4-Factor Risk Assessment: Guide for HDOs
Post Summary
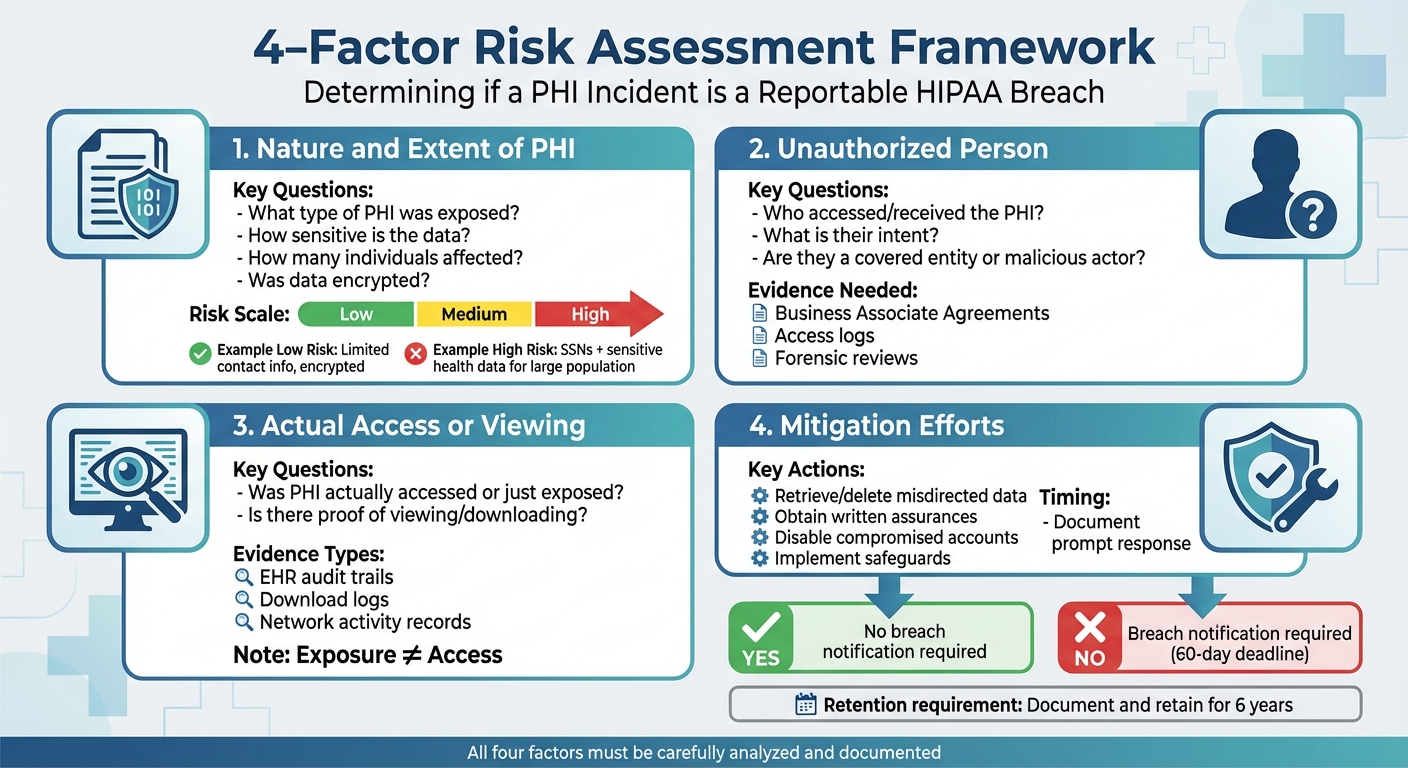
When a healthcare organization mishandles protected health information (PHI), federal law requires determining if it's a reportable breach or if the risk of compromise is low. The HIPAA Breach Notification Rule outlines a four-factor assessment to guide this decision:
- Nature of the PHI: Assess the sensitivity of the exposed data, like Social Security numbers or medical records.
- Unauthorized Party: Evaluate who accessed or received the data and their potential to misuse it.
- Access or Viewing: Confirm if the PHI was actually accessed or just exposed.
- Mitigation Efforts: Review actions taken to reduce potential harm, such as retrieving data or securing systems.
Each factor must be carefully analyzed, documented, and retained for six years to ensure compliance. Properly applying this process helps healthcare organizations avoid unnecessary reporting, regulatory penalties, and reputational damage. By integrating this framework into incident response plans, organizations can handle breaches efficiently and protect patient trust.
HIPAA 4-Factor Risk Assessment Framework for Healthcare Organizations
The Four Assessment Factors Explained
The Department of Health and Human Services (HHS) and the Office for Civil Rights (OCR) require healthcare organizations to assess any unauthorized use or exposure of Protected Health Information (PHI) using four key factors. These evaluations help determine whether there’s a low probability of compromise under 45 C.F.R. §164.402.
Each factor must be carefully documented and weighed to reach a well-supported conclusion. Many healthcare delivery organizations (HDOs) use qualitative ratings - like low, medium, or high risk - for each factor to decide the overall likelihood of compromise and whether breach notifications are necessary. Below is a breakdown of these four critical factors.
Factor 1: Nature and Extent of PHI Involved
This factor examines what kind of PHI was exposed and how easily it could be used to identify or harm individuals. Key considerations include:
- Identifiers and Re-identification Risk: Personal details like Social Security numbers (SSNs), medical record numbers, or driver’s license numbers pose a higher risk than general demographic data.
- Clinical Sensitivity: Information about mental health, HIV status, substance use, reproductive health, or genetic details is particularly sensitive under U.S. privacy norms. Financial data, such as bank account or payment card numbers, also increases the potential for identity theft or fraud.
- Scope and Volume: The number of affected individuals, the depth of data (e.g., years of medical history versus a single test result), and the amount of information per person are all crucial. For example, a single appointment reminder email sent to the wrong person carries far less risk than a database containing hundreds of detailed patient records.
- Format and Protections: Encrypted data (when encryption keys remain secure) significantly lowers risk. On the other hand, unencrypted files, unredacted paper records, or free-text notes that could identify individuals - especially in small communities - heighten the risk.
HDOs often use a qualitative scale to rate this factor. For instance:
- Low risk: Limited contact information secured by strong encryption.
- Medium risk: Names paired with common diagnostic codes for a small group.
- High risk: Full identifiers combined with sensitive health or financial data for a large population.
Factor 2: Unauthorized Person Who Used or Received PHI
This factor evaluates who accessed or received the PHI and their potential to misuse or disclose it. The risk depends on the recipient’s identity, intent, and environment.
For example:
- A HIPAA-covered entity, like another hospital, may pose a lower risk due to professional ethics and secure data handling practices.
- Malicious actors or unknown recipients, on the other hand, present a much higher risk.
- Even within an organization, an employee accessing PHI for personal reasons (e.g., viewing an ex-partner's records) could lead to misuse, despite their familiarity with HIPAA.
To assess this factor, HDOs should gather evidence such as:
- Business Associate Agreements or attestations from recipients confirming proper handling or destruction of PHI.
- Logs and technical controls (e.g., encrypted email gateways) showing how the data was transmitted or stored.
- Forensic reviews of email headers, network activity, or access logs to verify whether PHI was routed securely or exposed to untrusted parties.
Factor 3: Actual Acquisition or Viewing of PHI
This factor focuses on whether PHI was actually accessed, copied, or viewed versus merely being exposed. The distinction is crucial.
Evidence of actual access includes:
- Logs showing unauthorized viewing, downloading, or copying of PHI.
- Audit trails from electronic health records (EHRs) confirming repeated access to sensitive data, such as in insider "snooping" incidents.
- Verified data exfiltration during ransomware attacks.
Conversely, if logs or other evidence confirm that no one accessed the data - such as a misconfigured cloud storage bucket exposed briefly but not accessed - it may support a low-risk conclusion, especially if other factors also point to minimal risk.
Cases where PHI has been clearly accessed or exfiltrated typically result in a high-risk rating and are more likely to trigger breach notifications.
Factor 4: Extent to Which the Risk Has Been Mitigated
This factor assesses the steps taken to reduce the likelihood of PHI misuse after an incident. Effective mitigation measures include:
- Retrieving or deleting misdirected data (e.g., recalling emails, revoking shared links, or wiping devices).
- Obtaining written assurances from recipients that data was not used or disclosed and has been securely destroyed.
- Disabling compromised accounts, resetting passwords, or correcting system vulnerabilities.
- Implementing long-term safeguards like workforce training, improved access controls, or enhanced monitoring.
The timing and thoroughness of these actions are critical. Prompt responses - backed by documentation like logs or attestations - help lower residual risk. However, while offering credit monitoring or identity theft protection can help affected individuals, these measures alone don’t eliminate breach notification requirements.
Ultimately, Factor 4 evaluates whether the organization followed formal incident response protocols and Security Rule standards to minimize potential harm. A strong, well-documented mitigation effort can influence the overall assessment of risk and the need for notifications.
How to Prepare for a Four-Factor Risk Assessment
Getting ready for a four-factor risk assessment means setting up your incident response process to seamlessly include this framework. Healthcare Delivery Organizations (HDOs) need the right tools to conduct thorough and defensible assessments. Preparation starts with three key elements: a comprehensive PHI asset inventory, well-documented incident response (IR) plans with detailed logging, and centralized risk management platforms to simplify workflows and documentation. By investing in these areas, organizations can quickly scope incidents, gather evidence reliably, and make notification decisions that stand up to regulatory scrutiny.
Build a PHI Asset Inventory
A thorough PHI (Protected Health Information) asset inventory is the foundation for accurate and efficient assessments. Begin by listing every system and repository that handles PHI. This includes electronic health records (EHRs), billing systems, lab and imaging platforms (PACS), patient portals, telehealth applications, email, cloud storage, backup systems, mobile apps, and networked medical devices. For each system, document details like the PHI data elements it contains - such as Social Security numbers, medical record numbers, clinical data, and financial information. Also, track typical data volumes, the patient populations served, and whether sensitive categories like behavioral health, HIV status, or reproductive health records are involved.
Next, map how data flows between systems to understand where PHI moves internally and externally. Keep these data flow diagrams updated and tied to specific incident scenarios so investigators can quickly identify what PHI might be affected during an incident. Mark high-risk assets - those associated with sensitive diagnoses, research data, or large patient groups - for priority review. To keep the inventory current, implement a formal change-management process that ensures new systems, integrations, and vendors are added during onboarding.
Establish Incident Response Plans and Logging
Create a HIPAA-compliant incident response plan that clearly defines what constitutes a security incident versus a suspected breach. Outline when and how to initiate a four-factor risk assessment for situations like misdirected emails, lost devices, EHR snooping, or cloud misconfigurations. Assign specific roles for triage, investigation, analysis, legal and compliance reviews, and final notification decisions. Include timelines that align with the HIPAA Breach Notification Rule, ensuring decisions are made within the 60-day deadline.
Strong logging and evidence collection processes are essential for each step of the four-factor assessment. Set up procedures to preserve logs and obtain attestations from recipients - such as confirmations of deletion or non-use - as part of mitigation efforts. Conduct tabletop exercises to simulate incidents like lost laptops, misdirected emails, or employee snooping. These exercises should include performing the four-factor assessment, documenting decisions, and making notification determinations under time constraints.
Use Risk Management Platforms
Centralized platforms for risk and compliance management can help HDOs ensure consistency, streamline processes, and stay audit-ready. These platforms can maintain the PHI asset inventory and vendor list, including business associate agreements and service details related to PHI handling. They also store incident records, four-factor assessment templates, mitigation steps, approvals, and final decisions for at least six years, as required by HIPAA.
Platforms like Censinet RiskOps™ simplify third-party and enterprise risk assessments across clinical systems, medical devices, and supply chains. They integrate directly with PHI asset and vendor inventories, benchmark cybersecurity measures, and facilitate collaboration with vendors to improve security controls. For example, Tower Health used Censinet RiskOps to streamline its risk assessments, enabling three full-time employees to return to their primary roles while handling more assessments with just two dedicated staff members. Similarly, Baptist Health replaced spreadsheets with the platform, gaining access to a broader network of hospitals for collaboration and partnership. These examples highlight how specialized tools cut down on manual effort, boost efficiency, and support audit-ready, defensible assessments.
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." - Matt Christensen, Sr. Director GRC, Intermountain Health
sbb-itb-535baee
How to Implement the Four-Factor Risk Assessment
Integrate with Incident Response Processes
Once you've established your PHI inventory and incident response (IR) plan, the next step is weaving the four-factor risk assessment into your incident response workflow. Identify key decision points in your response playbooks where this assessment should be triggered - specifically when there's a suspected impermissible use or disclosure of PHI under the HIPAA Privacy Rule. Update intake forms and ticketing systems to include essential questions that flag PHI involvement, such as the types of data affected, systems impacted, and the number of records involved. If the use or disclosure seems impermissible, ensure these cases are automatically routed to privacy and security leads for further evaluation.
During triage, confirm whether PHI is involved and assess the scope of the incident. Document your breach determination thoroughly, as this will guide your next steps, including notification requirements and corrective actions. After the incident, conduct a review to confirm that the assessment was applied correctly, timelines (like the 60-day breach notification window) were met, and any lessons learned were integrated into your broader response and risk management strategies. This approach ensures consistency in documentation and smooth role assignments for future incidents.
Standardize Documentation and Reporting
For every incident, create a detailed record that includes the timeline, affected systems, PHI details, factor-specific analyses with supporting evidence, mitigation actions, final breach determination, and leadership approvals.
Structure your reports with separate sections for each of the four factors. Instead of providing a single overall conclusion, break down the analysis by factor, tying specific data - like EHR access logs showing views or web logs indicating no downloads - directly to your risk evaluation. Clearly explain why the risk is categorized as low, medium, or high and how mitigation efforts influenced this assessment. HIPAA guidance and industry standards recommend keeping these records, along with related policies and procedures, for at least six years to demonstrate compliance. Using structured templates and centralized repositories, such as those available in platforms like Censinet RiskOps, can simplify storage, retrieval, and reporting, ensuring consistency across incidents.
Assign Roles and Responsibilities
Clear role definitions are key to maintaining accountability throughout the process. Privacy officers should lead the assessment, interpreting HIPAA Privacy and Breach Notification requirements and drafting the final breach determination. Security teams play a critical role by providing technical evidence - such as logs, forensic analyses, and system configurations - and evaluating the likelihood of PHI being accessed or viewed, as well as the effectiveness of mitigation strategies. Compliance and legal counsel ensure regulatory alignment and help manage litigation risks, while clinical leaders offer insights into the sensitivity of clinical data and potential operational impacts. For high-risk or large-scale incidents, executive leadership or a risk committee should review and approve decisions, particularly when notifications to patients, media, or regulators are necessary.
Vendors and business associates also have responsibilities under their Business Associate Agreements (BAAs) to report incidents promptly. Managing these obligations through a structured third-party risk process - or using platforms like Censinet RiskOps - can help ensure consistent handling across your entire network of partners.
Conclusion
The four-factor risk assessment goes beyond being just a compliance requirement - it's a practical framework designed to safeguard patient data, bolster regulatory compliance, and enable quicker, defensible responses to incidents. By consistently examining the nature and scope of PHI, the unauthorized recipient, whether the data was accessed or viewed, and the effectiveness of mitigation efforts, healthcare delivery organizations (HDOs) can confidently determine breaches that withstand OCR scrutiny while maintaining patient trust.
Integrating this framework into daily workflows not only streamlines compliance but also improves efficiency. Embedding the assessment into incident response playbooks creates repeatable processes that minimize decision delays, speed up triage, and ensure well-documented, audit-ready records. Over time, recurring patterns - such as workforce errors, vendor missteps, or gaps in controls - can inform targeted security measures and training, fostering long-term operational resilience.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." - Terry Grogan, CISO, Tower Health
Platforms like Censinet RiskOps™ are designed with healthcare in mind, integrating PHI inventories, vendor profiles, and incident workflows. These tools make it easier to collect evidence, perform standardized analyses for each factor, and maintain consistent reporting across the organization. What once might have been a manual, spreadsheet-heavy process becomes a streamlined, collaborative effort. With every incident documented in the same way and tied to relevant asset and vendor data, teams can respond confidently, while leadership can demonstrate a mature, risk-based compliance program to regulators and stakeholders.
Make the four-factor assessment a cornerstone of your approach. With clearly defined roles, thorough logging, and the right tools, you'll not only meet HIPAA's breach notification requirements but also create a foundation for reducing risk and enhancing patient data protection. By adopting this disciplined approach, you can strengthen your organization’s defenses and uphold the trust of the patients you serve.
FAQs
How does a four-factor risk assessment help healthcare organizations avoid unnecessary breach notifications?
A four-factor risk assessment is a critical tool for healthcare organizations to pinpoint and address potential vulnerabilities before they lead to data breaches. By carefully examining these weak points, organizations can take deliberate steps to minimize risks, lowering the likelihood of incidents that might trigger breach notifications.
This approach not only helps meet regulatory standards but also spares organizations from unnecessary reporting. More importantly, it protects patient trust and ensures the security of sensitive information, such as Protected Health Information (PHI).
How do mitigation efforts influence the overall risk level in healthcare risk assessments?
Mitigation efforts are key to lowering risks by tackling known vulnerabilities, preventing incidents, and reducing their potential impact. By putting strong controls in place, these measures help decrease residual risk - the level of risk that remains even after safeguards are applied.
In the healthcare sector, where protecting patient information and maintaining uninterrupted operations are top priorities, effective mitigation strategies play a vital role. They strengthen compliance, shield sensitive data, and ensure the security of essential systems.
Why is it necessary to keep documentation for each factor for six years?
Maintaining records for six years is crucial to comply with legal and regulatory standards, especially in healthcare, where strict compliance is non-negotiable. These records provide a dependable historical account, aiding in precise risk assessments and ensuring accountability during audits or forensic reviews.
By keeping these documents intact, healthcare organizations can show they’ve exercised due diligence, uphold transparency, and protect themselves from potential compliance challenges down the road.


