Healthcare Quality Reporting and Vendor Risk: Ensuring Data Integrity
Post Summary
Healthcare organizations in the U.S. face major challenges in maintaining data integrity, especially when working with third-party vendors. These vendors are deeply involved in managing patient data, electronic health records (EHRs), and analytics platforms - key components of healthcare quality reporting. However, weak vendor risk management can lead to data breaches, compliance violations, and disruptions in patient care.
Key Takeaways:
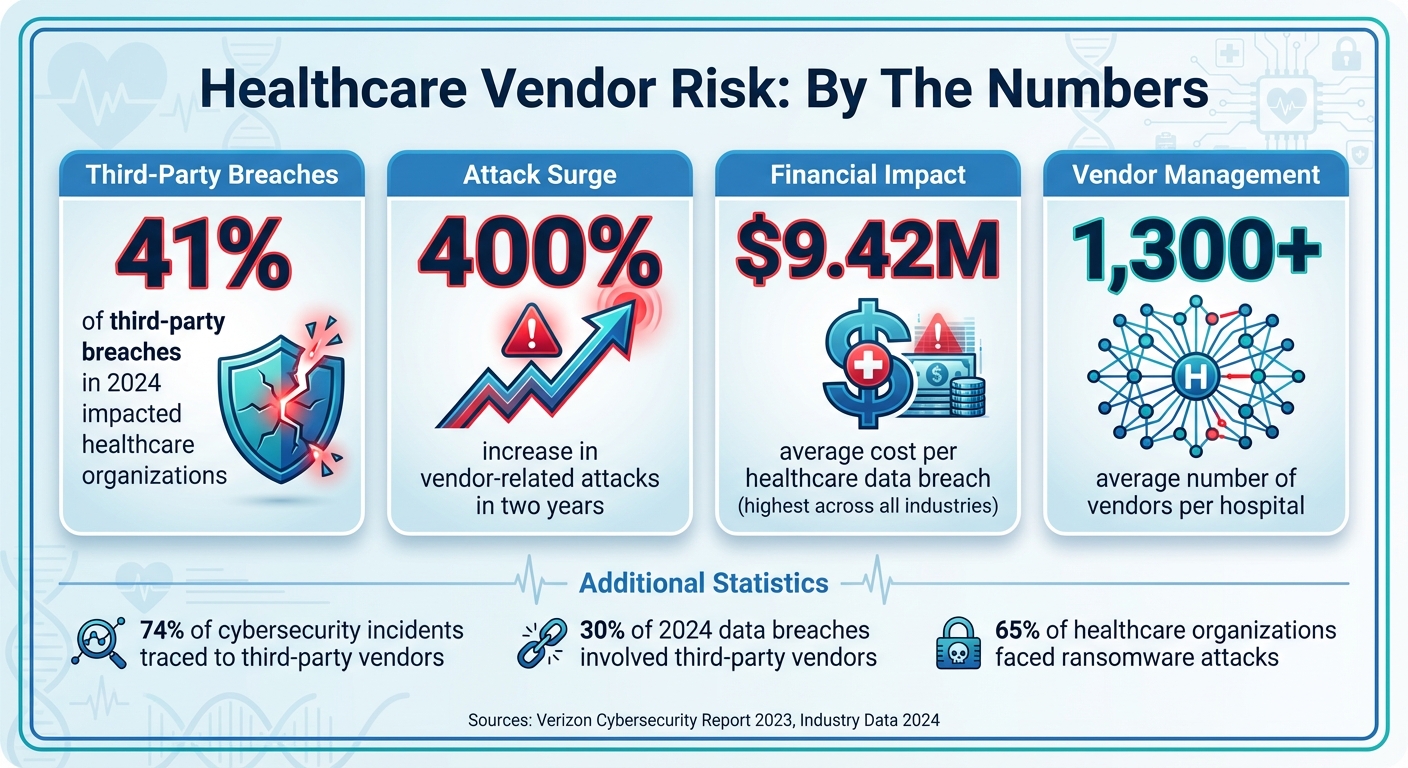
- Vendor Risks Are Growing: 41% of third-party breaches in 2024 impacted healthcare organizations, with vendor-related attacks surging by 400% in two years.
- Financial Impact: Data breaches cost healthcare an average of $9.42 million per incident, the highest across industries.
- Patient Safety at Stake: Compromised data can lead to flawed clinical decisions and jeopardized care.
- Internal Weaknesses: Poor governance and lack of continuous vendor oversight increase vulnerabilities.
Solutions for Healthcare Organizations:
- Pre-Contract Evaluations: Assess vendor security certifications like SOC 2 and HITRUST before signing agreements.
- Stronger Contracts: Include enforceable clauses for data integrity, security, and offboarding procedures.
- Continuous Monitoring: Use tools like Censinet RiskOps™ to track vendor performance and flag risks in real-time.
- Governance Integration: Make vendor risk management a part of quality oversight to align with regulatory requirements like HIPAA.
Third-party vendors are critical to healthcare operations, but they also introduce risks that cannot be ignored. A structured approach to vendor risk management is essential to safeguard data integrity, protect patient safety, and ensure compliance with strict reporting standards.
Healthcare Vendor Risk Statistics: Breach Impact and Costs 2024
How Vendor Risk Compromises Data Integrity in Quality Reporting
Where Vendors Introduce Risk in the Quality Data Lifecycle
Vendors play a role in nearly every phase of the healthcare data lifecycle, and each stage brings its own set of risks to data integrity. At the data capture stage, errors can arise during initial recording and input by EHR providers, medical device software vendors, telehealth platforms, or third-party labs integrated with EHR systems. Even patient engagement platforms - like those used for appointment reminders and messaging - can contribute to these issues. According to the 2023 Verizon Cybersecurity Report, 74% of cybersecurity incidents or unauthorized access in healthcare were traced back to third-party vendors [6].
In the data aggregation and storage stage, companies like AWS, Microsoft Azure, and Google Cloud Platform, along with IT and networking vendors, handle large volumes of patient information. Problems like system outages, unauthorized access, or incomplete data transfers at this stage can corrupt entire datasets. The processing phase introduces additional risks, as billing, coding, and claims management services transform raw data into reportable formats. Finally, during the reporting stage, third-party vendors may inadvertently expose sensitive data to unauthorized access or even data loss. These vulnerabilities collectively threaten the accuracy and reliability of healthcare quality reporting.
The Impact of Vendor-Caused Data Integrity Problems
When vendors fail to safeguard data integrity, the fallout can ripple across financial, operational, and patient safety areas. A striking example occurred in April 2022, when OneTouchPoint, a third-party printing and mailing vendor, experienced unauthorized access that exposed sensitive information for over 2.6 million individuals and impacted dozens of healthcare providers. The breach revealed patient names, addresses, medical records, and test results [2]. Similarly, the 2024 Change Healthcare attack compromised data for 100 million individuals, disrupting critical systems like electronic prescribing, claims submission, and payments. The Office of Civil Rights described the incident as having an "unprecedented impact on patient care and privacy" [6].
Healthcare data breaches are not just disruptive - they’re incredibly costly. On average, a single breach costs $9.42 million, the highest among all industries [4]. Beyond financial losses, compromised data can lead to incorrect quality scores, triggering audits and penalties. For instance, the Eye Care Leaders ransomware attack in December 2021 affected about 3.7 million patient records. The company faced over $4 million in settlements to affected patients and providers [2]. These technical failures often expose deeper operational weaknesses, exacerbating vulnerabilities within organizations.
Internal Gaps That Increase Vendor Risks
Many healthcare organizations struggle with internal governance, which amplifies vendor risks. Without a modern data governance framework, maintaining data quality in today’s complex cloud and AI-driven environments becomes a daunting task. Inconsistent security measures across departments create exploitable gaps, while the absence of clear data quality policies makes it difficult to evaluate vendor performance or hold them accountable for failures.
Additionally, manual processes and lack of coordination between IT, compliance, and clinical teams lead to sporadic, rather than continuous, vendor oversight. These internal shortcomings directly compromise the reliability of quality reporting. Alarmingly, in 2024, nearly 30% of data breaches involved third-party vendors, a sharp increase from the previous year [2]. This underscores the urgent need for stronger internal governance to address these growing risks effectively.
Building a Vendor Risk Management Framework for Healthcare
Key Components of a Vendor Risk Management Framework
Creating a vendor risk management framework to protect healthcare quality reporting starts with categorizing vendors based on their risk level. This involves evaluating their access to Protected Health Information (PHI) and their importance to quality reporting processes. By doing so, organizations can ensure that sensitive data is safeguarded through strong controls, maintaining the integrity of their reporting systems.
The framework should align with established guidelines like the NIST Cybersecurity Framework and ISO 27001 [5]. It’s essential to integrate security, risk management, and compliance functions into the process. As technology evolves - particularly with advancements like AI - new tools and endpoints introduce additional risks, making it crucial for risk management strategies to adapt [5]. These classifications also pave the way for more robust contractual protections.
Contract and Legal Protections for Data Integrity
Contracts and Business Associate Agreements (BAAs) should include precise, enforceable cybersecurity requirements. Using "if-then" clauses can ensure compliance and accountability [3]. Unfortunately, many healthcare organizations overlook this critical language, leaving them exposed when incidents occur.
Contracts should also define data quality Service Level Agreements (SLAs) with measurable performance targets. For instance, SaaS vendors might be required to maintain minimum system uptime, while IT providers could be held to specific timelines for security patches, maintenance, and resolving priority issues. Programs like Adobe's Vendor Security Review Program and Microsoft's SSPA Program set an example by requiring vendors to adhere to industry standards and agree to ongoing security evaluations [1]. Key metrics such as HIPAA compliance rates, the number of violations, issue severity, and corrective action completion from periodic audits are essential [1].
Equally important are detailed offboarding procedures. Contracts must outline steps for securely returning or destroying data, revoking access, and conducting final security audits when the vendor relationship ends [3][1]. This process should include tasks like removing access permissions, changing passwords, deactivating physical security badges, revoking network access, and obtaining a signed statement from the vendor confirming the destruction of patient records [1]. Platforms like Censinet RiskOps™ reinforce these practices by streamlining and enforcing such risk management protocols.
Using Censinet RiskOps™ for Risk Management

Censinet RiskOps™ simplifies vendor risk management by centralizing assessments through automated workflows combined with human oversight. It offers real-time dashboards to monitor vendor security, ensuring a proactive approach to risk management.
Censinet AI™ enhances this process by speeding up third-party risk assessments. Vendors can quickly complete security questionnaires, while the system automatically summarizes their evidence and documentation, highlights product integration details, and identifies fourth-party risk exposures. It generates detailed risk summary reports based on assessment data, helping risk teams address complex vendor risks efficiently. With advanced routing and orchestration tools, Censinet RiskOps™ acts like "air traffic control" for governance and risk management - directing critical findings and tasks to the right stakeholders for review and approval. This creates a streamlined, unified approach to managing vendor risks.
Solutions to Protect Data Integrity Across Vendor Ecosystems
Pre-Contract Due Diligence and Vendor Assessments
Before signing any vendor agreements, it's essential to evaluate the potential risks tied to access levels, the sensitivity of the data involved, and the criticality of the services provided[3][2]. Start by requesting detailed security documentation, such as SOC 2, ISO 27001, or HITRUST certifications. Carefully review these materials for any exceptions, qualified opinions, or remediation plans, and assess whether these issues could directly affect your specific use case[2].
"Without this in-depth evaluation, you risk overlooking critical vulnerabilities." - Pondurance[3]
Use open-ended questions in vendor questionnaires to uncover risks that might otherwise go unnoticed[3]. Be alert for warning signs like outdated audits, vague answers, or incomplete documentation. If anything seems inconsistent or misaligned with your risk profile, don't hesitate to ask follow-up questions[2]. To streamline your efforts, categorize vendors based on the sensitivity of the data they handle and the level of integration they have with your systems. This allows you to focus your attention on the most critical relationships[3][2].
"This isn't about mistrusting vendors. It's about building transparent, accountable partnerships where both sides are committed to security." - Steve Ryan, Senior Manager of BARR's Attest Services Practice and Head of BARR's Healthcare Services[2]
Once due diligence is complete, reinforce these measures with a structured onboarding process.
Implementation Controls and Vendor Onboarding
A consistent and standardized onboarding process is key to avoiding data integrity issues. Clearly outline expectations in contracts and codes of conduct, ensuring compliance with regulations like HIPAA, your organization's security policies, and requirements for promptly reporting security incidents or breaches[8][9]. Business Associate Agreements (BAAs) should clearly define the vendor's services and their HIPAA obligations, with regular reviews to keep them up to date[1].
Centralize the onboarding process by using a supplier portal. This portal can streamline registration, documentation, and security updates, ensuring consistency across all vendors[8]. Additionally, give suppliers controlled access to update their own records. This not only improves data accuracy but also reduces administrative overhead[8].
Continuous Monitoring and Reassessment
Once vendors are onboarded, ongoing monitoring becomes critical to managing risks effectively. For high-risk vendors, implement real-time monitoring systems to flag unusual activity, such as suspicious logins or unexpected traffic patterns[1]. This is increasingly important, as vendor-related attacks have surged by over 400% in the past two years, and 41% of third-party breaches in 2024 impacted healthcare organizations[1][3].
Conduct periodic risk assessments tied to each vendor's risk level[1]. Only accept certifications like HITRUST, SOC 2 Type 2, and ISO 27001 that reflect ongoing compliance rather than a one-time evaluation[1]. Develop a vendor scoring system with measurable metrics, such as minimum SaaS uptime, IT security patch rates, and HIPAA compliance levels. This helps you track vendor performance and address potential issues before they escalate[1]. Don't forget to include fourth-party risks (subcontractors) in your evaluations to ensure the entire supply chain is secure[1].
Use a Plan of Action and Milestones (POA&M) to document and track remediation efforts for any identified risks. This should include resources, milestones, and deadlines for completion[3]. Regularly review audit trails to monitor data changes - keeping track of who made modifications, when, and why. This ensures accountability throughout your relationship with the vendor[10][7].
sbb-itb-535baee
Connecting Vendor Risk Management to Quality Governance and Compliance
Adding Vendor Risk to Quality Governance
Quality committees shouldn't view vendor risk as just an IT issue - it needs to be part of their broader oversight responsibilities. By incorporating vendor performance indicators alongside quality metrics, committees can identify risks that could impact patient safety or compromise data accuracy. This approach allows for smarter decisions, like renegotiating contracts or tightening controls, which directly support data integrity across reporting systems.
Centralizing vendor risk data gives quality governance teams a clearer picture of which vendors to work with, which contracts may need adjustments, and where stronger controls are necessary. This transforms vendor risk management from a routine checklist into a strategic tool that drives quality improvement efforts. By embedding vendor risk into quality oversight, organizations are better positioned to meet stringent regulatory standards.
Meeting Regulatory Requirements Through Vendor Risk Management
Managing vendor risk isn’t just good practice - it’s a compliance necessity under regulations like HIPAA. It also supports adherence to frameworks such as GDPR, PCI DSS, and Medicare-Medicaid Conditions of Participation [1]. A solid vendor risk management program ensures third parties follow the laws and maintain the required security levels for handling protected health information. Through a systematic review of vendor risks, healthcare organizations can show auditors and regulators that they’re taking meaningful steps to protect patient data and ensure uninterrupted services [11].
How Censinet AI Enables Continuous Oversight

Censinet AI simplifies vendor risk assessments, making compliance and oversight easier to manage. It automates critical tasks like gathering vendor documentation, highlighting integration specifics, and identifying fourth-party risks.
What sets it apart is its human-in-the-loop model, where automation supports decision-making rather than replacing it. With customizable rules and review processes, risk teams stay in control while scaling their operations to handle increasingly complex vendor relationships. Acting as a centralized hub, Censinet AI routes key findings and tasks to the right stakeholders for review and approval. Additionally, Censinet RiskOps consolidates all AI-related policies, risks, and tasks, strengthening proactive monitoring and compliance efforts outlined earlier.
Conclusion
Vendor risk poses a direct threat to critical aspects of healthcare, including data integrity, patient safety, and regulatory compliance. With the average hospital managing relationships with over 1,300 vendors and 41% of third-party breaches in 2024 impacting healthcare organizations, the potential for vulnerabilities has grown immensely [3]. Every vendor connection is a possible gateway for data breaches, which can lead to flawed clinical decisions and jeopardized patient safety [10].
The numbers paint a stark picture: vendor-related attacks have surged by more than 400% in just two years, and over 65% of healthcare organizations have faced at least one ransomware attack [1]. The fallout from these incidents includes hefty lawsuits, financial penalties, operational disruptions, and a loss of trust. As the American Hospital Association warns:
"The national consequences of cyberattacks targeting mission-critical third-party providers can be even more devastating than when hospitals or health systems are attacked directly" [3].
Given these escalating risks, solutions like Censinet RiskOps™ offer a lifeline by simplifying and strengthening threat management. This platform automates compliance tasks, standardizes vendor evaluations, and continuously monitors the vendor ecosystem, reducing the chances of breaches and ensuring governance teams stay informed. With Censinet AI, risk assessments that once took weeks can now be completed in seconds, highlighting critical issues for stakeholders and providing full visibility - even into fourth-party risks that are often overlooked.
Incorporating robust vendor risk management into a quality governance framework is no longer optional - it’s essential. Protecting data integrity requires a proactive strategy that integrates vendor oversight into broader patient safety and quality initiatives. By holding every third party to the same high standards, healthcare organizations can better safeguard patient outcomes and maintain compliance in an increasingly complex landscape. A unified approach to vendor risk management is key to meeting these challenges head-on.
FAQs
What steps should healthcare organizations take to evaluate a vendor’s security before signing a contract?
Healthcare organizations can assess a vendor's security by conducting thorough due diligence. This process involves reviewing security questionnaires, performing risk assessments, and verifying compliance certifications like HITRUST, SOC 2, or ISO 27001. It's equally important to examine the vendor's cybersecurity measures and request supporting documentation, such as security certifications and insurance policies, to ensure robust protection.
For ongoing security, organizations should outline clear cybersecurity requirements and incident response responsibilities within contracts and Business Associate Agreements (BAAs). Regular monitoring and periodic reassessments are key to staying compliant and addressing new risks as they arise.
What key stages in healthcare quality reporting are most vulnerable to vendor-related risks?
Healthcare data integrity faces potential threats at various critical points. For instance, during system integration, errors or misconfigurations can lead to inaccuracies in data. Cybersecurity threats are another major concern, as breaches or unauthorized access can put sensitive patient information at risk. Moreover, medical device vulnerabilities, such as outdated software or systems lacking necessary patches, can open the door to data tampering or even loss.
Recognizing these risks allows healthcare organizations to take proactive steps to protect data integrity and maintain dependable reporting.
How does Censinet RiskOps™ support real-time vendor risk management and ensure data integrity?
Censinet RiskOps™ streamlines vendor risk management by automating critical tasks such as onboarding, risk assessments, and ongoing monitoring. This automation enables organizations to quickly pinpoint and mitigate potential security threats, safeguarding sensitive information and staying compliant with regulations.
By taking a proactive stance, Censinet RiskOps™ helps ensure that healthcare quality reporting stays both accurate and secure, reducing risks tied to third-party vendors. This allows healthcare organizations to prioritize delivering excellent care while maintaining trust and meeting regulatory requirements.


