EHR Vendor Risk Assessment: Protecting Clinical Data and Ensuring System Reliability
Post Summary
When choosing an EHR vendor, the risks tied to data security, compliance, and system reliability can’t be ignored. A single vulnerability in a vendor’s system could lead to data breaches, HIPAA violations, or disruptions in patient care. This guide simplifies the process of assessing EHR vendors by focusing on key steps:
- Map Data Flows: Identify all systems interacting with patient data, including portals, billing tools, and telehealth platforms.
- Governance Framework: Assign a security officer, train staff, and document safeguards to meet HIPAA requirements.
- Evaluate Risks: Review vendors for security, privacy, uptime, interoperability, and compliance certifications.
- Monitor Continuously: Track vendor performance, reassess risks regularly, and manage incidents proactively.
- Use Tools: Automation platforms like Censinet RiskOps™ can streamline assessments and monitoring.
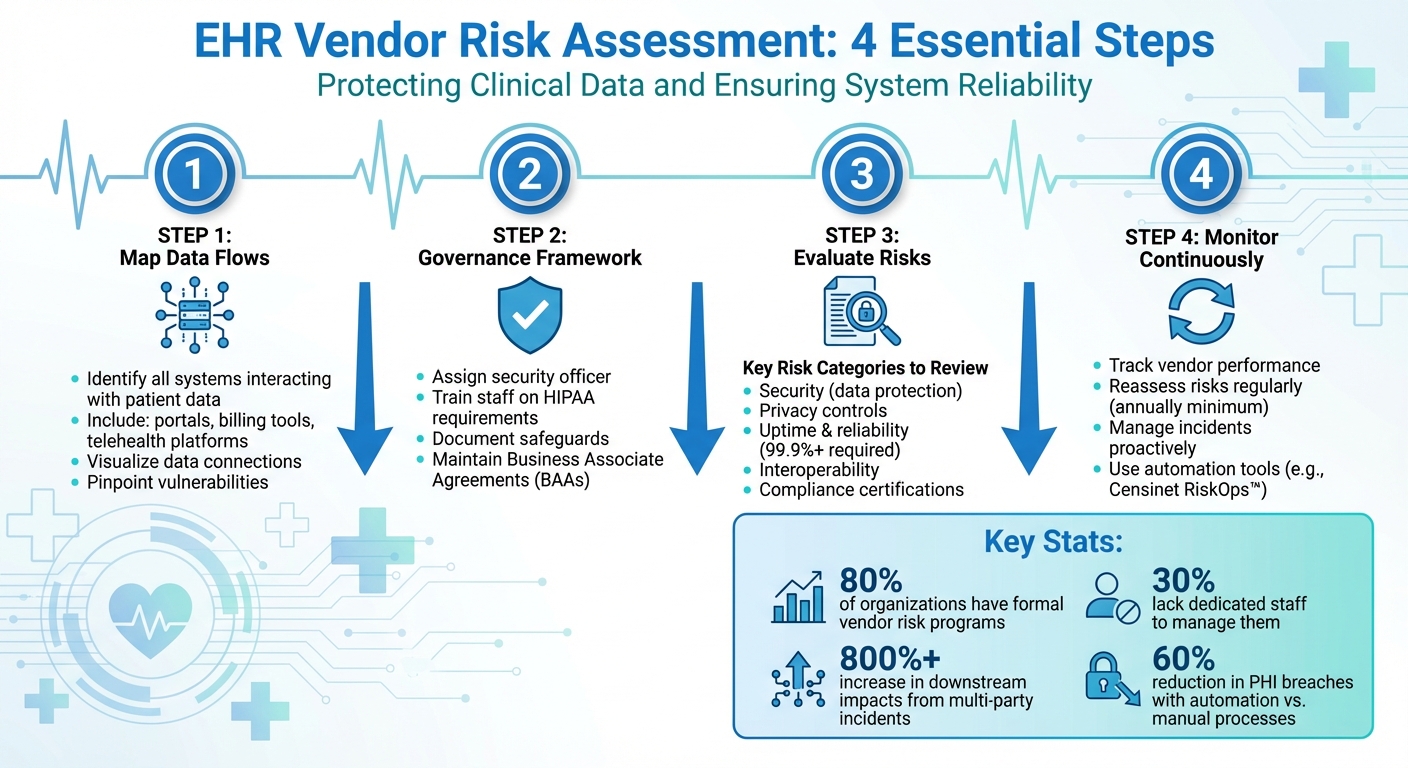
4-Step EHR Vendor Risk Assessment Process for Healthcare Organizations
Core Components of EHR Vendor Risk Assessment
Defining the Scope of EHR Vendor Risk
The first step in creating a strong vendor risk program is identifying every system and service that interacts with patient data. This goes beyond just your primary EHR platform. It includes related tools like patient portals, e-prescribing software, diagnostic and lab interfaces, billing systems, health information exchange (HIE) connections, telehealth platforms, and even backup systems. Mapping out these connections helps you visualize data flows and pinpoint vulnerabilities. Without a clear scope, hidden risks can easily slip through the cracks. Once you've mapped out all the touchpoints, you're in a better position to establish a governance framework that keeps everything secure.
Creating a Governance Framework
To protect electronic protected health information (ePHI), healthcare organizations need a solid governance framework guided by the HIPAA Security Rule. This framework should include administrative safeguards such as appointing a security officer, providing staff training, implementing access controls, and scheduling regular assessments. Proper documentation is also critical - this includes recording all security measures, maintaining Business Associate Agreements (BAAs), and outlining a plan for managing vendors who handle ePHI. It's important to note that while EHR vendors play a role in data security, they are not responsible for HIPAA compliance. That responsibility falls on healthcare providers. After completing a risk analysis, organizations should develop an actionable plan, which might involve updating software, adjusting workflows, revising policies, or conducting additional staff training [1].
Key Risk Categories to Evaluate
A thorough Security Risk Analysis (SRA) is essential for identifying vulnerabilities and putting safeguards in place. Once the governance framework is set, healthcare organizations should evaluate vendors across several critical risk categories to understand and mitigate potential threats:
- Security: Review how vendors protect data both at rest and in transit. This includes examining authentication protocols, incident response plans, and disaster recovery strategies.
- Privacy Controls: Ensure vendors handle patient consent properly and restrict data access to authorized users only.
- Availability and Reliability: Check for uptime guarantees, system redundancy, and how quickly vendors respond to support requests to ensure consistent system performance.
- Interoperability: Evaluate how well the vendor's system integrates with other clinical tools without compromising security.
- Compliance: Confirm that vendors meet HIPAA requirements, hold up-to-date certifications, and undergo regular audits to prove adherence to industry standards [2].
Step-by-Step Process for EHR Vendor Risk Assessment
Vendor Intake and Classification
Start by identifying every vendor that interacts with your EHR environment. This means reviewing vendor agreements, contracts, and purchase orders to compile a complete inventory. Don't forget to include ancillary systems like patient portals, lab interfaces, and billing tools in this review [3]. Assign a security official to oversee the entire process and ensure you stick to a consistent risk evaluation methodology [4].
Next, categorize vendors based on risk factors such as the size of their practice, patient volume, specialty, and how deeply they're integrated into your systems [5][6]. To streamline this, use an evaluation matrix that scores vendors on key areas like security, compliance, data access, functionality, and credentials [5]. This approach helps flag high-risk vendors - especially those handling sensitive ePHI - for more detailed scrutiny.
Risk Analysis and Mitigation Planning
Once vendors are classified, dive deeper with a thorough risk analysis to uncover vulnerabilities. Assess each vendor's security protocols, privacy measures, system availability, interoperability, and compliance certifications [5][6]. Key areas to focus on include encryption methods, system uptime (aim for 99.9% or higher), disaster recovery plans, and certifications like HIPAA, HITECH, and the 21st Century Cures Act [5][6].
Document your findings and create a mitigation plan that addresses any gaps. This might involve requesting additional documentation, updating Business Associate Agreements, or implementing compensating controls. For vendors with significant risks, set clear timelines for remediation and assign follow-up responsibilities to ensure accountability.
After mitigation plans are set, stay proactive by monitoring vendors continuously and establishing robust incident management protocols.
Continuous Monitoring and Incident Management
Ongoing monitoring is crucial. Keep an eye on vendor performance by tracking metrics like uptime, adherence to service level agreements, and software updates that could introduce new vulnerabilities [5]. Establish clear escalation procedures and communication protocols for handling incidents [5][7]. For high-risk vendors, schedule regular reassessments - at least once a year - to evaluate changes in their security practices, financial stability, or compliance status. This ensures your EHR environment remains secure and compliant over time.
sbb-itb-535baee
Best Practices for EHR Vendor Risk Management
A structured risk assessment process is key to effective EHR vendor management. Here are some practical steps to help secure and simplify the process.
Standardizing Risk Assessments
Consistency is crucial when evaluating EHR vendors. While the HIPAA Security Rule doesn't prescribe a single method for risk analysis, it does require any chosen approach to meet specific objectives [2][1]. To ensure a reliable process, use established frameworks like NIST guidelines (SP 800-30, 800-66, 800-100, 800-115) for safeguarding electronic protected health information. The HITRUST Common Security Framework (CSF) is another helpful resource that ties existing frameworks to risk assessment and management [2].
Customized questionnaires are a great way to dig deeper into vendors' capabilities. Include questions on references, compliance, disaster preparedness, cybersecurity governance, and security controls [8]. For added support, organizations like the Healthcare Information and Management Systems Society (HIMSS) offer IT security self-assessment tools [2]. Tailor the depth of your assessments based on the vendor's role and importance.
"Risk is subjective - what one organization or industry can tolerate, another can't." - Jon M. Quigley, Principal, Value Transformation [8]
To streamline your evaluations, create a "perfect vendor" profile that reflects your organization's current and future needs. This profile can serve as a benchmark for future assessments and RFPs [8]. Use a consistent risk assessment matrix - like a 3x4 non-numeric scale for severity and likelihood - to evaluate threats and assign risk levels [8]. Document every step of the process, including data collection, identified threats, security measures, and risk level assignments [2].
Once a standardized approach is in place, automation can take efficiency to the next level.
Using Automation to Improve Efficiency
Manual oversight can be slow and prone to errors. By automating third-party risk management, healthcare organizations have reduced PHI breach incidents by up to 60% compared to manual processes [9]. This not only improves compliance but also enhances patient safety.
Censinet RiskOps™ is one tool that automates the entire workflow - from initial assessments to continuous monitoring. It offers real-time visibility into vendor compliance, security certifications, and emerging risks, ensuring you can address issues proactively [9]. The platform also lets you create tailored assessment templates based on vendor criticality and data access levels, streamlining the evaluation process through automated questionnaire distribution and response collection [9].
For even greater efficiency, Censinet AI™ accelerates risk assessments by allowing vendors to complete security questionnaires in seconds. It automatically summarizes vendor documentation, captures key integration details, identifies fourth-party risks, and generates risk summary reports. This blend of automation and human oversight shortens assessment cycles while keeping critical decisions in the hands of risk teams.
The platform’s advanced routing capabilities act like "air traffic control" for risk management, directing key findings and tasks to the appropriate stakeholders. With real-time data displayed in an intuitive dashboard, Censinet RiskOps™ becomes a centralized hub for managing AI-related risks, policies, and tasks.
While automation simplifies workflows, strong contracts remain a cornerstone of effective risk management.
Including Risk Requirements in Contracts
Your Business Associate Agreements (BAAs) and service contracts are your first line of defense. Embedding risk requirements in these agreements ensures that vendors uphold their responsibilities from the start.
Contracts should mandate that vendors implement up-to-date data security measures and comply with healthcare regulations like HIPAA, HITECH, the 21st Century Cures Act, and ONC-authorized certification bodies (ONC-ACBs) [5]. These certifications are non-negotiable for vendors handling clinical data.
Include an uptime guarantee of at least 99.9% to maintain high system availability [5]. Additionally, require vendors to have robust disaster recovery and business continuity plans to address potential outages [5]. These provisions create accountability and provide recourse if vendors fall short.
"The VRA doesn't stop once the vendor is engaged. Monitor for any variations in agreed-upon deliverables or processes." - Salma Suzie Fakhri, Owner and Director of FC2Y, Oceana 144 [8]
Set clear triggers for contract reviews, such as financial troubles, legal issues, or safety concerns [8]. Schedule regular reviews based on vendor risk levels: low-risk vendors might be reviewed annually, while high-risk vendors may need reviews twice a year or quarterly. Conduct a thorough review at least 180 days before contract renewal [8]. This ensures your agreements stay relevant as circumstances change.
Conclusion
Key Takeaways
Assessing the risks associated with EHR vendors is a critical step in safeguarding clinical data and ensuring system reliability. Recent statistics reveal that while nearly 80% of organizations have formal vendor risk assessment programs, around 30% lack the dedicated staff needed to effectively manage this responsibility [10]. This gap leaves organizations vulnerable to fines, lawsuits, financial losses, and damage to their reputation.
The ripple effect of multi-party incidents is staggering, with downstream impacts increasing by over 800% [10]. A striking example is the December 2022 breach involving Avem Health Partners and 365 Data Centers, which exposed the records of more than 271,000 patients [10]. This case highlights the reality that even a vendor’s security lapse can compromise patient data, regardless of how secure an organization’s internal systems might be.
Building a strong vendor risk program demands constant evaluation of all business partners. Taking a proactive approach - such as vendor classification, ongoing monitoring, and periodic reassessments - helps address potential issues before they escalate. Collaboration across departments like Compliance, IT, Security, Legal, and Finance ensures more thorough risk evaluations. Tools like Censinet RiskOps™ and Censinet AI™ bring automation into the mix, offering real-time insights into vendor compliance and emerging risks. These efforts collectively protect clinical data and enhance system reliability.
Next Steps for Healthcare Leaders
With these insights in mind, it’s time for healthcare leaders to take action. Start by reviewing your current vendor risk management practices and establishing a formal program with dedicated staff. Develop consistent criteria for evaluating vendor risks, ensuring that even vendors providing minor services are assessed, as they can still pose significant risks if they have access to sensitive data or physical spaces.
Classify vendors based on their risk level and the impact they have on your organization. For each vendor, create a detailed risk management plan that outlines specific responses, assigns responsibilities, and identifies mitigation strategies. Conduct assessments annually - or more often - to keep pace with changes in vendor operations and regulatory requirements. Regularly refine your criteria, methodologies, and tools to stay ahead of evolving risks [11]. Strengthening your vendor risk management program today will help protect patient data, improve system reliability, and ensure compliance with regulations in the long run.
FAQs
What are the essential elements of a successful EHR vendor risk assessment?
An effective electronic health record (EHR) vendor risk assessment focuses on a few essential elements to safeguard clinical data and keep systems running smoothly. These include assessing potential risks, keeping a close eye on vendor performance, ensuring adherence to regulatory requirements, and having a strong incident response plan ready to go.
It's equally important to prioritize continuous monitoring. This helps organizations catch and address vulnerabilities before they become serious issues. By concentrating on these areas, healthcare providers can protect sensitive patient information and ensure their systems remain dependable for delivering quality care.
How does Censinet RiskOps™ improve EHR vendor risk management?
Censinet RiskOps™ makes managing EHR vendor risks easier and more efficient by automating essential tasks like risk assessments and vendor evaluations. With its real-time monitoring capabilities, it ensures ongoing compliance tracking, enabling organizations to spot and tackle vulnerabilities as they arise.
By cutting down on manual work and enhancing precision, Censinet RiskOps™ helps healthcare providers safeguard sensitive clinical data while keeping their systems dependable.
Why is continuous monitoring essential for managing risks with EHR vendors?
Continuous monitoring plays a key role in managing risks associated with EHR vendors. It provides real-time insights into a vendor's security status, making it possible to spot potential vulnerabilities or threats early on. This enables swift action to safeguard sensitive patient information.
Beyond protecting data, continuous monitoring helps ensure the stability of essential systems. By addressing risks promptly, it minimizes the chances of disruptions in clinical operations, supporting both secure data management and uninterrupted patient care.


