Cloud Vendor Risk Management for Healthcare: Security, Compliance, and Continuity
Post Summary
Healthcare organizations rely heavily on cloud vendors for managing sensitive patient data and critical systems. But this dependence introduces serious risks, including data breaches, compliance challenges, and operational disruptions. Here's what you need to know:
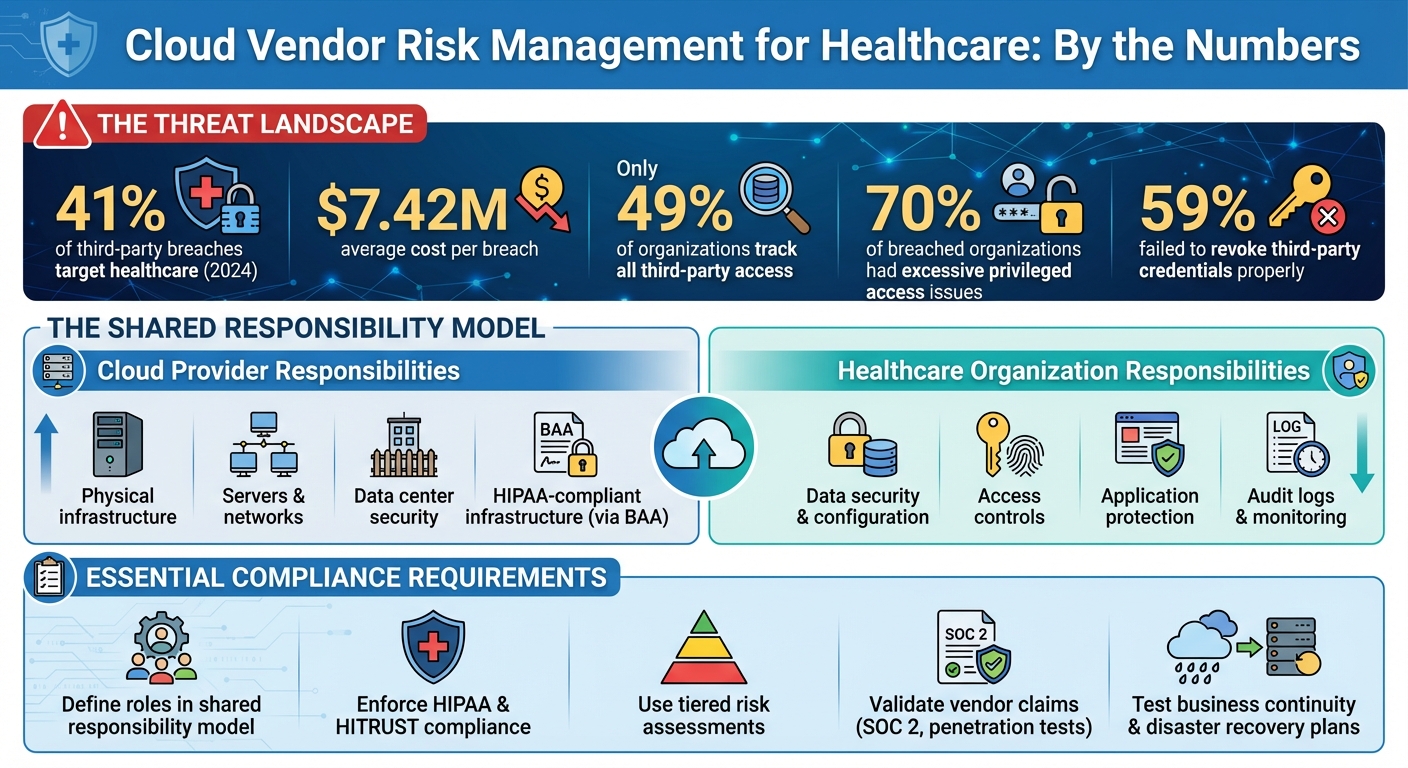
- Healthcare leads in third-party breaches: In 2024, 41% of such breaches targeted this sector, with an average cost of $7.42 million per breach.
- HIPAA compliance complexities: Cloud providers and healthcare organizations share security responsibilities, but unclear boundaries often lead to vulnerabilities.
- Vendor visibility issues: Only 49% of organizations track all third-party access, increasing security risks.
- Operational risks: Disruptions like the 2024 Change Healthcare ransomware attack highlight the need for robust continuity plans.
To manage these risks, healthcare organizations must:
- Clearly define roles in the shared responsibility model.
- Enforce HIPAA and HITRUST compliance with detailed agreements and certifications.
- Use tiered risk assessments and standardized security questionnaires.
- Validate vendor claims with evidence like SOC 2 reports and incident response plans.
- Develop and test business continuity and disaster recovery plans with vendors.
Tools like Censinet RiskOps can simplify vendor risk management by automating assessments, evidence reviews, and real-time monitoring. By prioritizing security, compliance, and continuity, healthcare organizations can protect patient data and maintain uninterrupted care.
Healthcare Cloud Vendor Risk Management: Key Statistics and Security Framework
The Shared Responsibility Model for Cloud Security
In cloud environments, providers sign a Business Associate Agreement (BAA) to guarantee HIPAA-compliant infrastructure. Meanwhile, healthcare organizations must secure their data by configuring systems correctly, implementing strict access controls, maintaining detailed logs, and protecting applications effectively[4].
Who Does What: Roles and Responsibilities
Cloud service providers (CSPs) handle the security of the underlying infrastructure - this includes physical hardware, servers, networks, and data centers that keep everything running. On the other hand, healthcare organizations are tasked with safeguarding the data and applications they host on this infrastructure. For instance, if a database is misconfigured and exposes patient records, the responsibility falls on the healthcare organization, not the cloud vendor.
The dynamic becomes more complicated when Managed Service Providers (MSPs) enter the picture. With multiple parties involved, there's a higher chance of missing critical security controls. To prevent this, organizations must clearly define and map out who is responsible for each control - whether it’s the CSP, MSP, or internal IT team[4]. Without this clarity, gaps in security can emerge. This layered responsibility underscores the importance of continuous risk management, a topic explored further in the following section. Unclear boundaries often lead to vulnerabilities, making it essential to define these roles explicitly.
What This Means for Healthcare Organizations
Clearly defining responsibilities is critical to identifying vulnerabilities. Surprisingly, only 49% of organizations maintain a complete inventory of all third parties with access to their networks, and just 45% know which third parties can access their most sensitive data[5]. This lack of visibility creates significant security risks.
"Cloud strategists must also ensure governance programs explicitly map who owns which controls (the CSP, MSP, or internal IT) and maintain continuous oversight through dashboards and audits."
The statistics reveal the risks: 70% of organizations that experienced third-party breaches cited excessive privileged access as a key factor, while 59% failed to revoke third-party access credentials when they should have[5]. These issues stem not from cloud vendors but from how healthcare organizations manage their responsibilities in the shared responsibility model. By explicitly defining each vendor’s role, organizations can avoid ambiguity and ensure no critical security measure is overlooked[4].
HIPAA and HITRUST Compliance for Cloud Vendors
When healthcare organizations choose cloud vendors, they form a legally binding partnership that directly impacts patient privacy and regulatory compliance. Any Cloud Service Provider (CSP) handling electronic Protected Health Information (ePHI) automatically becomes a Business Associate under HIPAA. This status means they are directly accountable for unauthorized uses or disclosures of PHI, failing to safeguard ePHI, or not reporting breaches[6].
It’s important to note that no cloud platform is inherently HIPAA compliant. As Schellman explains, "Large public clouds (like AWS and Azure) may support HIPAA compliance, but they cannot offer or guarantee it because compliance comes not from having a certain kind of technology or platform, but rather from configuring the platform in the appropriate ways"[3]. This puts the onus on healthcare organizations to ensure their vendors not only provide the necessary infrastructure but also configure and secure it properly.
HIPAA Security and Privacy Rules
The cornerstone of any relationship with a cloud vendor is the Business Associate Agreement (BAA). This agreement must clearly outline how the CSP will handle ePHI, including making it accessible when patients exercise their rights to access, amend, or request an accounting of disclosures[6]. Healthcare organizations must confirm that vendors follow through on implementing these safeguards.
Key safeguards include ensuring CSPs use file integrity monitoring to detect unauthorized alterations or destruction of ePHI, training employees on PHI cybersecurity best practices, and classifying data based on its sensitivity[2][3]. Risk analysis should also address vulnerabilities specific to the cloud environment, such as the risks of storing ePHI on servers located outside the United States[6].
Additionally, the Service Level Agreement (SLA) must align with both the BAA and HIPAA regulations. The SLA should cover critical areas like system availability, backup and recovery processes, the return of data after service termination, and limitations on the use, retention, and disclosure of information[6][2]. Discrepancies between these documents can create compliance gaps, which may lead to violations during audits.
While HIPAA compliance is the baseline, healthcare organizations can look for additional vendor assurances through industry-recognized certifications.
HITRUST Certification in Vendor Selection
Although HIPAA compliance is non-negotiable, HITRUST certification provides an added level of confidence, making vendor evaluation more straightforward. HITRUST consolidates various regulatory standards - including HIPAA, NIST, and ISO - into a unified certification process. A cloud vendor with HITRUST certification has demonstrated, through a rigorous third-party assessment, that their security controls and risk management practices meet high standards.
For healthcare organizations working with numerous vendors, HITRUST certification simplifies the due diligence process. Rather than conducting separate evaluations for each regulatory framework, organizations can rely on HITRUST’s comprehensive assessment. However, ongoing monitoring is still critical. It’s also essential to confirm that the HITRUST certification covers the specific services being used and remains up to date.
How to Assess Cloud Vendor Security Risks
For healthcare organizations juggling intricate vendor ecosystems, protecting sensitive patient data demands a structured approach to evaluating vendor risks.
Risk Assessment Frameworks
Not all vendors pose the same level of risk. For example, a cloud provider hosting your electronic health records system requires far more scrutiny than a vendor handling your marketing emails. Using a tiered risk classification system ensures you focus your efforts where it matters most. Vendors can be categorized based on the sensitivity of the data they manage, their role in patient care, and their potential impact on your organization.
Critical vendors - those essential to operations, patient care, or revenue - should undergo thorough security evaluations. This includes detailed questionnaires, on-site inspections, and ongoing monitoring. Medium-risk vendors might only need standardized questionnaires and occasional reviews, while low-risk vendors handling non-sensitive data can be assessed with simpler processes. This approach ensures you're dedicating the right amount of attention to higher-risk relationships while streamlining evaluations for less critical ones.
Using Standardized Security Questionnaires
Standardized security questionnaires are key to consistent and HIPAA-compliant vendor evaluations. Instead of reinventing the wheel with custom assessments, rely on established industry frameworks.
Your questionnaires should address the essentials: access controls (like user authentication and privileged access management), encryption practices (both in transit and at rest), incident response capabilities, employee security training, and subcontractor management. Be specific. For instance, ask, "Do you encrypt ePHI using AES-256 or equivalent?" instead of a vague, "Do you use encryption?" Clear, pointed questions lead to more actionable answers.
Collecting and Validating Vendor Evidence
Once you've categorized vendors and collected questionnaire responses, the next step is to confirm their claims with hard evidence. This is where validation becomes critical - it separates surface-level compliance from actual security practices. Request documentation like SOC 2 Type II reports, penetration testing results, vulnerability scan reports, and incident response plans. Always check the dates on these documents - a report from three years ago won't reflect their current security posture.
But don’t stop at collecting documents. Ask open-ended questions during follow-ups to dig deeper. For example, if a vendor claims they conduct quarterly penetration tests, ask about the findings from their most recent test and how they addressed any critical vulnerabilities. You can also request sample incident response timelines from past events to gauge their ability to detect and respond to threats quickly. These conversations often reveal whether a vendor is genuinely implementing the controls they claim or simply maintaining impressive paperwork.
sbb-itb-535baee
Ensuring Operational Continuity with Cloud Vendors
With cyber risks becoming more prevalent, maintaining operational continuity with cloud vendors is essential to ensure uninterrupted healthcare services. When a cloud vendor experiences a disruption, the ripple effects can jeopardize patient care almost immediately. A stark example of this was the 2024 Change Healthcare cyberattack. The BlackCat ransomware group forced the company to disconnect its systems, leading to widespread delays in patient authorizations and cash flow issues for providers. According to the American Hospital Association, this incident highlighted that attacks on third-party providers can have even more severe national consequences than direct attacks on hospitals or health systems [4][1]. These scenarios emphasize the importance of having a robust plan to maintain operational continuity.
Incident Response Planning
An effective incident response plan shouldn’t stop at your organization’s boundaries - it must include every cloud vendor managing critical operations. Start by embedding cybersecurity requirements into your Business Associate Agreements (BAAs) and contracts. These agreements should clearly define required security measures, outline consequences for non-compliance, and assign accountability for protecting data and reporting breaches [1]. Additionally, contracts should specify what triggers an incident, who needs to be notified, and the communication channels to be used.
Establishing and rehearsing communication protocols with vendors is equally important. For instance, ChristianaCare, which operates hospitals in Delaware and nearby states, actively monitors news for cyber incidents involving its suppliers. When a vendor is affected, they immediately reach out to assess whether their data is involved [5]. This proactive approach - combining detailed contracts, regular assessments, and rehearsed response plans - ensures teams are prepared when a security incident occurs. Clearly defining cybersecurity roles for both internal teams and vendors further reduces confusion during a crisis [1].
While immediate incident response is critical, long-term operational resilience depends on thorough continuity and recovery strategies.
Business Continuity and Disaster Recovery
Work closely with your vendors to create Business Continuity and Disaster Recovery (BCDR) plans that include automated failover systems, geographically diverse backups, and recovery protocols tailored to your Recovery Point Objectives (RPO) and Recovery Time Objectives (RTO) [4]. These plans should address not just data breaches but also broader issues like system outages and challenges accessing electronic health records (EHRs) [5].
However, having plans isn’t enough - they need to be tested. Many organizations fall short by failing to regularly test recovery procedures. Conducting routine disaster recovery drills, including vendors in these exercises, ensures operational resilience when it matters most [4]. Service Level Agreements (SLAs) should include clear performance metrics, penalties for non-compliance, and escalation procedures with strict deadlines to prevent prolonged disruptions [7]. For any risks identified with a vendor, maintain a Plan of Action and Milestones (POA&M) to track progress and ensure issues are addressed without delay [1].
Using Censinet RiskOps for Cloud Vendor Management

Managing cloud vendor risks can be a daunting task, often bogged down by inefficiencies like endless email chains and manual document reviews. Censinet RiskOps tackles these challenges by offering a centralized platform that simplifies the process of assessing, monitoring, and managing third-party risks. By automating key workflows, it removes the hassle of traditional methods and provides real-time insights into potential risks.
Automated Risk Assessments with Censinet Connect
Censinet Connect takes the headache out of vendor risk assessments by automating the entire process. Forget about chasing vendors through email or creating custom questionnaires - this tool provides pre-built, healthcare-specific security questionnaires that vendors can complete directly on the platform. This streamlined approach not only speeds up onboarding but also ensures evaluations are consistent across the board.
Censinet AITM for Evidence Review
Reviewing vendor evidence can be a tedious and time-consuming task, but Censinet AITM changes the game. Powered by artificial intelligence, it quickly summarizes vendor documentation, highlights key integration details, flags potential fourth-party risks, and generates detailed risk reports. While the AI takes care of the heavy lifting, human oversight ensures the final insights are accurate and actionable. It’s a smart way to save time without sacrificing thoroughness.
Command Center for Risk Visualization
The Command Center acts as a hub for risk teams, offering a real-time, bird’s-eye view of vendor risk data. By pulling together information from assessments and evidence reviews, it makes it easy to identify vendors that might need extra scrutiny. This unified dashboard is especially helpful for teams juggling multiple cloud vendors, ensuring no critical risks slip through the cracks.
Conclusion
Keeping cloud vendor risks in check requires constant attention to security, compliance, and operational stability. For healthcare organizations, the stakes are especially high. With frequent breaches, a web of vendor relationships, and significant financial risks on the line, the pressure to act decisively is immense.
To tackle these challenges, healthcare organizations need to take proactive steps. The shared responsibility model means staying on top of vendor security practices, ensuring compliance with HIPAA and HITRUST, and having flexible incident response plans ready to go. Simply relying on annual assessments isn’t enough anymore - security landscapes shift, and threats emerge daily [8]. Advanced tools now make it easier to handle what used to be a tedious process.
Censinet RiskOps offers a solution by automating risk assessments, speeding up evidence reviews with AI, and providing real-time insights through a centralized dashboard. This shifts vendor risk management from a slow, manual effort to a forward-thinking, efficient system that matches the fast-paced demands of the healthcare sector.
Strong vendor risk management doesn’t just protect patient data - it ensures uninterrupted care and safeguards your organization’s reputation. By embedding security into every stage of vendor relationships, from initial contracts to ongoing monitoring, you can build resilience against the ever-present threats targeting healthcare’s critical systems and sensitive data. Leveraging modern strategies and tools, healthcare organizations can protect patient safety while keeping operations running smoothly.
FAQs
What steps can healthcare organizations take to manage cloud vendor responsibilities effectively?
Healthcare organizations can stay on top of cloud vendor responsibilities by clearly defining security roles and obligations in their vendor agreements. This way, both parties are on the same page when it comes to the shared responsibility model.
It's also important to regularly review vendor security practices to ensure they meet healthcare compliance requirements like HIPAA and SOC 2. Setting up a system for audits or assessments can help confirm that these standards are being followed.
Finally, keeping open lines of communication with vendors is crucial. This allows for quick action in addressing risks, managing incidents, and implementing fixes. A proactive approach like this not only protects sensitive patient information but also helps maintain seamless care delivery.
What should a Business Associate Agreement include to comply with HIPAA regulations?
A HIPAA-compliant Business Associate Agreement (BAA) is designed to clearly define how protected health information (PHI) will be handled and secured. Here are the key components that should be included:
- Scope of data use and handling: Clearly outline the types of PHI covered and the specific ways it can be used or disclosed.
- Security requirements: Specify technical and administrative safeguards, such as encryption, access controls, and other measures to protect PHI.
- Breach notification procedures: Establish a timeline and process for reporting breaches, ensuring timely communication in case of a security incident.
- Compliance obligations: Require adherence to HIPAA and HITECH standards, ensuring both parties meet their regulatory responsibilities.
- Roles and responsibilities: Define the duties of each party to avoid confusion and ensure accountability.
- Audit rights: Grant the ability to conduct periodic reviews to confirm compliance with the agreement.
- Data return or destruction: Include instructions for securely returning or destroying PHI when the contract ends to prevent unauthorized access.
- Contingency planning: Address how service disruptions will be managed to maintain operations and protect patient data.
By including these elements, the agreement ensures both parties fulfill their legal responsibilities while safeguarding sensitive health information.
What are the benefits of HITRUST certification when assessing cloud vendors in healthcare?
HITRUST certification offers healthcare organizations a structured framework for evaluating the security measures of cloud vendors. It aligns with key compliance standards like HIPAA, playing a critical role in protecting sensitive patient information.
With HITRUST, organizations can pinpoint and address potential risks more efficiently, close gaps in vendor security assessments, and simplify the continuous monitoring of cloud providers' safeguards. This certification not only ensures vendors uphold stringent data protection standards but also helps maintain smooth operations and reinforces patient confidence.


