Healthcare IT Infrastructure Vendor Risk: Network, Security, and System Reliability
Post Summary
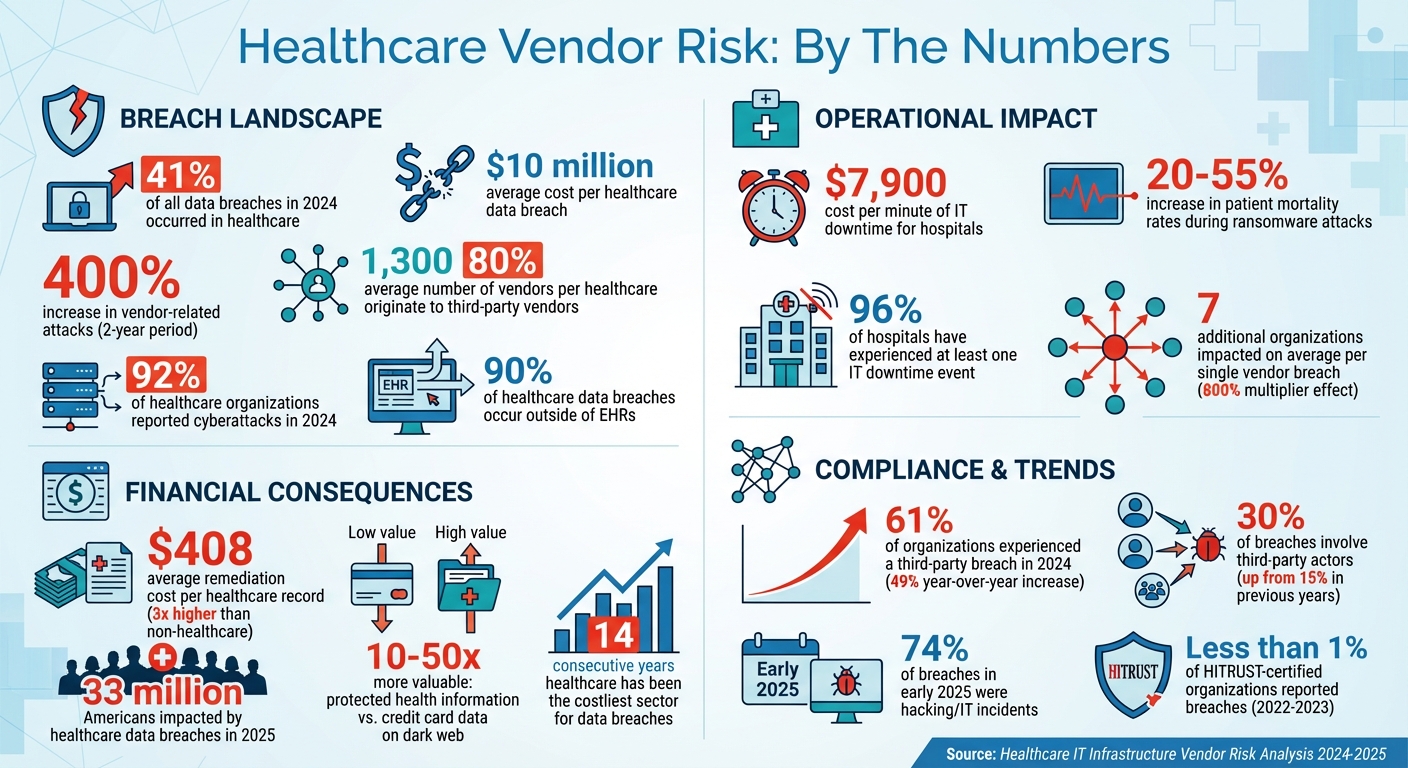
Healthcare organizations face growing risks from their IT vendors. With over 1,300 vendors per organization on average, these partnerships introduce vulnerabilities that can jeopardize patient safety, disrupt operations, and lead to costly data breaches. In 2024, healthcare experienced 41% of all data breaches, with vendor-related attacks increasing by 400% in just two years. The average cost of a breach? Nearly $10 million.
Key risks include:
- Cybersecurity threats: 80% of stolen patient records originate from third-party vendors, often due to inadequate defenses.
- System reliability issues: IT downtime costs hospitals $7,900 per minute and can delay care, increasing patient mortality rates by up to 55% during ransomware attacks.
- Compliance challenges: HIPAA regulations hold healthcare organizations accountable for vendor failures, with stricter rules introduced in 2025.
To address these challenges, healthcare providers must implement structured vendor risk management strategies. This includes using frameworks like HITRUST or NIST CSF, enforcing strong contract terms, conducting regular audits, and monitoring vendor performance. Tools like Censinet RiskOps™ can simplify these processes, offering real-time risk visibility and automated workflows.
The stakes are high. Vendor risk management isn’t just about protecting data - it’s critical to maintaining patient care and trust.
Healthcare Vendor Risk Statistics: Breaches, Costs, and Impact Data 2024-2025
Network Vulnerabilities from Healthcare IT Vendors
How Vendor Networks Create Cyber Risks
Third-party vendors often serve as weak links in healthcare networks, offering entry points that cybercriminals can exploit. Instead of targeting heavily secured hospital systems, attackers focus on vendors with less robust defenses - such as billing companies, outsourced IT providers, and medical device manufacturers [3]. Once they gain access to these vendor networks, attackers can move laterally into critical systems that house patient data and manage care operations.
Shockingly, 80% of stolen patient records now come from third-party vendors rather than directly from hospitals [4]. Even more alarming, 90% of healthcare data breaches occur outside of electronic health records, often through systems managed by vendors [4]. Traditional perimeter defenses are no longer sufficient. A single breach in a vendor's network can ripple through entire healthcare systems, disrupting operations and compromising the data of millions of patients [4].
Vendors are appealing targets for attackers because they often have extensive access to healthcare networks but weaker security measures. Issues like outdated encryption, poor access controls, and unpatched systems create vulnerabilities that sophisticated cybercriminals can exploit. Unfortunately, standard Business Associate Agreements (BAAs) have proven ineffective against these advanced threats [4].
These risks aren't just theoretical. They’ve led to real-world breaches with significant consequences, as the following examples demonstrate.
Healthcare Network Breach Examples
Vendor-related breaches have catastrophic financial and operational consequences. Healthcare remains the most targeted industry for cyberattacks and continues to endure the highest breach costs - marking it as the costliest sector for the 14th straight year [4]. In 2024 alone, 92% of healthcare organizations reported cyberattacks, with 33 million Americans impacted by data breaches in 2025 [4].
The fallout from these breaches often extends far beyond the initial target. In fact, downstream entities affected by multi-party incidents outnumber the primary victims by more than 800% [5]. On average, a single vendor-related breach impacts seven additional organizations, creating a web of disruption that requires extensive coordination to manage [4]. Adding to the urgency, protected health information is highly valuable - fetching 10 to 50 times more than credit card data on dark web marketplaces [4]. This makes healthcare vendor networks an irresistible target for financially motivated attackers.
Security Threats from Vendor Relationships
Common Vendor Security Risks
Vendor relationships often open the door to a variety of security vulnerabilities, making them prime targets for cybercriminals. One of the most destructive threats is ransomware, which frequently arises during attacks on vendors with weaker security measures. In early 2025, hacking and IT-related incidents were responsible for nearly 74% of breaches, affecting 90% of the individuals impacted [8].
A major issue lies in many vendors' reliance on outdated systems, inadequate security protocols, and weak authentication processes - even when they have privileged access to sensitive healthcare data. Modern software compounds this risk, as 70–90% of its components are often sourced from open-source or third-party libraries, significantly expanding the attack surface [10]. Supply chain attacks have surged, doubling since April 2025 to an average of 26 incidents per month [10]. The 2025 Verizon Data Breach Investigations Report highlights that third-party involvement in breaches has risen to 30%, a sharp increase from 15% in earlier years [10].
The financial impact is staggering: remediation costs for healthcare records average $408 per record, nearly three times higher than the cost for non-healthcare records [7]. According to a 2024 Third-Party Risk Management Study, 61% of organizations reported experiencing a third-party data breach or cybersecurity incident - a 49% year-over-year increase [9]. Even smaller healthcare providers are not spared; 83% of 1,300 surveyed physician practices reported falling victim to cyberattacks [6].
These vulnerabilities not only inflate the financial burden of breaches but also expose organizations to severe regulatory consequences.
Regulatory and Compliance Consequences
When vendors fail to secure their systems, the fallout extends beyond financial losses, triggering harsh regulatory and compliance penalties. Under HIPAA regulations, healthcare organizations are held accountable for the security failures of their third-party associates [2]. This means that even if a breach originates from a vendor, the healthcare organization bears the responsibility.
The regulatory environment is becoming increasingly strict. HIPAA, for instance, is undergoing its first major updates in over a decade. These changes propose removing the distinction between "required" and "addressable" controls, making previously optional security measures mandatory [11]. Organizations will also need to perform annual compliance audits and address risks posed by emerging technologies like AI and quantum computing [11]. In February 2025 alone, more than 46 large breaches were reported to the Department of Health and Human Services Office for Civil Rights, affecting over 1.2 million individuals [8].
When a vendor-related breach occurs, healthcare organizations must notify affected patients, conduct forensic investigations, implement corrective measures, and endure extended regulatory scrutiny. Beyond fines and penalties, these incidents can severely damage an organization's reputation, eroding patient trust and straining business relationships. With 41% of third-party breaches in 2024 impacting healthcare organizations [1] - and the average hospital working with over 1,300 vendors [1] - the compliance challenges can quickly become overwhelming, especially for those relying on outdated, rules-based risk management strategies.
System Reliability Challenges with IT Vendors
Downtime and Performance Risks
Failures in healthcare IT systems can wreak havoc on patient care and hospital operations. A staggering 96% of hospitals have faced at least one IT downtime event, with almost a quarter of these lasting over eight hours [14]. The financial impact is equally alarming - unplanned IT downtime costs healthcare organizations an average of $7,900 per minute [14].
The causes of such disruptions vary widely and are often unpredictable. For example, in July 2024, a faulty software update from CrowdStrike's Falcon cybersecurity software caused network issues in 759 out of 2,232 U.S. hospitals, affecting 34% of them [12]. This error resulted in 1,098 network disruptions, with 21.8% impacting patient-facing services and 15.4% affecting operational areas [12]. While most services were restored within six hours (58.1%), some outages stretched beyond 48 hours, affecting 7.8% of cases [12].
Beyond the financial strain, system failures directly threaten patient safety. Ransomware attacks in 2024 compromised the records of 25.6 million patients across the U.S. [13]. A University of Minnesota study revealed that during ransomware attacks, patient mortality rates increase by 20%, with the most severe incidents leading to a mortality spike of 36–55% among already admitted patients [13]. When IT systems fail, healthcare providers are forced to revert to manual procedures, increasing the risk of errors [12][13].
"The most critical consequence: delayed care, errors in treatment, or missed diagnoses due to unavailable data. This directly impacts clinical outcomes." - Affiliated Resource Group [14]
Physical infrastructure issues can be just as devastating. On December 26, 2022, a water leak caused an electrical fire that disabled an electronic health record (EHR) system for 48 hours, disrupting operations for over a week [15].
These incidents highlight the importance of proactive vendor oversight to safeguard patient safety and maintain operational continuity.
Methods for Maintaining System Uptime
Given these risks, healthcare organizations must take proactive steps to ensure system reliability. One of the most effective tools is a well-defined Service Level Agreement (SLA). These agreements outline specific uptime guarantees, maximum allowable downtimes, response times for critical incidents, and penalties for non-compliance. By setting measurable standards, SLAs hold vendors accountable for their performance.
Continuous performance monitoring is another critical strategy. Real-time systems that track server response times, application performance, network latency, and resource usage can help detect early signs of trouble. If a vendor's systems start showing signs of decline, such as slower response times or increased error rates, organizations can step in before minor issues escalate into major failures.
Redundancy planning is equally important. This involves maintaining backup systems, creating failover protocols, and documenting manual downtime procedures. Regular disaster recovery drills ensure that these plans are effective and that staff are well-prepared to handle emergencies.
Finally, regular vendor performance reviews help maintain accountability and track long-term reliability trends. These reviews should measure incident frequency and severity, compare actual uptime against SLA commitments, evaluate response times, and analyze root causes of past failures. If a vendor consistently underperforms, healthcare organizations must escalate their concerns, renegotiate contracts, or consider switching to a more reliable partner.
sbb-itb-535baee
Vendor Risk Assessment Frameworks
Healthcare organizations need a structured approach to evaluate vendor risks, ensuring vulnerabilities are identified, controls are assessed, and compliance with regulations is maintained [16][17].
Different frameworks offer unique methods for identifying risks. For instance, HITRUST CSF weaves risk identification into compliance assessments [17]. NIST CSF focuses on understanding the business context, pinpointing critical assets, and addressing vendor-related cybersecurity risks [17]. Meanwhile, ISO 27001 emphasizes managing information security risks through an Information Security Management System (ISMS) [16]. The impact of these frameworks is clear - fewer than 1% of HITRUST-certified organizations reported security breaches between 2022 and 2023 [17].
Many organizations combine HIPAA requirements with frameworks like ISO 27001 to bolster their vendor risk strategies [16]. The choice of a framework depends on factors like organizational goals, industry demands, and compatibility with existing systems [16]. As Gaurav Kapoor, co-CEO of MetricStream, notes:
"For example, healthcare organizations need to be HIPAA-compliant because they're dealing with very private patient information" [16].
This foundation enables organizations to implement risk tiering and automation for more efficient vendor management.
Using HITRUST, NIST CSF, and ISO 27001

Each of these frameworks offers distinct advantages for evaluating risks related to networks, security, and reliability:
- HITRUST CSF: Specifically designed for healthcare, it integrates HIPAA requirements with other security standards and provides a detailed control catalog. This makes it highly effective for safeguarding patient data and ensuring clinical systems remain secure.
- NIST CSF: Known for its flexibility, it uses five core functions - Identify, Protect, Detect, Respond, and Recover - to help organizations assess their cybersecurity posture and prioritize improvements without being tied to a specific vendor.
- ISO 27001: This international standard establishes a formal ISMS, emphasizing continuous improvement. It’s particularly useful for demonstrating due diligence in vendor selection and oversight, especially in healthcare’s complex regulatory landscape.
Choosing the right framework depends on an organization’s specific needs. For example, some healthcare providers prioritize HITRUST for its healthcare focus but may also incorporate NIST CSF for operational technology vendors or ISO 27001 for international suppliers. Consistently applying the selected framework ensures uniformity in risk assessments across vendor relationships.
Vendor Tiering by Data Sensitivity
Not every vendor poses the same level of risk. A cloud provider managing electronic health records is far riskier than a vendor supplying office furniture. By categorizing vendors based on the sensitivity of the data they handle and their operational impact, healthcare organizations can allocate resources efficiently. This approach places greater scrutiny on high-risk vendors while simplifying assessments for lower-risk ones.
Vendors are typically classified into tiers:
- Critical vendors: These include those managing protected health information (PHI), supporting life-critical systems, or maintaining network infrastructure. They require thorough assessments, frequent audits, and continuous monitoring.
- High-risk vendors: These may handle payment data, access internal networks, or support essential operations.
- Medium- and low-risk vendors: These generally have limited data access and minimal operational impact.
"If a cloud service provider is storing patient data and they aren't HIPAA-compliant, it doesn't matter how good their general cybersecurity looks. You're still on the hook", explains Michael Herrick, Founder and HIPAA risk analyst at HIPAA for Humans [16].
Risk tiers aren’t fixed. Vendors initially considered low-risk may shift to higher-risk categories if their roles expand to include handling sensitive data or supporting regulated activities. Regular reassessment ensures that tiering reflects current risks as vendor relationships evolve [16].
Using Censinet RiskOps™ for Vendor Assessments
Automation can dramatically streamline vendor risk assessments, which can otherwise be a resource-heavy process. Censinet RiskOps™ simplifies this by automating workflows and centralizing vendor risk data into a single platform.
The system provides real-time visibility into the security status of third-party relationships. Automated processes, powered by Censinet AI™, reduce assessment timelines from weeks to days. Vendors are guided through tasks like completing questionnaires, collecting evidence, and submitting documentation, all while human oversight ensures critical decisions remain in the hands of risk teams. The platform’s AI summarizes vendor evidence, highlights product integration details, identifies fourth-party risks, and generates concise risk reports. Configurable rules and review processes keep decision-making firmly under human control.
Censinet RiskOps™ also offers benchmarking tools, enabling organizations to compare vendor security practices against industry averages and peer performance. Dashboards highlight urgent risks, while trend analysis flags vendors with declining security postures. This data-driven approach transforms vendor risk management into a proactive strategy for safeguarding patient safety and maintaining operational stability.
Methods for Reducing Network, Security, and Reliability Risks
Once vendor risks are identified, healthcare organizations need to take proactive steps to address them. This involves using well-defined contract terms, collaborating on incident response plans, and maintaining continuous monitoring. Let’s break down these strategies.
Contract Terms and Audit Rights
Contracts should clearly outline vendor responsibilities and establish penalties for failing to meet technical standards or for security breaches [1].
But it’s not just about compliance. Vendors should also be required to actively participate in the organization's cybersecurity efforts. This includes collaborating on incident response planning, running disaster recovery tests, and contributing to business continuity plans [1].
Additionally, contracts should grant periodic audit rights, allowing organizations to verify that vendors remain compliant over time [9].
Joint Incident Response Planning
Even with strong contracts in place, a vendor-related security incident can disrupt healthcare operations in an instant. That’s why having a coordinated incident response plan is non-negotiable [1].
Both the healthcare organization and its vendors need clearly defined roles and responsibilities when it comes to cybersecurity. This ensures everyone knows what to do during an incident, reducing confusion and delays [1]. Vendors should maintain detailed incident response plans and undergo regular audits to confirm these plans are functional and up to date [9]. During contract discussions, organizations should evaluate the vendor's response capabilities to ensure they align with internal protocols. This alignment is critical for minimizing disruptions to patient care and speeding up recovery efforts.
Ongoing Monitoring and Risk Scoring
Continuous monitoring is essential for keeping tabs on vendor performance. Metrics like system uptime, patch management, and incident response times provide valuable insights into a vendor's security posture.
Regular audits and reassessments are equally important. These help organizations detect changes that could stem from issues like budget cuts, staff turnover, or an expanded attack surface. By catching these shifts early, healthcare providers can address vulnerabilities before they jeopardize critical systems.
Tools like Censinet RiskOps™ simplify this ongoing process. Its dashboards spotlight urgent risks and track performance trends, while its benchmarking features allow organizations to compare vendor practices against industry standards. This data-driven approach moves vendor oversight from a one-off task to a continuous effort, helping to safeguard patient safety and maintain operational stability.
Conclusion
Healthcare organizations must take vendor risk management seriously. With 41% of third-party breaches in 2024 affecting healthcare organizations and the average hospital relying on over 1,300 vendors [1], the stakes are incredibly high. These breaches go beyond IT concerns - they're patient safety issues that can jeopardize critical services and expose sensitive health data.
The Change Healthcare breach serves as a stark reminder of how devastating attacks on mission-critical third-party providers can be, as highlighted by the American Hospital Association [1].
Addressing these risks demands a well-rounded strategy. This includes conducting thorough vendor assessments using frameworks like HITRUST and NIST CSF, establishing clear contract terms with audit rights, planning joint incident response measures, and continuously monitoring vendor performance. Organizations should focus on their most critical vendors, integrate cybersecurity requirements into contracts, and maintain oversight with regular audits and risk scoring.
Effective tools can simplify this process. For example, Censinet RiskOps™ streamlines vendor risk management by providing dashboards that flag urgent risks, track performance, and benchmark vendor practices against industry standards. Additionally, Censinet AI™ speeds up assessments, allowing vendors to complete security questionnaires in seconds, all while retaining essential human oversight for critical decisions.
Vendor risk management isn’t just a regulatory requirement under HIPAA - it’s a crucial step in protecting patient care. By taking proactive measures, organizations can secure their networks, strengthen defenses, and ensure reliable systems that support patient safety.
FAQs
What steps can healthcare organizations take to reduce cybersecurity risks from vendors?
Healthcare organizations can better protect themselves from vendor-related cybersecurity risks by conducting thorough risk assessments before entering partnerships. Regularly monitoring vendors' security practices and ensuring they comply with regulations like HIPAA are key steps in this process. It's also important to include clear security requirements in contracts and perform routine audits to confirm compliance.
Focusing on high-priority vendors, creating incident response plans that involve vendor collaboration, and leveraging automated tools can simplify risk management efforts. When a vendor relationship ends, having proper offboarding procedures in place is essential to address any potential vulnerabilities. These practices help secure healthcare IT systems while keeping operations running smoothly.
How can vendor-related IT failures impact patient safety in healthcare?
Vendor-related IT failures can pose significant risks to patient safety. They can result in data breaches, which expose sensitive patient information, or disrupt essential healthcare operations like accessing medical records or running diagnostic systems. Such interruptions can delay treatment, potentially leading to harmful or even life-threatening situations for patients.
On top of that, system outages or reliability problems can interfere with communication among healthcare providers, making patient care even more challenging. This makes it clear that strong vendor risk management is crucial for keeping operations running smoothly and safeguarding patient well-being.
Why is managing vendor risk essential for healthcare compliance and protecting patient data?
Managing vendor risk in healthcare is essential for protecting sensitive patient information, staying compliant with regulations like HIPAA, and ensuring seamless operations. Taking a proactive stance on vendor risks helps healthcare organizations minimize the chances of cybersecurity threats, prevent data breaches, and steer clear of expensive legal or financial setbacks.
A strong vendor risk management strategy also ensures that third-party partners adhere to stringent industry standards, which plays a key role in safeguarding patient safety and maintaining the reliability of healthcare IT systems. This not only reinforces trust but also supports long-term stability in an environment where regulatory demands are high.


