Healthcare Supply Chain Vendor Risk: Disruption Prevention and Contingency Planning
Post Summary
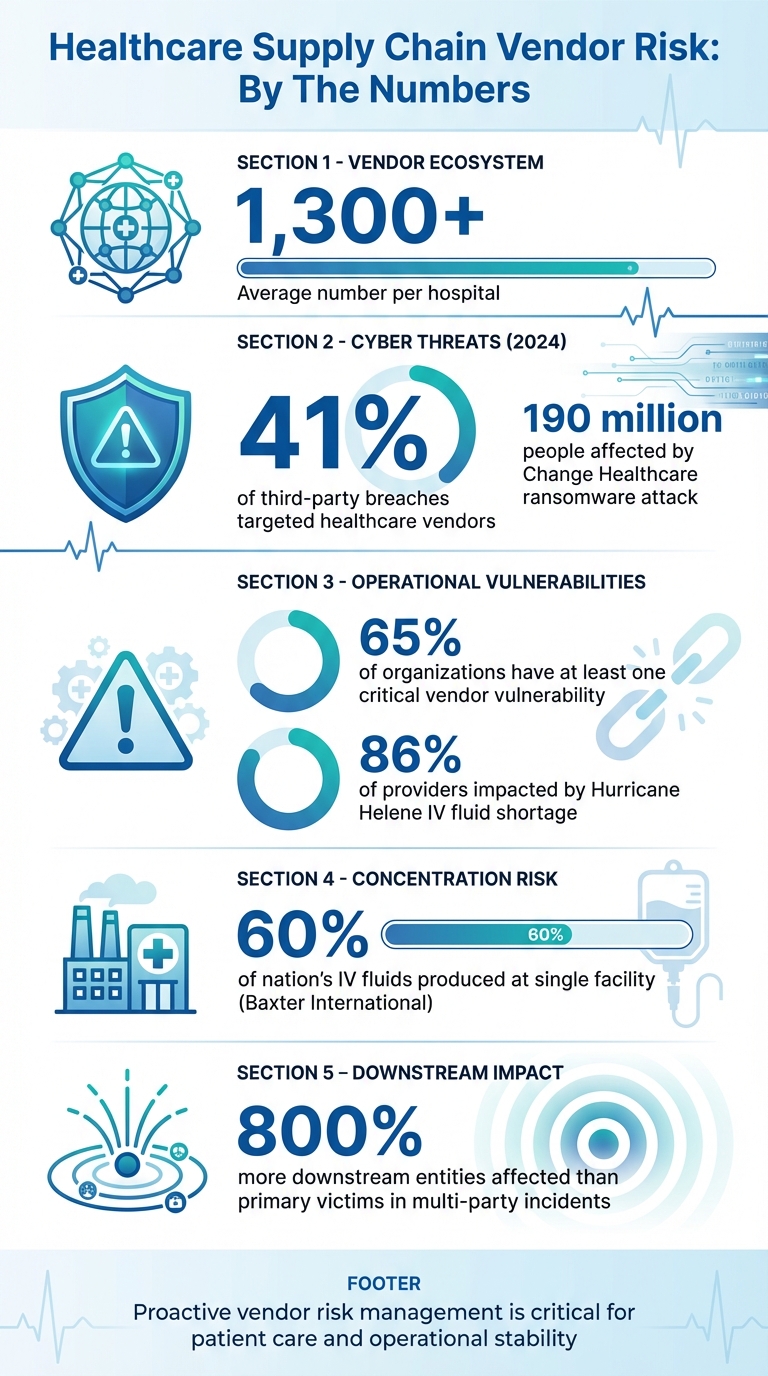
Healthcare supply chains are under constant pressure from cyberattacks, natural disasters, and operational failures. Hospitals rely on over 1,300 vendors, making disruptions a serious threat to patient care and financial stability. In 2024, 41% of third-party breaches targeted healthcare vendors, with incidents like a ransomware attack compromising data for 190 million people. Physical disruptions, such as Hurricane Helene flooding a key IV fluid production plant, led to nationwide shortages impacting 86% of providers.
Key Takeaways:
- Cyber threats and single points of failure are major risks.
- 65% of organizations report at least one critical vendor vulnerability.
- Weak vendor risk management leaves healthcare providers exposed.
To mitigate these risks:
- Centralize vendor inventories to track dependencies and risks.
- Prioritize vendor risks by categorizing based on criticality.
- Strengthen contracts with clear security and accountability clauses.
- Develop and test contingency plans for vendor failures.
- Coordinate incident response with vendors for faster recovery.
Healthcare Vendor Risk Statistics and Impact 2024
Common Vulnerabilities in Healthcare Supply Chains
Healthcare supply chains face numerous challenges that can disrupt operations and jeopardize patient care. Identifying these weak spots is essential for creating a stronger, more reliable system.
Cybersecurity Risks in Vendor Networks
Vendor networks are a prime target for cyberattacks, including ransomware, phishing, and data breaches [2]. Alarmingly, 41% of breaches in 2024 were linked to third-party networks [2], and ransomware incidents more than doubled between 2022 and 2023, affecting over 250 organizations [1].
One of the most striking examples occurred in 2024 when a ransomware attack on Change Healthcare compromised the data of 190 million individuals. This attack disrupted billing systems for thousands of providers and delayed reimbursements as healthcare teams scrambled to access critical patient information [1]. In another case, a cyberattack on a blood center forced providers across several southern states to implement emergency blood conservation and prioritization protocols [1].
These cybersecurity risks are just one layer of the vulnerabilities affecting healthcare supply chains.
Operational Risks: Single Points of Failure
Over-reliance on a small number of suppliers or facilities - referred to as concentration risk - can create critical single points of failure. A study found that 65% of organizations have at least one such vulnerability in their supply chains [1].
Take, for instance, Hurricane Helene in late 2024. The storm caused severe flooding at Baxter International's North Carolina plant, which produced 60% of the nation’s IV fluids. This disruption led to a nationwide shortage, impacting 86% of healthcare providers. The FDA had to step in, authorizing emergency imports to address the crisis. It wasn’t until February 2025 that the plant resumed normal production levels [1].
"The deeply layered healthcare supply chain not only creates interdependencies but leads to limited transparency that then elevates risk. Transportation, storage, logistics, and controls all have potential flashpoints. Conversely, concentration risk arises in scenarios where there are few critical areas or underlying infrastructures. If these areas are compromised, it can have a widespread impact", explained Paul Mee, Joshua Shi, and Scott Bartley of Oliver Wyman [1].
These operational challenges highlight the importance of addressing vulnerabilities at every level of the supply chain.
Gaps in Current Vendor Risk Management
Many healthcare organizations struggle with weak vendor relationships and ineffective risk management practices [2]. Business associate agreements often lack enforceable terms to address technical requirements, like data encryption, leaving organizations exposed. Vendor risk assessments, in many cases, devolve into check-the-box exercises rather than meaningful safeguards. This lack of focus spreads resources thin across a sprawling vendor ecosystem, making it harder to prioritize critical partners [2].
Midsized healthcare organizations face even steeper obstacles due to limited resources. Common issues include incomplete vendor inventories, inadequate due diligence during onboarding, and failure to incorporate vendors into core cybersecurity measures like incident response and disaster recovery plans [2]. These gaps not only increase the risk of cyberattacks but also leave organizations ill-prepared to handle disruptions when they occur.
Strategies for Vendor Risk Management
Tackling vulnerabilities in vendor relationships requires a thoughtful and organized approach. For healthcare organizations, this means shifting from a reactive stance to a proactive strategy that prioritizes risk mitigation and ensures smoother operations.
Creating a Centralized Vendor Inventory
Many healthcare organizations struggle to maintain a clear view of their vendor ecosystem. Without a centralized inventory, identifying risks or understanding how vendors impact critical operations becomes nearly impossible. Digital tools can play a key role in continuously monitoring vendor risks [1].
"While leading healthcare organizations are at the forefront of exploring local solutions to mitigate supply chain threats, they often lack the data, supplier insight, and tools to confidently identify and gauge the interconnected risks." – Oliver Wyman [1]
To address this, organizations should create a centralized inventory that outlines each vendor's services, data access, system dependencies, contract terms, and security posture. This comprehensive overview helps uncover dependencies, spot potential concentration risks, and make informed decisions about vendor relationships. Tools like Censinet RiskOps™ simplify this process by offering a centralized platform for maintaining inventories and automating risk monitoring. With a complete vendor picture, resources can be allocated more effectively based on the criticality of each vendor.
Vendor Tiering and Risk Prioritization
Trying to manage risks equally across a large vendor network isn’t practical. For context, the average hospital works with more than 1,300 vendors [2]. Risk-based tiering provides a way to focus on the vendors that pose the greatest threats to operations and patient care.
The process begins by categorizing vendors based on their criticality and exposure to risk. High-priority vendors are often those that support essential clinical services or represent single points of failure. By using this tiered approach, organizations can concentrate their resources where they’re needed most [1].
Security and Resilience in Vendor Contracts
Once vendor risks are prioritized, it’s crucial to formalize expectations through well-structured contracts. These agreements strengthen vendor relationships while reducing the likelihood of disruptions. Contracts and Business Associate Agreements should clearly define cybersecurity requirements, specifying the necessary security controls and assigning accountability [2]. Including "if-then" clauses ensures vendors are held responsible for meeting these standards [2].
Long-term contracts should also include flexibility clauses, allowing renegotiation in response to unexpected events, such as major tariff changes that could impact market conditions [4]. Additionally, contracts should outline offboarding procedures, such as data return or destruction, access termination, and final security audits. These measures help protect organizations even after a vendor relationship ends [2].
sbb-itb-535baee
Developing Vendor Contingency Plans
Even with thorough contracts and detailed risk assessments, disruptions can still happen. The difference between a minor hiccup and a full-blown crisis often lies in preparation. Healthcare organizations must create contingency plans that outline how to respond when critical vendors fail.
Mapping Vendors to Clinical Services
Using a complete inventory of vendors, healthcare organizations should map each vendor to the clinical services they support. This step is key to prioritizing contingency planning. Start by identifying the vendors that are most essential to your operations - those that have the greatest impact on patient care and revenue [2]. This mapping process helps organizations understand how integrated each vendor is in daily operations and sets the groundwork for determining acceptable downtime limits.
Recent disruptions have highlighted the importance of identifying critical vendors and defining how long operations can tolerate downtime. Leverage digital tools and AI-driven platforms to perform risk assessments that uncover deep connections within your supply chain and provide context for various risks [1].
Testing and Improving Contingency Plans
A contingency plan that hasn’t been tested is as good as useless. Regularly conduct scenario planning by simulating crises like natural disasters, cyberattacks, or supply chain shortages to evaluate your response strategies and operational workflows in real-time [1]. These exercises should involve cross-functional teams, including procurement, IT, and clinical operations, to ensure all perspectives are considered [1].
Organizations that use scenario planning tools like predictive analytics are twice as likely to avoid supply chain disruptions compared to their peers [5]. Incorporate critical vendors into incident response plans, disaster recovery tests, and business continuity exercises, and rehearse these protocols frequently [2]. Regular training and drills help teams prepare for real-world challenges [1]. Leading organizations also conduct "stress tests" to identify vulnerabilities, benchmark against best practices, and analyze lessons learned from past disruptions [5].
Once plans are refined, clear communication and coordination with vendors during incidents become the next priority.
Coordinating Incident Response with Vendors
Effective communication is crucial during a disruption. Clearly define and communicate cybersecurity roles and responsibilities within your organization and with vendors [2]. Service-Level Agreements (SLAs) should include specific performance metrics. For example, SaaS vendors might have uptime minimums, while IT providers could have targets for security patches, maintenance schedules, defect rates, and response times [3].
"The AHA further noted this cyberattack 'demonstrated that the national consequences of cyberattacks targeting mission-critical third-party providers can be even more devastating than when hospitals or health systems are attacked directly.'" – American Hospital Association (AHA) [2]
Use real-time visibility tools to monitor vendor compliance, security certifications, and emerging risks. These tools can send immediate notifications to stakeholders about vendors that need reassessment or have critical documents nearing expiration [6]. Maintain centralized documentation for vendor contracts, security assessments, compliance certifications, and incident reports. Features like version control and audit trails ensure easy access for regulatory audits and help clarify vendor responsibilities and performance during an incident [6].
Conclusion: Building Resilience in Healthcare Supply Chains
Healthcare organizations can no longer approach vendor risk management as just another box to check. With 41% of third-party breaches in 2024 impacting healthcare organizations - making it the hardest-hit industry - and hospitals managing thousands of vendors, the stakes couldn't be higher [2]. The transition from transactional supply chain practices to a strategic approach is no longer optional; it's critical for maintaining both patient care and operational stability [7].
True resilience requires more than surface-level compliance. It demands thorough vendor visibility, proactive risk evaluations, and well-tested contingency plans. For instance, companies that integrate AI into supply chain management have seen disruptions drop by as much as 50% [8]. These advanced tools go beyond simply tracking vendors - they reveal hidden interdependencies, predict potential breakdowns, and provide actionable solutions when vital supplies are in jeopardy.
Platforms like Censinet RiskOps™ use AI and automation to continuously evaluate and monitor vendor risks across extensive networks. They highlight connections that reach even tier-n suppliers and contextualize risks using real-time data. With capabilities such as automated vendor monitoring, centralized documentation, and real-time compliance alerts, healthcare organizations can pinpoint vulnerabilities and address emerging risks before they affect patient care.
The cost of ignoring these risks is steep. Operational disruptions can snowball into regulatory fines, lawsuits, financial losses, and long-term reputational harm [2][9]. Even more alarming, downstream entities impacted by multi-party incidents outnumber primary victims by over 800% [9]. A single vendor’s failure can ripple across the entire healthcare ecosystem, underscoring the urgent need for proactive investment in digital risk management.
To safeguard against future disruptions, healthcare organizations should prioritize digital tools, integrate cybersecurity clauses into vendor contracts, and routinely test contingency plans. These steps are essential to securing operations and ensuring uninterrupted care.
FAQs
What are the best ways for healthcare organizations to centralize and manage vendor inventories effectively?
Healthcare organizations can better manage vendor inventories by taking a structured approach to vendor risk management. Start with a formal risk assessment process, which could include standardized questionnaires, audits, and third-party risk ratings to pinpoint potential vulnerabilities.
For smoother operations, automated tools can be a game-changer. These tools allow real-time monitoring and create efficient workflows for assessments. By using them, organizations gain a clearer view of the supply chain, making it easier to identify and resolve risks while maintaining the continuity of essential healthcare services.
How can healthcare organizations effectively identify and prioritize vendor risks to prevent supply chain disruptions?
To pinpoint and manage vendor risks effectively, begin with comprehensive risk assessments, concentrating on your most essential vendors. Look into potential weak points, such as operational, strategic, and financial risks, while making sure cybersecurity requirements are explicitly outlined in your contracts.
Leverage tools like real-time monitoring to keep a close watch on vendor performance. Diversify your supplier network to minimize reliance on any single vendor, reducing potential vulnerabilities. It’s also crucial to establish strong contingency plans to maintain operations smoothly in the face of unexpected disruptions. Taking these proactive steps can help healthcare organizations protect their supply chains and maintain consistent operations.
Why is it important to regularly test contingency plans in healthcare supply chains?
Regular testing of contingency plans is a must for healthcare organizations to stay ready for unexpected disruptions. It’s a way to spot potential gaps in those plans and make adjustments before they turn into real problems.
By addressing weak points ahead of time, organizations can reduce risks to patient care and keep operations running smoothly, even when supply chain issues arise. Regular drills and reviews also ensure that staff know the procedures inside and out, allowing them to respond faster and more effectively when challenges hit.


