The Connected Patient: Medical AI Cybersecurity in the IoT Era
Post Summary
Connected patient care refers to the integration of technology, such as IoT devices and medical AI, to enhance patient monitoring, diagnosis, and treatment.
IoT enables real-time data collection and device interconnectivity, improving patient outcomes and operational efficiency in healthcare.
Medical AI supports diagnostics, predictive analytics, and personalized treatment plans, enhancing decision-making and patient care.
Cybersecurity protects sensitive patient data and ensures the integrity of connected medical devices, reducing risks of breaches and cyberattacks.
Challenges include data privacy concerns, interoperability issues, and the need for robust cybersecurity measures.
Organizations can adopt advanced risk management frameworks, implement encryption, and ensure compliance with healthcare regulations.
The rise of connected healthcare - powered by AI and IoT devices - has transformed patient care into a 24/7, data-driven model. While this shift enables continuous monitoring, early detection of health issues, and tailored treatments, it also exposes healthcare systems to cyber threats. Breaches in connected devices or AI systems can compromise patient safety, disrupt operations, and lead to severe financial and regulatory consequences.
Key points:
- Connected Devices: Wearables, smart monitors, and AI tools now enable real-time health tracking and decision-making.
- Cyber Risks: Vulnerabilities in IoT devices and AI systems can lead to ransomware attacks, data theft, or compromised patient care.
- Regulations: U.S. laws like HIPAA and FDA's cybersecurity requirements mandate strict safeguards for patient data and devices.
- Security Measures: Zero Trust architecture, network segmentation, encryption, and AI governance are critical to securing healthcare systems.
- Continuous Defense: Monitoring, risk prioritization, and rapid incident response are essential to protect patient data and maintain care delivery.
The challenge lies in balancing the benefits of connected healthcare with the need for strong, proactive cybersecurity measures to safeguard both patient lives and sensitive information.
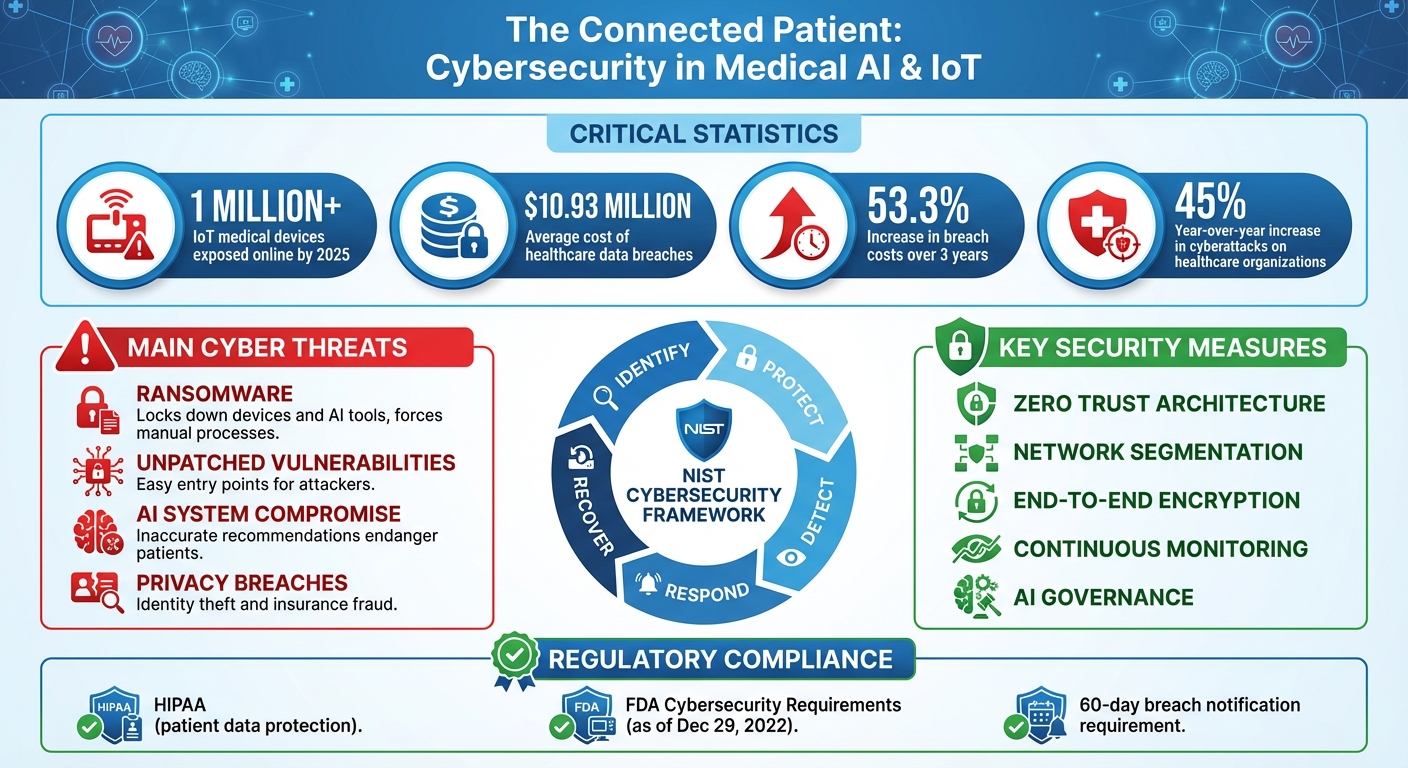
Medical AI and IoT Cybersecurity Threats: Key Statistics and Impact
Cyber Threats Facing AI-Enabled IoT in Healthcare
How AI and IoT Are Used in Healthcare
Across the U.S., healthcare providers are embracing AI and IoT technologies to enhance patient care and streamline their operations. Remote monitoring systems now track vital signs and deliver real-time data directly to providers, helping them respond faster to patient needs. AI-powered diagnostic tools analyze everything from medical imaging to lab results and patient histories, enabling earlier and more precise disease detection. Meanwhile, smart medical devices like insulin pumps, pacemakers, and ventilators adjust treatments on the fly based on real-time patient data.
These advancements offer clear clinical benefits, yet they come with significant security risks. Many devices are designed with a focus on functionality, often neglecting robust cybersecurity measures. This lack of attention to security - combined with outdated systems and inconsistent updates - leaves devices vulnerable to attacks. The rapid digitization of healthcare has also expanded the attack surface, creating numerous entry points for cybercriminals far beyond traditional hospital IT systems [8][7]. These vulnerabilities set the stage for the cyber threats explored in the next section.
Main Cyber Threats to Connected Patients
Ransomware is one of the most disruptive threats to healthcare organizations today. Health records are highly valuable on the black market, and the critical nature of healthcare services increases the likelihood of ransom payments. When ransomware infiltrates hospital networks, it can lock down connected medical devices and AI diagnostic tools, forcing staff to rely on slower, manual processes. Unpatched vulnerabilities in devices provide attackers with easy entry points, enabling them to manipulate treatment settings or steal sensitive patient data.
AI systems, which play a growing role in clinical decision-making, are also at risk. If compromised, these systems could deliver inaccurate recommendations, endangering patient care. Privacy breaches in connected healthcare environments expose personal information, leaving patients vulnerable to identity theft, insurance fraud, and other crimes. Beyond the immediate data loss, these breaches create operational headaches that ripple through the organization, as discussed next.
How Cyber Attacks Affect Healthcare Operations
The impact of cyberattacks on AI-enabled IoT systems extends well beyond stolen data. These attacks can delay critical procedures, disrupt access to essential patient information, and even force system shutdowns, jeopardizing the real-time monitoring patients rely on for their safety.
Financially, healthcare organizations face steep costs from ransom payments, system recovery efforts, and potential fines for violating regulations like HIPAA. The interconnected nature of AI and IoT systems means that a single breach can cascade across multiple platforms, amplifying the damage and prolonging recovery times. These operational disruptions highlight the urgent need for stronger security measures in healthcare technology.
Creating a Cybersecurity Framework for Medical AI and IoMT
When it comes to protecting medical AI systems and Internet of Medical Things (IoMT) devices, simply installing software isn’t enough. Healthcare organizations need a well-structured cybersecurity framework. This framework should not only address regulatory compliance but also establish clear governance and manage the growing web of external partners involved with AI and IoT technologies. These foundational elements are essential for implementing strong operational controls.
Meeting U.S. Regulations and Standards
Cybersecurity programs in healthcare must align with a variety of U.S. regulations. At the core of these is HIPAA, which focuses on safeguarding patient data. However, the regulatory landscape has expanded. For example, as of December 29, 2022, the FDA requires all premarket submissions for cyber devices to include robust cybersecurity plans [6][12].
The NIST Cybersecurity Framework provides a practical blueprint for healthcare organizations to structure their security measures. It revolves around five key functions: Identify, Protect, Detect, Respond, and Recover. This framework not only helps organizations communicate a common cybersecurity approach across departments and external partners but also demonstrates compliance while fostering resilience in connected systems.
Setting Up AI Risk Governance
AI systems demand a level of governance that goes beyond traditional IT oversight. The Health Sector Coordinating Council (HSCC) has identified five critical areas for guiding AI cybersecurity efforts: Education and Enablement, Cyber Operations and Defense, Governance, Secure-by-Design Principles, and Third-Party Risk and Supply Chain Transparency [9]. These focus areas provide a roadmap for building strong AI governance structures.
Healthcare organizations should establish an AI governance committee that includes experts in clinical care, IT security, legal matters, and risk management. This committee can create policies for AI validation to ensure algorithms perform as intended without introducing safety risks. Additionally, they can oversee processes for monitoring algorithm performance, addressing unexpected outcomes, and managing updates. A solid cybersecurity framework for medical AI and IoMT systems integrates compliance, operational resilience, and patient safety into every decision [10][11].
Managing Third-Party Risks in AI and IoMT
The risks don’t stop at internal systems - external partnerships also require careful oversight. Vendors, device manufacturers, and software providers often introduce vulnerabilities into connected healthcare environments. For instance, maintaining control over product support, lifecycle management, device monitoring, and regulatory compliance can be a major challenge [7]. Even a single vulnerability in an IoT device could ripple across an entire hospital network [8].
Supply chain attacks pose a serious threat to patient data and critical systems [13]. To counter these risks, healthcare organizations need to adopt rigorous vendor assessment processes. Evaluating the security practices of external partners before integrating new AI or IoMT solutions is crucial. Additionally, continuous monitoring of vendor relationships is necessary to ensure security standards remain strong as products evolve and new vulnerabilities appear. Protecting these external connections is key to maintaining safe and uninterrupted patient care.
Technical and Operational Security Controls
Building an effective cybersecurity framework is just the beginning. Healthcare organizations must go a step further by converting these policies into practical technical safeguards and operational procedures. These measures are essential for protecting IoMT devices and AI systems from real-world risks, ensuring patient data stays secure and medical devices operate safely.
Secure Architecture for IoMT and AI Systems
A strong security foundation for IoMT starts with Zero Trust architecture. This approach assumes that no device or user can be trusted by default. Every device, AI application, and user is treated as a potential risk until authenticated and continuously verified [7][2]. Unlike traditional perimeter-based models, Zero Trust eliminates automatic trust, creating a more secure environment.
Network segmentation is another critical layer of protection. By dividing healthcare networks into isolated zones, devices can only communicate with approved systems and services [14]. For instance, an insulin pump should interact exclusively with its designated monitoring system - not with unrelated systems like billing software. Micro-segmentation takes this concept further by applying precise security policies to individual devices or small groups. This ensures that even if one device is compromised, the breach remains contained.
Hardened edge security gateways act as checkpoints for all IoMT traffic. These gateways centralize control, enforcing firewall rules, protocol filtering, and intrusion detection [14]. Every data packet is inspected before reaching critical systems, reducing the risk of malicious activity. To make these measures scalable, automating identity and certificate lifecycle management eliminates vulnerabilities linked to static credentials that attackers could exploit [7].
Securing IoMT Devices and Patient Data
Once a secure network architecture is in place, attention must shift to protecting the connected devices and the sensitive data they handle. For example, implementing secure boot processes ensures that only authenticated firmware can run on devices, while hardware security modules safeguard cryptographic keys.
End-to-end encryption is vital for protecting patient data, both at rest and in transit [1]. For example, when a connected cardiac monitor sends heart rate data to a central system, encryption ensures that any intercepted information remains unreadable. Continuous monitoring of all connected devices provides real-time visibility, helping security teams quickly detect and address rogue or unmanaged devices that could pose a threat [7][15].
Robust onboarding and provisioning processes are also key. From the moment a device is added to the network, it should receive unique credentials and access permissions tailored to its role [10]. When devices reach the end of their lifecycle, secure decommissioning processes must wipe patient data and revoke credentials. This prevents outdated equipment from becoming a security loophole.
Security Controls for AI Systems
AI systems, which are increasingly integral to healthcare, require their own tailored security measures. Techniques like adversarial testing and runtime integrity checks ensure that AI algorithms function as intended without external interference.
Data provenance and integrity controls play a critical role in securing AI systems [11]. These measures track the origins of training data throughout the AI development process, using cryptographic verification to confirm that data comes from trusted sources and remains unaltered. Audit trails document every change to datasets, providing accountability and making it easier to trace and resolve issues. Separating training environments from production systems adds another layer of protection, preventing experimental AI models from unintentionally affecting live patient care [11]. Together with secure data handling practices, these safeguards help ensure that AI-driven healthcare decisions are accurate, reliable, and safe for patients.
sbb-itb-535baee
Continuous Cyber Risk Management
Relying solely on technical controls isn’t enough. Healthcare organizations need to shift from a reactive mindset to a proactive approach that anticipates potential threats before they happen [3]. This continuous effort is key to protecting both patient data and the delivery of care. By adopting this approach, technical safeguards work hand-in-hand with ongoing operational vigilance.
Risk Prioritization and Monitoring
The first step is to prioritize vulnerabilities based on how easily they can be exploited and the importance of the assets involved in your specific healthcare setting [17]. For example, vulnerabilities in critical medical devices demand immediate attention, while lower-risk issues in non-essential administrative devices can be addressed later.
Medical devices pose unique challenges because they often operate on outdated software, making them especially vulnerable to cyberattacks [17]. That’s why continuous monitoring with risk scoring is essential to spot unusual activity before it escalates into a full-blown threat [16][4]. Tools like Censinet RiskOps™ offer centralized visibility across your connected systems, enabling real-time threat detection and automated risk scoring. Its command center consolidates risk data into a user-friendly dashboard, helping security teams identify emerging threats and prioritize fixes based on their impact on clinical operations. Linking these risk insights directly to response actions is crucial for minimizing harm.
Incident Response for AI and IoMT Threats
When a security incident occurs, acting quickly and accurately is critical. Incident response plans must address the specific challenges of IoMT (Internet of Medical Things) and AI systems, where a compromised device can directly affect patient care. Device isolation protocols should allow security teams to quarantine affected equipment without disrupting essential clinical functions. For instance, if a connected cardiac monitor is compromised, the response plan must isolate the device while ensuring continuous patient monitoring through backup systems.
Under HIPAA regulations, organizations must notify affected patients within 60 days and report breaches involving more than 500 individuals to the Department of Health and Human Services. Additionally, clinical teams must be alerted immediately to ensure patient safety isn’t compromised. Close coordination between IT security and clinical staff is essential for maintaining both cybersecurity and patient care. Lessons learned from incidents should feed back into improving the overall cybersecurity program.
Measuring and Improving Cybersecurity Programs
To strengthen cybersecurity efforts, measurable outcomes are essential. IoMT security, in particular, requires constant monitoring and risk reduction across complex, high-stakes environments [18]. Incorporating IoMT security into a broader strategy - such as using Zero Trust principles, strong identity management, and coordinated response plans - creates a more resilient system [18]. Tracking metrics like the time it takes to detect threats, the percentage of devices with up-to-date security patches, and the number of unmanaged devices on the network provides clear indicators of how well the program is working.
The Health Sector Coordinating Council (HSCC) is working on an AI Governance Maturity Model to help organizations evaluate their current capabilities and identify areas for improvement. Platforms like Censinet promote collaborative risk management by connecting healthcare organizations in a shared risk network, allowing them to compare their security measures with industry peers. Additionally, tools like Censinet AI™ streamline risk assessments by automating tasks such as vendor questionnaires, evidence validation, and risk reporting. This reduces risks efficiently while ensuring human oversight remains a key part of the process.
Conclusion
The concept of the connected patient represents a leap forward in healthcare while simultaneously presenting a significant cybersecurity challenge. With AI and IoT technologies now woven into the fabric of clinical care, the potential attack surface has grown exponentially. By 2025, over 1 million IoT medical devices were exposed online[7], and the cost of healthcare data breaches has skyrocketed to $10.93 million - an alarming 53.3% increase over just three years[4]. These numbers illustrate the pressing need to shift from reactive responses to proactive, continuous defenses.
Healthcare organizations can no longer rely on reactive cybersecurity strategies. Cyberattacks don’t just threaten data - they endanger patient care, disrupt critical operations, delay procedures, and, most importantly, jeopardize lives[3][5][20]. Addressing these threats demands more than isolated technical fixes; it calls for embedding security into every layer of clinical risk management. This is where the comprehensive frameworks discussed earlier become vital.
One of the biggest hurdles lies in addressing internal vulnerabilities. Many healthcare providers face organizational challenges that leave their IoT systems exposed. Issues like unmanaged devices, weak authentication, and outdated medical equipment make easy targets for cybercriminals[7][8][19][20]. Overcoming these risks requires strong leadership, sufficient resources, and collaboration between IT security teams and clinical staff. Breaking down silos between these groups is essential.
A proactive, ongoing approach to risk management is the only way forward. This involves adopting robust cybersecurity frameworks that align with evolving U.S. regulations, establishing clear AI governance, securing third-party partnerships, and ensuring constant vigilance with real-time monitoring and rapid incident response strategies. With cyberattacks on healthcare organizations increasing by 45% year-over-year[4][15], the need for action has never been more urgent.
Protecting connected patient systems isn’t a one-off task - it’s a continuous commitment to safeguarding both data and lives. Healthcare organizations that recognize this reality and invest in comprehensive, adaptive cybersecurity measures will be better equipped to deliver safe, cutting-edge care in this era of IoT and AI. By integrating strong cybersecurity practices into clinical operations, healthcare providers can truly realize the promise of the connected patient while keeping their systems and patients secure.
FAQs
What cybersecurity risks do IoT devices pose in healthcare settings?
IoT devices in healthcare come with their share of cybersecurity challenges. Among the most pressing issues are unauthorized access, often due to the use of weak or default passwords, and outdated software vulnerabilities that hackers can exploit. There's also the looming danger of data breaches, which can expose highly sensitive patient information. On top of that, ransomware attacks pose a serious risk, encrypting crucial data and potentially disrupting hospital operations. Even worse, compromised medical devices can serve as gateways for attackers, jeopardizing both system integrity and patient safety.
To combat these threats, healthcare organizations need to implement strong security practices. This includes ensuring regular software updates, adopting robust authentication protocols, and continuously monitoring connected devices to identify and address potential risks without delay.
What are the best practices for effectively implementing a Zero Trust architecture in healthcare organizations?
To put a solid Zero Trust architecture in place for healthcare, it's crucial to constantly confirm the identity of all users and devices accessing your network. This means using multi-factor authentication (MFA) and implementing strict access controls to minimize the risk of unauthorized access.
Another key step is network segmentation. By dividing your network into smaller, isolated sections, you can limit lateral movement, protecting sensitive patient data and critical devices from potential threats. It's also essential to maintain real-time visibility of all connected devices, keeping an eye out for any unusual activity that might signal a security issue. Automating security policies and incident responses can help your organization act swiftly in the face of vulnerabilities or breaches, reducing potential damage.
These strategies can help healthcare organizations build stronger defenses and safeguard their interconnected systems, especially as IoT continues to play a larger role in the industry.
How can healthcare organizations keep AI systems secure and reliable in connected environments?
To keep AI systems in healthcare secure, it's crucial to implement continuous monitoring. This approach helps identify and respond to potential threats as they emerge. Performing regular vulnerability assessments is another key step, as it allows organizations to spot and address system weaknesses before they can be exploited.
Using a zero trust architecture is also essential. This model ensures that every access request is thoroughly verified, adding an extra layer of protection. At the same time, strong access controls should be in place to restrict system access to authorized personnel only.
Incorporating AI-powered threat detection tools can significantly improve the ability to detect unusual activity or cyber threats early. Additionally, adhering to regulations like HIPAA ensures that patient data is managed with the highest level of security. Finally, a well-prepared incident response plan is vital. It enables organizations to act swiftly and effectively to minimize damage if a security breach occurs.
Related Blog Posts
Key Points:
What is connected patient care, and why is it important?
Connected patient care refers to the integration of IoT devices, medical AI, and digital tools to enhance healthcare delivery.
- IoT devices collect and transmit real-time patient data, enabling continuous monitoring and timely interventions.
- Medical AI analyzes this data to support diagnostics, treatment planning, and personalized care.
- This approach improves patient outcomes, reduces hospital readmissions, and enhances operational efficiency.
How does IoT impact healthcare?
IoT transforms healthcare by connecting medical devices, wearables, and sensors to clinical networks:
- Real-time monitoring: IoT devices provide continuous data on patient vitals and conditions.
- Improved diagnostics: IoT-enabled imaging systems and sensors enhance diagnostic accuracy.
- Operational efficiency: IoT streamlines workflows, such as inventory management and patient tracking.
- However, IoT also introduces cybersecurity risks, requiring robust protections.
What are the cybersecurity risks of connected medical devices?
Connected medical devices face several cybersecurity risks:
- Data breaches: Unauthorized access to sensitive patient information.
- Ransomware attacks: Cybercriminals can lock devices or systems, disrupting care.
- Device vulnerabilities: Many IoT devices run outdated software, making them easy targets for hackers.
- AI manipulation: Attackers can tamper with AI models, leading to incorrect diagnoses or treatment plans.
Why is cybersecurity critical in connected patient care?
Cybersecurity is essential to protect patient safety and data integrity:
- Safeguards sensitive data: Prevents unauthorized access to personal health information.
- Ensures device functionality: Protects IoT devices from being hacked or disrupted.
- Builds trust: Patients and providers rely on secure systems for accurate and safe care delivery.
- Without robust cybersecurity, connected care becomes a liability instead of an advantage.
How can healthcare organizations secure IoT and AI systems?
Organizations can take several steps to secure connected systems:
- Implement encryption: Protects data in motion and at rest.
- Adopt zero-trust architectures: Verifies every connection to prevent unauthorized access.
- Conduct regular audits: Identifies and mitigates vulnerabilities in IoT and AI systems.
- Segment networks: Isolates IoT devices to prevent lateral attacks.
- Comply with regulations: Ensures adherence to standards like HIPAA and GDPR.
What is the future of connected patient care?
The future of connected patient care is promising:
- AI-driven diagnostics: Advanced AI models will improve diagnostic accuracy and speed.
- Secure IoT ecosystems: Enhanced cybersecurity measures will protect connected devices and data.
- Personalized care: IoT and AI will enable tailored treatment plans based on real-time data.
- Improved patient outcomes: Connected care will reduce hospitalizations and enhance overall healthcare quality.


