Healthcare Facilities Management Vendor Risk: Safety, Compliance, and Operations
Post Summary
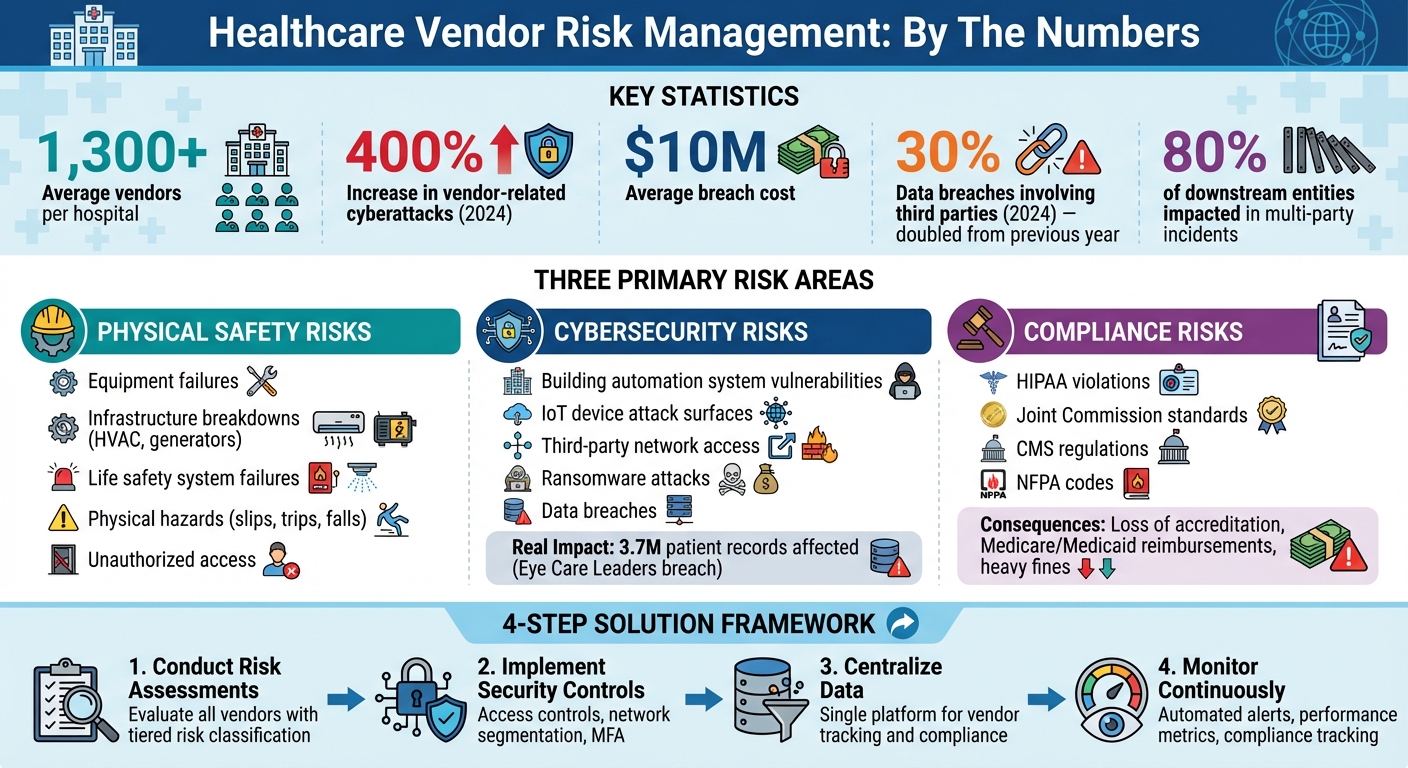
Managing vendors in healthcare facilities is a high-stakes challenge. With over 1,300 vendors per hospital on average, risks tied to physical safety, cybersecurity, and compliance can directly affect patient care, legal obligations, and operational continuity. In 2024, vendor-related cyberattacks on healthcare grew by 400%, with average breach costs nearing $10 million. This article outlines how healthcare organizations can mitigate these risks through structured vendor management programs, centralized data systems, and continuous monitoring.
Key Takeaways:
- Types of Risks: Physical safety (equipment failures, hazards), cybersecurity (breaches in building systems), and compliance (HIPAA, CMS, NFPA standards).
- Impact: Disruptions to patient care, legal penalties, and reputational damage.
- Solutions:
- Conduct detailed risk assessments for all vendors.
- Implement secure access controls and network segmentation.
- Use centralized platforms to track vendor data, compliance, and performance.
- Automate monitoring and risk evaluations with tools like Censinet RiskOps™.
- Action Steps: Define clear vendor policies, classify risks, monitor performance, and ensure secure offboarding processes.
By focusing on these strategies, healthcare leaders can better safeguard their facilities, patients, and compliance standing.
Healthcare Vendor Risk Management Statistics and Key Risk Areas
Primary Risk Areas in Facilities Vendor Management
When managing facilities vendors, three main areas of risk come into play: physical safety, cybersecurity, and compliance. Each of these can lead to operational disruptions with serious consequences. Physical safety risks arise when critical infrastructure fails - think of an HVAC system breaking down in a sterile surgical suite, emergency generators not functioning during a power outage, or life safety systems failing during an evacuation. Cybersecurity risks, on the other hand, stem from vulnerabilities in connected building management systems, which could allow attackers to access sensitive data or disable essential services. Lastly, compliance risks involve meeting the strict requirements from HIPAA, CMS, The Joint Commission, and NFPA codes, which demand constant oversight of your vendor network. Let’s break down each of these risk areas further.
Physical Safety Risks in Healthcare Facilities
Failures in infrastructure don’t just inconvenience healthcare operations - they can put lives at risk. Natural disasters or even criminal actions can damage facilities, causing delays and adding to recovery costs. For example, stolen computing equipment containing unsecured protected health information creates a direct risk that vendors must address.
Equipment malfunctions are another critical concern. A diagnostic machine that isn’t properly maintained can lead to unnecessary tests or even missed diagnoses. On top of that, physical hazards like slips, trips, and falls - whether due to construction work or poor maintenance - pose immediate dangers to both patients and staff. To address these risks, healthcare organizations must ensure that every vendor, from cleaning crews to physical security providers, maintains high safety standards and thorough documentation throughout their operations. And while these physical risks are evident, digital vulnerabilities bring their own set of challenges.
Cybersecurity Risks in Building and OT Systems
The rise of building automation and IoT devices has expanded the potential attack surface for cyber threats. A single weak link in a vendor’s system can open the door for attackers to infiltrate internal networks. The statistics are alarming: in 2024, nearly 30% of data breaches involved a third party, doubling the rate from the previous year [4]. Back in 2019, 41% of healthcare facilities reported breaches, often tied to phishing schemes, system flaws, or poorly managed third-party vendors [5].
Real-world examples highlight the severity of these risks. In December 2021, a ransomware attack on Eye Care Leaders - an electronic medical record platform - affected 3.7 million patient records and led to settlements exceeding $4 million. Similarly, in April 2022, OneTouchPoint, a third-party printing and mailing vendor, experienced a breach that compromised the data of over 2.6 million individuals, exposing patient names, addresses, medical records, and test results [4]. Even when offboarding vendors, cybersecurity risks remain. Organizations may forget to revoke vendor access, or vendors might fail to delete patient data as required by HIPAA. Additionally, interconnected systems mean that issues like power outages, cyberattacks, or HVAC failures can have cascading effects if vendors haven’t implemented proper safeguards.
Regulatory and Compliance Requirements
Healthcare organizations bear the full responsibility of ensuring their entire vendor network complies with regulations. This includes facilities contractors, who must meet the standards set by laws like HIPAA and the HITECH Act. These regulations extend to third-party Business Associates, with non-compliance resulting in severe penalties. Upcoming HIPAA updates in 2025 will impose even stricter cybersecurity standards for facilities vendors.
Beyond HIPAA, The Joint Commission enforces protocols for life safety systems, emergency management, and overall care environments. CMS regulations require healthcare providers to maintain safe physical environments and robust emergency preparedness plans. NFPA codes also play a key role, governing the installation and maintenance of fire safety systems, emergency power, and building infrastructure. Failing to meet these regulatory requirements can lead to serious consequences. For instance, a failed Joint Commission survey could jeopardize accreditation, CMS violations might result in losing Medicare and Medicaid reimbursements, and HIPAA breaches can lead to hefty fines and significant damage to patient trust and organizational reputation.
Creating a Vendor Management Program for Healthcare Facilities
Building a vendor management program requires a well-structured approach that tackles physical safety, cybersecurity, and regulatory compliance. With vendor-related incidents potentially causing serious financial and operational disruptions, establishing a solid program is not just important - it’s necessary. The foundation lies in involving the right stakeholders, setting clear policies, and organizing vendor data into a centralized system. Key elements such as governance, standardized policies, and centralization form the core of a successful vendor management program.
Governance and Cross-Department Collaboration
Managing vendor risks effectively is not a task for a single department. It demands input from multiple areas, including facilities management, IT, compliance, legal, procurement, and executive leadership [1]. Each of these groups brings a unique perspective, from understanding operational dependencies to identifying cybersecurity risks and ensuring contractual obligations are met.
To avoid confusion, assign specific roles and responsibilities early on. Designate who has the authority to make vendor-related risk decisions. For instance, when a facilities vendor needs approval or an issue arises, everyone involved should know exactly who to turn to. This clarity ensures smoother operations and faster problem resolution.
Establishing Policies and Standards for Vendor Risk
Your vendor risk policies should clearly outline how vendors are evaluated, categorized, and monitored. One effective approach is to implement a tiered risk system - classifying vendors as low, medium, high, or critical risk based on factors like data sensitivity, service importance, and system integration [1][4]. For example, a janitorial service with no access to systems might be low risk, while an HVAC vendor managing building automation systems connected to your network would likely fall into the high or critical category.
Document specific security requirements, onboarding steps, and monitoring schedules for each tier. Use standardized evaluations with clear definitions, scoring criteria, and risk thresholds to ensure consistency. Additionally, policies should require ongoing monitoring and periodic reassessments, with the frequency determined by the vendor’s risk level [1][5].
Centralizing Vendor Data and Risk Information
Centralizing vendor data is crucial for managing both operational challenges and cybersecurity risks. Relying on scattered spreadsheets can lead to oversight issues and delays. Instead, use a centralized platform to consolidate vendor inventories, risk assessments, compliance records, and performance metrics. This “single source of truth” ensures that decision-makers have access to the same, up-to-date information when addressing regulatory updates, vendor concerns, or emerging threats.
According to Compyl, "Centralized information sharing is a must for healthcare organizations. Decision-makers need to communicate with each other about regulatory updates, vendor issues, security concerns, necessary policy changes, and emerging threats. What one department misses may raise red flags for another because of a broader perspective" [1].
A centralized system should also track vendor certifications, compliance attestations, assessments, and audit results. Automated alerts for expiring documents or escalating risks can help organizations stay ahead of potential problems.
Risk Assessment and Monitoring Processes for Facilities Vendors
Risk assessment and monitoring are the cornerstones of managing vulnerabilities in your vendor network. These processes build on your vendor management program by evaluating specific risks tied to each vendor and tracking their performance over time. Facilities vendors, in particular, present distinct challenges. They often have physical access to buildings, might connect to building automation systems, and can directly affect patient safety. Your evaluation and monitoring efforts should reflect these unique considerations, forming the foundation for the security and performance measures discussed below.
Tailoring Risk Assessments for Facilities Vendors
Start by cataloging all facilities vendors, even those whose risks may seem minimal at first glance. Vendors like janitorial or landscaping services could still pose threats if they have access to sensitive areas or data [6][1]. While nearly 80% of organizations have a formal vendor risk assessment program, about 30% lack dedicated staff to manage this task [6], leading to potential gaps in evaluations.
When assessing vendors, focus on three key areas: physical safety, cybersecurity, and operational dependency. For example, an HVAC vendor managing building automation systems demands a more detailed evaluation than a groundskeeping team. HVAC vendors often connect to networks, control environmental systems critical to patient care, and may handle sensitive facility data. Assess their network security measures, access controls, and overall practices. These evaluations directly inform the security and operational measures you'll need to implement.
Strengthening Security and Operational Controls
One critical step is network segmentation. By isolating building automation systems, HVAC controls, and other operational technology (OT) from your primary clinical network, you can limit the potential fallout if a vendor's credentials are compromised.
For vendors requiring system access for maintenance or monitoring, secure remote access protocols are a must. Use multi-factor authentication, restrict access to specific times and systems, and log all vendor activities. Ensure identity management systems can immediately revoke access when contracts end or personnel changes occur.
Physical access controls are just as important for facilities vendors. Track who enters your buildings, when they arrive, and which areas they access. Badge systems, sign-in logs, and escort policies for high-security zones help reduce the risk of unauthorized entry and maintain accountability.
Monitoring Vendor Performance and Compliance
Once security controls are in place, continuous monitoring of vendor performance and compliance is essential. Threats and compliance standards evolve, so staying proactive is key. For high-risk vendors, real-time monitoring can flag suspicious activities like unusual log-ins, unexpected traffic patterns, or unauthorized actions [1]. This is crucial, especially considering that in 2024, nearly one-third (30%) of data breaches involved third parties - double the rate of the previous year [4].
"Many businesses fall short in evaluating vendor compliance after onboarding. A year is a long time, and you can't afford to allow vulnerabilities or compliance violations to creep in." – Compyl [1]
Define clear performance metrics in your Service Level Agreements (SLAs). For facilities vendors, these could include system uptime requirements, emergency repair response times, equipment defect rates, and timely completion of scheduled maintenance [1]. Consistently track these metrics and address any deviations immediately.
To ensure compliance, monitor HIPAA-related audit violations, their severity, and completed corrective actions [1]. Depend on ongoing certifications and reports - like HITRUST certification, SOC 2 Type II annual reports, or ISO 27001 - rather than relying solely on point-in-time assessments. Where possible, conduct independent audits of key vendors, as third-party reports may not always provide the full picture [1].
Implement a Plan of Action and Milestones (POA&M) to manage remediation efforts for identified risks. This plan should outline tasks, required resources, milestones, and completion dates [2]. Such a structured approach ensures accountability and prevents issues from being overlooked.
Finally, use anomaly detection tools to identify unusual vendor behavior early, such as irregular access patterns or unexpected system changes [3]. This is especially critical given that downstream entities impacted by multi-party incidents outnumber primary victims by over 800% [6]. Proactive monitoring protects not only your organization but also your patients and partners.
sbb-itb-535baee
Using Technology Platforms for Vendor Risk Management
Trying to manage vendor risks manually across different departments - like facilities, IT, and compliance - can lead to delays and leave vulnerabilities in your security measures. By building on centralized vendor data and governance practices, technology platforms now bring risk monitoring and management under one roof. These platforms turn vendor risk management from a scattered, reactive process into a streamlined, proactive system.
Automating Risk Assessments and Monitoring Workflows
Automation takes the hassle out of repetitive tasks like sending out questionnaires and scoring assessments. For example, Censinet RiskOps™ simplifies vendor risk management by automating assessments across IT, operational technology (OT), and facilities domains. It uses a centralized repository to store all vendor documentation, making everything accessible in one place [7][8].
With tools like Censinet AI, vendors can complete security questionnaires in seconds, while the platform summarizes documentation and generates easy-to-understand risk reports. Importantly, automation doesn’t replace human oversight - it complements it. Risk teams stay in control by setting customizable rules and reviewing automated processes to ensure decisions are well-informed.
Continuous monitoring adds another layer of protection, offering real-time visibility into vendor performance and compliance. The platform sends alerts when security risks change or new vulnerabilities arise. By integrating with third-party risk intelligence sources, it provides timely insights into a vendor’s ethical practices, financial stability, security posture, and compliance status [7]. This approach helps organizations catch potential problems as they develop, rather than waiting for scheduled reviews.
Improving Collaboration Between Risk Management Teams
Managing vendor risks effectively in healthcare settings means teamwork between facilities managers, IT security staff, compliance officers, and procurement teams. Centralized platforms make collaboration easier by giving everyone access to the same risk data through shared dashboards and workflows [9]. For instance:
- Facilities teams can check cybersecurity risks tied to building automation vendors.
- IT teams can monitor physical access risks.
- Compliance officers can stay updated on regulatory changes and vendor issues in real-time.
Censinet RiskOps™ ensures accountability by directing assessment results and related tasks to the appropriate stakeholders. Its consolidated dashboards present vendor performance, compliance levels, and risk scores in one view, keeping all teams on the same page. These tools not only improve communication but also provide the foundation for actionable, data-driven decisions.
Using Data and AI for Program Improvement
AI and data-driven tools take vendor risk management to the next level by validating evidence, drafting policies, and spotting risk trends. Building on earlier governance and monitoring frameworks, AI insights help refine processes over time [9]. For example, Censinet AI analyzes assessment data to uncover integration details and fourth-party risks, offering a deeper understanding of the vendor network.
The platform’s risk dashboard acts as a central hub, pulling together real-time data to manage policies, risks, and tasks. With access to a collaborative network of healthcare organizations and over 50,000 vendors, Censinet RiskOps™ continuously reduces vendor risk [9]. As more data flows through the system, AI models become better at predicting risks and suggesting mitigation strategies, making the program stronger with each passing day.
Conclusion and Next Steps
Managing vendor risks in healthcare facilities isn't just about ticking off compliance boxes - it’s about protecting patients and ensuring smooth operations. With numerous vendors and a steady stream of breaches making headlines, healthcare leaders need to take vendor risk management to a higher level.
Overview of Risks and Mitigation Approaches
Healthcare facilities face vendor risks in four key areas: physical safety, cybersecurity, regulatory compliance, and operational continuity. Physical safety risks might involve unauthorized access or equipment malfunctions that could jeopardize patient or staff safety. Cybersecurity threats, on the other hand, often target building automation systems or operational technology, creating vulnerabilities for hackers to exploit. Compliance risks demand strict adherence to HIPAA, Joint Commission standards, and state regulations, especially when vendors handle sensitive data. Operational risks could disrupt critical services if vendors fail to deliver or unexpectedly terminate relationships.
Real-world incidents highlight the importance of conducting thorough risk assessments, maintaining constant monitoring, and establishing standardized evaluation processes for every vendor partnership.
How Technology Platforms Support Vendor Risk Management
Technology platforms offer healthcare organizations a way to simplify and enhance vendor risk management. For example, Censinet RiskOps™ unifies fragmented processes into a streamlined, automated system. By centralizing vendor data, it provides real-time insights into vendor performance, improving collaboration across departments like IT, compliance, and procurement.
Censinet AI takes efficiency up a notch by enabling vendors to complete security questionnaires in seconds, validating evidence, and generating detailed risk reports. Its risk dashboard aggregates real-time data, helping organizations manage policies, monitor risks, and track tasks - all while maintaining the essential human oversight that healthcare demands.
Practical Steps for Healthcare Leaders
To tackle vendor risks effectively, healthcare leaders can take the following steps:
- Conduct detailed risk assessments before onboarding vendors and schedule regular evaluations based on their risk profiles.
- Set clear expectations for cybersecurity and compliance by embedding strong contractual requirements with defined consequences for non-compliance.
- Monitor vendors continuously to identify and address potential problems as they arise.
- Plan secure offboarding processes, including removing access, changing passwords, deactivating badges, and confirming data destruction [1][2].
- Adopt technology platforms to automate workflows, centralize vendor data, and transform vendor risk management into a proactive, patient-centered approach.
FAQs
What steps can healthcare facilities take to assess and manage vendor risks effectively?
Healthcare facilities can tackle vendor risks effectively by beginning with a detailed risk assessment. This means examining vendors based on key factors such as how sensitive the data they handle is, their impact on daily operations, and their ability to meet regulatory requirements. After this evaluation, vendors can be grouped into different risk levels, making it easier to focus oversight where it's most needed.
To keep operations safe and compliant over time, facilities should consider using established frameworks like NIST or HITRUST. Adding continuous performance monitoring and setting up clear contractual agreements can further strengthen their approach. Regularly conducting due diligence and staying in close communication with vendors are also essential steps to reduce disruptions and ensure everything runs smoothly.
What are the biggest cybersecurity risks healthcare vendors pose?
Healthcare vendors bring with them a range of cybersecurity challenges, such as data breaches, ransomware attacks, and supply chain vulnerabilities. These risks often arise due to weak security measures, mishandling of sensitive patient information, or inadequate oversight of vendor systems.
On top of that, insider threats - whether through deliberate actions or unintentional mistakes - can expose critical data. Poorly secured vendor systems can also act as gateways for cybercriminals to infiltrate healthcare networks. To address these concerns, healthcare organizations need to ensure vendors follow stringent security protocols and consistently evaluate their compliance with industry standards.
How can centralized platforms enhance vendor risk management in healthcare facilities?
Centralized platforms make vendor risk management more efficient by bringing all vendor-related information into one system. This setup provides clearer insights into potential risks, simplifies vendor evaluations, supports ongoing monitoring, and enhances team communication. As a result, healthcare organizations can better align with industry regulations.
By organizing workflows and minimizing overlooked risks, these platforms help protect sensitive data, ensure uninterrupted operations, and keep patient safety at the forefront while managing vendor relationships more effectively.
Related Blog Posts
- Building Vendor Risk Frameworks for Healthcare IT
- Healthcare Vendor Risk Management Framework: Templates, Tools, and Best Practices
- Healthcare Benchmark Study Reveals Vendor Risk Management Consumes 20% of IT Resources
- Long-Term Care Facility Vendor Risk Management: Resident Safety and Regulatory Compliance


