Healthcare Accreditation and Vendor Risk: NCQA, AAAHC, and TJC Requirements
Post Summary
Healthcare organizations must meet strict standards from NCQA, AAAHC, and TJC to maintain accreditation while managing vendor risks. These standards focus on credentialing, data security, and compliance to ensure patient safety and operational integrity.
Key takeaways:
- NCQA: Requires timely credential verification and audits for vendors handling sensitive data. Starting July 2025, stricter timelines apply (e.g., 120-day Primary Source Verification).
- AAAHC: Focuses on credentialing in ambulatory care and supply chain oversight. Re-credentialing every three years and monitoring for sanctions are mandatory.
- TJC: Emphasizes vendor screening, infection control, and physical environment standards. Updates in 2025 reduced and consolidated standards to streamline compliance.
With rising vendor-related breaches (30% in 2024), healthcare entities are accountable for third-party failures, making robust vendor risk management essential for accreditation and patient safety.
NCQA Vendor Risk Requirements
The National Committee for Quality Assurance (NCQA) sets strict guidelines for managing vendor relationships within health plans, Accountable Care Organizations (ACOs), and Credential Verification Organizations (CVOs). Under the principle of Respondeat Superior [6], your organization bears full responsibility for vendor performance. This means that if a vendor misses key verification deadlines, the liability falls on your shoulders. NCQA's requirements are designed to ensure healthcare organizations remain accountable for the actions and performance of every vendor they work with. Below, we break down the key NCQA standards that define these responsibilities.
Credentialing and Recredentialing Standards
NCQA mandates that healthcare organizations verify specific clinician credentials within set timeframes. For example:
- Licensure, malpractice history, board certifications, and sanctions: Must be verified within 180 days.
- Work history and application responses: Require verification within 365 days.
- Education and DEA/CDS certifications: While no specific timeframes are set, documentation is still required [3].
Starting July 1, 2025, NCQA is tightening these requirements further. Organizations seeking accreditation will need to complete Primary Source Verification (PSV) within 120 days, while certification demands verification within just 90 days before committee decisions [7]. Monthly monitoring will also become mandatory, including checks for Medicare/Medicaid exclusions, SAM.gov verification, and real-time tracking of license expirations [6][7].
An example of success in meeting these rigorous standards is Fifth Avenue Healthcare Services, which earned NCQA Credentialing Accreditation in June 2023 [5].
Third-Party Risk Assessment Requirements
In addition to credentialing, NCQA enforces detailed third-party risk assessment protocols to ensure compliance when vendors handle credentialing tasks or access Personally Identifiable Information (PII). Your organization must verify that vendors meet NCQA's documentation standards, and every change to credentialing data must include a full audit trail. This audit trail should document who made the change, what was altered, when it occurred, and why [7].
Vendors must also:
- Conduct annual staff training on maintaining information integrity.
- Implement policies for managing practitioner sanctions, complaints, and adverse events, with a 30-day notification window for reporting [7].
Furthermore, organizations are expected to evaluate vendor technology for its ability to support efficient PSV processing, secure monthly monitoring, and the safe handling of Protected Health Information (PHI) and PII. Importantly, outsourcing these functions does not relieve your organization of accountability. Instead, it highlights the need for meticulous vendor selection and ongoing oversight to maintain NCQA accreditation and protect patient information effectively. Compliance with these standards is critical for both accreditation and safeguarding sensitive data.
AAAHC Vendor Risk Requirements
The Accreditation Association for Ambulatory Health Care (AAAHC) is dedicated to improving the quality of care in ambulatory healthcare settings. Their "1095 Strong, quality every day" approach emphasizes continuous improvement and accountability [8][9]. Similar to NCQA, AAAHC evaluates organizations on their credentialing and re-credentialing processes to ensure patient safety and uphold high standards of care [3]. This responsibility extends to any vendors your organization works with, whether they provide clinical services or manage supply chain operations.
AAAHC's credentialing standards require thorough verification of healthcare providers’ qualifications. This includes licenses, certifications, education, training, work history, and malpractice claims history. Additionally, organizations must check for sanctions or disciplinary actions through resources like the National Practitioner Data Bank (NPDB), System for Award Management (SAM), and the Office of Inspector General's List of Excluded Individuals and Entities (OIG-LEIE) [10]. Primary source verification is a key step, and re-credentialing is generally required every three years [10].
In September 2025, AAAHC introduced an "Updated Toolkit Highlighting Credentialing and Privileging in Ambulatory Health Care." This toolkit is designed to help organizations navigate the detailed process of verifying healthcare professionals’ qualifications and understanding their scope of practice [8][9]. It serves as a practical guide for implementing AAAHC standards in ambulatory care settings.
Meeting AAAHC standards offers more than just accreditation. For instance, accredited organizations can qualify for Medicare and Medicaid certification without needing separate federal or state inspections [9]. Accreditation also enhances your ability to attract and retain skilled healthcare professionals, reduces risks through structured reviews and best practices, and provides documentation that may lead to financial and operational advantages with vendors [9]. These standards are particularly important for managing the unique risks associated with clinical vendors and supply chain partners.
Clinical Vendors and Supply Chain Partners
Third-party vendors play an increasingly important role in healthcare operations, but they also introduce specific risks. To maintain AAAHC accreditation and ensure patient safety, ambulatory organizations must apply strict oversight and verification to both clinical vendors and supply chain partners.
Your vendor credentialing process should cover several key areas, including verification of business credentials, background checks (such as criminal records and fraud history), and certification validation [11]. Credentialing should be an integral part of the onboarding process, with ongoing reviews to ensure compliance with current standards [4]. Regular monitoring is crucial to identify any sanctions or exclusions that may affect your vendors [4].
Providing vendors with ongoing training on topics like patient privacy, security, machinery installation, and waste disposal can help ensure compliance with AAAHC standards [11]. Additionally, comprehensive orientation programs and updated contracts that include specific security requirements and Service Level Agreements aligned with AAAHC expectations strengthen your organization’s risk management framework.
The consequences of vendor failures can be severe. For example, in April 2022, OneTouchPoint - a third-party printing and mailing vendor - experienced a data breach due to unauthorized system access. This incident impacted over 2.6 million individuals and numerous healthcare providers, including Anthem, Kaiser Permanente, and Blue Cross. Compromised data included patient names, addresses, medical records, and test results [2]. This case highlights the critical need for rigorous vendor risk management to maintain AAAHC accreditation and safeguard patient information.
TJC Vendor Risk Requirements
The Joint Commission (TJC) has been updating its standards to emphasize the importance of vendor risk management in ensuring patient safety and regulatory compliance. These updates, aligned with the standards of NCQA and AAAHC, focus on areas like the Environment of Care and high-risk processes [12][13]. Unlike NCQA and AAAHC, TJC allows healthcare organizations to choose their own risk assessment methods - such as Root Cause Analysis, Failure Mode and Effect Analysis, or SWOT Analysis - based on their specific needs [12].
On June 30, 2025, TJC announced significant changes to its standards for hospitals and critical access hospitals, set to take effect on January 1, 2026 [14][15]. This initiative, called "Accreditation 360: The New Standard", reduced the total number of standards from 1,551 to 774 by consolidating 714 requirements [14][15][17]. For example, the Environment of Care and Life Safety chapters were merged into a single "Physical Environment" chapter, cutting the number of performance elements for hospitals by 46–48% [15].
Starting in July 2025, TJC standards became publicly searchable, increasing accessibility and transparency [14][15]. The updated standards also place greater emphasis on infection control, emergency preparedness, and data security - key areas for vendor compliance [16]. Healthcare organizations are encouraged to review the TJC crosswalk to align their documentation with these updated standards before their next survey [14][15]. These changes set the stage for more thorough vendor screening processes, detailed below.
Primary Source Verification and Leadership Oversight
TJC's vendor oversight framework reflects its dedication to patient safety and high-quality care. Healthcare organizations are required to screen and monitor vendors and their representatives according to national, state, and local regulations. This includes verifying training, certifications (like safety practices and HIPAA compliance), immunization records, and conducting background checks [4]. Additionally, organizations must cross-check vendor identifying details, such as tax IDs, against federal and state sanctions lists [4].
During onboarding, it's essential to review vendor documentation, such as cybersecurity certifications, insurance policies, credit histories, and operational details, to confirm compliance [1]. Independent audits of primary vendors can reveal compliance issues that might not be evident from self-reported certifications [1]. Ongoing monitoring for exclusions or sanctions is equally crucial for maintaining accreditation.
An effective vendor risk management program starts with clearly defined roles and responsibilities. This includes appointing a vendor risk management professional and forming a cross-functional team with members from executive leadership, legal, compliance, IT, and procurement departments [1]. Leadership should implement standardized evaluation criteria, including detailed policies, scoring systems, and risk thresholds, to ensure consistency and reduce bias [1]. Centralized communication about regulatory updates, vendor-related issues, and policy changes is also essential [1].
Life Safety and Environment of Care Standards
TJC’s updated standards extend to the physical environment and operational safety, consolidating Life Safety and Environment of Care requirements to better align with the Centers for Medicare & Medicaid Services' Conditions of Participation [14][15]. These standards affect how organizations manage vendors involved in areas like medical equipment maintenance and facility operations.
Using Computerized Maintenance Management Systems (CMMS) can simplify vendor-related tasks by automating equipment maintenance schedules, tracking medical devices, and generating compliance reports for the Environment of Care and Life Safety standards [16]. Vendor staff who impact patient care must meet the same qualifications and certifications required of internal teams, as outlined in TJC’s human resources standards [16].
To stay ahead of compliance issues, organizations should conduct mock surveys and regular internal audits [16]. Industry groups like ASHE are also expanding their educational resources, such as the Physical Environment Survey Readiness Program, to help facilities adapt to the new standards [15]. Training all staff who interact with vendors on these updated requirements is essential for maintaining consistent compliance throughout the organization [16].
How NCQA, AAAHC, and TJC Standards Compare
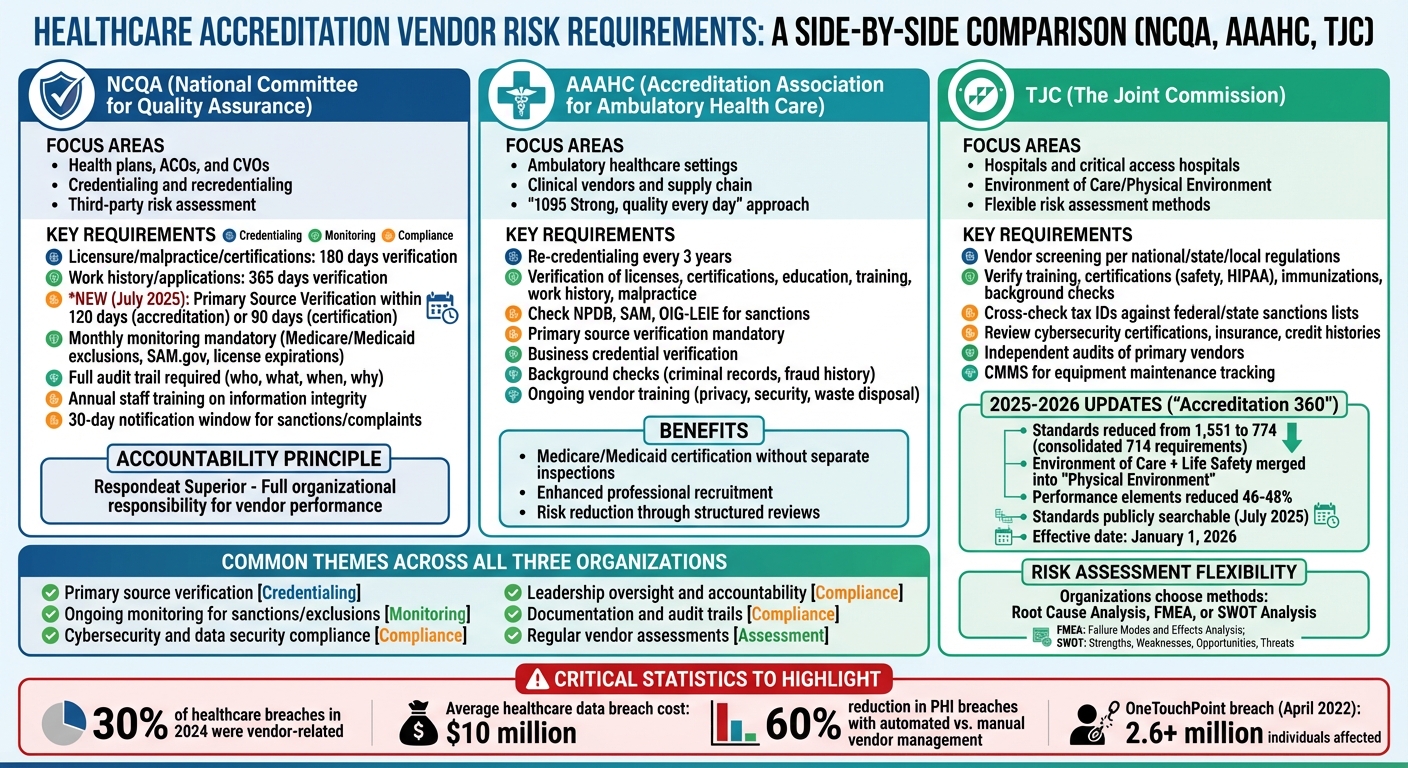
NCQA vs AAAHC vs TJC Healthcare Vendor Risk Requirements Comparison
NCQA, AAAHC, and TJC each outline specific requirements for healthcare organizations to manage vendor risks, using distinct methods for verification, monitoring, and risk assessment[19][20]. Because these standards differ, a single, universal approach to vendor risk management won’t work. Instead, organizations need to develop customized programs that address the unique demands of each accreditation standard. This complexity highlights the importance of creating risk management strategies that are both efficient and tailored to meet diverse requirements.
One of the biggest hurdles is juggling these overlapping but distinct requirements effectively. Relying on manual vendor management processes often falls short, as they struggle to handle the complexity and scale of today’s healthcare supply chains. This can leave organizations vulnerable and lead to inconsistencies in security assessments[18]. On the other hand, healthcare organizations that adopt automated third-party risk management solutions see a significant reduction in PHI breaches - up to 60% compared to manual methods[18].
Side-by-Side Comparison
To comply with multiple accreditation standards, healthcare organizations should create a unified risk classification system that works across all three frameworks. This involves defining vendor risk categories based on factors like PHI access, system criticality, and regulatory requirements. By using automated, standardized assessments and consolidating the most rigorous elements from each accreditation standard, organizations can streamline their processes. This approach not only eliminates redundant evaluations but also ensures thorough compliance with all necessary guidelines[18].
sbb-itb-535baee
Vendor Evaluation Criteria for Accreditation Compliance
When it comes to meeting accreditation standards, having clear and consistent vendor evaluation criteria is non-negotiable for healthcare organizations. Whether it's NCQA, AAAHC, or TJC requirements, the stakes are high. Third-party breaches remain a serious threat, with the average cost of a healthcare data breach climbing to nearly $10 million[1]. This makes prioritizing vendor security qualifications over cost savings a critical decision for protecting patient data and maintaining organizational integrity.
To standardize vendor risk management (VRM) evaluations, organizations should adopt detailed policies, scoring systems, and risk thresholds. This ensures assessments are consistent and free from bias[1]. Key factors like cybersecurity, regulatory compliance, and risk management must take precedence, as the financial and reputational damage of a breach can far exceed the short-term savings of selecting a less secure vendor[1].
Relying solely on third-party reports like SOC 2 Type 2 audits isn’t enough. While they provide useful insights, they may not address specific HIPAA compliance needs or unique organizational risks. Conducting independent audits of critical vendors, where possible, can fill these gaps[1]. Additionally, it’s important to consider fourth-party risks - those introduced by a vendor’s subcontractors. Including questions about subcontractors in security reviews and audits helps address these hidden vulnerabilities[1].
Cybersecurity and Risk Assessment Standards
One cornerstone of vendor evaluation is compliance with the HIPAA Security Rule, which is undergoing updates to mandate more controls and annual compliance audits. These updates also address emerging risks, including those related to AI and quantum computing[1][2]. When assessing vendor cybersecurity measures, organizations should verify key certifications such as SOC 2, ISO 27001, and HITRUST. HITRUST, in particular, stands out in healthcare, offering a robust, adaptable framework with three assurance levels (e1, i1, r2) and guided remediation steps[2].
The consequences of inadequate vendor security are well-documented through past breaches, which highlight the financial and reputational fallout of poor oversight. To meet these challenges, automated tools can play a vital role in streamlining and strengthening vendor assessments.
Tools for Automated Vendor Assessment
Manual evaluations often fall short when dealing with the complexity of today’s healthcare supply chains. They can lead to inconsistent assessments and add unnecessary strain to compliance efforts. This is where platforms like Censinet RiskOps™ come in. By automating vendor evaluations, Censinet RiskOps™ validates evidence, documents risks, and ensures alignment with NCQA, AAAHC, and TJC standards. The platform’s Censinet AI™ speeds up the process, enabling vendors to complete security questionnaires in seconds. It also summarizes evidence, identifies fourth-party risks, and generates detailed risk reports - all while maintaining oversight and scaling risk management efficiently.
A key best practice is to adopt ongoing assessments based on each vendor’s risk profile, rather than limiting evaluations to the initial due diligence stage[1]. This continuous monitoring approach aligns with accreditation standards and ensures compliance is maintained between formal survey cycles. By integrating automated tools and recurring evaluations, healthcare organizations can stay ahead of risks and meet the rigorous demands of accreditation requirements.
Using Censinet for Vendor Risk Management
Healthcare organizations face the dual challenge of maintaining accreditation and managing a wide range of vendor risks. Censinet RiskOps™ simplifies this process by centralizing vendor risk management and providing efficient tools for monitoring third-party risks. This platform takes vendor risk assessment to the next level by combining compliance needs with operational efficiency.
Censinet RiskOps™ for Accreditation Compliance
Censinet RiskOps™ features a centralized, automated dashboard that streamlines the entire data collection process, making collaboration among risk teams much easier. This allows teams to focus on addressing critical risk areas during accreditation surveys. Routine tasks like data gathering and initial assessments are automated, freeing up risk managers to concentrate on more strategic responsibilities. By consolidating vendor risk data, the platform ensures healthcare organizations can maintain a clear and comprehensive view of compliance standards for NCQA, AAAHC, and TJC requirements.
Protecting PHI and Supply Chains
When it comes to safeguarding patient data and ensuring secure supply chains, Censinet RiskOps™ offers continuous vendor monitoring tailored to each vendor's level of importance. Its adaptable framework allows organizations to choose between internal, external, or hybrid monitoring approaches, making it easier to meet both operational goals and compliance mandates.
Maintaining Accreditation Through Continuous Vendor Monitoring
To consistently comply with standards set by NCQA, AAAHC, and TJC, healthcare organizations need to maintain ongoing oversight of their vendor relationships. Accreditation isn’t just about meeting requirements at the start - it's about demonstrating continuous compliance. This level of oversight is made possible by leveraging automated tools and scalable processes, as outlined below.
Automated Monitoring and Reporting
Managing vendor compliance manually just doesn’t cut it when dealing with large networks. Automated monitoring tools provide real-time updates on vendor compliance by flagging issues like expiring certifications, security concerns, or policy violations as they arise. For example, these systems can alert risk teams when a vendor’s HIPAA compliance documents are about to expire or when a security assessment uncovers vulnerabilities requiring immediate action.
These platforms also simplify audit preparation by centralizing compliance records. They track remediation efforts, log periodic reassessments, and maintain certifications such as SOC 2 or HITRUST. With all this data in one place, organizations can easily demonstrate their ongoing vendor oversight during accreditation reviews.
Scaling Vendor Risk Management
While automation handles alerts and reporting, human expertise is still a crucial part of the process. As healthcare organizations grow their vendor networks, balancing the need for thorough oversight with increased volume becomes a challenge. Tools like Censinet AI help by automating tasks such as reviewing questionnaires, validating documentation, and summarizing risk findings. However, final decisions remain in the hands of risk professionals.
This approach, often called "human-in-the-loop", combines AI’s efficiency with human judgment. Configurable rules ensure that critical decisions - like approving high-risk vendors - always involve human review. This strategy allows risk teams to oversee a growing number of vendors effectively, ensuring compliance with NCQA, AAAHC, and TJC standards without sacrificing quality or accuracy.
Conclusion
Aligning vendor risk management with the standards set by NCQA, AAAHC, and TJC isn't just about ticking off accreditation checkboxes - it's about creating a lasting framework that prioritizes patient safety and ensures compliance over the long haul. These accrediting bodies hold healthcare organizations to high standards, demanding quality care and strict regulatory adherence, including thorough oversight of vendor relationships. When your vendor risk program incorporates credentialing checks, cybersecurity evaluations, and supply chain monitoring to meet these standards, you help your organization maintain its accreditation and safeguard its operations.
As mentioned earlier, third-party breaches are a growing concern, making continuous vendor monitoring a necessity rather than an option. The ever-changing nature of vulnerabilities means that one-time assessments are no longer sufficient to ensure ongoing compliance with NCQA, AAAHC, and TJC requirements.
An effective vendor risk management strategy ensures that third parties are held to the same high standards as your internal teams. Whether they’re supplying medical devices, managing sensitive health data, or providing clinical staff, vendors play a critical role in healthcare operations. Ensuring they meet these rigorous standards not only protects your accreditation but also reinforces patient safety.
The use of automated monitoring tools alongside human expertise allows organizations to scale their vendor oversight effectively. Automation simplifies compliance tracking and reporting, while skilled professionals retain control over key decisions. This balanced approach enables healthcare organizations to grow their vendor networks without sacrificing the standards required by accrediting bodies.
FAQs
What are the main differences in vendor risk requirements for NCQA, AAAHC, and TJC accreditation?
NCQA places a strong emphasis on quality assurance and patient safety, focusing on evaluating organizational performance through detailed criteria. AAAHC, on the other hand, caters to outpatient settings with a more adaptable approach, encouraging ongoing improvement that aligns with the unique needs of these healthcare environments. Meanwhile, TJC (The Joint Commission) concentrates on national safety and quality standards, highlighting clinical outcomes, thorough risk management, and ensuring compliance across all areas of care delivery.
What steps can healthcare organizations take to manage vendor risk and maintain accreditation?
Healthcare organizations can tackle vendor risk and maintain accreditation by taking a proactive approach. This includes conducting thorough risk assessments for all vendors, clearly outlining cybersecurity and compliance expectations in contracts, and keeping a close eye on high-risk vendors through regular monitoring. Another key step is implementing structured offboarding procedures to minimize long-term risks.
To meet accreditation standards like those set by NCQA, AAAHC, and TJC, it’s essential to integrate vendors into your organization’s cybersecurity and incident response plans. Assigning clear responsibilities for vendor management and securing leadership buy-in are also crucial steps. Using established frameworks like NIST or HITRUST, along with performing routine audits, can strengthen compliance efforts and help reduce risks effectively.
What are the advantages of using automated tools for managing vendor risks in healthcare?
Automated tools bring a host of advantages when it comes to managing vendor risks in healthcare. For starters, they simplify complex processes like onboarding and risk assessments, cutting down on manual work, reducing errors, and saving valuable time. With continuous monitoring, these tools ensure that potential risks are spotted and addressed without delay.
They also play a crucial role in helping organizations meet industry standards such as HIPAA and HITRUST. By automating documentation and reporting, these solutions make compliance tasks far less daunting. Features like risk scoring and vendor tiering allow healthcare organizations to focus their efforts on the most critical third-party risks, ensuring resources are used wisely. In short, these tools boost efficiency, improve precision, and help maintain compliance and accreditation with less hassle.


