Healthcare Vendor Risk Auditing: Regulatory Preparation and Documentation
Post Summary
Healthcare organizations rely on third-party vendors for critical services like IT, clinical systems, and revenue management. However, these partnerships come with serious risks, including data breaches and regulatory non-compliance. By 2024, 30% of data breaches are expected to involve third parties. The average cost of a healthcare data breach is nearly $10 million, and over 65% of healthcare organizations have faced ransomware attacks. Vendor risk auditing is essential for compliance with laws like HIPAA, which mandates organizations to ensure vendor security through agreements and continuous monitoring.
This guide outlines six key steps for healthcare organizations to manage vendor risks effectively:
- Build a detailed vendor inventory: Identify all third-party relationships and classify vendors by risk level.
- Align audits with regulations: Translate laws like HIPAA and HITECH into measurable audit goals.
- Conduct vendor risk assessments: Use questionnaires and evidence collection to evaluate vendor compliance.
- Organize documentation: Maintain structured records like contracts, policies, and certifications for audits.
- Run practice audits: Test your processes to identify and fix compliance gaps.
- Monitor vendors continuously: Track security practices and maintain audit-ready reports.
Tools like automation platforms can simplify these processes, helping organizations stay compliant and prepared for regulatory audits.
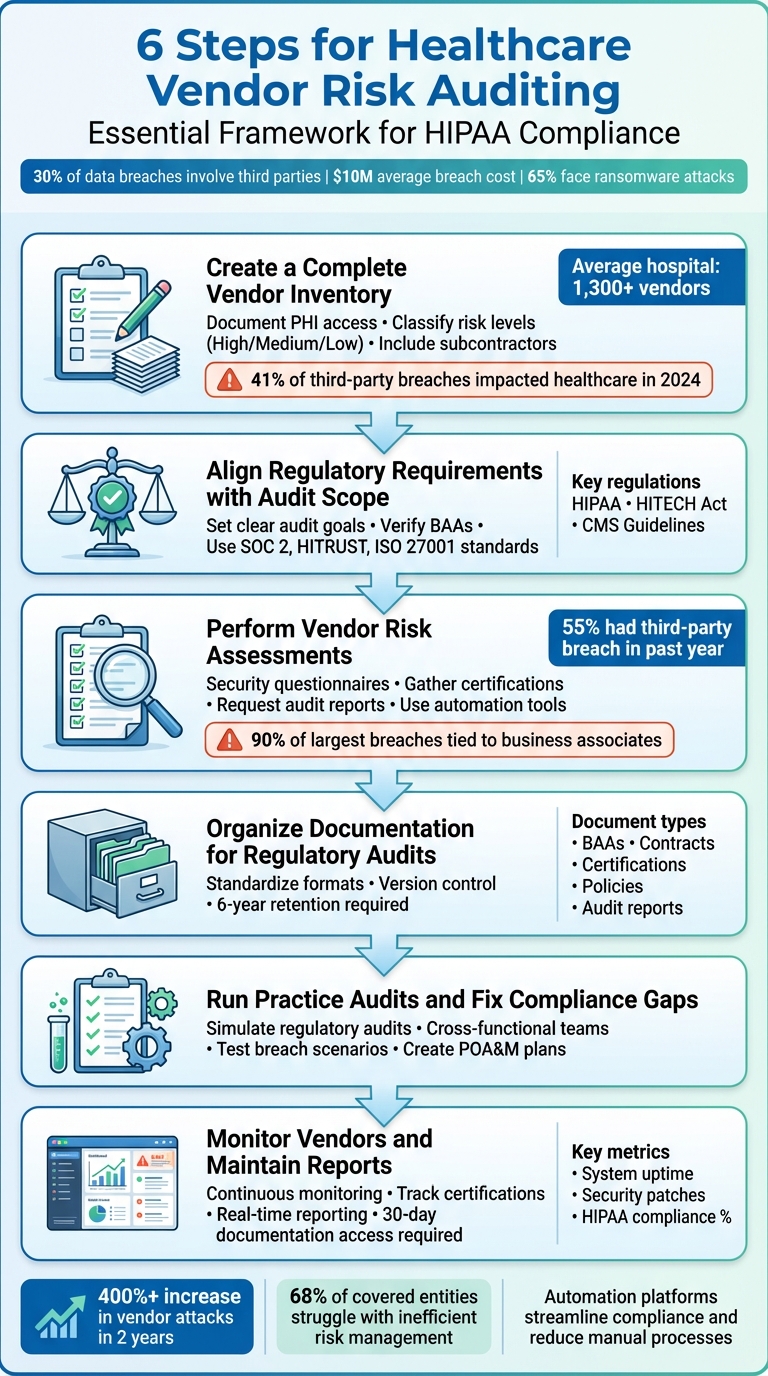
6 Steps for Healthcare Vendor Risk Auditing and Compliance
Step 1: Create a Complete Vendor Inventory
Hospitals, on average, collaborate with over 1,300 vendors [4]. Without a detailed inventory, it’s nearly impossible to pinpoint potential risks or determine which vendors require more scrutiny. Start by listing every third-party relationship your organization has - this includes vendors in IT, clinical services, billing, telehealth, medical devices, and marketing. Pay special attention to any third party that interacts with your systems, handles patient data, or supports operational processes.
For each vendor, document their role, the services they provide, and the type of data they access. Make a note of whether they handle protected health information (PHI), have access to your network, or manage critical patient care systems. Don’t forget to include subcontractors in this inventory. In 2024, 41% of third-party breaches impacted healthcare organizations [4], with vendor-related attacks skyrocketing by over 400% in just two years [1]. These subcontractors introduce what’s known as fourth-party risks, which can leave your organization vulnerable to unexpected breaches. Creating this inventory lays the groundwork for assessing and managing risks accurately.
Assign Risk Levels to Each Vendor
Once you’ve compiled your inventory, classify vendors into high, medium, or low-risk categories based on factors like PHI access, their role in operations, and their subcontractor relationships. High-risk vendors might include cloud service providers like AWS or Microsoft Azure, EHR system providers, medical device software vendors, payment processors, and telehealth platforms [3]. These vendors typically have access to sensitive data or are integral to operations, meaning any compromise could significantly disrupt patient care.
On the other hand, low-risk vendors - such as external marketing firms with no access to internal systems or patient data - don’t require as much oversight [3]. When determining risk levels, think about the potential financial or operational fallout of a breach or service failure. Use standardized criteria to make sure your classification process is consistent across all vendors [1].
Document All Vendor Relationships
Keep a detailed record of every vendor relationship, including contracts, Business Associate Agreements (BAAs), access permissions, security certifications, and audit results. This documentation should answer critical questions like: What data does this vendor access? What security measures are in place? Who are their subcontractors? When was their last security assessment? Having clear, accurate records makes regulatory audits easier and ensures you can respond quickly if an incident occurs.
Step 2: Align Regulatory Requirements with Audit Scope
Once you've built a detailed vendor inventory, the next step is to connect regulatory requirements directly to your audit criteria. This means breaking down the laws and guidelines that apply to your industry and translating them into clear, measurable objectives for your audits. In healthcare, the regulatory landscape is intricate, with both federal and state laws demanding specific actions for managing vendor relationships. This process lays the groundwork for focused and effective risk assessments.
Review Key Healthcare Regulations
One of the most critical regulations for healthcare vendor audits is HIPAA (Health Insurance Portability and Accountability Act). HIPAA's Privacy, Security, and Breach Notification Rules set the standard for vendor audits. Under the Security Rule, organizations must implement strong administrative, technical, and physical safeguards to protect Electronic Protected Health Information (ePHI). This includes conducting a comprehensive risk analysis that extends to all vendors handling ePHI.
The HITECH Act (Health Information Technology for Economic and Clinical Health Act) builds on HIPAA by strengthening privacy protections and imposing stricter penalties for non-compliance. Additionally, CMS Guidelines (Conditions of Participation for Medicare and Medicaid) ensure that vendor services meet Medicare and Medicaid compliance requirements. Upcoming changes to the HIPAA Security Rule may eliminate the distinction between "required" and "addressable" controls, potentially introducing mandatory safeguards and annual compliance audits.
Set Clear Audit Goals and Standards
Now that the regulatory framework is defined, it’s time to turn those requirements into actionable audit goals. Start by verifying that vendors are implementing key data protection measures like encryption, access controls, and secure data storage. Each vendor handling ePHI must have a signed Business Associate Agreement (BAA) that outlines safeguards, breach reporting duties, and subcontractor responsibilities. Go beyond the basics - review their security policies, incident response plans, employee training programs, and physical security measures to ensure compliance.
To further refine your audit process, align vendor requirements with established standards such as SOC 2 Type II, HITRUST CSF, ISO 27001, and PCI-DSS. Use these frameworks to determine how often vendors should be audited based on their risk level. For example, high-risk vendors may need annual or even continuous monitoring, while lower-risk vendors might only require audits every two to three years. This tiered approach helps you focus resources where they’re needed most.
Step 3: Perform Vendor Risk Assessments
Now that you've defined your audit scope and regulatory requirements, it's time to assess how well your vendors align with security and compliance standards. This means digging into how they protect data, manage access, and handle security incidents - all while ensuring the process stays manageable, even if you're dealing with dozens (or hundreds) of vendors.
Distribute Security Questionnaires and Gather Evidence
Start by sending out standardized security questionnaires tailored to each vendor's risk level. For high-risk vendors who handle sensitive data like ePHI, include questions covering areas like administrative safeguards, technical controls, physical security, and incident response plans. Don't forget to add subcontractor-specific questions to uncover any hidden risks [1].
Ask vendors to back up their responses with documentation. This might include compliance certifications like SOC 2 Type II, HITRUST assessments, ISO 27001, or PCI-DSS attestations [1][2][8]. You should also request third-party audit reports, recent penetration test results, and remediation plans (POA&M) that explain how they're addressing vulnerabilities [2][7]. Take time to review their security policies, data handling procedures, access controls, and employee training programs. If anything is missing or unclear, follow up right away [5].
Here's why this step is so critical: 55% of healthcare organizations reported a data breach caused by a third party in the past year. In 2022, 90% of the largest healthcare breaches were tied to business associates, with the average cost exceeding $10 million per incident [6]. Despite these alarming stats, 68% of HIPAA-covered entities and 79% of business associates admit their third-party risk management processes are inefficient. Worse yet, 60% of covered entities and 72% of business associates believe their current methods fail to prevent breaches [6].
Use Automation to Streamline Risk Assessments
Manual reviews of vendor documentation can be slow and inconsistent. That’s where automation comes in. Platforms like Censinet RiskOps™ simplify the process by automating key parts of vendor risk assessments. For example, Censinet AI™ allows vendors to complete their security questionnaires online. The platform then summarizes the evidence, highlights key integration details, flags fourth-party risks, and generates comprehensive risk summary reports.
Automation tools like these also help maintain oversight. Configurable rules and workflows ensure your risk team stays in control while the platform handles tasks like evidence validation and initial risk scoring. Real-time data is centralized in a single dashboard, making it easy to track vendor policies, risks, and tasks. Advanced routing ensures findings are sent to the right stakeholders, so issues are addressed quickly and efficiently.
Step 4: Organize Documentation for Regulatory Audits
Once your vendor risk assessments are complete, the next step is to organize your documentation in a way that ensures you're ready for audits. Disorganized files can lead to wasted time, unnecessary stress, and even penalties during audits. Keeping your documentation well-structured helps avoid delays, reduces the risk of fines, and demonstrates compliance and transparency [7].
Gather Required Documentation
After conducting your risk assessments, shift your focus to gathering all the materials needed for audits. Build on your existing inventory by including compliance-specific documents. Key categories to collect include:
- Operational Documents: Business Associate Agreements (BAAs), vendor contracts, and internal policies.
- Data Privacy Documents: Policies related to data collection, training logs, and incident response plans.
- Technical Security Documents: Access control policies, encryption standards, vulnerability management details, and penetration testing reports.
- Audit Documents: Third-party certifications like SOC 2 Type II, HITRUST, and ISO 27001, along with corrective action plans [2][7].
Create a structured framework to manage these documents, ensuring they are easy to collect, share, and store. This framework should align with regulatory requirements like HIPAA [7]. When reviewing third-party audit reports, pay close attention to the scope, testing methods, and whether subcontractors were included in the audit. If any expected controls or processes were not covered, follow up with the vendor to obtain additional evidence [2].
Create Standard Documentation Formats
Using standardized templates for your documentation can make a big difference. These templates should include key details such as risk description, owner, likelihood, impact, response strategy, and status [9]. A consistent format not only makes the documents easier to read but also ensures all critical information is captured [9].
To maintain consistency across your organization, align your documentation with established risk management frameworks like ISO 31000, COSO, HIPAA, SOC 2, or HITRUST. Assign responsibility for each document - whether to a specific individual or department - to ensure risks are tracked, managed, and updated as needed [9].
Keep version control and audit trails to document all changes over time. This is essential for maintaining compliance and simplifying audits. Schedule regular reviews - whether monthly, quarterly, or annually - to reassess risks, update controls, and incorporate any new developments. This approach ensures your documentation stays up-to-date and fully aligned with your compliance strategy [9].
sbb-itb-535baee
Step 5: Run Practice Audits and Fix Compliance Gaps
Once your documentation is in order, it’s time to test your vendor risk management program against regulatory standards. Running practice audits can help you pinpoint compliance gaps early, allowing you to address them before they become bigger issues. Internal auditors play a key role here - they can assess how effective your controls are, spot weaknesses in your processes, and suggest ways to improve your third-party risk management efforts [5].
Conduct Internal Practice Audits
Your practice audits should mimic the structure and rigor of actual regulatory audits, such as those conducted by agencies like OCR or CMS. This approach helps you uncover potential issues before the regulators do [10]. Start by reviewing vendor service agreements to ensure they meet necessary standards and provide sufficient coverage. Your internal audit team should also focus on areas that regulators typically examine, such as Business Associate Agreements, data security measures, breach notification protocols, and access management policies.
Bring together cross-functional teams to conduct these reviews. As AuditBoard highlights:
Collaboration across the organization is a key component. Partnerships between IT, compliance, and clinical teams are essential for aligning organizational goals and risk priorities, including cybersecurity and regulatory compliance [10].
Incorporate simulated breach exercises, such as ransomware attack scenarios, to test your incident response plans. EY research emphasizes the importance of these exercises:
Proactively testing different types of simulated ransomware attacks can assist teams in identifying and closing response gaps and improve recovery times [10].
These practice audits not only help you find vulnerabilities but also set the stage for effective remediation in the next phase.
Create Plans to Fix Identified Problems
For every issue identified, develop a Plan of Action and Milestones (POA&M). This plan should outline the tasks, resources, timelines, and milestones needed to resolve each problem [4].
Focus your efforts on the most critical vulnerabilities first, especially those involving high-risk vendors or areas with significant compliance implications. Addressing these issues promptly ensures your organization stays on track. Once remediation plans are underway, you’ll be ready to move on to continuous vendor monitoring in the next step.
Step 6: Monitor Vendors and Maintain Reports
Keeping tabs on vendors and maintaining thorough documentation is crucial for staying compliant. A solid vendor risk management program should consistently monitor changes in vendor security practices, identify emerging risks, and keep detailed records that regulators can review at any time. This step ensures your organization is always audit-ready while maintaining strong vendor relationships throughout their lifecycle [11]. It builds on your remediation efforts, emphasizing that vendor compliance is an ongoing process - not a one-time task.
Track Vendor Compliance and Risks
Using your documented assessments as a foundation, continuous monitoring helps you stay ahead of evolving vendor risks. This means integrating oversight throughout every stage of the vendor lifecycle - from onboarding to offboarding [11]. For vendors classified as high-risk, require ongoing security certifications rather than relying on one-time assessments. Certifications like HITRUST, SOC 2 Type II, and ISO 27001 are essential as they validate continuous compliance [1].
Keep an eye on critical performance metrics, such as:
- System uptime minimums
- Adherence to security patches
- Maintenance records
- Equipment defect rates
- Response times
- HIPAA compliance percentages
- Violations found and issue severity
- Corrective actions completed during audits [1]
Set up incident alerts and require vendors to provide regular attestations to confirm they remain compliant.
Create Reports Ready for Auditors
Platforms like Censinet RiskOps™ simplify compliance by generating detailed, real-time reports that keep your documentation audit-ready. By centralizing all vendor risk management activities, the platform ensures quick access to records - a vital feature since HIPAA mandates organizations to produce documentation within 30 days of a compliance request or investigation [6].
Your reporting system should cover the following:
- Risk analyses and remediation plans
- Sanctions policies
- Procedures for reviewing information system activity regularly [6]
Additionally, make sure to store all documentation for at least six years, as required by regulatory guidelines [6]. Censinet RiskOps™ acts as a hub for risk management, offering visual dashboards that consolidate real-time data. These dashboards make it easy for both internal stakeholders and auditors to understand your compliance efforts. With this centralized system, you’ll always be ready to demonstrate your organization’s dedication to effective vendor risk management when regulators come knocking.
Conclusion
Vendor risk auditing is not a one-and-done task - it's an ongoing effort, and for good reason. In healthcare, vendor-related attacks have surged by over 400% in just two years, with the average cost of a data breach now approaching $10 million[1]. Adding to the urgency, 90% of the largest healthcare data breaches in 2022 were tied to business associates of HIPAA-covered entities[6].
By following the six steps outlined earlier, your organization can establish a strong compliance framework. This not only helps reduce the risk of HIPAA violations but also ensures you're better equipped to adapt to changing regulatory demands[6].
Tools like Censinet RiskOps™ can make a significant difference. The platform centralizes vendor data and automates tedious manual processes - critical for the 68% of covered entities and 79% of business associates struggling with inefficiencies in traditional risk management[6]. With streamlined operations, your organization can take a proactive stance on compliance and stay ready for regulatory challenges.
FAQs
What are the essential steps for managing vendor risks in healthcare effectively?
Effective vendor risk management in healthcare calls for a planned and forward-thinking strategy. Begin by performing thorough due diligence on all vendors to uncover any potential risks. It's equally important to implement ongoing monitoring to keep tabs on changes in vendor performance or compliance over time.
Group your vendors by their risk levels, focusing your assessments on those that present higher risks. Regular risk evaluations are crucial for identifying vulnerabilities, and keeping organized compliance records ensures you're prepared for audits. Set up clear communication channels with vendors to quickly address any issues. Finally, when terminating a partnership, make sure vendors are offboarded securely to safeguard sensitive information.
How does Censinet RiskOps™ simplify and improve vendor risk auditing for healthcare organizations?
Censinet RiskOps™ takes the hassle out of vendor risk auditing by automating essential steps such as onboarding, conducting risk assessments, and ongoing monitoring. This not only cuts down on manual effort but also reduces errors, making workflows smoother and more reliable.
With real-time data on vendor compliance and risk, healthcare organizations can make quicker, better-informed decisions while adhering to regulatory requirements. By simplifying these processes, Censinet RiskOps™ allows healthcare providers to concentrate on delivering excellent patient care without sacrificing cybersecurity or compliance.
Why is it important to continuously monitor vendors for healthcare compliance?
Keeping a close eye on vendors is crucial for healthcare compliance. Why? It helps organizations spot and address risks like cyber threats, data breaches, and regulatory lapses before they escalate. This kind of real-time monitoring ensures vendors stick to security controls and comply with important regulations like HIPAA.
Staying alert not only protects against vulnerabilities that could lead to hefty fines, damage to reputation, or even jeopardize patient safety, but it also strengthens partnerships with vendors. Plus, it helps ensure everyone stays on track with compliance standards over the long haul.


