CMS Compliance and Vendor Risk: Medicare Requirements for Healthcare Organizations
Post Summary
Managing Medicare compliance is a high-stakes challenge for healthcare organizations. Here's why: CMS regulations hold providers accountable not just for their own operations but also for the actions of their vendors. From billing errors to data breaches, any misstep by third-party contractors can result in denied claims, audits, fines, or even exclusion from Medicare programs.
To stay compliant, healthcare organizations must:
- Ensure vendors meet CMS standards, including compliance plans, regular audits, and training.
- Continuously monitor vendors for risks like billing errors, PHI breaches, and exclusion list violations.
- Use robust contracts to define vendor responsibilities, especially for FDRs (First Tier, Downstream, and Related Entities).
- Leverage technology for centralized risk management, automation, and real-time monitoring.
CMS compliance isn't just about meeting regulations - it's about protecting your organization's financial health and reputation. This article breaks down how to navigate vendor risks and build a compliance program that works.
CMS Medicare Requirements for Vendor Relationships
Managing vendor risk is a key part of staying compliant with CMS regulations, especially for organizations participating in Medicare programs. CMS outlines specific rules for handling vendor relationships, particularly those involving First Tier, Downstream, and Related Entities (FDRs). These requirements, detailed in Title 42, apply to Medicare, Medicare Advantage (Part C), and Prescription Drug Benefit (Part D) programs [1]. Meeting these obligations is crucial for maintaining eligibility in these programs and avoiding compliance risks. Let's explore these requirements in the areas of compliance, data integrity, and emergency preparedness.
CMS Requirements for Vendors and FDRs
Healthcare organizations are required to ensure that all FDRs meet the same compliance standards that apply to the organization itself. Vendors involved in Medicare-related operations must implement documented compliance plans, which should include codes of conduct, training programs, conflict-of-interest protocols, policies, and regular audits [2]. Additionally, the OIG Exclusions Program prohibits organizations from working with individuals or entities listed on state or federal exclusion lists, such as the OIG's List of Excluded Individuals and Entities (LEIE) [2]. If a vendor or individual is excluded, no federal healthcare funds can be used for services provided by or through that party [2].
Unlike initial onboarding, vendor management requires continuous monitoring to ensure compliance. This includes verifying exclusion statuses and maintaining audit readiness. Under the legal principle of Respondeat Superior, any actions or mistakes by a vendor reflect directly on the healthcare organization [2].
"A healthcare organization is ultimately responsible for the actions, inactions, bad actors, and billings submitted by or through its vendors or the vendor's employees. This is due to a legal doctrine called Respondeat Superior (the healthcare organization chose to contract with and involve a vendor as a part of its services and is responsible for vetting and monitoring the vendor's actions)."
Data Accuracy and Reporting Standards
Accurate data handling is a growing focus for CMS, especially as reporting standards tighten for 2025. Precision in data submissions is becoming a key measure of healthcare quality [6]. Vendors involved in areas like claims processing, risk adjustment, or quality reporting must meet stringent accuracy requirements. Errors in these areas can lead to non-compliance, financial penalties, or loss of performance incentives [6].
For Medicare Set-Asides (MSAs), Section 111 reporting is mandatory for settlements involving Medicare beneficiaries [6]. Healthcare organizations must ensure their vendors meet these high data integrity standards, particularly when managing billing operations, electronic health records, or quality measure reporting. Mistakes in coding or data submissions by vendors can result in denied claims, audits, and other financial consequences for the contracting organization.
Emergency Preparedness and Business Continuity Requirements
CMS also mandates strict emergency preparedness standards for healthcare organizations and their vendors. These standards, outlined in the Conditions of Participation and Conditions for Coverage within Title 42 of the Code of Federal Regulations, require organizations to coordinate effectively during emergencies or disasters [1]. Vendors must demonstrate robust disaster recovery plans, clear incident response strategies, and reliable business continuity measures to maintain access to critical systems and Protected Health Information (PHI) during crises [2].
Vendor contracts should include provisions for emergency data backups, alternative communication methods, and recovery time objectives. This is especially important for vendors managing IT systems, patient data, or supply chains, as disruptions in these areas can directly impact patient care and Medicare compliance obligations.
Vendor Risk Areas for Medicare Compliance
To meet Medicare compliance standards, healthcare organizations must address key vendor risk areas beyond the basic requirements set by CMS. These risks fall into three primary categories: PHI security and privacy, billing and revenue cycle operations, and clinical services, which also include medical devices and supply chains. Each category comes with specific compliance challenges and potential repercussions for falling short.
PHI Security and Privacy Risks
Vendors managing Protected Health Information (PHI) must adhere to HIPAA and the HITECH Act, which form the backbone of CMS's security expectations for Medicare programs. CMS enforces minimum security and privacy measures through its Acceptable Risk Safeguards (ARS), which are based on NIST SP 800-53 standards [4]. Data breaches in this area can lead to regulatory penalties, financial losses, and damage to an organization's reputation.
To mitigate these risks, healthcare organizations should ensure vendors:
- Use HIPAA-compliant and SOC 2–certified software.
- Implement secure data storage and access protocols.
- Provide thorough training on privacy and security procedures.
Ongoing oversight is essential to ensure vendors consistently meet CMS standards for security and privacy.
Billing and Revenue Cycle Vendor Risks
Billing vendors pose significant compliance challenges, as errors can result in denied claims, overpayments, and regulatory scrutiny. These vendors must ensure accurate coding, proper documentation, and adherence to medical necessity guidelines. For example, an OIG audit conducted in October 2025 on the VNA Care Network found billing errors in 15% of claims, leading to $6,171 in overpayments due to unsupported codes and non-compliant services [8].
Additionally, vendors must help organizations avoid violations of the False Claims Act, Anti-Kickback Statute, and Stark Law. To minimize risks:
- Conduct regular audits of vendor billing workflows.
- Provide continuous staff training on current coding systems (e.g., ICD-10, CPT, HCPCS).
- Monitor for fraud, waste, and abuse in billing practices.
Clinical, Medical Device, and Supply Chain Vendor Risks
Clinical vendors are responsible for ensuring their services align with CMS requirements for care coordination, documentation accuracy, and medical necessity. This is particularly critical for specialized programs like Chronic Care Management (CCM) and Advanced Primary Care Management (APCM), where detailed documentation of care coordination and up-to-date care plans are mandatory. A 2023 OIG report on Medicare Remote Patient Monitoring (RPM) highlighted gaps in compliance, revealing that 43% of patients did not receive all required service components, and 44% of Medicare records lacked ordering provider details [11]. Such lapses can jeopardize compliance and reimbursement.
Medical device and supply chain vendors also play a crucial role in maintaining care quality. They are expected to track performance data and implement corrective actions as part of an organization's quality management plan [7]. To manage risks effectively:
- Screen all vendor employees against the OIG's List of Excluded Individuals and Entities (LEIE).
- Require annual training on fraud, waste, and abuse [9].
How to Build a CMS-Compliant Vendor Risk Management Program
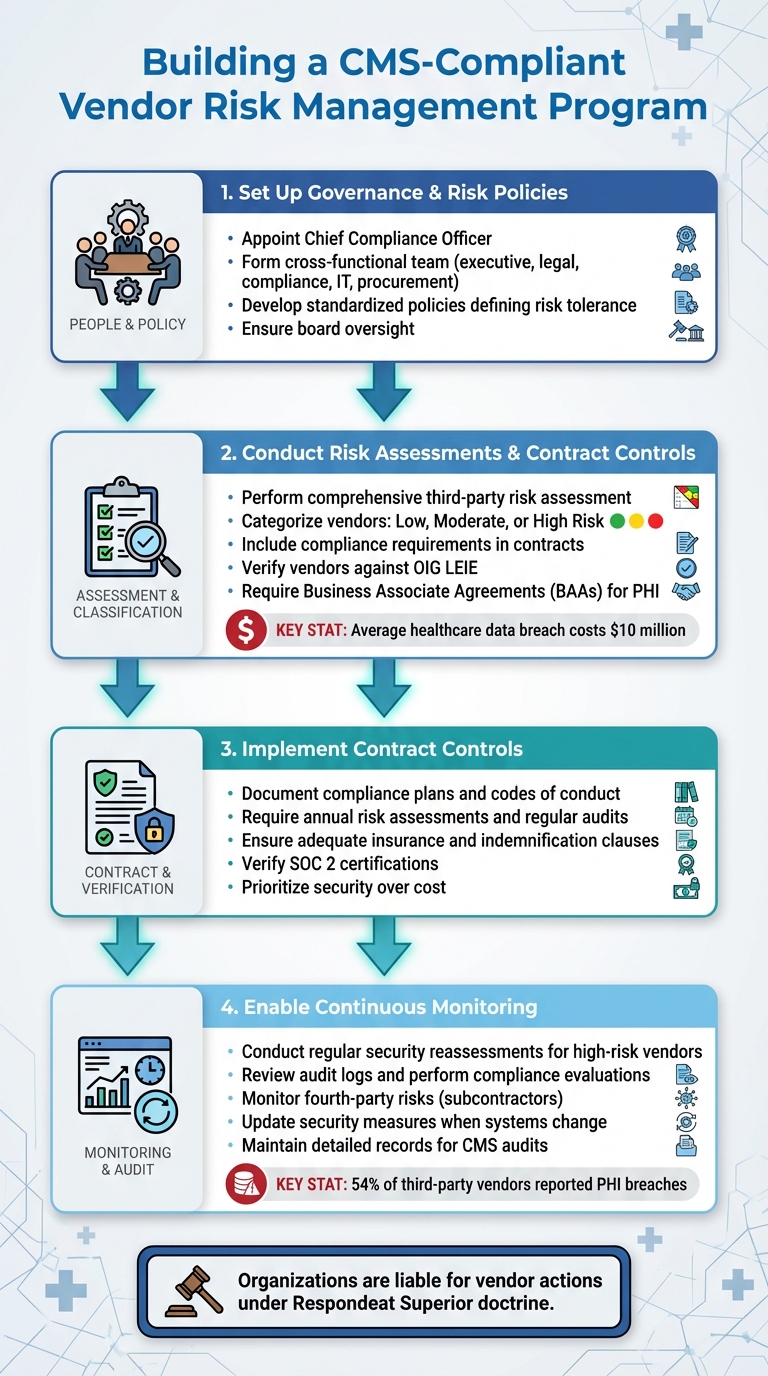
4-Step Framework for Building a CMS-Compliant Vendor Risk Management Program
Creating a CMS-compliant vendor risk management program calls for structured governance, thorough assessments, and consistent oversight. With vendor-related breaches on the rise and more than half of third-party vendors reporting PHI breaches [12][14], it's essential to establish a clear framework from the beginning. Here's a breakdown of the key steps to build an effective program.
Setting Up Governance and Risk Policies
The first step is to assign clear responsibilities for vendor risk management. A chief compliance officer should be appointed to enforce policies, provide staff training, evaluate risks, and report directly to the board [3]. Supporting this role with a cross-functional team - including members from executive leadership, legal, compliance, IT, and procurement - ensures that vendor risk management receives the attention it needs [12].
Next, develop standardized policies that define your organization's risk tolerance, evaluation criteria, and scoring requirements in line with CMS standards. These policies should be easily accessible and detailed enough to guide consistent decision-making for all vendor relationships [12][13]. Board oversight is crucial to ensure compliance becomes a core part of every vendor interaction, rather than an afterthought.
Risk Assessments and Contract Controls
Once governance is in place, focus on assessing risks and setting up contract controls. Start with a comprehensive third-party risk assessment across your organization to pinpoint vendor-related risks in areas like claims processing, IT, and patient services [12]. Evaluate each vendor individually, categorizing them as low, moderate, or high risk based on factors like PHI exposure, system integration, financial impact, and potential operational disruptions [12].
Contracts should include specific compliance requirements to protect your organization. These requirements might involve documented compliance plans, codes of conduct, training programs, and policies that align with CMS standards [2]. To mitigate risks, include clauses for annual risk assessments, regular audits, adequate insurance, and indemnification. If vendors handle PHI, ensure you have up-to-date Business Associate Agreements (BAAs) that clearly define their responsibilities [12]. Additionally, verify that vendors aren’t listed on the OIG’s List of Excluded Individuals and Entities (LEIE), as federal healthcare funds cannot be used for services from excluded parties [2].
When selecting vendors, prioritize security over cost. Given that the average healthcare data breach costs nearly $10 million [12], investing in vendors with strong compliance frameworks is a sound financial decision. Look for tangible proof of compliance, such as SOC 2 certifications, documented disaster recovery plans, incident response protocols, and audit logs, rather than relying on verbal assurances [12][2].
Continuous Monitoring and Audit Preparation
Ongoing monitoring is essential for high-risk vendors. Regularly conduct security reassessments, review audit logs, and perform compliance evaluations to catch potential issues early, such as errors in documentation, billing, or workflows [10][15]. Keeping detailed records of these activities is critical for demonstrating due diligence during CMS audits.
Don’t overlook fourth-party risks - those introduced by your vendors’ subcontractors. Include subcontractor-related questions in security reviews and require vendors to extend your compliance standards to their partners through contractual agreements [12]. Update security measures whenever there are changes to your practices or electronic systems, and use audit logs to track user activities in critical systems like EHRs [10]. By staying proactive, your organization can quickly address emerging risks and remain prepared for audits at all times.
sbb-itb-535baee
Using Technology for CMS and Vendor Risk Compliance
Handling CMS compliance and managing vendor risks manually has become nearly impossible - especially when 54% of third-party vendors in healthcare reported data breaches involving PHI over just two years [14]. To address this, healthcare organizations are turning to technology platforms that simplify the process of managing hundreds of vendor relationships while meeting Medicare requirements.
Centralized Vendor Risk Management Platforms
Digital platforms have revolutionized how organizations approach vendor risk assessments. Tools like Censinet RiskOps™ consolidate all vendor management tasks into one platform, eliminating the need for spreadsheets and scattered documentation. These systems centralize vendor inventories, automate compliance workflows, and align audit programs with established risk management frameworks [12]. Instead of hunting down certifications or contracts across various departments, risk managers can access everything - like Business Associate Agreements and SOC 2 reports - from one convenient location.
The key advantage is standardization. These platforms enforce consistent evaluation criteria, ensuring every vendor is assessed the same way [12]. This not only reduces bias but also speeds up the process and creates a reliable documentation trail - exactly what CMS auditors require. Additionally, these systems flag missing or outdated documents, such as expired insurance certificates, lapsed HiTRUST certifications, or outdated disaster recovery plans [14].
Automation and AI for Vendor Risk Management
Automation is transforming vendor risk assessments into quick and efficient processes. For example, Censinet AI™ can summarize vendor documentation, capture integration details, highlight fourth-party risks, and generate risk summary reports - all in seconds. This technology ensures oversight while significantly improving the speed and efficiency of evaluations.
Repetitive compliance tasks are another area where automation shines. Platforms can automatically screen vendors against the OIG's List of Excluded Individuals and Entities [2] or send alerts for expiring certifications and vulnerabilities [14]. Findings are routed to the appropriate reviewers through built-in workflows, allowing healthcare teams to address issues before they escalate into compliance violations. Real-time alerts and dashboards enhance this process, giving teams the tools to act quickly and effectively [14].
Real-Time Dashboards and Compliance Metrics
Modern risk management systems offer user-friendly dashboards that deliver real-time insights. Compliance officers can instantly see which vendors pose the highest risks, track overdue assessments, and identify documentation gaps. These dashboards also help monitor vendor progress, spot trends, and generate detailed audit reports [12].
This visibility is particularly useful for meeting specific CMS requirements. Organizations can ensure vendors comply with PHI safeguarding standards, maintain necessary insurance coverage, and adhere to emergency preparedness plans - all through a centralized platform. This digital oversight strengthens continuous monitoring efforts. When audits roll around, these platforms provide the detailed documentation needed to prove due diligence across all vendor relationships [14].
Conclusion
Key Lessons for Healthcare Organizations
Ensuring CMS compliance through vendor relationships isn't just a legal box to check - it's a critical safeguard for both finances and reputation. Healthcare organizations are held accountable for vendor missteps, whether it's billing errors, data breaches, or other compliance failures [2]. For instance, improper payments in 2024 reached alarming levels [5], and non-compliance can lead to denied claims, hefty fines, audits, or even exclusion from federal healthcare programs.
The doctrine of Respondeat Superior underscores this responsibility, making organizations liable for vendor misconduct. Whether it's a billing contractor submitting fraudulent claims or a technology partner mishandling protected health information (PHI), the repercussions fall squarely on the healthcare provider [2]. To mitigate these risks, organizations must adopt a structured approach: thorough vendor vetting, ongoing monitoring, strong contractual agreements, and diligent oversight. With increased penalties for working with excluded vendors [2], proactive risk management isn't optional - it's essential.
Next Steps for Improving Vendor Compliance
To strengthen your vendor compliance framework, consider these actionable steps:
- Build a solid governance foundation by appointing a compliance officer and forming an oversight committee.
- Develop clear policies that align with HIPAA, HITECH, and CMS regulations, and ensure vendors implement their own compliance programs [5].
- Screen all vendors against the OIG's exclusion list and require certifications like HiTRUST and SOC 2 to confirm their credentials [2].
Leveraging technology can make these tasks more manageable. Platforms like Censinet RiskOps™ simplify compliance by centralizing vendor data, automating workflows, and providing real-time dashboards to track risks and documentation gaps. These tools eliminate the need for manual spreadsheets and ensure audit-ready records that meet CMS standards. Additionally, Censinet AI™ speeds up the process by summarizing vendor documentation, integrating details, and generating risk reports almost instantly - enabling efficient oversight without compromising on thoroughness.
"Compliance isn't just a regulatory requirement; it's a reflection of your practice's commitment to ethical, patient-centered care." - Jon-Michial Carter, ChartSpan [5]
Regular training, internal audits, and consistent policy enforcement are equally vital. By combining strong governance with advanced technology, healthcare organizations can effectively manage vendor risks while safeguarding the integrity of Medicare programs.
FAQs
What CMS compliance requirements must healthcare vendors follow?
Healthcare vendors collaborating with Medicare are required to meet CMS standards as defined by the Social Security Act. These standards encompass certification, safety protocols, and quality measures. To ensure compliance, vendors undergo audits and surveys aimed at verifying adherence to federal regulations.
Key rules, such as those outlined in 42 CFR Part 422 Subpart V, specifically address areas like Medicare Advantage communications and marketing practices. Additionally, vendors must prioritize patient safety, safeguard data, and uphold operational integrity to remain in compliance.
What steps can healthcare organizations take to ensure vendors comply with Medicare requirements?
Healthcare organizations can stay on top of Medicare requirements by setting up a strong system to monitor vendor compliance. This involves performing regular audits, carefully reviewing vendor-provided documentation, and ensuring vendors follow CMS and HHS regulations. It’s also essential to screen vendors against exclusion lists like the OIG List of Excluded Individuals/Entities (LEIE) to avoid working with entities that aren’t eligible.
Another key step is verifying that vendors adhere to cybersecurity and data privacy standards, such as holding SOC or HITRUST certifications. Regular risk assessments play a big role in spotting potential weak points. Using automated compliance tools can make this process easier by tracking vendor performance, confirming credentials, and quickly addressing any compliance issues. These steps not only help maintain Medicare compliance but also reduce risks tied to third-party partnerships.
How does technology help healthcare organizations manage CMS compliance and vendor risks?
Technology plays a crucial role in handling CMS compliance and managing vendor risks within the healthcare sector. It allows for real-time tracking, streamlines risk assessments, and ensures the secure management of sensitive information. By incorporating advanced tools, healthcare organizations can monitor compliance continuously and tackle vulnerabilities head-on.
Here’s how technology makes a difference:
- Automating risk assessments and compliance audits: Saves time and reduces human error.
- Implementing robust security measures: Features like multi-factor authentication enhance data protection.
- Keeping detailed audit logs: Essential for monitoring third-party vendor activities.
These technological solutions not only simplify adherence to Medicare regulations but also reduce risks tied to external vendors, creating a safer and more efficient healthcare system.


