Healthcare Business Continuity Planning: Managing Vendor Dependencies and Risks
Post Summary
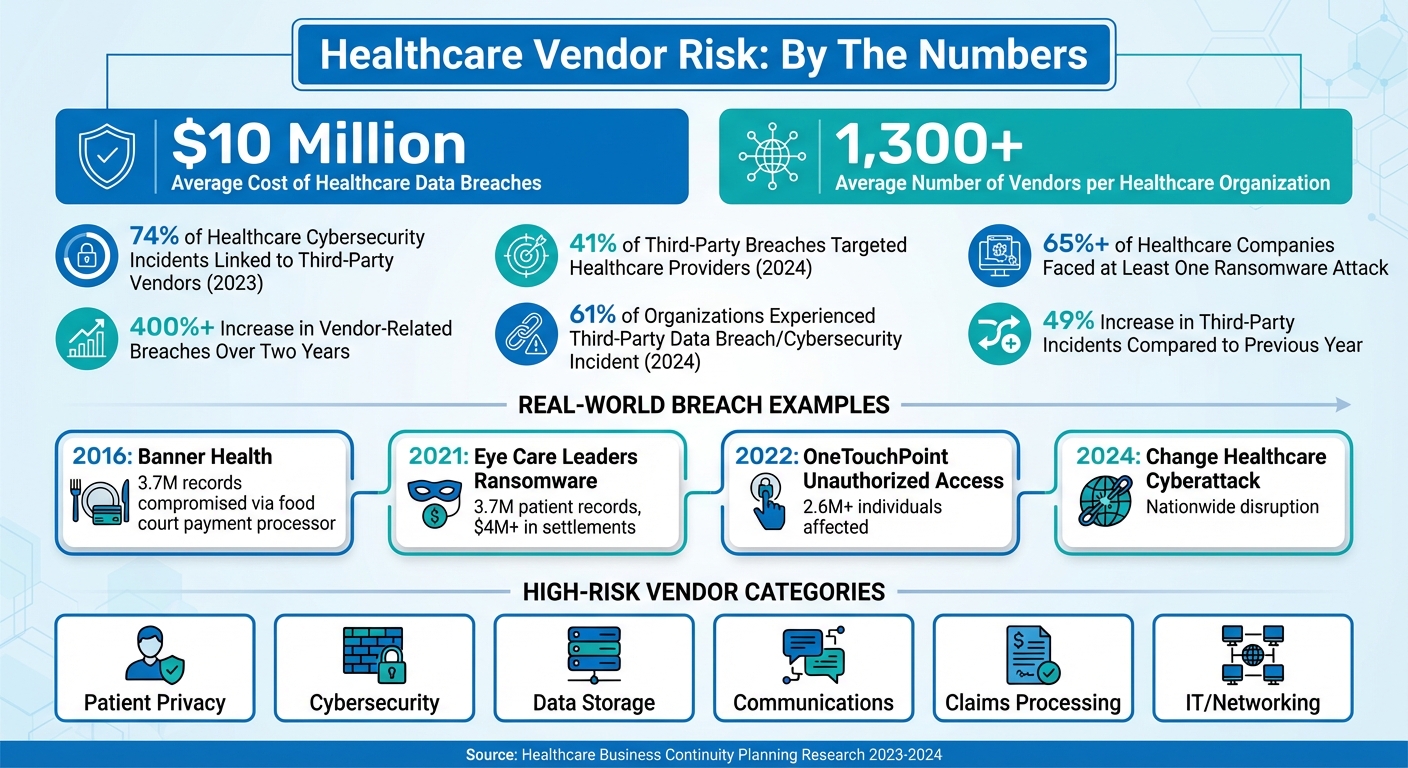
Healthcare organizations rely on over 1,300 vendors on average, making vendor management a critical part of maintaining patient care and operational stability. But this dependency also introduces risks, as evidenced by alarming statistics: in 2023, 74% of healthcare cybersecurity incidents were linked to third-party vendors, and by 2024, 41% of third-party breaches targeted healthcare providers.
Vendor failures - caused by cyberattacks, supply chain disruptions, or technical issues - can halt diagnostic tools, block access to patient records, and disrupt medication supplies. To mitigate these risks, healthcare providers must:
- Identify and prioritize critical vendors based on their impact on patient care, financial health, and operations.
- Evaluate potential disruption scenarios to understand their effect on daily operations and response timelines.
- Implement risk mitigation strategies like redundancy, vendor quality agreements, and regular audits.
- Align business continuity plans with vendors by integrating incident response protocols and conducting joint recovery tests.
Platforms like Censinet RiskOps™ simplify vendor risk management by automating assessments, monitoring risks in real time, and providing centralized oversight of vendor networks. With healthcare data breaches costing nearly $10 million on average, continuous monitoring and proactive risk management are essential to maintaining uninterrupted patient care and compliance.
Healthcare Vendor Risk Statistics and Critical Impact Areas
How to Conduct a Vendor Impact Analysis
Conducting a vendor impact analysis is all about pinpointing which vendors are essential to your organization's operations. It's not just about identifying them; it's about understanding how they affect patient care, daily operations, and financial health. The ultimate goal? To figure out where your vulnerabilities lie and allocate resources to protect those areas.
Start with a thorough third-party risk assessment. This will give you a clear picture of your vendor risk profile across every department[4].
Identifying and Prioritizing Critical Vendors
Not every vendor carries the same level of importance. For instance, a vendor managing your electronic health records (EHR) is far more critical than one supplying office furniture. To make sense of it all, classify vendors into categories like low, moderate, or critical, based on how they affect healthcare operations[4].
When evaluating vendors, focus on key factors such as:
- How much access they have to your systems
- Their potential impact on patient care and safety
- The financial consequences of a breach
- The fallout if the vendor’s business fails
A stark example of this is the 2024 Change Healthcare cyberattack, which disrupted operations nationwide. It highlighted how a failure from a third-party provider could have consequences far worse than direct attacks on hospitals[1].
The American Hospital Association emphasized, "the national consequences of cyberattacks targeting mission-critical third-party providers can be even more devastating than when hospitals or health systems are attacked directly"[1].
Certain vendor categories deserve extra scrutiny, especially those involved in patient privacy, cybersecurity, data storage, communications, claims processing, and IT/networking. These areas are directly tied to your ability to deliver care and maintain compliance. Vendors in these high-risk areas should be prioritized based on their role in patient care or revenue generation[1].
Even vendors that seem low-risk can surprise you. Take the 2016 Banner Health breach, for example. Hackers gained access to 3.7 million records through a food court payment processor. This case underscores why a comprehensive risk assessment is essential - even vendors with minimal data access can become weak points[4].
To make evaluations consistent, standardize your process. Set clear policies, risk thresholds, and scoring requirements for vendors in each risk category. For example, vendors classified as "critical" should face the same certification standards, audit schedules, and risk mitigation steps. A vendor scoring system can also help you track progress, flag potential issues, and generate reports for better decision-making[4].
Assessing Disruption Scenarios and Their Impact
Once you've identified your critical vendors, the next step is to evaluate potential disruption scenarios. What happens if one of these vendors fails? Consider a range of possibilities - system outages, cyberattacks, supply chain issues, natural disasters, or even vendor bankruptcy. For each vendor, identify which services would be affected and how quickly the disruption would ripple through your organization.
Look at both operational and financial consequences. For example, if your EHR vendor goes offline for 24 hours, how many patients would be affected? Would clinicians lose access to medication histories? Could you still admit new patients or process billing and claims? With healthcare data breaches averaging nearly $10 million in costs, the stakes are enormous[4].
Timing matters, too. Some disruptions are immediate, like a medical device vendor's system failing mid-surgery. Others, like delays from a pharmaceutical supplier, might unfold more gradually. Understanding these timelines helps you decide how much buffer time you’ll need and when to activate backup plans.
Go beyond the obvious risks. Engage all relevant departments to uncover hidden vulnerabilities that might otherwise be missed. Comprehensive risk management requires input from across the organization[4].
Finally, document everything in a way that supports decision-making. For each critical vendor, record their services, accessed systems, possible disruption scenarios, their impact on care and operations, financial risks, and current mitigation strategies. This documentation not only strengthens your business continuity planning but also provides a solid case for investing in risk mitigation measures when presenting to leadership.
Strategies for Mitigating Vendor Risks
After identifying potential disruptions, the next step is to implement strong strategies to manage vendor risks effectively[1]. This involves creating detailed mitigation plans tailored to your most critical vendors.
Creating Vendor Risk Mitigation Plans
One key approach is building redundancy into your essential systems. For instance, dual sourcing ensures you have a backup option if your primary vendor fails. Imagine your EHR system goes offline - having a secondary data access point can keep operations running and patient care uninterrupted. Focus on addressing single points of failure, but there's no need to duplicate every vendor relationship.
Another critical step is establishing vendor quality agreements. These agreements should clearly define expectations for security, uptime, and incident response. They must outline what happens during a failure - who gets notified, how quickly the vendor must act, and the steps they’ll take to resolve the issue. For example, in December 2021, Eye Care Leaders, an electronic medical record platform, fell victim to a ransomware attack that compromised around 3.7 million patient records. The attackers deleted configuration files and databases, leading to over $4 million in settlements to both patients and providers[2]. Well-structured agreements enforce accountability and ensure swift action when problems arise.
To keep vendors accountable, require regular compliance attestations and conduct periodic audits. A 2024 Third-Party Risk Management Study revealed that 61% of organizations faced a third-party data breach or cybersecurity incident - a 49% increase compared to the previous year[3]. Scheduled audits and documentation reviews help verify that vendors are adhering to agreed-upon protocols.
Aligning Business Continuity Plans with Vendors
Effective risk management also means aligning your business continuity plans with those of your vendors. This includes integrating third-party vendors into your cybersecurity measures, such as incident response plans, disaster recovery tests, and overall business continuity efforts[1]. Collaborate with critical vendors to understand their continuity strategies and identify gaps where your plans may not align.
Vendor-specific incident response plans are essential. These plans should detail notification procedures, identify affected systems, and outline communication strategies for patients, stakeholders, and regulators[2]. For instance, in April 2022, OneTouchPoint, a third-party printing and mailing vendor, experienced unauthorized system access, impacting over 2.6 million individuals and numerous healthcare providers, including Anthem, Kaiser Permanente, and Blue Cross[2]. Having a clear incident response plan ensures swift action in such scenarios.
Additionally, establish and rehearse emergency communication protocols with your vendors[1]. Conduct joint disaster recovery tests annually to identify coordination issues and refine response measures. Assign and clearly communicate cybersecurity roles and responsibilities within your organization and with vendors to prevent confusion during critical moments[1][4]. These proactive steps strengthen collaboration and enhance your ability to respond effectively to threats.
Using Censinet RiskOps for Vendor Risk Management

Managing vendor risks manually can overwhelm healthcare organizations, especially when dealing with numerous third-party relationships. Relying on disconnected tools often creates gaps that can leave organizations vulnerable at critical times. Censinet RiskOps™ offers a solution by providing a centralized platform tailored specifically for healthcare risk management.
This platform simplifies the process of assessing, monitoring, and managing vendor relationships throughout their lifecycle. Instead of juggling multiple tools, you gain a single, unified view of all third-party risks. This comprehensive perspective is crucial for business continuity planning, helping you pinpoint potential vulnerabilities across your vendor network. By consolidating these processes, Censinet RiskOps™ also enables automated assessments, making risk management more efficient and less time-consuming.
Centralizing and automating vendor risk management ensures smoother operations, even during disruptions.
Automated Vendor Risk Assessments
Traditional vendor risk assessments can be resource-intensive, often requiring significant time and effort. Censinet RiskOps™ changes this by automating tasks like questionnaires and documentation submissions. This automation reduces the workload for internal teams while ensuring consistency across all vendor evaluations.
With Censinet AI™, the process becomes even faster. Vendors can complete security questionnaires in seconds instead of weeks. The AI reviews vendor evidence and documentation, extracts key details about integrations and fourth-party risks, and generates comprehensive risk summary reports. By handling these time-consuming tasks, the platform allows your team to focus on more strategic activities.
Through automation, Censinet AI™ not only speeds up assessments but also enhances the depth of risk analysis.
AI-Powered Risk Analysis and Monitoring
Censinet AI™ takes risk management a step further with real-time insights presented through an intuitive dashboard. This centralized view aggregates data from your entire vendor ecosystem, helping you quickly identify high-risk vendors and prioritize mitigation efforts. Key findings and tasks are automatically routed to the appropriate stakeholders for review and action.
The platform strikes a balance between automation and human oversight. Configurable rules and review processes ensure your team retains control while scaling operations effectively. This approach not only accelerates response times but also strengthens your organization’s ability to maintain continuity during disruptions. With Censinet AI™, you gain the tools to manage risks proactively and confidently.
sbb-itb-535baee
Maintaining Resilience Through Continuous Vendor Monitoring
Managing vendor risks doesn’t stop after the onboarding process. Many healthcare organizations fail to prioritize ongoing vendor compliance, which can lead to vulnerabilities and violations over time [4]. Considering that over 65% of healthcare companies have faced at least one ransomware attack and the average cost of a data breach in the healthcare sector is nearing $10 million, consistent oversight is more important than ever [4].
Continuous monitoring plays a key role in identifying risks as they emerge. Achieving true visibility means understanding all connected assets and third-party relationships [3]. Without this ongoing diligence, vendor vulnerabilities can remain unnoticed, creating potential security gaps. Regular monitoring works hand-in-hand with initial risk assessments, ensuring any issues are addressed promptly.
Real-Time Vendor Performance Tracking
Continuous monitoring is just the beginning - real-time performance tracking takes it a step further by offering actionable insights. Censinet RiskOps™ supports this process by providing centralized oversight of your entire vendor ecosystem. The platform leverages external vulnerability scans and threat intelligence to identify risks as they arise [5].
To make tracking effective, establish clear metrics within your service-level agreements (SLAs). For SaaS vendors, this might include minimum system uptime requirements. For IT providers, focus on metrics like security patch deployment rates, maintenance schedules, equipment defect rates, and response times [4]. These benchmarks help you spot trends and address issues before they disrupt operations. Standardizing vendor evaluations with detailed policies, scoring systems, and risk thresholds ensures consistent monitoring across all vendor relationships [4].
This level of real-time tracking also strengthens communication and collaboration with your vendors.
Maintaining Communication and Collaboration with Vendors
Frequent communication with vendors ensures alignment on security protocols and business continuity goals. Incorporate vendors into your incident response plans, disaster recovery exercises, and business continuity strategies [1]. Establish and rehearse emergency communication procedures so every party knows their role during a crisis. This collaborative approach enhances your ability to mitigate risks and maintain operational stability.
Cybersecurity requirements should be explicitly outlined in contracts and Business Associate Agreements (BAAs). Use clear, actionable terms to define the expected security measures and specify consequences for non-compliance. Include "if-then" clauses to assign accountability in the event of a breach [1][6]. Additionally, implement a Plan of Action and Milestones (POA&M) to track and address vendor risks, ensuring all remediation efforts are completed [1]. This structured approach keeps vendors accountable and focused on meeting your security expectations.
Conclusion: Managing Vendor Dependencies for Healthcare Continuity
Vendor risk management isn't just about checking regulatory boxes - it's a critical step to keep healthcare operations running smoothly and securely. The numbers paint a stark picture: vendor-related breaches have skyrocketed by over 400% in just two years[4], and in 2024, 41% of third-party breaches impacted healthcare organizations[1]. With hospitals juggling relationships with more than 1,300 vendors on average[1], it’s clear that robust oversight is non-negotiable to protect patient data and maintain uninterrupted care.
To tackle these risks effectively, healthcare organizations need to focus on reducing vendor vulnerabilities to manageable levels. This involves conducting in-depth vendor impact analyses, crafting contracts with clear accountability measures, and ensuring vendors are fully integrated into incident response and business continuity plans. Embedding cybersecurity requirements directly into contracts and Business Associate Agreements adds another layer of protection against potential threats[1].
Consistent monitoring is the backbone of any successful vendor risk management strategy. With the average cost of a healthcare data breach nearing $10 million[4], adopting a proactive approach isn’t just smart - it’s financially essential. Real-time tracking, standardized evaluation criteria, and open communication channels help ensure vendors stay aligned with security expectations throughout the partnership.
Technology can make this process more efficient. Platforms like Censinet RiskOps™ give healthcare organizations a centralized hub to manage sprawling vendor networks. By combining automated risk assessments with AI-driven insights, these tools provide quick, scalable solutions while keeping human oversight at the core.
FAQs
How can healthcare organizations identify and prioritize their most critical vendors?
Healthcare organizations can determine their most critical vendors by assessing their influence on patient care, data protection, and operational continuity. Begin by pinpointing vendors that handle sensitive patient information, support key clinical services, or maintain essential infrastructure.
After identifying these vendors, group them into risk categories by considering factors such as their role in care delivery, cybersecurity measures, and resilience during disruptions. Allocate more resources to high-risk vendors to ensure they adhere to stringent security and compliance standards, reducing potential threats to both your organization and your patients.
What are the best strategies for managing third-party vendor risks in healthcare?
To address risks associated with third-party vendors, begin with thorough due diligence. This involves assessing their reliability, security measures, and adherence to healthcare regulations. Clearly defined contracts are essential - lay out roles, responsibilities, and detailed security expectations to safeguard sensitive information.
Next, prioritize ongoing monitoring of vendor performance and potential risks. Use tools or frameworks specifically designed to meet healthcare requirements. Standardize vendor management processes, including conducting regular risk assessments and implementing a secure offboarding procedure when the partnership concludes. These measures help maintain smooth operations and protect essential services, even during unexpected disruptions.
Why is continuous vendor monitoring important for healthcare business continuity?
Continuous vendor monitoring plays a key role in keeping healthcare operations running smoothly. It provides real-time insights into vendor performance and security, allowing organizations to spot weaknesses early and tackle risks before they escalate. This kind of vigilance helps reduce the likelihood of data breaches, service disruptions, and compliance violations.
By staying ahead of potential issues, healthcare providers can protect patient care and essential services, ensuring that any disruptions are handled quickly without affecting the delivery of quality healthcare.
Related Blog Posts
- Clinical Continuity Planning: Ensuring Patient Care During Vendor Disruptions
- The AWS Outage Exposed Cloud Vulnerabilities - What It Means for Healthcare Business Continuity
- Clinical Continuity Planning: Ensuring Patient Care During Vendor Disruptions
- Healthcare Supply Chain Vendor Risk: Disruption Prevention and Contingency Planning


