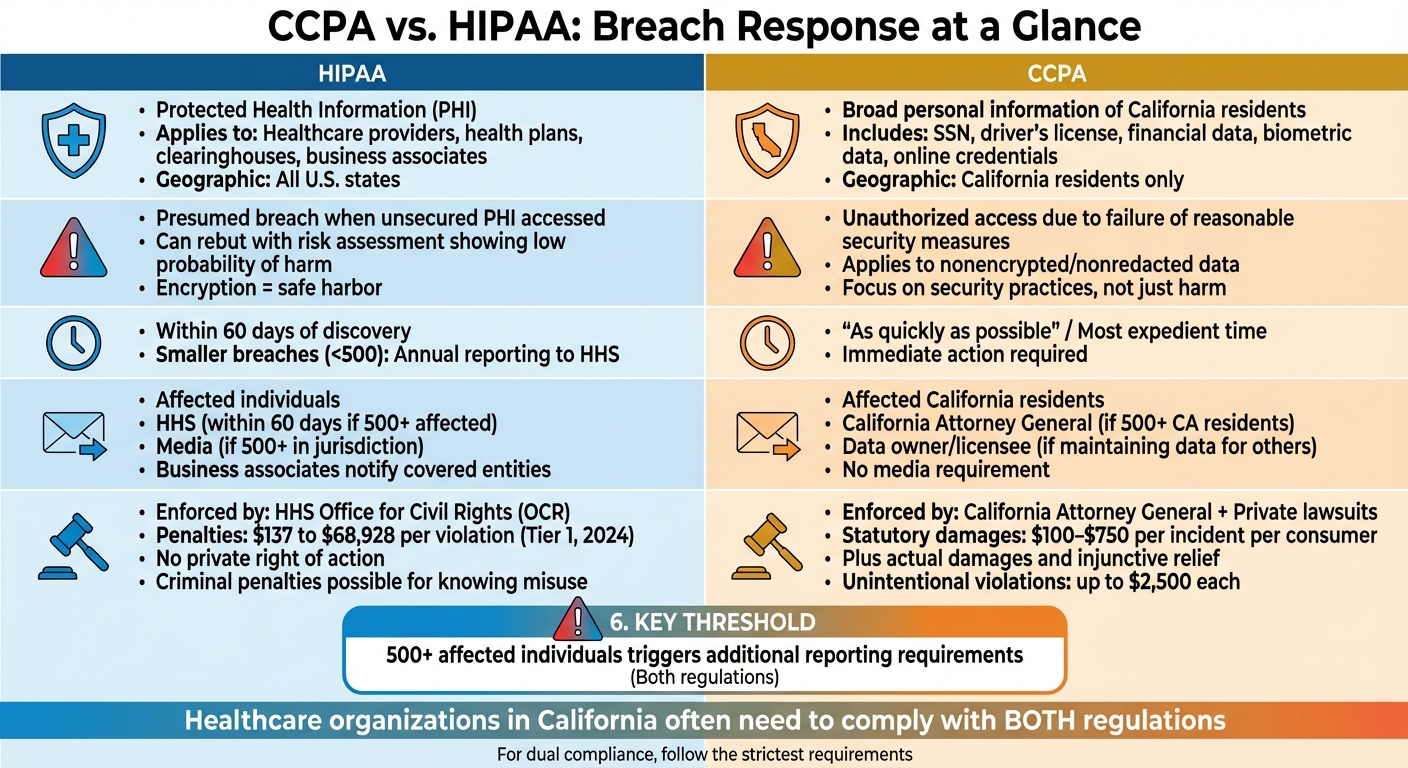
CCPA vs HIPAA Breach Response Requirements Comparison Chart
HIPAA Breach Response Requirements
What Counts as a Breach Under HIPAA
Under HIPAA, any unauthorized access to unsecured Protected Health Information (PHI) is generally presumed to be a breach. However, your organization can challenge this presumption by conducting a thorough risk assessment to demonstrate that the likelihood of harm is low. This assessment evaluates factors such as the type and extent of the PHI involved, who accessed it, and efforts to mitigate the situation.
For instance, if an unencrypted laptop containing patient records is stolen, this is typically considered a breach. On the other hand, if the laptop is encrypted and the encryption keys remain secure, the PHI is deemed protected, and notification requirements are generally not triggered. These criteria form the foundation for understanding the notification rules that follow.
HIPAA Notification Timelines and Recipients
When a breach is confirmed, compliance with HIPAA's notification timelines is critical. Affected individuals must be informed without delay, and no later than 60 days after the breach is discovered[6]. For breaches involving 500 or more individuals in a single state or jurisdiction, the following steps are required:
- Notify affected individuals.
- Inform the Department of Health and Human Services (HHS) through its online breach portal.
- Alert prominent media outlets serving the impacted region.
For breaches affecting fewer than 500 individuals, the incident can be documented internally. However, HHS must still be notified, no later than 60 days after the end of the calendar year in which the breach occurred.
Business associates also play a role - they are required to notify the covered entity promptly, as outlined in their contracts. Notifications sent to individuals should be clear and easy to understand. They must include:
- A brief explanation of what happened.
- The types of PHI involved.
- Steps individuals can take to protect themselves.
- Actions being taken to investigate and prevent future incidents.
- Contact details for further questions or concerns[6].
This structured approach to reporting highlights HIPAA's focus on accountability and transparency.
HIPAA Enforcement and Penalties
The Office for Civil Rights (OCR) within HHS enforces HIPAA's breach notification rules, with penalties based on the level of responsibility. Starting in 2024, Tier 1 violations - where the breach occurred without the organization's knowledge - carry fines ranging from $137 to $68,928 per violation[7]. Beyond monetary penalties, OCR can require corrective action plans, ongoing monitoring, or, in severe cases, refer violations to the Department of Justice for criminal prosecution.
Criminal penalties apply when PHI is knowingly misused or disclosed. These penalties become harsher if there’s intent to profit from the data or if false pretenses are involved[5]. While OCR typically handles civil cases, particularly egregious violations can lead to criminal charges, including fines and imprisonment.
It’s also important to note that HIPAA sets a federal standard, but state laws can impose stricter requirements. For example, Puerto Rico requires notification within 10 days of a breach and imposes fines of up to $5,000 per violation for delays[6]. Healthcare organizations must ensure their response plans address both federal and state obligations to remain compliant.
CCPA Breach Response Requirements
What Counts as a Breach Under CCPA
Under the CCPA, a breach occurs when unauthorized access or acquisition of computerized personal information compromises its security, confidentiality, or integrity [2][4].
This includes a resident’s name combined with sensitive details like Social Security numbers, driver’s license or state ID numbers, financial account or payment card data (including credentials), medical or health insurance information, biometric data, or online account credentials [9]. The CCPA introduces an important distinction: its private right of action applies specifically to breaches involving nonencrypted and nonredacted personal information, where the breach stems from a business’s failure to maintain reasonable security procedures and practices [2][3].
Encryption and redaction can shield data from notification requirements and statutory damages [2][4]. This protection extends beyond health-related data alone. Healthcare organizations should note that while PHI (Protected Health Information) governed by HIPAA is mostly excluded from CCPA, this exemption applies only to that specific category of data - not the organization as a whole [3].
CCPA Notification Timelines and Content
California law requires businesses to notify affected California residents immediately after discovering a breach, with limited delays allowed for law enforcement needs or determining the breach’s scope [9]. If an organization holds data for another entity, it must notify the data owner or licensee as soon as the breach is detected [9].
The notification must include several key details:
- Name and contact information of the notifying entity
- A list of the types of personal information exposed
- Relevant dates (e.g., when the breach occurred and was discovered)
- A brief description of the breach
- Contact details for major credit reporting agencies if Social Security or driver’s license/ID numbers were involved [9]
Additionally, if the breach affects more than 500 California residents, the business must submit a sample copy of the notice to the California Attorney General [2].
Next, let’s take a closer look at how CCPA enforcement mechanisms and penalties set it apart from other regulations.
CCPA Enforcement and Penalties
The CCPA allows affected consumers to claim statutory damages ranging from $100 to $750 per incident - or actual damages - along with injunctive relief when their nonencrypted or nonredacted personal information is compromised [3][10]. This marks a major shift from HIPAA, which does not grant individuals the right to sue for damages directly.
The California Attorney General also plays a key role in enforcing CCPA breach obligations through regulatory actions. Legal experts have noted a rise in class-action lawsuits leveraging CCPA’s private right of action, particularly against hospitals and healthcare-adjacent companies when the breached data falls outside HIPAA’s PHI exemption [3][10]. Increasingly, both regulators and plaintiffs interpret "reasonable security" to include advanced cybersecurity measures - like encryption, multi-factor authentication, vendor risk management, and regular risk assessments - rather than just basic IT safeguards [2][10].
Healthcare organizations face twofold risks: scrutiny from the Attorney General and direct litigation from affected California residents. Unlike HIPAA’s tiered penalty approach, which considers intent and knowledge, CCPA imposes statutory damages on a per-consumer, per-incident basis. This means a single breach involving thousands of California residents can result in significant financial exposure. The best defense? Demonstrating that your organization has implemented and maintained security measures suited to the sensitivity of the data you handle [2][3]. For healthcare providers subject to both CCPA and HIPAA, having a robust breach response plan is not optional - it’s essential.
CCPA vs. HIPAA: Breach Response Differences
Let’s dive into how HIPAA and CCPA handle breach responses differently. For healthcare organizations serving California residents, understanding these distinctions is crucial since they often need to align with both regulations when creating an incident response plan.
Scope and Protected Data
HIPAA focuses on safeguarding protected health information (PHI), which includes any identifiable health details managed by covered entities like health plans, healthcare providers, clearinghouses, and their business associates - regardless of where the patients reside [11]. PHI under HIPAA is primarily tied to clinical health data.
CCPA, on the other hand, casts a wider net. It protects personal information of California residents, which includes names linked to Social Security numbers, driver’s license numbers, financial details, biometric data, and online credentials [9]. This means that while clinical records might fall under HIPAA, other data like employee HR records or patient billing addresses could be governed by CCPA.
Breach Triggers and Definitions
Under HIPAA, a breach is presumed when unsecured PHI is accessed, acquired, used, or disclosed without authorization - unless a risk assessment shows a low probability of compromise [11]. Organizations must assess factors such as the nature of the data, who accessed it, whether it was viewed, and what mitigation steps were taken. If PHI is encrypted and the encryption keys remain secure, notification requirements can typically be avoided.
In contrast, CCPA ties breach liability to incidents involving unauthorized access, exfiltration, theft, or disclosure of personal information due to a failure to implement reasonable security measures [2]. Two seemingly similar incidents might be treated differently under CCPA depending on whether the organization can prove it had proper controls in place. While HIPAA evaluates breaches based on the likelihood of harm, CCPA zeroes in on whether reasonable security practices were followed [2].
These differing definitions result in distinct notification protocols.
Notification Timelines and Recipients
The table below highlights the key differences in notification requirements:
| Requirement | HIPAA | California Breach Law (CCPA Context) |
|---|---|---|
| Timeline to notify individuals | Without unreasonable delay, but no later than 60 calendar days after discovery [11] | As quickly as possible, taking into account law enforcement and containment needs [9] |
| Regulatory notification | Notify HHS (OCR) within 60 days for breaches affecting 500+ individuals; smaller breaches reported annually [11] | Notify the California Attorney General if 500+ California residents are affected [9] |
| Media notification | Required for media outlets in the affected area if 500+ individuals are impacted [11] | Not required |
| Business associate/vendor notification | Business associates must notify covered entities within 60 days [11] | Entities maintaining data must inform the data owner upon discovery [9] |
These timelines reflect the contrasting approaches to enforcement, which we’ll explore next.
Enforcement and Penalties
Enforcement mechanisms further distinguish HIPAA from CCPA.
HIPAA enforcement is managed solely by the HHS Office for Civil Rights (OCR), which investigates breaches and complaints - particularly those involving 500 or more individuals [11]. Penalties under HIPAA range from $100 to $50,000 per violation, with annual caps. Notably, individuals cannot file lawsuits for HIPAA violations; only the government has the authority to enforce compliance.
CCPA, however, allows affected California residents to file private lawsuits for breaches involving nonencrypted or nonredacted personal information. Damages can range from $100 to $750 per incident, plus actual damages and injunctive relief [10]. The California Attorney General can also take enforcement actions, adding another layer of exposure. For breaches impacting thousands of residents, statutory damages can add up quickly. Legal experts have observed a rise in class-action lawsuits, especially when compromised data falls outside HIPAA’s PHI scope.
Healthcare organizations must navigate dual risks: federal oversight under HIPAA and potential lawsuits from California residents under CCPA. The best defense under both frameworks? Demonstrating strong and consistent security measures.
sbb-itb-535baee
Managing Dual Compliance: CCPA and HIPAA Together
When Both Regulations Apply
Healthcare organizations in California often find themselves navigating the requirements of both HIPAA and CCPA. This dual compliance typically comes into play when an organization qualifies as a HIPAA-covered entity or business associate and meets the definition of a "business" under CCPA - usually due to serving California residents and reaching CCPA's revenue or data thresholds [2].
This overlap is part of everyday operations. For instance, marketing websites often track visitor behavior using cookies and collect form submissions, which fall under CCPA's purview. At the same time, these organizations handle PHI in their electronic health records. Patient portals, which blend PHI with other consumer data, add another layer of complexity. Mobile health apps gather everything from device identifiers and usage patterns to appointment details. Additionally, third-party tools like CRM systems, telehealth platforms, and call centers frequently process both PHI and other personal information [2]. When a breach occurs in any of these systems, organizations must assess their obligations under both frameworks. This requires a unified strategy that aligns HIPAA and CCPA compliance at every stage of breach management.
Building an Integrated Incident Response Plan
The foundation of dual compliance lies in a unified data classification system. This system should differentiate between PHI under HIPAA, personal information regulated by California law, de-identified data, and operational system data [2]. Organizations need to map their systems to these classifications and identify which regulations apply. Tools like data flow diagrams and inventories that label sources as "CCPA-only", "HIPAA-only", or "dual-regulated" can streamline incident response by enabling faster and more accurate scoping [2].
Decision trees are another essential component. These tools help determine whether a breach involves PHI, California residents, encrypted data, or affects more than 500 individuals. To simplify compliance, organizations should follow the strictest notification timeline, regardless of the regulation. The plan should also clearly outline all required notifications, including those to affected individuals, HHS, the California Attorney General (if more than 500 California residents are impacted), and media outlets when thresholds are met [11][9][2].
Equally important are governance updates. Business associate agreements must require timely and detailed breach notifications from business associates to meet HIPAA's Breach Notification Rule [11][2]. Similarly, contracts with CCPA service providers should include breach notification clauses and cooperation requirements that align with California timelines [9][2]. Vendor due diligence should ensure that service providers are equipped to handle dual compliance, including segregating PHI from other personal information, preserving forensic evidence, and delivering timely impact reports.
Using Technology to Streamline Breach Response
Technology plays a critical role in managing dual compliance. Platforms like Censinet RiskOps™ simplify the process by centralizing risk assessments, automating incident triage, and tagging breaches by data type and applicable regulations. These platforms enable automated workflows for incident intake, triage, and impact assessment, ensuring that incidents are categorized accurately (e.g., PHI, California personal information, or both). Collaboration tools further streamline responses by synchronizing efforts across covered entities, business associates, and CCPA service providers. They also maintain a consolidated incident log and evidence repository, which is invaluable for inquiries from HHS and state regulators.
The benefits of these tools are evident. For example, Terry Grogan, CISO at Tower Health, shared that adopting Censinet RiskOps™ allowed three full-time employees to return to their primary roles, while the organization now performs more risk assessments with just two full-time employees. James Case, VP & CISO at Baptist Health, highlighted how the platform eliminated the need for spreadsheets and fostered collaboration with a larger network of hospitals. Matt Christensen, Sr. Director GRC at Intermountain Health, underscored the importance of using healthcare-specific tools:
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare."
Conclusion
Key Differences Between CCPA and HIPAA
CCPA and HIPAA take different approaches when it comes to breach response, which is particularly important for healthcare organizations in California to understand. Under HIPAA, a breach is assumed when there’s unauthorized access, acquisition, use, or disclosure of unsecured Protected Health Information (PHI) - unless a risk assessment shows a low probability of compromise. On the other hand, CCPA ties breaches to unauthorized access caused by insufficient security measures and applies to a broader range of personal information beyond just health data [2][3].
Notification timelines also vary. HIPAA requires organizations to notify affected parties within 60 days of discovering a breach. In contrast, California law insists on notification "in the most expedient time possible." Additionally, California law requires notifying the state Attorney General if a breach impacts over 500 residents - something not mandated by HIPAA [1][2][4][8].
Enforcement is another key area of difference. HIPAA penalties, as adjusted by HHS OCR, can start as low as $137 per violation for breaches where the organization lacked knowledge. Meanwhile, the CCPA imposes fines of up to $2,500 per unintentional violation and provides California residents with a private right of action for certain breaches - an option not available under HIPAA [2][3][10].
Understanding these distinctions is essential for shaping effective compliance strategies.
Compliance Best Practices
The unique requirements of HIPAA and CCPA highlight the importance of a well-thought-out and unified incident response plan. Healthcare organizations can take several steps to improve their breach response processes. For instance, encrypting PHI and other personal data - both at rest and in transit - can prevent many incidents from being classified as breaches, which can reduce the need for notifications.
Developing an integrated incident response plan with clear decision-making workflows ensures organizations can quickly determine whether HIPAA or CCPA applies and meet the shortest notification deadlines. Standardized notification templates are also crucial. These templates should include details about the incident, the types of data affected, relevant dates, protective measures taken, and guidance for those impacted.
Strengthening third-party risk management is another critical step. This includes using robust HIPAA business associate agreements and CCPA-compliant data processing terms, as well as requiring vendors to report incidents promptly. Tools like Censinet RiskOps™ can simplify these efforts by automating key tasks such as incident triage, evidence collection, and cross-organization collaboration. By streamlining these processes, healthcare organizations can reduce the manual workload and enhance their overall security and compliance posture.
FAQs
How can healthcare organizations stay compliant with both CCPA and HIPAA regulations?
To comply with both CCPA and HIPAA, healthcare organizations need a well-rounded strategy for managing data security and privacy. This involves using tools designed for the job, like Censinet RiskOps™, which can simplify third-party assessments and keep an eye on cybersecurity risks.
Some essential actions include encrypting sensitive information, enforcing strict access controls, and regularly training staff on privacy protocols. Keeping breach response plans current is equally important. Additionally, ongoing audits and thorough documentation are vital to meet the reporting requirements set by both regulations.
How does encryption impact breach notification requirements under CCPA and HIPAA?
Encryption plays a key role in deciding whether a data breach needs to be reported under CCPA and HIPAA. When sensitive information, like patient data or protected health information (PHI), is encrypted in a way that makes it unreadable or unusable, the incident might not be considered reportable.
Both regulations acknowledge encryption as an effective safeguard that can spare organizations from issuing breach notifications. However, this exemption only applies if the encryption meets specific standards, ensuring that unauthorized individuals cannot access the data. This underscores how critical it is to adopt strong encryption practices to minimize compliance risks and keep sensitive information secure.
What are the risks for organizations that don't follow CCPA and HIPAA breach response rules?
Failing to follow CCPA and HIPAA breach response rules can have serious consequences. Organizations could face substantial fines, including penalties of up to $7,500 per violation under HIPAA. On top of that, they may also deal with lawsuits from individuals whose personal data was compromised.
The fallout doesn’t stop at financial penalties. Non-compliance can tarnish an organization’s reputation, weaken patient trust, and invite more regulatory oversight. These issues can disrupt daily operations and strain long-term relationships with both patients and business partners.


