How Compliance Training Prevents Data Breaches
Post Summary
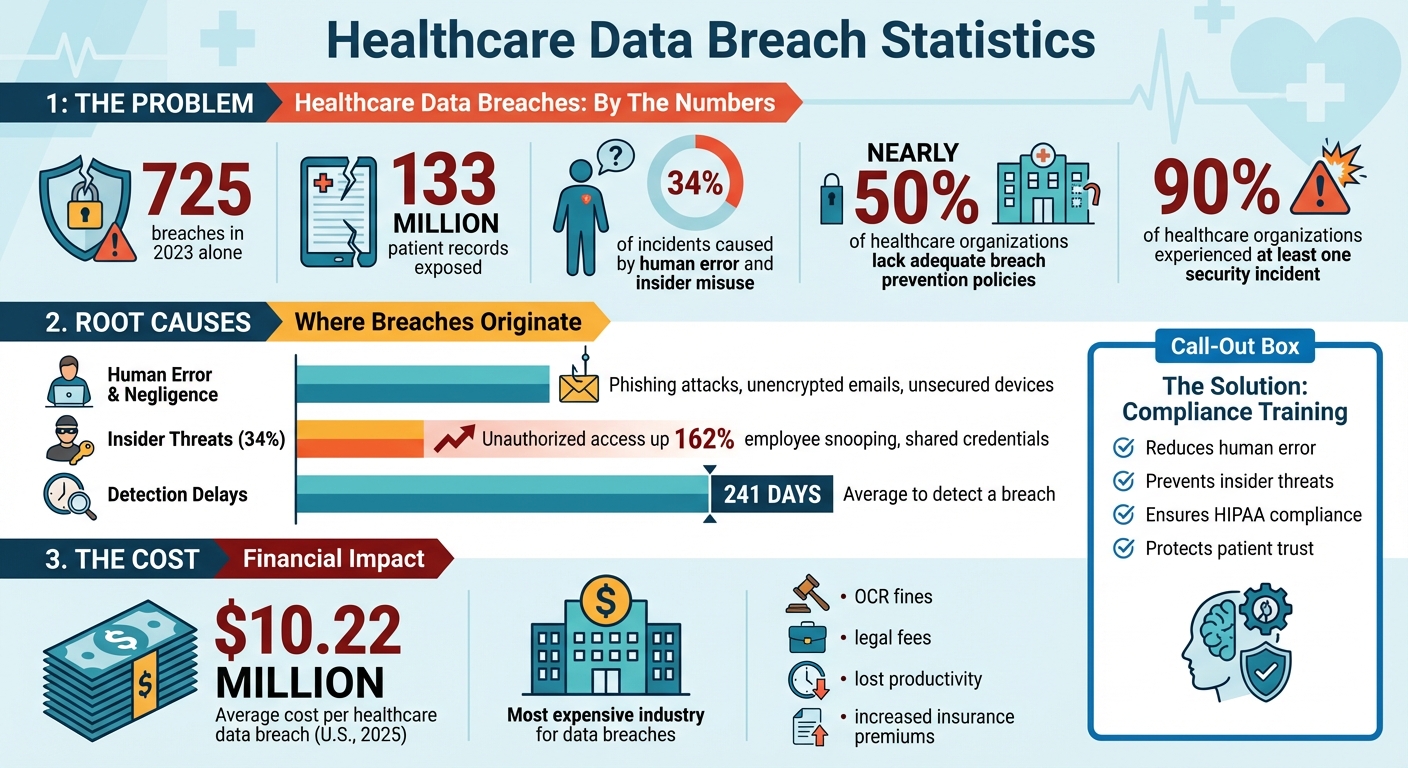
Data breaches in healthcare are skyrocketing. In 2023 alone, 725 breaches exposed over 133 million patient records, with human error and insider misuse driving 34% of incidents. Despite these risks, nearly half of healthcare organizations lack the policies, technology, and expertise to prevent breaches.
The solution? Compliance training. It equips staff with the skills to handle sensitive data securely, recognize phishing attempts, and follow HIPAA rules. By focusing on role-specific scenarios - like avoiding snooping or encrypting emails - training reduces risks and proves regulatory compliance.
Key takeaways:
- Human error is a major cause of breaches (e.g., phishing, mishandling data).
- Insider threats are rising, with unauthorized access up 162%.
- Compliance training simplifies HIPAA rules into actionable steps tailored to each role.
- Tools like Censinet RiskOps™ help target training to high-risk areas.
Investing in ongoing, role-based training not only reduces breaches but also protects patient trust and avoids costly penalties.
Healthcare Data Breach Statistics and Human Error Impact 2023-2025
Common Causes of Healthcare Data Breaches
Human Error and Negligence
Every day, healthcare professionals handle a massive amount of sensitive patient data, making even small mistakes a big deal. Phishing and social engineering attacks often target busy staff, tricking them into clicking on malicious links or sharing login details [2]. Simple errors, like sending emails without encryption, leaving devices unattended, or improperly disposing of patient records, can expose critical information [2][13]. Even something as basic as forgetting to log out of a secure system can create opportunities for unauthorized access [2]. These seemingly minor lapses not only result from human error but also open the door for insiders to misuse data.
Unauthorized Access and Insider Threats
Insider activity accounts for over 34% of healthcare data breaches, making it a significant concern [11]. One common issue is "snooping", where employees access patient records they have no business viewing [2]. Shared login credentials at communal workstations are another problem, as they blur accountability and make it tough to track individual actions [2]. Alarmingly, incidents of unauthorized access and disclosure have risen by 162% in recent years, pointing to gaps in access control measures [9]. Insider threats come in two forms: intentional misuse, like fraud, and unintentional mistakes, often due to a lack of understanding about access restrictions [2]. Without strong role-based access controls, detailed logging, and clear training on data access protocols, these risks will only grow [2].
Regulatory and Financial Consequences
When breaches happen, the fallout goes far beyond internal missteps. The Office for Civil Rights (OCR) may step in, requiring corrective action plans, stricter training, and even issuing hefty fines [5]. The financial toll doesn’t stop there - incident response costs, legal fees, and lost productivity add up quickly [5]. Healthcare remains the most expensive industry for data breaches, with costs per incident far exceeding other sectors [14]. Organizations also face rising cyber insurance premiums and often have to redirect funds from patient care to fix security issues [2]. On top of that, breaches can tarnish a provider’s reputation, leading to bad press, patient complaints, and a loss of trust. Patients may start to doubt whether their healthcare providers can keep their personal information safe. Restoring that trust requires open communication and a clear commitment to improving security [3].
Compliance Training as a Regulatory Requirement
HIPAA Training Requirements
Under HIPAA, training isn’t optional - it’s a requirement. Covered entities and business associates must ensure their workforce is trained on the Privacy and Security Rules, tailoring the content to specific roles. For example, the training needs of a billing clerk differ significantly from those of a physician or an IT administrator. The Security Rule emphasizes "security awareness and training" as a key administrative safeguard, while the Breach Notification Rule requires staff to recognize potential breaches, assess risks, and report incidents without delay. On top of HIPAA, additional state and federal laws impose even stricter training requirements.
State and Federal Law Requirements
HIPAA sets the foundation, but states like California, Texas, and New York have introduced more stringent privacy, security, and breach-notification rules. These often feature faster notification deadlines and broader definitions of personal information [8]. For organizations providing substance use disorder (SUD) treatment, compliance with 42 CFR Part 2 is essential. This regulation mandates specialized training on maintaining confidentiality and obtaining proper consent for SUD records [10]. According to a peer-reviewed NIH analysis, 41.2 million healthcare records were exposed in 505 breaches during 2019 [10]. Addressing these overlapping regulations not only strengthens an organization’s security measures but also highlights the importance of comprehensive training that meets every applicable legal standard - not just HIPAA.
Documentation for Compliance Audits
Proper documentation is critical for proving compliance. Regulatory audits require clear and organized records showing that employees have been adequately trained. These records should include policies, attendance logs, assessments, and any remedial training efforts [4][6]. By May 31, 2025, the Office for Civil Rights (OCR) had closed nine investigations that resulted in financial penalties for entities failing to document sufficient risk analyses [8]. Maintaining these records in a centralized system with audit trails and retention schedules aligned with HIPAA and state requirements can help organizations quickly provide evidence of compliance. Regulators expect training to be ongoing, not just a one-time event. Periodic refreshers and updates following policy changes or breaches are essential, making thorough documentation just as important as the training itself [8][15].
Core Components of Effective Compliance Training Programs
Role-Based Training for Different Staff
Effective compliance training starts with tailoring the content to the specific roles within your organization. Each team interacts with patient data differently, so their training must reflect those unique responsibilities. For example:
- Clinicians need scenario-based training that emphasizes minimal data access, secure charting practices, authorized disclosures, and proper use of electronic health records (EHR). They should also be reminded not to share logins or leave workstations unlocked.
- IT and security teams require a more technical focus, covering topics like access control, logging, patching, encryption, backups, and incident response protocols aligned with the HIPAA Security Rule.
- Business office and front-desk staff should learn practical skills such as verifying patient identity, securely handling printed protected health information (PHI), managing record requests, and avoiding casual disclosures in public spaces.
- Executives and managers need training on governance, understanding regulatory risks, and fostering a security-first culture by enforcing policies and responding effectively to audits.
Real-world examples make training more impactful. For instance, a scenario could involve a nurse leaving a workstation unlocked, allowing unauthorized access to patient charts. Another might feature a billing clerk accidentally emailing unencrypted PHI or an IT admin misconfiguring remote access, leading to a security breach. Each case should highlight the violated policy, how the issue was detected, the regulatory and financial consequences, and the correct behavior to prevent such incidents. Studies show that about 24% of physicians fail to detect malware, and 50% are vulnerable to privacy breaches [9].
These role-specific scenarios naturally lead into broader training on recognizing external threats, such as phishing, to ensure comprehensive protection.
Phishing and Social Engineering Awareness
Phishing and social engineering attacks are among the most common threats to healthcare organizations. To combat these, staff need training to identify phishing attempts by spotting red flags like unusual sender addresses, urgent language, unexpected attachments or links, and fake login pages. They should also be taught to verify requests for sensitive information - such as credentials, wire transfers, or PHI - using alternative communication methods.
Training should go beyond email scams to include other forms of social engineering, such as:
- Voice phishing (vishing): Fraudulent phone calls designed to extract sensitive information.
- SMS phishing (smishing): Text messages that attempt to trick recipients into revealing data.
- Tech support scams: Fake IT support calls or messages.
- Physical social engineering: Tactics like tailgating or impersonating a vendor to gain unauthorized access.
Hands-on exercises, like phishing simulations and tabletop scenarios, can give staff practical experience. These activities allow employees to practice identifying threats and following proper escalation procedures, all in a controlled environment. Immediate feedback from these exercises reinforces the lessons and prepares staff to handle real-world attacks confidently.
Secure Data Handling and Disposal
Proper handling and disposal of data are essential to protecting patient information. Training should emphasize that PHI must only be transmitted through approved, encrypted channels, such as secure email, messaging platforms, or patient portals. Personal email accounts, consumer messaging apps, and unencrypted texts are strictly off-limits.
For employees using personal devices under a bring-your-own-device (BYOD) policy, training should outline enrollment requirements, security measures like screen locks and encryption, and restrictions against saving PHI to personal cloud storage. Staff must also understand when encryption is required - for example, for data at rest on mobile devices or data in transit via email or VPN - and learn how to verify that encrypted channels are in use.
When it comes to disposing of PHI, clear protocols are critical. Paper records should be shredded using locked bins designated for secure document disposal. For electronic media - like hard drives, USB drives, copier storage, or medical device memory - approved methods include secure wiping, degaussing (magnetic erasure), or physical destruction. These processes should be managed by IT or authorized vendors, with detailed logs kept for audit purposes.
Training should also address how to handle lost or stolen devices. Employees need to know the importance of immediate reporting so that measures like remote wiping or other containment actions can be taken without delay.
To stay ahead of emerging risks, organizations can use platforms like Censinet RiskOps™. These tools help update training content based on evolving risk assessments, third-party vendor vulnerabilities, and identified control gaps, ensuring that staff education remains aligned with current threats and compliance requirements.
sbb-itb-535baee
Implementing and Sustaining Compliance Training Programs
Training Frequency and Delivery Methods
To build a strong foundation for compliance, it's essential to have a structured training schedule. New employees - whether they're clinicians, administrative staff, or contractors - should complete comprehensive HIPAA privacy and security training as part of their onboarding process. This ensures they understand the importance of secure practices before accessing patient data systems.
While annual refresher training is a standard expectation during audits, it’s not enough to keep up with today’s rapidly evolving threats. These yearly sessions should cover HIPAA regulations, the latest cybersecurity risks, and internal policies. For high-risk roles, such as IT staff or employees handling large volumes of PHI, quarterly microlearning sessions are highly effective. These are short, focused modules (5 to 10 minutes) that address emerging threats, like new phishing techniques or ransomware attacks. These quick lessons can be delivered via email, integrated into EHR workflows, or through an LMS for easy access.
The way training is delivered is just as important as how often it occurs. E-learning modules are ideal for large organizations, offering consistent content across locations and accommodating shift-based schedules. For topics like breach response, live virtual or in-person sessions provide opportunities for staff to engage directly with compliance officers and discuss real-world scenarios. Hands-on approaches, such as simulated phishing campaigns, help employees practice identifying threats in a controlled environment. For 24/7 operations, recorded sessions, mobile-friendly modules, and flexible scheduling ensure that night, weekend, and per diem staff receive the same quality of training. By combining these methods, you can meet the needs of diverse learning styles and work schedules. Once this structure is in place, the next step is measuring its effectiveness.
Measuring Training Effectiveness
To know if your training is making a difference, you need to track the right metrics. Start with engagement metrics like completion rates, on-time participation, and quiz scores by department. These numbers show whether employees are engaging with and understanding the material.
For a deeper look at impact, focus on behavioral metrics. Monitor phishing simulation click rates and how often staff report suspicious emails. A drop in clicks and an increase in reports signal better awareness. Keep an eye on incidents caused by human error, such as improper EHR access, lost devices, or misdirected communications - areas where training can directly improve behavior. You should also measure how quickly employees report suspicious activity, as this reflects their readiness to escalate potential issues.
Finally, tie training to real-world outcomes with result metrics. Look for decreases in reportable breaches to HHS, improved audit results, and fewer corrective actions related to workforce compliance. Considering the average cost of a healthcare data breach in the U.S. hit $10.22 million in 2025[12], even small reductions in incidents can have a big financial impact. Present these findings to leadership quarterly using dashboards that highlight trends over 6 to 12 months. This helps identify departments that may need extra support and keeps everyone aligned on progress.
Integrating Training Into Risk Management Frameworks
To maximize its impact, compliance training should be part of your overall risk management strategy - not a standalone effort. Document how your training program addresses specific risks identified during HIPAA risk assessments. This is especially important since failures in risk analysis are now the most frequently cited Security Rule violations[8].
Tools like Censinet RiskOps™ make it easier to connect training with risk management. For instance, if assessments reveal that certain vendors or systems pose higher risks for phishing or credential compromises, you can create targeted training for employees who interact with those platforms. The system aggregates data on PHI handling, incident trends, and control effectiveness, allowing you to link training metrics - such as reduced phishing susceptibility or faster incident reporting - to specific risk categories like third-party access or misuse of clinical applications.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." - Terry Grogan, CISO, Tower Health[1]
Conclusion
Compliance training plays a critical role in preventing data breaches. Recent statistics reveal that 725 breaches exposed 133 million records [8], and nearly 90% of healthcare organizations experienced at least one security incident [11]. The primary culprits - human error, phishing attacks, unauthorized access, and improper handling of Protected Health Information (PHI) - can be mitigated through focused education. By translating HIPAA regulations into actionable, everyday practices, organizations can empower every team member to contribute to data security.
This type of targeted training doesn’t just address vulnerabilities - it reshapes organizational behavior. It goes beyond meeting regulatory requirements by fostering a culture where protecting patient data becomes second nature. When staff across all roles - clinicians, administrators, and vendors - can recognize phishing attempts, verify recipients before sharing PHI, and report suspicious activities promptly, the risk and impact of breaches decrease significantly. Considering that breaches take an average of 241 days to detect [7], even small improvements in behavior can lead to meaningful results.
For compliance training to be most effective, it should be part of a larger risk management strategy. Connecting training efforts to risk assessments, audit outcomes, and incident patterns creates a dynamic system that continuously improves both educational content and security measures. Tools like Censinet RiskOps™ enable healthcare organizations to link training metrics - such as phishing test results or policy violations - with broader risk data from vendors, clinical systems, and medical devices. This approach helps prioritize areas where additional training or enhanced controls are most needed, strengthening overall security and resilience.
At its core, protecting PHI is about protecting patients and maintaining trust. Organizations that commit to ongoing compliance training and integrate it with risk management strategies not only align with regulations but also safeguard their reputation and the confidence of their patients. The stakes are simply too high to ignore.
FAQs
How does compliance training help reduce mistakes in handling patient data?
Compliance training plays a key role in reducing errors related to handling patient information. By educating staff on proper procedures for managing sensitive data, it builds awareness of potential risks and reinforces effective practices. This ensures employees clearly understand their responsibilities in safeguarding patient privacy. Taking these steps helps prevent mistakes and bolsters the overall security of patient data.
What makes a role-based compliance training program effective?
An effective compliance training program tailored to roles within an organization zeroes in on the specific duties and challenges each position entails. It ensures employees fully grasp their responsibilities when it comes to safeguarding data and maintaining patient privacy.
Here are the key elements:
- Defined roles and responsibilities: Training is built around the unique challenges and risks tied to each role.
- Custom training materials: Content is designed to align with the tasks and duties of specific positions.
- Continuous education and updates: Regular sessions keep staff informed about changes in regulations and emerging threats.
- Periodic assessments: These help measure how well employees understand and follow compliance guidelines.
- Reinforcement strategies: Practical examples and reminders ensure compliance becomes part of everyday routines.
By focusing on the specific needs of each role, this approach equips healthcare teams to handle risks more effectively and protect sensitive information from breaches.
What are the best ways to measure the success of compliance training?
To measure how well compliance training is working, organizations can focus on a few key indicators: completion rates, test scores, and how well employees retain knowledge over time. A drop in data breaches and better adherence to established protocols are also clear signs that the training is hitting the mark.
Regularly performing risk assessments and collecting feedback from employees can uncover areas that need attention. Tools like Censinet RiskOps™ can make these assessments easier and offer useful insights into compliance and risk management strategies.


